Advanced Networking: Network Address Translation (NAT)
... • STUN-enabled hosts send an exploratory message to the external STUN server to determine the transmit and receive ports to use • The STUN server examines the incoming message and informs the client which public IP address and ports were used by the NAT • These are communicated to e.g. – SIP proxies ...
... • STUN-enabled hosts send an exploratory message to the external STUN server to determine the transmit and receive ports to use • The STUN server examines the incoming message and informs the client which public IP address and ports were used by the NAT • These are communicated to e.g. – SIP proxies ...
Wireless Networking Technologies
... fading can wipe out narrow band signals for duration of the interference Solution: spread the narrow band signal into a broad band signal using a special code protection against narrow band interference ...
... fading can wipe out narrow band signals for duration of the interference Solution: spread the narrow band signal into a broad band signal using a special code protection against narrow band interference ...
20100810-OSG-NPW-Diagnostics
... • Does the problem occur all the time, frequently, or rarely? • Does the problem occur for only a specific application, many applications, or only some applications? • Is the problem reproducible on other machines? ...
... • Does the problem occur all the time, frequently, or rarely? • Does the problem occur for only a specific application, many applications, or only some applications? • Is the problem reproducible on other machines? ...
Network Load Balancing - Security Audit Systems
... enabled on the Advanced Server and Datacenter Server versions of the Windows 2000 operating system. It operates as an optional service for local area network (LAN) connections and can be enabled for one LAN connection in the system; this LAN connection is known as the cluster adapter. No hardware ch ...
... enabled on the Advanced Server and Datacenter Server versions of the Windows 2000 operating system. It operates as an optional service for local area network (LAN) connections and can be enabled for one LAN connection in the system; this LAN connection is known as the cluster adapter. No hardware ch ...
8.2 Interim Agreements on Key Issue #2: QoS
... 1a. Reflective QoS indication is signalled via inband or not signalled at all by the network. How to indicate reflective QoS to the UE is decided by the network during the PDU session establishment procedure. When reflective QoS is not signalled, all uplink flows use reflective QoS if there are corr ...
... 1a. Reflective QoS indication is signalled via inband or not signalled at all by the network. How to indicate reflective QoS to the UE is decided by the network during the PDU session establishment procedure. When reflective QoS is not signalled, all uplink flows use reflective QoS if there are corr ...
Slides for Chapter 3: Networking and
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
PPT source - IIT Bombay
... stationary computer laptop in a hotel (portable) wireless LAN in historic buildings Personal Digital Assistant (PDA) ...
... stationary computer laptop in a hotel (portable) wireless LAN in historic buildings Personal Digital Assistant (PDA) ...
2009毕业答辩
... ― SIP/IMS-based 1x circuit services architecture ― Packet data architecture ― Security framework ― Enhancements to mobile devices to make them more femtoaware ― Foundations of femtozone services (Local IP Access and Remote IP Access) ― Femtocell management architecture ...
... ― SIP/IMS-based 1x circuit services architecture ― Packet data architecture ― Security framework ― Enhancements to mobile devices to make them more femtoaware ― Foundations of femtozone services (Local IP Access and Remote IP Access) ― Femtocell management architecture ...
ppt
... • No need for periodic refresh - routes are valid until withdrawn, or the connection is lost • Incremental updates ...
... • No need for periodic refresh - routes are valid until withdrawn, or the connection is lost • Incremental updates ...
ppt - apnic
... 1b. For the non-profit/experimental candidate, the special-permission paper, issued by MOTC, is required. ...
... 1b. For the non-profit/experimental candidate, the special-permission paper, issued by MOTC, is required. ...
Top-Down Network Design
... For sales outside the United States please contact: International Sales ...
... For sales outside the United States please contact: International Sales ...
Module 8: Virtual LANs
... VLANs logically segment switched networks based on the functions, project teams, or applications of the organization regardless of the physical location or connections to the network. All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connecti ...
... VLANs logically segment switched networks based on the functions, project teams, or applications of the organization regardless of the physical location or connections to the network. All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connecti ...
A Reference Implementation Architecture for Deploying a Highly
... provisioned with no direct form of access at all. The sole mechanism of access to many of these systems for their end users is with some form of networking technology. Realizing these issues, it quickly becomes apparent that networking can become a weak point in application availability. But what do ...
... provisioned with no direct form of access at all. The sole mechanism of access to many of these systems for their end users is with some form of networking technology. Realizing these issues, it quickly becomes apparent that networking can become a weak point in application availability. But what do ...
SCTP - UMBC
... SCTP – Overview “SCTP is a reliable transport protocol operating on top of a connectionless packet network such as IP. …” – RFC 2960 Has built-in support for multi-homed hosts Is message-based – conserves the message boundaries. Classifies messages as: sequenced delivery of user messages ...
... SCTP – Overview “SCTP is a reliable transport protocol operating on top of a connectionless packet network such as IP. …” – RFC 2960 Has built-in support for multi-homed hosts Is message-based – conserves the message boundaries. Classifies messages as: sequenced delivery of user messages ...
cis185-ROUTE-lecture2-EIGRP-Part2
... PVCs to the local DLCI number. Split horizon is disabled by default on Frame Relay physical interfaces. Routes from Router R2 can be sent to Router R3, and vise-versa. Note: Inverse ARP does not provide dynamic mapping for the communication between routers R2 to R3 because they are not connect ...
... PVCs to the local DLCI number. Split horizon is disabled by default on Frame Relay physical interfaces. Routes from Router R2 can be sent to Router R3, and vise-versa. Note: Inverse ARP does not provide dynamic mapping for the communication between routers R2 to R3 because they are not connect ...
Link Layer
... Goal: allow host to dynamically obtain its IP address from network server when joining network support for mobile users joining network host holds address only while connected and “on” (allowing address reuse) renew address already in use DHCP overview: 1. host broadcasts “DHCP discover” m ...
... Goal: allow host to dynamically obtain its IP address from network server when joining network support for mobile users joining network host holds address only while connected and “on” (allowing address reuse) renew address already in use DHCP overview: 1. host broadcasts “DHCP discover” m ...
cisco 2-11
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
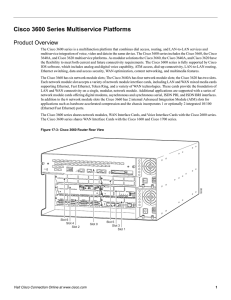
Cisco 3600 Series Multiservice Platforms
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
Chapter 6: The Transport Layer
... line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash. ...
... line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash. ...
Apuntes seguridad Redes Avanzadas 0708
... provide multicast connectivity to a source, using UDP-based encapsulation to overcome the lack of multicast connectivity. AMT builds dynamic tunnels from hosts and can support any host application. Although the AMT protocol is defined for both SSM and ASM traffic, it is primarily intended for use in ...
... provide multicast connectivity to a source, using UDP-based encapsulation to overcome the lack of multicast connectivity. AMT builds dynamic tunnels from hosts and can support any host application. Although the AMT protocol is defined for both SSM and ASM traffic, it is primarily intended for use in ...
Chapter 1 - Introduction
... – the forwarding function must find an entry in the forwarding table that specifies a next hop for D – The software examines each entry in the table by using the mask in the entry to extract a prefix of address D – It compares the resulting prefix to the Destination field of the entry • If the two a ...
... – the forwarding function must find an entry in the forwarding table that specifies a next hop for D – The software examines each entry in the table by using the mask in the entry to extract a prefix of address D – It compares the resulting prefix to the Destination field of the entry • If the two a ...
Chapter 1 - Introduction
... – the forwarding function must find an entry in the forwarding table that specifies a next hop for D – The software examines each entry in the table by using the mask in the entry to extract a prefix of address D – It compares the resulting prefix to the Destination field of the entry • If the two a ...
... – the forwarding function must find an entry in the forwarding table that specifies a next hop for D – The software examines each entry in the table by using the mask in the entry to extract a prefix of address D – It compares the resulting prefix to the Destination field of the entry • If the two a ...
Slide - ESnet
... OSCARS generated and managed virtual circuits at FNAL – one of the US LHC Tier 1 data centers. This circuit map (minus the yellow callouts that explain the diagram) is automatically generated by an OSCARS tool and assists the connected sites with keeping track of what circuits exist and where they ...
... OSCARS generated and managed virtual circuits at FNAL – one of the US LHC Tier 1 data centers. This circuit map (minus the yellow callouts that explain the diagram) is automatically generated by an OSCARS tool and assists the connected sites with keeping track of what circuits exist and where they ...
Cisco PIX 515E Security Appliance
... next-generation, three-tier management solution that includes the following features: • Comprehensive configuration and software image management • Device hierarchy with “Smart Rules”-based configuration inheritance • Customizable administrative roles and access privileges • Comprehensive enterprise ...
... next-generation, three-tier management solution that includes the following features: • Comprehensive configuration and software image management • Device hierarchy with “Smart Rules”-based configuration inheritance • Customizable administrative roles and access privileges • Comprehensive enterprise ...