MPLS Bandwidth Assured Layer 2 Services
... Single-cell relay & packed-cell relay – VC & VP mode Ethernet over MPLS – Port mode Frame Relay to ATM/Ethernet/PPP/HDLC interworking Ethernet to ATM interworking Traffic engineering & fast reroute for Layer 2 Fast reroute support for AToM TE tunnel selection for AToM VCs ...
... Single-cell relay & packed-cell relay – VC & VP mode Ethernet over MPLS – Port mode Frame Relay to ATM/Ethernet/PPP/HDLC interworking Ethernet to ATM interworking Traffic engineering & fast reroute for Layer 2 Fast reroute support for AToM TE tunnel selection for AToM VCs ...
Computer Networking : Principles, Protocols and Practice Release
... From a Computer Science viewpoint, the physical transmission of information through a wire is often considered as a black box that allows to transmit bits. This black box is often referred to as the physical layer service and is represented by using the DATA.request and DATA.indication primitives in ...
... From a Computer Science viewpoint, the physical transmission of information through a wire is often considered as a black box that allows to transmit bits. This black box is often referred to as the physical layer service and is represented by using the DATA.request and DATA.indication primitives in ...
Understanding Simple Network Management Protocol
... SNMP version 3 provides security features such as authentication (verifying that the request comes from a genuine source), privacy (encryption of data), authorization (verifying that the user allows the requested operation), and access control (verifying that the user has access to the objects reque ...
... SNMP version 3 provides security features such as authentication (verifying that the request comes from a genuine source), privacy (encryption of data), authorization (verifying that the user allows the requested operation), and access control (verifying that the user has access to the objects reque ...
Description
... The authentication feature is used in subscriber identification, authentication, and synchronization of the encryption key. This feature checks the validity of a subscriber's service requests to ensure that only legal subscribers can use network services. The authentication procedure is performed in ...
... The authentication feature is used in subscriber identification, authentication, and synchronization of the encryption key. This feature checks the validity of a subscriber's service requests to ensure that only legal subscribers can use network services. The authentication procedure is performed in ...
Star-crossed cube: an alternative to star graph
... graph is a permutation graph whose node degree is (n – 1) with n! nodes. The star graph, being regular and vertex (edge) symmetric, is asymptotically superior to the HC. In spite of these improved features, the n-star has a major disadvantage, which is that it grows to its next highest level by a ve ...
... graph is a permutation graph whose node degree is (n – 1) with n! nodes. The star graph, being regular and vertex (edge) symmetric, is asymptotically superior to the HC. In spite of these improved features, the n-star has a major disadvantage, which is that it grows to its next highest level by a ve ...
OS6850 AOS 6.4.3 R01 Release Notes
... The software versions listed below are the minimum required, except where otherwise noted. Switches running the minimum versions, as listed below, do not require any Uboot, Miniboot, or FPGA uprades when upgrading to AOS 6.4.3.R01. Switches not running the minimum version required should upgrade to ...
... The software versions listed below are the minimum required, except where otherwise noted. Switches running the minimum versions, as listed below, do not require any Uboot, Miniboot, or FPGA uprades when upgrading to AOS 6.4.3.R01. Switches not running the minimum version required should upgrade to ...
cit 852: data communication and network
... Assignment questions for the units in this course are contained in the Assignment File. You should be able to complete your assignments from the information and materials contained in your set textbooks, reading and study units. However, you may wish to use other references to broaden your viewpoint ...
... Assignment questions for the units in this course are contained in the Assignment File. You should be able to complete your assignments from the information and materials contained in your set textbooks, reading and study units. However, you may wish to use other references to broaden your viewpoint ...
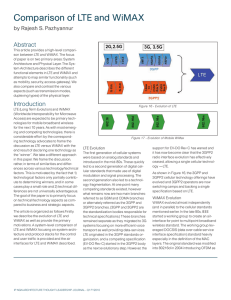
Comparison of LTE and WiMAX
... elements. The control and user plane traffic both are carried by the ASNGW. The protocols used between the gateways and the BS’ differ between LTE and WiMAX as well. LTE uses GTP (GPRS Tunneling Protocol) for the S1u and S1-AP/SCTP for S1c interface, while WiMAX uses GRE/UDP as the tunneling protoco ...
... elements. The control and user plane traffic both are carried by the ASNGW. The protocols used between the gateways and the BS’ differ between LTE and WiMAX as well. LTE uses GTP (GPRS Tunneling Protocol) for the S1u and S1-AP/SCTP for S1c interface, while WiMAX uses GRE/UDP as the tunneling protoco ...
Application of Mininet
... configured as a switch not a router. This is why it is called transparent bridge. Question 5-b If PC2 is configured as a IP router, we would see one more entry in the traceroute output indicating PC2. We changed the IP address of PC3 to 10.0.2.12/24. The previous ping command failed in this case. Be ...
... configured as a switch not a router. This is why it is called transparent bridge. Question 5-b If PC2 is configured as a IP router, we would see one more entry in the traceroute output indicating PC2. We changed the IP address of PC3 to 10.0.2.12/24. The previous ping command failed in this case. Be ...
Windows 7 Firewall - IT352 : Network Security
... Domain - the connection is authenticated to a domain controller for the domain of which it is a member. By default, all other networks are initially classified as public networks. User can identify the network as either public or private. ...
... Domain - the connection is authenticated to a domain controller for the domain of which it is a member. By default, all other networks are initially classified as public networks. User can identify the network as either public or private. ...
ip-shiv2004-routing-I
... consistent while the rest may be inconsistent. Large networks => inconsistency is a scalability issue. Consistency can be achieved in two ways: Fully distributed approach: a consistency criterion or invariant across the states of adjacent nodes Signaled approach: the signaling protocol sets up ...
... consistent while the rest may be inconsistent. Large networks => inconsistency is a scalability issue. Consistency can be achieved in two ways: Fully distributed approach: a consistency criterion or invariant across the states of adjacent nodes Signaled approach: the signaling protocol sets up ...
Basic Router Configuration
... The wireless LAN interface on the Cisco 1941W router enables connection to the router through interface wlan-ap0. For more information about configuring a wireless connection, see the “Configuring the Wireless Device” section on page 207. ...
... The wireless LAN interface on the Cisco 1941W router enables connection to the router through interface wlan-ap0. For more information about configuring a wireless connection, see the “Configuring the Wireless Device” section on page 207. ...
Understanding KaZaA
... process, a KaZaA-Lite ON first sends its query to the SN to which it is connected. We have learned from our measurement work that after receiving all the replies from its parent SN, the ON often disconnects and connects with a new SN, and resends the query to the new SN. During a specific search, th ...
... process, a KaZaA-Lite ON first sends its query to the SN to which it is connected. We have learned from our measurement work that after receiving all the replies from its parent SN, the ON often disconnects and connects with a new SN, and resends the query to the new SN. During a specific search, th ...
International Technical Support Organization High
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
Chapter 5 on Link/MAC Layer - Department of Computer and
... collision detection: easy in wired LANs: measure signal strengths, compare transmitted, received signals difficult in wireless LANs: received signal strength overwhelmed by local transmission strength (use CSMA/CA: we’ll get back to that in Ch 6) human analogy: the polite conversationalist ...
... collision detection: easy in wired LANs: measure signal strengths, compare transmitted, received signals difficult in wireless LANs: received signal strength overwhelmed by local transmission strength (use CSMA/CA: we’ll get back to that in Ch 6) human analogy: the polite conversationalist ...
ATM End User
... Remark: Signaling between the end-system and the ATM switch usually takes place over VPI=0 and VCI=5, although this is not always the case. If we implement a feature such as SVC tunneling, the signaling channel will often be over a VPI =/ 0. Also, some proprietary UNI and NNI protocols use VCI =/5 f ...
... Remark: Signaling between the end-system and the ATM switch usually takes place over VPI=0 and VCI=5, although this is not always the case. If we implement a feature such as SVC tunneling, the signaling channel will often be over a VPI =/ 0. Also, some proprietary UNI and NNI protocols use VCI =/5 f ...
Slide 1
... What are the only addresses routers know about before there is any routing knowledge? Network addresses of its own interfaces Network addresses of its neighbors. ...
... What are the only addresses routers know about before there is any routing knowledge? Network addresses of its own interfaces Network addresses of its neighbors. ...
datagram network
... Obtaining IP Addresses • Typically an ISP gets a block of IP addresses, and assigns them to customers – E.g. the ISP might get 200.23.16.0/20, which it breaks down into smaller subnets for each customer – 200.23.16.0/23 for one, 200.23.18.0/23 for another, etc. – That way, routing knows anything st ...
... Obtaining IP Addresses • Typically an ISP gets a block of IP addresses, and assigns them to customers – E.g. the ISP might get 200.23.16.0/20, which it breaks down into smaller subnets for each customer – 200.23.16.0/23 for one, 200.23.18.0/23 for another, etc. – That way, routing knows anything st ...
ZigBee: Home Wireless Control Made Simple
... • ZigBee Alliance: Consortium of >150 companies > Freescale is one of 8 World-Class Promoter Companies with a total market cap of more than US $150B > Over 140 Participant and adopter companies including over a dozen OEMs with a market cap of US $200B ...
... • ZigBee Alliance: Consortium of >150 companies > Freescale is one of 8 World-Class Promoter Companies with a total market cap of more than US $150B > Over 140 Participant and adopter companies including over a dozen OEMs with a market cap of US $200B ...
Access your control systems via the Internet
... management and monitoring of a range of Clipsal MinderPRO and CentralAXS systems. This enables remote monitoring of Alarm States as well as providing the ability of being able to remotely arm the system. ...
... management and monitoring of a range of Clipsal MinderPRO and CentralAXS systems. This enables remote monitoring of Alarm States as well as providing the ability of being able to remotely arm the system. ...
module10b
... • 2-way state – neighbor has received Hello message and replied with a Hello message of his own • Exstart state – beginning of the LSDB exchange between both routers. • Exchange state – DBD (Database Descriptor) packets are exchanged. DBDs contain LSAs headers. Routers see what LSAs they need. • Loa ...
... • 2-way state – neighbor has received Hello message and replied with a Hello message of his own • Exstart state – beginning of the LSDB exchange between both routers. • Exchange state – DBD (Database Descriptor) packets are exchanged. DBDs contain LSAs headers. Routers see what LSAs they need. • Loa ...
Specification - Wireless Section 26_Word
... consumption, Occupancy status in a colorized gradient (“weather” map) type of ...
... consumption, Occupancy status in a colorized gradient (“weather” map) type of ...
Chapter 1
... • Used to connect routers to external networks, usually over a larger geographical distance. • The Layer 2 encapsulation can be different types (PPP, Frame Relay, HDLC (High-Level Data Link Control) ). • Similar to LAN interfaces, each WAN interface has its own IP address and subnet mask, making it ...
... • Used to connect routers to external networks, usually over a larger geographical distance. • The Layer 2 encapsulation can be different types (PPP, Frame Relay, HDLC (High-Level Data Link Control) ). • Similar to LAN interfaces, each WAN interface has its own IP address and subnet mask, making it ...