Application Note: How to Evaluate WirelessHART Network and Device Performance
... This documentation is provided “as is” without warranty of any kind, either expressed or implied, including but not limited to, the implied warranties of merchantability or fitness for a particular purpose. This documentation might include technical inaccuracies or other errors. Corrections and impr ...
... This documentation is provided “as is” without warranty of any kind, either expressed or implied, including but not limited to, the implied warranties of merchantability or fitness for a particular purpose. This documentation might include technical inaccuracies or other errors. Corrections and impr ...
OSPF
... Cisco routers default to T1 (1.544 Mbps) on all serial interfaces and require manual modification with the bandwidth command. ...
... Cisco routers default to T1 (1.544 Mbps) on all serial interfaces and require manual modification with the bandwidth command. ...
Application Notes for Configuring QuesCom 300 IP/GSM Gateway
... In the sample configuration described in these Application Notes, when placing outbound calls to the public network, stations on Avaya Communication Manager must first dial the ARS Feature Access Code (FAC) before dialing an external number. The single digit “9” was used as the ARS FAC in the compli ...
... In the sample configuration described in these Application Notes, when placing outbound calls to the public network, stations on Avaya Communication Manager must first dial the ARS Feature Access Code (FAC) before dialing an external number. The single digit “9” was used as the ARS FAC in the compli ...
Paper Title (use style: paper title)
... Currently, multicast scoping technique uses either the “Time To Live” field in the IPv4 packet header or the scope field in case of IPv6. In IPv6, the scope filed is an integrated part of the multicast address itself. The IETF has particularly defined guidelines that explain how to assign and alloca ...
... Currently, multicast scoping technique uses either the “Time To Live” field in the IPv4 packet header or the scope field in case of IPv6. In IPv6, the scope filed is an integrated part of the multicast address itself. The IETF has particularly defined guidelines that explain how to assign and alloca ...
Raven and PinPoint GPRS User Guide
... GPRS is an IP-based service that offers fast, packet-switched access to data networks such as the Internet. It is a mobile service that improves the peak-time capacity of a GSM network. GPRS gives packet-switched access over GSM to external data networks with high peak transfer capacity. The main ob ...
... GPRS is an IP-based service that offers fast, packet-switched access to data networks such as the Internet. It is a mobile service that improves the peak-time capacity of a GSM network. GPRS gives packet-switched access over GSM to external data networks with high peak transfer capacity. The main ob ...
FCTC_Zamer_iscsi
... begins and ends?? By reading the length field in the iSCSI header Determines where in byte stream current message ends and next begins NIC must stay “in sync” with beginning of byte stream Works well in a perfect world (Maybe a SAN or LAN ????) ...
... begins and ends?? By reading the length field in the iSCSI header Determines where in byte stream current message ends and next begins NIC must stay “in sync” with beginning of byte stream Works well in a perfect world (Maybe a SAN or LAN ????) ...
re-feedback - Bob Briscoe
... • if unresponsive to congestion, get to keep whatever they need • r-t apps take more than fair share without asking the network ...
... • if unresponsive to congestion, get to keep whatever they need • r-t apps take more than fair share without asking the network ...
ExperimenTor: A Testbed for Safe and Realistic Tor Experimentation Kevin Bauer
... client’s security and performance over the course of several months of participation in the Tor network. While these experiments offer valuable insight into the proposed selection technique, they do not analyze the behavior of the proposed algorithm when many or all Tor clients use various configura ...
... client’s security and performance over the course of several months of participation in the Tor network. While these experiments offer valuable insight into the proposed selection technique, they do not analyze the behavior of the proposed algorithm when many or all Tor clients use various configura ...
PowerPoint - DePaul University
... Don't want to see packets with private IP addresses -A input -s 192.168.0.0/255.255.0.0 -d 0/0 -j DENY -A input -s 172.0.0.0/255.240.0.0 -d 0/0 -j DENY -A input -s 10.0.0.0/255.0.0.0 -d 0/0 -j DENY Let SSH, established TCP connections, FTP data, UDP and BOOTP/DHCP in -A -A -A -A -A ...
... Don't want to see packets with private IP addresses -A input -s 192.168.0.0/255.255.0.0 -d 0/0 -j DENY -A input -s 172.0.0.0/255.240.0.0 -d 0/0 -j DENY -A input -s 10.0.0.0/255.0.0.0 -d 0/0 -j DENY Let SSH, established TCP connections, FTP data, UDP and BOOTP/DHCP in -A -A -A -A -A ...
SAILOR 500/250 FleetBroadband Including 19” Rack Version
... connected to an electrical ground. The terminal must be grounded to the ship. For further grounding information refer to the Installation manual. Do not extend the cables beyond the lengths specified for the equipment. The cable between the terminal and antenna can be extended if it complies with th ...
... connected to an electrical ground. The terminal must be grounded to the ship. For further grounding information refer to the Installation manual. Do not extend the cables beyond the lengths specified for the equipment. The cable between the terminal and antenna can be extended if it complies with th ...
MPLS Transport Profile (MPLS-TP) - Center for Integrated Access
... plane may have applicability in scenarios where some equipment, especially equipment used at the edges of the network, does not support a dynamic control plane, or in which static configuration is preferred for security reasons. The NMS-driven control plane also allows operators to manage the packet ...
... plane may have applicability in scenarios where some equipment, especially equipment used at the edges of the network, does not support a dynamic control plane, or in which static configuration is preferred for security reasons. The NMS-driven control plane also allows operators to manage the packet ...
Hash-Based IP Traceback - Events
... path through the network. If a path can be traced through any number of non-subverted routers, then it must terminate at either the source of the flow or pass through a subverted router which can be considered to be a co-conspirator and treated appropriately. Hence, we are interested in constructing ...
... path through the network. If a path can be traced through any number of non-subverted routers, then it must terminate at either the source of the flow or pass through a subverted router which can be considered to be a co-conspirator and treated appropriately. Hence, we are interested in constructing ...
Lab – Configuring Dynamic and Static NAT (Instructor Version)
... Inside global / local: ________________ 1034, answers will vary. Outside global / local: ________________ 23 d. Because static NAT was configured for PC-A, verify that pinging from ISP to PC-A at the static NAT public address (209.165.200.225) is successful. e. On the Gateway router, display the NAT ...
... Inside global / local: ________________ 1034, answers will vary. Outside global / local: ________________ 23 d. Because static NAT was configured for PC-A, verify that pinging from ISP to PC-A at the static NAT public address (209.165.200.225) is successful. e. On the Gateway router, display the NAT ...
Configuring VoIP for SonicOS Enhanced
... designed to prevent malicious traffic from reaching protected VoIP phones and servers. Signature granularity allows SonicWALL IPS to detect and prevent attacks based on a global, attack group, or per-signature basis to provide maximum flexibility and control false positives. ...
... designed to prevent malicious traffic from reaching protected VoIP phones and servers. Signature granularity allows SonicWALL IPS to detect and prevent attacks based on a global, attack group, or per-signature basis to provide maximum flexibility and control false positives. ...
Hyper Converged 250 System for VMware vSphere Installation Guide
... The information contained herein is subject to change without notice. The only warranties for Hewlett Packard Enterprise products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional wa ...
... The information contained herein is subject to change without notice. The only warranties for Hewlett Packard Enterprise products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional wa ...
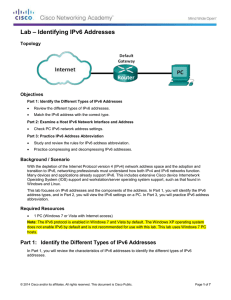
8.2.5.4 Lab – Identifying IPv6 Addresses
... There are other IPv6 address types that are either not yet widely implemented, or have already become deprecated, and are no longer supported. For instance, an anycast address is new to IPv6 and can be used by routers to facilitate load sharing and provide alternate path flexibility if a router beco ...
... There are other IPv6 address types that are either not yet widely implemented, or have already become deprecated, and are no longer supported. For instance, an anycast address is new to IPv6 and can be used by routers to facilitate load sharing and provide alternate path flexibility if a router beco ...
ITE PC v4.0 Chapter 1
... Different types of network media have different features and benefits Ethernet is the most common local area network (LAN) technology Ethernet ports are found on end user devices, switch devices, and other networking devices Cisco IOS switches have physical ports for devices to connect to, b ...
... Different types of network media have different features and benefits Ethernet is the most common local area network (LAN) technology Ethernet ports are found on end user devices, switch devices, and other networking devices Cisco IOS switches have physical ports for devices to connect to, b ...
Data Sheet UMUX NEBRA/NEBRO
... the UMUX multi-service access platform offers cost effective Fast Ethernet and Gigabit Ethernet connectivity combined with the proven reliability and manageability of SDH networks. This makes it ideal for bandwidth intensive point-to-point applications like corporate internet access, LAN interconnec ...
... the UMUX multi-service access platform offers cost effective Fast Ethernet and Gigabit Ethernet connectivity combined with the proven reliability and manageability of SDH networks. This makes it ideal for bandwidth intensive point-to-point applications like corporate internet access, LAN interconnec ...
TCPware for OpenVMS Network Control Utility
... DOCUMENTATION, included in the top-level directory of this release. Support and other services are available for ISC products - see http://www.isc.org for more information. ISC LICENSE, Version 1.0 1. This license covers any file containing a statement following its copyright message indicating that ...
... DOCUMENTATION, included in the top-level directory of this release. Support and other services are available for ISC products - see http://www.isc.org for more information. ISC LICENSE, Version 1.0 1. This license covers any file containing a statement following its copyright message indicating that ...
21-07-0029-00-Using the Unified Link Layer API (ULLA)
... Original Project Objectives • To solve the complexity and interoperability problem related to the large number of different APIs used for accessing communication interfaces • To provide triggers, handles and APIs for different smart, context sensitive and link/network aware applications • To solve ...
... Original Project Objectives • To solve the complexity and interoperability problem related to the large number of different APIs used for accessing communication interfaces • To provide triggers, handles and APIs for different smart, context sensitive and link/network aware applications • To solve ...
... Use Case: LAN and Services Interconnection to Scale within a Physical Site As an organization grows, the network must grow to accommodate the increased number of devices connecting to the network, as well as offer connectivity to additional services components of increased size. This design guide en ...
9.4.2 CSMA/CD – The Process
... Carrier Sense----In the CSMA/CD access method, all network devices that have messages to send must listen before transmitting. Multi-access---The media now has two devices transmitting their signals at the same time. Collision Detection----When a device is in listening mode, it can detect when ...
... Carrier Sense----In the CSMA/CD access method, all network devices that have messages to send must listen before transmitting. Multi-access---The media now has two devices transmitting their signals at the same time. Collision Detection----When a device is in listening mode, it can detect when ...
CN 2015 1-2 - DSpace
... home in which components such as the electrical system, heating and air conditioning system, and plumbing are integrated into the overall design. Taken from the Greek work "Topos" meaning "Place," Specifies the geometric arrangement of the network or a ...
... home in which components such as the electrical system, heating and air conditioning system, and plumbing are integrated into the overall design. Taken from the Greek work "Topos" meaning "Place," Specifies the geometric arrangement of the network or a ...
Fingerprinting Encrypted Tunnel Endpoints Vafa Dario Izadinia U
... together clues in the aftermath of a break-in; the more is known of the system as a whole, the more detailed the image that can be constructed. One method for acquiring this information is termed Operating System Fingerprinting, or OS Fingerprinting for short [127, 90, 123, 11, 77]. One form of OS F ...
... together clues in the aftermath of a break-in; the more is known of the system as a whole, the more detailed the image that can be constructed. One method for acquiring this information is termed Operating System Fingerprinting, or OS Fingerprinting for short [127, 90, 123, 11, 77]. One form of OS F ...