DEPLOYMENT IPV6 OVER IPV4 NETWORK INFRASTRUCTURE Tien Dung Hoang
... businesses in multi fields of ISP, technical solutions, software development, system integration, retails and finance. This thesis is divided in three chapters. Chapter 2 and 3 are theoretical parts of this thesis. The aim of chapter 2 is giving an overview on both IPv4 and IPv6, and concluding by ...
... businesses in multi fields of ISP, technical solutions, software development, system integration, retails and finance. This thesis is divided in three chapters. Chapter 2 and 3 are theoretical parts of this thesis. The aim of chapter 2 is giving an overview on both IPv4 and IPv6, and concluding by ...
Strategies for Internet Route Control Past, Present, and Future
... control the routing and TE decisions performed by routing domains. Therefore, this thesis explores different strategies on how to control such decisions in a highly efficient and accurate way. At present, this control mostly resides in BGP, but as mentioned above, BGP is in fact one of the main caus ...
... control the routing and TE decisions performed by routing domains. Therefore, this thesis explores different strategies on how to control such decisions in a highly efficient and accurate way. At present, this control mostly resides in BGP, but as mentioned above, BGP is in fact one of the main caus ...
3346 Software User Guide V6.3
... acts as a pass-through device and allows the workstations on your LAN to have public addresses directly on the internet. ...
... acts as a pass-through device and allows the workstations on your LAN to have public addresses directly on the internet. ...
Reorder Density (RD): A Formal, Comprehensive Metric for Packet Reordering
... treated as lost thereby decreasing the perceived quality of voice. To recover from reordering, the out-of-sequence packets are buffered until they can be played back in sequence to the application. Thus, an increase in out-of-order delivery by the network consumes more resources at the end-hosts, an ...
... treated as lost thereby decreasing the perceived quality of voice. To recover from reordering, the out-of-sequence packets are buffered until they can be played back in sequence to the application. Thus, an increase in out-of-order delivery by the network consumes more resources at the end-hosts, an ...
CS610 Final term MAGA file.. all paperz are in 1 file
... communicate and exchange information. The PDU information is only read by the peer layer on the receiving device and then stripped off, and data is handed over to the next upper layer. FINALTERM EXAMINATION Fall 2008 CS610- Computer Network Ref No: 325806 Time: 120 min Marks: 70 Question No: 1 ( Mar ...
... communicate and exchange information. The PDU information is only read by the peer layer on the receiving device and then stripped off, and data is handed over to the next upper layer. FINALTERM EXAMINATION Fall 2008 CS610- Computer Network Ref No: 325806 Time: 120 min Marks: 70 Question No: 1 ( Mar ...
2930F TAA Switch Series Data Sheet
... • Source-port filtering allows only specified ports to communicate with each other • RADIUS/TACACS+ eases switch management security administration by using a password authentication server • IEEE 802.1X, MAC, or Web authentication provides concurrent network access control and Web authentication of ...
... • Source-port filtering allows only specified ports to communicate with each other • RADIUS/TACACS+ eases switch management security administration by using a password authentication server • IEEE 802.1X, MAC, or Web authentication provides concurrent network access control and Web authentication of ...
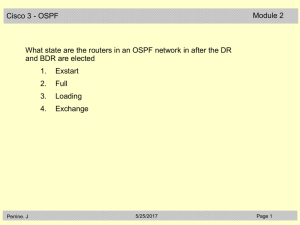
20088-2 CCNA3 3.1-02 Questions OSPF
... The link-state database is stored in a designated router and is accessed by each router in the area as needed. ...
... The link-state database is stored in a designated router and is accessed by each router in the area as needed. ...
`Talk` Applications in C and Java
... The server may now wait for a connection request to arrive on the local port and local address(es) it is bound to. This may be done by using the ACCEPT primitive which “blocks” until such a request arrives from a client. Making a call to a “blocking” function means that the program will appear to fr ...
... The server may now wait for a connection request to arrive on the local port and local address(es) it is bound to. This may be done by using the ACCEPT primitive which “blocks” until such a request arrives from a client. Making a call to a “blocking” function means that the program will appear to fr ...
CNC 8055 Educational
... newer). The possible connections are: • Connection from a PC: The connection may be initiated at any PC and addressed to any CNC. Two PC's cannot be connected to each other. To establish the connection, the WinDNC allows the user to enter the CNC's IP address to be used for the connection. • Connect ...
... newer). The possible connections are: • Connection from a PC: The connection may be initiated at any PC and addressed to any CNC. Two PC's cannot be connected to each other. To establish the connection, the WinDNC allows the user to enter the CNC's IP address to be used for the connection. • Connect ...
vPath - Cisco Communities
... client source, but increases deployment complexity and operation cost • Inline ADC’s become performance bottleneck high-performance ...
... client source, but increases deployment complexity and operation cost • Inline ADC’s become performance bottleneck high-performance ...
Tsunami 8000 Series (Point-to-point and Point-to
... The names “OpenSSL Toolkit” and “OpenSSL Project” must not be used to refer to, endorse, or promote the products or for any other purpose related to the products without prior written permission. For written permission, please contact [email protected]. This software is provided by the OpenSS ...
... The names “OpenSSL Toolkit” and “OpenSSL Project” must not be used to refer to, endorse, or promote the products or for any other purpose related to the products without prior written permission. For written permission, please contact [email protected]. This software is provided by the OpenSS ...
EE689 Lecture 12
... • A multicast sender uses the group address as the receiver’s address when sending packets • Network/routers keep track of actual receiving subnets/paths for this group address (not the actual receivers) • Receivers can reply to sender’s address or to group address ...
... • A multicast sender uses the group address as the receiver’s address when sending packets • Network/routers keep track of actual receiving subnets/paths for this group address (not the actual receivers) • Receivers can reply to sender’s address or to group address ...
UMTS - Kleines Seminar
... Evolution of wireless communication systems Features and services of UMTS ...
... Evolution of wireless communication systems Features and services of UMTS ...
SNAP Network Operating System - Synapse forums
... and receive serial data, or connect to other devices over connections like SPI and I2C. And with your own SNAPpy script in place, the device can be smart enough to know what signals and messages, or what combination of signals and messages, is important enough to act upon – whether that action is se ...
... and receive serial data, or connect to other devices over connections like SPI and I2C. And with your own SNAPpy script in place, the device can be smart enough to know what signals and messages, or what combination of signals and messages, is important enough to act upon – whether that action is se ...
Document
... 4 subnets can be represented with 2 bits (22 = 4) For a class B address, which already uses 16 bits for the network portion, the address would use 18 bits for the subnet portion ...
... 4 subnets can be represented with 2 bits (22 = 4) For a class B address, which already uses 16 bits for the network portion, the address would use 18 bits for the subnet portion ...
PDF
... 1 Information About the IPS Module on the ASA The IPS module might be a physical module or a software module, depending on your ASA model. For ASA model software and hardware compatibility with the IPS module, see the Cisco ASA Compatibility at http://www.cisco.com/en/US/docs/security/asa/compatibi ...
... 1 Information About the IPS Module on the ASA The IPS module might be a physical module or a software module, depending on your ASA model. For ASA model software and hardware compatibility with the IPS module, see the Cisco ASA Compatibility at http://www.cisco.com/en/US/docs/security/asa/compatibi ...
SnapGear Administration Guide Firmware Version 3.1.5
... equipment. This Agreement also will automatically terminate if you do not comply with any terms or conditions of this Agreement. Upon such termination you agree to destroy the Software Product and erase all copies residing on computer equipment. 7. PROTECTION OF CONFIDENTIAL INFORMATION. The Softwar ...
... equipment. This Agreement also will automatically terminate if you do not comply with any terms or conditions of this Agreement. Upon such termination you agree to destroy the Software Product and erase all copies residing on computer equipment. 7. PROTECTION OF CONFIDENTIAL INFORMATION. The Softwar ...
Gnutella2: A Better Gnutella?
... Gnutella2's method further reduces the number of messages sent for a query: Less ...
... Gnutella2's method further reduces the number of messages sent for a query: Less ...
The Gartner Glossary of Information Technology Acronyms and Terms
... asynchrony, autonomy, code mobility and higher-level messaging protocols. The primary design rationale of ABSE is to advocate software engineering principles that better match the characteristics of the real world, i.e., having dynamic and persistent entities communicating and interacting in coopera ...
... asynchrony, autonomy, code mobility and higher-level messaging protocols. The primary design rationale of ABSE is to advocate software engineering principles that better match the characteristics of the real world, i.e., having dynamic and persistent entities communicating and interacting in coopera ...
On peer-to-peer (P2P) content delivery
... sharing applications, such as BitTorrent or eDonkey, chop the file into blocks (also called pieces, packets) and deliver the chopped block in non sequential order. Therefore, the shared video is not playable until the entire video is retrieved. But even on a slow connection, the video will look grea ...
... sharing applications, such as BitTorrent or eDonkey, chop the file into blocks (also called pieces, packets) and deliver the chopped block in non sequential order. Therefore, the shared video is not playable until the entire video is retrieved. But even on a slow connection, the video will look grea ...
BSR Troubleshooting Guide
... 2. Isolate the cause or symptom of the problem and try to determine its scope. For example, determine if it is the whole HFC network, a particular subnetwork on the HFC network, or just one subscriber that is experiencing the problem. See Isolating the Problem, later in this document, for more infor ...
... 2. Isolate the cause or symptom of the problem and try to determine its scope. For example, determine if it is the whole HFC network, a particular subnetwork on the HFC network, or just one subscriber that is experiencing the problem. See Isolating the Problem, later in this document, for more infor ...
No Slide Title
... • When a router detects that a packetshould have gone to a different (better) router, the router (here R2) • forwards the packet to the correct router • sends an ICMP redirect message to the host • Host uses ICMP message to update its routing table ...
... • When a router detects that a packetshould have gone to a different (better) router, the router (here R2) • forwards the packet to the correct router • sends an ICMP redirect message to the host • Host uses ICMP message to update its routing table ...
The History of nordunet
... via nordunet that the Nordic national research networks (nrens) have access to other research networks around the world and to the general Internet. nordunet is not only a data network, but also a non-profit organization acting as a framework for Nordic collaboration in networking. As such, it repres ...
... via nordunet that the Nordic national research networks (nrens) have access to other research networks around the world and to the general Internet. nordunet is not only a data network, but also a non-profit organization acting as a framework for Nordic collaboration in networking. As such, it repres ...
Active Mapping - University of California, Berkeley
... accepted by the receiver. To do so, we can use any service for which we can tell by its response whether it received the specific data. To date, we have developed concrete implementations of SSH and HTTP beneath this abstraction. Other tests require simpler abstract interfaces. PMTU determination, f ...
... accepted by the receiver. To do so, we can use any service for which we can tell by its response whether it received the specific data. To date, we have developed concrete implementations of SSH and HTTP beneath this abstraction. Other tests require simpler abstract interfaces. PMTU determination, f ...