Firewall and Network Address Translation Feature
... ease of use. Unlike a traditional firewall, they will keep pace with rapid changes in Internet-based applications, enabling enterprises to see the benefits of web-based technology without costly security issues. The AR-Series firewalls also supports Network Address Translation (NAT), allowing a sing ...
... ease of use. Unlike a traditional firewall, they will keep pace with rapid changes in Internet-based applications, enabling enterprises to see the benefits of web-based technology without costly security issues. The AR-Series firewalls also supports Network Address Translation (NAT), allowing a sing ...
(IP) routers
... Resource-portable IP Router ? • Network virtualization, such as ETSI network functions virtualization (NFV) , is a promising technology for next generation networks. • resource portability of Internet protocol (IP) routers (e.g., routing state, traffic state, configurations) is expected to result i ...
... Resource-portable IP Router ? • Network virtualization, such as ETSI network functions virtualization (NFV) , is a promising technology for next generation networks. • resource portability of Internet protocol (IP) routers (e.g., routing state, traffic state, configurations) is expected to result i ...
WAP - ICMP - Extra Reading File
... proper configuration of IP address and subnet mask. A default gateway must also be configured if datagrams are to travel outside of the local network. • A router also must have the TCP/IP protocol properly configured on its interfaces, and it must use an appropriate routing protocol. If these co ...
... proper configuration of IP address and subnet mask. A default gateway must also be configured if datagrams are to travel outside of the local network. • A router also must have the TCP/IP protocol properly configured on its interfaces, and it must use an appropriate routing protocol. If these co ...
Advanced Routing Mechanisms in ASON/GMPLS Networks by Fernando Agraz Bujan
... PLI Node OLSA diagram (left) and Node PLI top level TLV (right) . . . PLI Link OLSA diagram (left) and Link PLI top level TLV (right) . . . . PLI Node OLSA diagram (left) and Node Identifier sub-TLV (right) . . . Link Identifier, Local Interface and Remote Interface sub-TLVs . . . . . . Component, W ...
... PLI Node OLSA diagram (left) and Node PLI top level TLV (right) . . . PLI Link OLSA diagram (left) and Link PLI top level TLV (right) . . . . PLI Node OLSA diagram (left) and Node Identifier sub-TLV (right) . . . Link Identifier, Local Interface and Remote Interface sub-TLVs . . . . . . Component, W ...
Device Management System
... under an executed MSA (Master Service Agreement) with Company, billing will occur when the first data transmission occurs, such as SMS, MicroBurst, or an IP session. All transmissions will be charged. This typically applies to devices that are under test and development, but have not yet been commer ...
... under an executed MSA (Master Service Agreement) with Company, billing will occur when the first data transmission occurs, such as SMS, MicroBurst, or an IP session. All transmissions will be charged. This typically applies to devices that are under test and development, but have not yet been commer ...
WAP - ICMP - Extra Reading File
... proper configuration of IP address and subnet mask. A default gateway must also be configured if datagrams are to travel outside of the local network. • A router also must have the TCP/IP protocol properly configured on its interfaces, and it must use an appropriate routing protocol. If these co ...
... proper configuration of IP address and subnet mask. A default gateway must also be configured if datagrams are to travel outside of the local network. • A router also must have the TCP/IP protocol properly configured on its interfaces, and it must use an appropriate routing protocol. If these co ...
Computer Networking : Principles, Protocols and Practice
... as xorp or quagga . Furthermore, the documents that define almost all of the Internet protocols have been developed within the Internet Engineering Task Force (IETF) using an open process. The IETF publishes its protocol specifications in the publicly available RFC and new proposals are described in ...
... as xorp or quagga . Furthermore, the documents that define almost all of the Internet protocols have been developed within the Internet Engineering Task Force (IETF) using an open process. The IETF publishes its protocol specifications in the publicly available RFC and new proposals are described in ...
SMS Messaging in SS7 Networks: Optimizing Revenue with Modular
... providers are working overtime to develop innovative ways to increase usage and revenue. Because Europe is a mature market segment [Forrester] for SMS services and people feel comfortable using them, premium or high-value services such as gaming, information alerts, and advertising are expected to f ...
... providers are working overtime to develop innovative ways to increase usage and revenue. Because Europe is a mature market segment [Forrester] for SMS services and people feel comfortable using them, premium or high-value services such as gaming, information alerts, and advertising are expected to f ...
Worksheet 1 (Router Programming)
... The router will not be able to connect to other routers unless it runs a routing protocols which is the same as the other routers. This allows the routers to determine the best path to a remote device. In this case the RIP protocol is set-up with the router rip command, and then each of the networks ...
... The router will not be able to connect to other routers unless it runs a routing protocols which is the same as the other routers. This allows the routers to determine the best path to a remote device. In this case the RIP protocol is set-up with the router rip command, and then each of the networks ...
SwitchBlade® x908 [Rev ZJ]
... The increasing convergence of services and applications in the enterprise has led to increasing demand for highly available networks with minimal downtime. High bandwidth is also required for the multiple applications simultaneously using the network. Real-time applications like surveillance, video ...
... The increasing convergence of services and applications in the enterprise has led to increasing demand for highly available networks with minimal downtime. High bandwidth is also required for the multiple applications simultaneously using the network. Real-time applications like surveillance, video ...
Table of Contents - HP Enterprise Group
... 3.7.3 Introduction to IPv6 DNS....................................................................................... 3-41 3.7.4 Ping IPv6 and Tracert IPv6 ................................................................................... 3-42 3.7.5 IPv6 Telnet ..................................... ...
... 3.7.3 Introduction to IPv6 DNS....................................................................................... 3-41 3.7.4 Ping IPv6 and Tracert IPv6 ................................................................................... 3-42 3.7.5 IPv6 Telnet ..................................... ...
Abstract obvious solutions, avoiding parallel processing of packets of
... trends indicate that network link speed approximately doubles every nine months [3, 4]. Thus, the network link speeds increase at a faster rate than the computing speed. The Internet itself is growing in size, resulting in the increase of routing tables sizes in backbone routers [5]. Consequently, t ...
... trends indicate that network link speed approximately doubles every nine months [3, 4]. Thus, the network link speeds increase at a faster rate than the computing speed. The Internet itself is growing in size, resulting in the increase of routing tables sizes in backbone routers [5]. Consequently, t ...
scratch
... Textbook describes Internet Port Addresses in terms of OSI’s “TSAP” concept • Your Instructor believes that this is confusing for those not familiar with OSI, even though these OSI concepts are helpful for a formal orientation. • This instructor-inserted slide seeks to summarize pgs 509-512 and 554 ...
... Textbook describes Internet Port Addresses in terms of OSI’s “TSAP” concept • Your Instructor believes that this is confusing for those not familiar with OSI, even though these OSI concepts are helpful for a formal orientation. • This instructor-inserted slide seeks to summarize pgs 509-512 and 554 ...
SERVICE DESCRIPTION: Optus Evolve Service
... Optus will include on the Optus invoice in Australian dollars, the third party interconnecting carrier 's charges together with an administration fee, which will be charged to you at the exchange rate determined by Optus at the date of conversion; ...
... Optus will include on the Optus invoice in Australian dollars, the third party interconnecting carrier 's charges together with an administration fee, which will be charged to you at the exchange rate determined by Optus at the date of conversion; ...
McAfee.com Virus Scan Online
... A computer running a 32-bit version of Windows. This includes all versions of Windows 95, 98, 98SE and 2000. It also includes Windows ME and NT 4.0. Windows 3.11 with Win32s cannot support Visual Trace. Windows 95 users need to have installed the Winsock 2 update. If you receive an error message whe ...
... A computer running a 32-bit version of Windows. This includes all versions of Windows 95, 98, 98SE and 2000. It also includes Windows ME and NT 4.0. Windows 3.11 with Win32s cannot support Visual Trace. Windows 95 users need to have installed the Winsock 2 update. If you receive an error message whe ...
RS-BA1 Instruction Manual
... Depending on your radio, a few functions or modes cannot be used, or you will need to update the radio’s firmware to operate a CW keyer, using the RS-BA1. Depending on the PC performance (OS, environment, etc.), the USB audio may be interrupted, or a control by the PC software may get delayed. If th ...
... Depending on your radio, a few functions or modes cannot be used, or you will need to update the radio’s firmware to operate a CW keyer, using the RS-BA1. Depending on the PC performance (OS, environment, etc.), the USB audio may be interrupted, or a control by the PC software may get delayed. If th ...
M051055
... DUAL enables EIGRP routers to determine whether a path advertised by a neighbor is looped or loop-free, and allows a router running EIGRP to find alternate paths without waiting on updates from other routers. Therefore, EIGRP minimizes both the routing instability triggered by topology changes and t ...
... DUAL enables EIGRP routers to determine whether a path advertised by a neighbor is looped or loop-free, and allows a router running EIGRP to find alternate paths without waiting on updates from other routers. Therefore, EIGRP minimizes both the routing instability triggered by topology changes and t ...
3rd Edition, Chapter 5 - Department of Computer and Information
... collision detection: easy in wired LANs: measure signal strengths, compare transmitted, received signals difficult in wireless LANs: received signal strength overwhelmed by local transmission strength (use CSMA/CA: we’ll get back to that in Ch 6) human analogy: the polite conversationalist ...
... collision detection: easy in wired LANs: measure signal strengths, compare transmitted, received signals difficult in wireless LANs: received signal strength overwhelmed by local transmission strength (use CSMA/CA: we’ll get back to that in Ch 6) human analogy: the polite conversationalist ...
Cisco Nexus 1000V for Microsoft Hyper-V
... Vastly simplified host networking configuration Faster, repeatable and consistent host provisioning Clear segregation of ownership, accelerated problem resolution ...
... Vastly simplified host networking configuration Faster, repeatable and consistent host provisioning Clear segregation of ownership, accelerated problem resolution ...
Study on a Fast OSPF Route Reconstruction Method Under Network
... Of course, the Hello Interval is one of the OSPF parameters and there is a simple way for Hello Interval to be set to under 10 sec to reduce Router Dead Interval. However, this is not feasible for commercial ISPs. This method was analyzed by paper [3] by measuring ISPs topologies and it was reported ...
... Of course, the Hello Interval is one of the OSPF parameters and there is a simple way for Hello Interval to be set to under 10 sec to reduce Router Dead Interval. However, this is not feasible for commercial ISPs. This method was analyzed by paper [3] by measuring ISPs topologies and it was reported ...
Simple Network Management Protocol (SNMP) Primer
... Read-Write: A Read-Write setting allows the value of the MIB object to be accessed as well as modified. A client can issue the setRequest command as well as the getRequest and getNextRequest. If one tries to access an SNMP Agent with the wrong SNMP Community String name, the Agent refuses to provide ...
... Read-Write: A Read-Write setting allows the value of the MIB object to be accessed as well as modified. A client can issue the setRequest command as well as the getRequest and getNextRequest. If one tries to access an SNMP Agent with the wrong SNMP Community String name, the Agent refuses to provide ...
DYNAMIC MANAGEMENT AND RESTORATION OF VIRTUAL PATHS IN BROADBAND NETWORKS
... Network management is a wide field including topics as diverse as fault restoration, network utilisation accounting, network elements configuration, security, performance monitoring, etc. This thesis focuses on resource management of broadband networks that have the mechanisms for performing resourc ...
... Network management is a wide field including topics as diverse as fault restoration, network utilisation accounting, network elements configuration, security, performance monitoring, etc. This thesis focuses on resource management of broadband networks that have the mechanisms for performing resourc ...
Dude, where’s that IP? Circumventing measurement-based IP geolocation
... providers [13] however, have identified and blocked access from known proxies; but this does not prevent all clients from circumventing geographic controls. Similarly, cloud providers may attempt to break location restrictions in their SLAs to move customer VMs to cheaper locations. Governments that ...
... providers [13] however, have identified and blocked access from known proxies; but this does not prevent all clients from circumventing geographic controls. Similarly, cloud providers may attempt to break location restrictions in their SLAs to move customer VMs to cheaper locations. Governments that ...
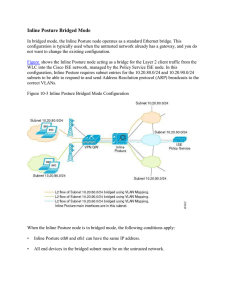
15360608-Inline Posture Bridged Mode
... Consider the following when configuring filters: • As typically implemented, Inline Posture enforces authentication requirements on endpoints that attempt to access the network. Device and subnet filters are used to validate or deny WLC and VPN devices. • For certain devices, you may want to bypass ...
... Consider the following when configuring filters: • As typically implemented, Inline Posture enforces authentication requirements on endpoints that attempt to access the network. Device and subnet filters are used to validate or deny WLC and VPN devices. • For certain devices, you may want to bypass ...
Design and Configure a Network Using Single-Area OSPF
... Design and Configure a Network Using Single-Area OSPF LSPs do not need to be sent periodically. An LSP only needs to be sent: • During initial startup of the router or of the routing protocol process • Whenever there is a change in the topology, including a link going down or coming up, or a neighb ...
... Design and Configure a Network Using Single-Area OSPF LSPs do not need to be sent periodically. An LSP only needs to be sent: • During initial startup of the router or of the routing protocol process • Whenever there is a change in the topology, including a link going down or coming up, or a neighb ...






![SwitchBlade® x908 [Rev ZJ]](http://s1.studyres.com/store/data/008053519_1-53b0e3770fa5647be537fdbf48703248-300x300.png)