Giuseppe Razzano , Neeli R. Prasad , Roberto De Paolis
... ·Ease of installation, reduced costs, scalability are among the reasons that have led to an enormous diffusion of wireless systems. An ever increasing number of private houses and small offices are now equipped with wireless access. ·Federal security agency in USA has announced that unsecured Wi-Fi ...
... ·Ease of installation, reduced costs, scalability are among the reasons that have led to an enormous diffusion of wireless systems. An ever increasing number of private houses and small offices are now equipped with wireless access. ·Federal security agency in USA has announced that unsecured Wi-Fi ...
Computer Networks BITS ZC481
... systems to edge router? residential access nets institutional access ...
... systems to edge router? residential access nets institutional access ...
Chapter 7 Part 2 Networks
... will make it more difficult for hackers to find your access code. – Disable SSID broadcast. Most routers are set up to broadcast their SSIDs so they are “discoverable” or other devices can find them. (This would be good protection from the accidental piggybacking. – Change the default password ...
... will make it more difficult for hackers to find your access code. – Disable SSID broadcast. Most routers are set up to broadcast their SSIDs so they are “discoverable” or other devices can find them. (This would be good protection from the accidental piggybacking. – Change the default password ...
mobility - INFONETICS, Inc.
... Simple 56Kbaud dial-up circuits; $15-$25/month plus cost of phone line. 56Kbaud dial-up lines should be used only as a last resort for ...
... Simple 56Kbaud dial-up circuits; $15-$25/month plus cost of phone line. 56Kbaud dial-up lines should be used only as a last resort for ...
IS-Networks
... 2. Ring: computers are linked by a closed loop 3. Bus: all messages are broadcast to the entire network and each device identifies messages sent to it ...
... 2. Ring: computers are linked by a closed loop 3. Bus: all messages are broadcast to the entire network and each device identifies messages sent to it ...
Network Planning Technical Sub
... DNSOne for entering DNS records for the Medical School while continuing to use their existing DHCP servers and will contact ITSS to get started. Network updates Barry – There is still a shortage of available IP addresses at the Medical School. Setting shorter lease times has helped to get by, but th ...
... DNSOne for entering DNS records for the Medical School while continuing to use their existing DHCP servers and will contact ITSS to get started. Network updates Barry – There is still a shortage of available IP addresses at the Medical School. Setting shorter lease times has helped to get by, but th ...
How Client/Server Networks Work
... all these tasks, or several servers might share the duties (often by dedicating each server to one particular task). ...
... all these tasks, or several servers might share the duties (often by dedicating each server to one particular task). ...
Dual Radio Outdoor Wireless Mesh Router
... topology that reduces installation costs by simplifying the installation procedures, and a selfhealing network ensuring the best possible and most reliable connectivity. An advanced quality of service (QoS) mechanism is employed to provide priority to VoIP and other high priority traffic, and fairly ...
... topology that reduces installation costs by simplifying the installation procedures, and a selfhealing network ensuring the best possible and most reliable connectivity. An advanced quality of service (QoS) mechanism is employed to provide priority to VoIP and other high priority traffic, and fairly ...
Technology Chapter 23: Computer and Internet Communication
... Hypertext markup language: a type of coding that tells a receiving computer how a page should look. Input devices: devices that allow an operator to enter data into a computer’s operating system. Internet: interconnected networks of computers that share information. Internet access: the way a comput ...
... Hypertext markup language: a type of coding that tells a receiving computer how a page should look. Input devices: devices that allow an operator to enter data into a computer’s operating system. Internet: interconnected networks of computers that share information. Internet access: the way a comput ...
Business Use of the Internet
... 2. Ring: computers are linked by a closed loop 3. Bus: all messages are broadcast to the entire network and each device identifies messages sent to it ...
... 2. Ring: computers are linked by a closed loop 3. Bus: all messages are broadcast to the entire network and each device identifies messages sent to it ...
The Internet is a global communication network which acts as a
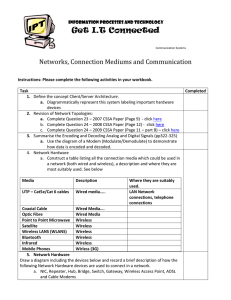
... a. Use the diagram of a Modem (Modulate/Demodulate) to demonstrate how data is encoded and decoded. 4. Network Hardware a. Construct a table listing all the connection media which could be used in a network (both wired and wireless), a description and where they are most suitably used. See below Med ...
... a. Use the diagram of a Modem (Modulate/Demodulate) to demonstrate how data is encoded and decoded. 4. Network Hardware a. Construct a table listing all the connection media which could be used in a network (both wired and wireless), a description and where they are most suitably used. See below Med ...
Computer Networks
... • 2a. Further segmentation and reassembly – Error detection • Need to be able to able to detect errors that may occur on the imperfect transmission line ...
... • 2a. Further segmentation and reassembly – Error detection • Need to be able to able to detect errors that may occur on the imperfect transmission line ...
Bell Canada Holdings Strategic Plan 2004
... Operational Excellence = Strong Service & Experience Environment √ @ High Efficiency √ ...
... Operational Excellence = Strong Service & Experience Environment √ @ High Efficiency √ ...
What is the internet
... years ago by the U.S. Department of Defense. The ARPAnet was an experimental network designed to support military research--in particular, research about how to build networks that could withstand partial outages (like bomb attacks) and still function. ...
... years ago by the U.S. Department of Defense. The ARPAnet was an experimental network designed to support military research--in particular, research about how to build networks that could withstand partial outages (like bomb attacks) and still function. ...
Chapter 6: Wireless and Mobile Networks
... exceeds # wired phone subscribers! computer nets: laptops, palmtops, PDAs, Internet-enabled phone promise anytime untethered Internet access two important (but different) challenges ...
... exceeds # wired phone subscribers! computer nets: laptops, palmtops, PDAs, Internet-enabled phone promise anytime untethered Internet access two important (but different) challenges ...
Test your knowledge
... They establish these standards because it will avoid problems associated with incompatibility between hardware and software components, organisations such as the Institution of Electrical and Electronics Engineers develop network standards. ...
... They establish these standards because it will avoid problems associated with incompatibility between hardware and software components, organisations such as the Institution of Electrical and Electronics Engineers develop network standards. ...
CHAPTER 7 - McGraw Hill Higher Education
... Unified Communication (UC)—The integration of communication channels into a single service Peer-to-Peer (P2P)—A computer network that relies on the computing power and bandwidth of the participants in the network rather than a centralized server Voice over IP (VoIP)—Uses IP technology to trans ...
... Unified Communication (UC)—The integration of communication channels into a single service Peer-to-Peer (P2P)—A computer network that relies on the computing power and bandwidth of the participants in the network rather than a centralized server Voice over IP (VoIP)—Uses IP technology to trans ...
Wide Area Network - Clydebank High School
... A secret code that you would use to gain access to a computer. Must be changes regularly and should not be to easy. ...
... A secret code that you would use to gain access to a computer. Must be changes regularly and should not be to easy. ...
SpeedTouch™ 585(i) v6
... All rights reserved ©2005, Thomson. Printed in EU. 585v6_ed01 All trademarks are owned by their respective owners. Product specifications subject to change without prior notice. ...
... All rights reserved ©2005, Thomson. Printed in EU. 585v6_ed01 All trademarks are owned by their respective owners. Product specifications subject to change without prior notice. ...
Accessing Oakton`s Wireless Network
... www.oakton.edu, etc.). For security reasons, access to internal applications is not allowed. Transmissions of secure information such as ID’s, credit card numbers, passwords, etc. may be intercepted by wireless users in or near the building. Oakton is not responsible for damage to personal property ...
... www.oakton.edu, etc.). For security reasons, access to internal applications is not allowed. Transmissions of secure information such as ID’s, credit card numbers, passwords, etc. may be intercepted by wireless users in or near the building. Oakton is not responsible for damage to personal property ...
CIS 100 Emerge Terms: Exam #3 Bluetooth: enables digital devices
... Bluetooth: enables digital devices to communicate directly with each other wirelessly over short distances. Cascading Style Sheets (CSS): allows easy application of visual styles for fonts, colors, layouts, and other page attributes to create visual themes for webpages and sites. Cellular Network: r ...
... Bluetooth: enables digital devices to communicate directly with each other wirelessly over short distances. Cascading Style Sheets (CSS): allows easy application of visual styles for fonts, colors, layouts, and other page attributes to create visual themes for webpages and sites. Cellular Network: r ...
ITGS
... – Saves money (as in printer sharing), because only one printer must be purchased for the network ...
... – Saves money (as in printer sharing), because only one printer must be purchased for the network ...
What is the internet - New Mexico State University
... years ago by the U.S. Department of Defense. The ARPAnet was an experimental network designed to support military research--in particular, research about how to build networks that could withstand partial outages (like bomb attacks) and still function. ...
... years ago by the U.S. Department of Defense. The ARPAnet was an experimental network designed to support military research--in particular, research about how to build networks that could withstand partial outages (like bomb attacks) and still function. ...