IPv6 at Monash University
... – Has severely restricted IPv6 for small campuses that use 3750's as their routers – I hope Cisco will put IPv6 in IP SERVICES ...
... – Has severely restricted IPv6 for small campuses that use 3750's as their routers – I hope Cisco will put IPv6 in IP SERVICES ...
HP TCP/IP Services for OpenVMS Management Command Reference
... UNIX® is a registered trademark of The Open Group. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as co ...
... UNIX® is a registered trademark of The Open Group. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as co ...
Introduction to IPv6
... IPv6 can offer new opportunities as it eliminates NAT: Example: AJAX applications, Multimedia. You would need to give IPv6 Support to Software that runs on top of IP or that handle IP addresses. Example: ODBC, JDBC drivers upgrade, Database tables, log. ...
... IPv6 can offer new opportunities as it eliminates NAT: Example: AJAX applications, Multimedia. You would need to give IPv6 Support to Software that runs on top of IP or that handle IP addresses. Example: ODBC, JDBC drivers upgrade, Database tables, log. ...
Serial Server Installation Guide
... manual as MSS_xxxxxx. The xxxxxx string represents the last six digits of the MSS Ethernet address. Be sure to note the Ethernet address before conÞguring the unit. ...
... manual as MSS_xxxxxx. The xxxxxx string represents the last six digits of the MSS Ethernet address. Be sure to note the Ethernet address before conÞguring the unit. ...
User Guide
... Defining the Billing Options {Billing Options} ............................................... Setting Up the Information and Control Console {ICC Setup} ....................... ...
... Defining the Billing Options {Billing Options} ............................................... Setting Up the Information and Control Console {ICC Setup} ....................... ...
ESnet - Indico
... provide multiple, independent connections for ESnet sites to the ESnet core network ...
... provide multiple, independent connections for ESnet sites to the ESnet core network ...
The Internet and Its Uses
... A switch builds its MAC address table by recording the MAC addresses of the nodes connected to each of its ports. Once a MAC address for a specific node on a specific port is recorded in the address table, the switch then knows to send traffic destined for that specific node out the port. When an ...
... A switch builds its MAC address table by recording the MAC addresses of the nodes connected to each of its ports. Once a MAC address for a specific node on a specific port is recorded in the address table, the switch then knows to send traffic destined for that specific node out the port. When an ...
Optical Interconnection Networks
... – one optically switched (Banyan topology to reduce power loss) – one electronically switched – as proposed, the two networks have identical topology [Chamberlain97] ...
... – one optically switched (Banyan topology to reduce power loss) – one electronically switched – as proposed, the two networks have identical topology [Chamberlain97] ...
third edition
... Our intent is that the book should serve as the text for a comprehensive networking class, at either the graduate or upper-division undergraduate level. We also believe that the book’s focus on core concepts should be appealing to industry professionals who are retraining for network-related assignm ...
... Our intent is that the book should serve as the text for a comprehensive networking class, at either the graduate or upper-division undergraduate level. We also believe that the book’s focus on core concepts should be appealing to industry professionals who are retraining for network-related assignm ...
A. IMS/Internet interworking scenario.
... integrity, integrity mechanisms always provide some type of proof of data origin. Knowing that a message has not been modified without knowing who initially created the message would be useless. Confidentiality mechanisms keep unauthorized parties from getting access to the contents of a message. Co ...
... integrity, integrity mechanisms always provide some type of proof of data origin. Knowing that a message has not been modified without knowing who initially created the message would be useless. Confidentiality mechanisms keep unauthorized parties from getting access to the contents of a message. Co ...
Wireless Datagram Protocol
... You may use this document or any part of the document for internal or educational purposes only, provided you do not modify, edit or take out of context the information in this document in any manner. You may not use this document in any other manner without the prior written permission of the WAP F ...
... You may use this document or any part of the document for internal or educational purposes only, provided you do not modify, edit or take out of context the information in this document in any manner. You may not use this document in any other manner without the prior written permission of the WAP F ...
Slide 1
... 2) For States with Boundary Intermediate System (BIS), deployment of IPS based AMHS and/or inter State ATN circuits may be considered depending on the impact on the regional ATN network connectivity and redundancy, and the agreement with the adjacent States; 3) For AFS interface to adjacent regions, ...
... 2) For States with Boundary Intermediate System (BIS), deployment of IPS based AMHS and/or inter State ATN circuits may be considered depending on the impact on the regional ATN network connectivity and redundancy, and the agreement with the adjacent States; 3) For AFS interface to adjacent regions, ...
IPv6 Deployment Status in KT/Korea
... strategy council driven by MIC • No Telco’s are now ready to deploy IPv6 as they see IPv6 as business, not as infrastructure upgrade • They’re still research-oriented even though they have IPv6 deployment plans – KT, SKT, etc KT Future Technology Laboratory ...
... strategy council driven by MIC • No Telco’s are now ready to deploy IPv6 as they see IPv6 as business, not as infrastructure upgrade • They’re still research-oriented even though they have IPv6 deployment plans – KT, SKT, etc KT Future Technology Laboratory ...
PowerPoint 프레젠테이션
... a host connected to a cellular IP network must be able to send IP datagram to hosts outside the cellular IP network datagrams arriving to a cellular IP network should be delivered with high probability to the destination host datagram delivery in a cellular IP network should be take placed without l ...
... a host connected to a cellular IP network must be able to send IP datagram to hosts outside the cellular IP network datagrams arriving to a cellular IP network should be delivered with high probability to the destination host datagram delivery in a cellular IP network should be take placed without l ...
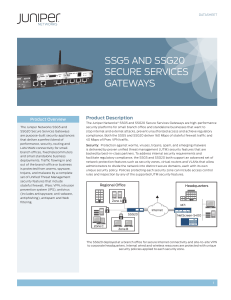
SSG5 and SSG20 Secure Services Gateways
... compliance. Both the SSG5 and SSG20 deliver 160 Mbps of stateful firewall traffic and 40 Mbps of IPsec VPN traffic. Security: Protection against worms, viruses, trojans, spam, and emerging malware is delivered by proven unified threat management (UTM) security features that are backed by best-in-cla ...
... compliance. Both the SSG5 and SSG20 deliver 160 Mbps of stateful firewall traffic and 40 Mbps of IPsec VPN traffic. Security: Protection against worms, viruses, trojans, spam, and emerging malware is delivered by proven unified threat management (UTM) security features that are backed by best-in-cla ...
Effective communication - Docbox
... Where Smart Grids meet M2M Smart grids needs a reliable and gridwide monitoring infrastructure “Most utilities don't know that users have lost power until customers pick up the phone and call them” WASA: Monitoring and display of power-system components and performance across interconnections ...
... Where Smart Grids meet M2M Smart grids needs a reliable and gridwide monitoring infrastructure “Most utilities don't know that users have lost power until customers pick up the phone and call them” WASA: Monitoring and display of power-system components and performance across interconnections ...
VoIPTutorial FCC 2011-05 - Computer Science, Columbia
... Intermediary ex: Net Address Translator (NAT), Firewalls, App Level Gateways (ALG), SBC,... (the good, the bad and the ugly) Saltzer, J., Reed, D., and Clark, D.D. End-to-End Arguments in System Design, 1981 D. Isenberg: “Rise of the Stupid Network”, 1997 RFC 1958, B. Carpenter: “Architectural Princ ...
... Intermediary ex: Net Address Translator (NAT), Firewalls, App Level Gateways (ALG), SBC,... (the good, the bad and the ugly) Saltzer, J., Reed, D., and Clark, D.D. End-to-End Arguments in System Design, 1981 D. Isenberg: “Rise of the Stupid Network”, 1997 RFC 1958, B. Carpenter: “Architectural Princ ...
Computer Networking : Principles, Protocols and Practice
... as xorp or quagga . Furthermore, the documents that define almost all of the Internet protocols have been developed within the Internet Engineering Task Force (IETF) using an open process. The IETF publishes its protocol specifications in the publicly available RFC and new proposals are described in ...
... as xorp or quagga . Furthermore, the documents that define almost all of the Internet protocols have been developed within the Internet Engineering Task Force (IETF) using an open process. The IETF publishes its protocol specifications in the publicly available RFC and new proposals are described in ...
Configuring VoIP for SonicOS Standard
... designed to prevent malicious traffic from reaching protected VoIP phones and servers. Signature granularity allows SonicWALL IPS to detect and prevent attacks based on a global, attack group, or per-signature basis to provide maximum flexibility and control false positives. ...
... designed to prevent malicious traffic from reaching protected VoIP phones and servers. Signature granularity allows SonicWALL IPS to detect and prevent attacks based on a global, attack group, or per-signature basis to provide maximum flexibility and control false positives. ...
23002-a20 - Network architecture
... This Specification is provided for future development work within 3GPP only. The Organisational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organisational Partners' Publications Of ...
... This Specification is provided for future development work within 3GPP only. The Organisational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organisational Partners' Publications Of ...
2. Principles governing the use of TCP/IP on the GTS
... This Attachment does not cover fundamentals of TCP/IP but focuses on those aspects that are essential for successful application on the GTS. Such aspects include appropriate use of the GTS compared with the Internet, co-existence of the GTS and the Internet, IP and X.25 and Autonomous System address ...
... This Attachment does not cover fundamentals of TCP/IP but focuses on those aspects that are essential for successful application on the GTS. Such aspects include appropriate use of the GTS compared with the Internet, co-existence of the GTS and the Internet, IP and X.25 and Autonomous System address ...
Layer 2 WAN Technology Design Guide - August 2014
... Service providers implement these Ethernet services by using a variety of methods. MPLS networks support both Ethernet over MPLS (EoMPLS) and Virtual Private LAN Service (VPLS). You can use other network technologies, such as Ethernet switches in various topologies, to provide Ethernet Layer 2 WAN ...
... Service providers implement these Ethernet services by using a variety of methods. MPLS networks support both Ethernet over MPLS (EoMPLS) and Virtual Private LAN Service (VPLS). You can use other network technologies, such as Ethernet switches in various topologies, to provide Ethernet Layer 2 WAN ...
ITE PC v4.0 Chapter 1
... Different types of network media have different features and benefits. Ethernet is the most common local area network (LAN) technology. Ethernet ports are found on end user devices, switch devices, and other networking devices. Cisco IOS switches have physical ports for devices to connect to ...
... Different types of network media have different features and benefits. Ethernet is the most common local area network (LAN) technology. Ethernet ports are found on end user devices, switch devices, and other networking devices. Cisco IOS switches have physical ports for devices to connect to ...
PDF - This Chapter (405.0 KB)
... The hostname is used in CLI prompts and default configuration filenames. If you do not configure the router hostname, the router uses the factory-assigned default hostname “Router.” Do not expect capitalization and lowercasing to be preserved in the hostname. Uppercase and lowercase characters are t ...
... The hostname is used in CLI prompts and default configuration filenames. If you do not configure the router hostname, the router uses the factory-assigned default hostname “Router.” Do not expect capitalization and lowercasing to be preserved in the hostname. Uppercase and lowercase characters are t ...
IP Datagram - La Salle University
... Different physical networks have different MTUs. The MTU may also be set by the network administrator. If the source computer transmits packets that are too large for some network encountered on the way to its destination, then a router will break the packet into smaller packets (fragmenting). Ideal ...
... Different physical networks have different MTUs. The MTU may also be set by the network administrator. If the source computer transmits packets that are too large for some network encountered on the way to its destination, then a router will break the packet into smaller packets (fragmenting). Ideal ...