Test 3 review guide 50 questions 10 T/F and 40 multiple choices
... 49- Search engine 50- Helper applications: Plug-ins, players 51- Chat and text messaging 52- Domain name server 53- URL and IP address. 54- Sorting and selection queries ...
... 49- Search engine 50- Helper applications: Plug-ins, players 51- Chat and text messaging 52- Domain name server 53- URL and IP address. 54- Sorting and selection queries ...
Document
... - a router is a device that forwards packets between distinct Layer 3 networks - a router usually has at 2 or more physical network interfaces, though not a strict condition ...
... - a router is a device that forwards packets between distinct Layer 3 networks - a router usually has at 2 or more physical network interfaces, though not a strict condition ...
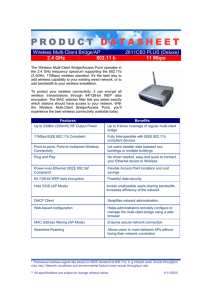
Wireless Multi-Client Bridge/AP 2611CB3 PLUS (Deluxe) 2.4 GHz
... Power-over-Ethernet (IEEE 802.3af Compliant) ...
... Power-over-Ethernet (IEEE 802.3af Compliant) ...
tr-5a series - Baltic Networks
... a self-forming network topology that reduces installation costs by simplifying the installation procedures, and a selfhealing network ensuring the best possible and most reliable connectivity. An advanced quality of service (QoS) mechanism is employed to provide priority to VoIP and other high prior ...
... a self-forming network topology that reduces installation costs by simplifying the installation procedures, and a selfhealing network ensuring the best possible and most reliable connectivity. An advanced quality of service (QoS) mechanism is employed to provide priority to VoIP and other high prior ...
Digital Literacy – Computer Basics – Common Computer Terminology
... A group of computers and associated devices that are linked together to facilitate sharing information is called a ___________. The main computer on a network is called a _________. You use a ______________to access the hardware and software on a network. ___________are commonly used as communicatio ...
... A group of computers and associated devices that are linked together to facilitate sharing information is called a ___________. The main computer on a network is called a _________. You use a ______________to access the hardware and software on a network. ___________are commonly used as communicatio ...
Tsou_2003AAG. ppt - Internet Mapping Services for San Diego
... – Traditional RS and GIS software are very expensive, difficult to use. – Regional program managers and park rangers seldom have the necessary resources or training to access RS/GIS data – There is a strong need to develop an easy-to-use, inexpensive set of field survey tools ...
... – Traditional RS and GIS software are very expensive, difficult to use. – Regional program managers and park rangers seldom have the necessary resources or training to access RS/GIS data – There is a strong need to develop an easy-to-use, inexpensive set of field survey tools ...
4 Communication networks
... NIC detects signals simultaneously at its receives and transmit interfaces The station closest detects the collision transmits a 32-bit jam message onto ...
... NIC detects signals simultaneously at its receives and transmit interfaces The station closest detects the collision transmits a 32-bit jam message onto ...
Start a wireless network with up to 4X the range and 12X
... high-speed cable or DSL Internet connection. The Access Point built into the Router uses the very latest wireless networking technology: Wireless-N (draft 802.11n). By overlaying the signals of multiple radios, Wireless-N’s “Multiple In, Multiple Out” (MIMO) technology multiplies the effective data ...
... high-speed cable or DSL Internet connection. The Access Point built into the Router uses the very latest wireless networking technology: Wireless-N (draft 802.11n). By overlaying the signals of multiple radios, Wireless-N’s “Multiple In, Multiple Out” (MIMO) technology multiplies the effective data ...
Acceptable Use Policy (AUP)
... accordance with the missions and purposes of the networks they use on the Internet and with the laws of Texas and the United States. ...
... accordance with the missions and purposes of the networks they use on the Internet and with the laws of Texas and the United States. ...
Chapter 6 Business Networks & Telecommunications
... for transmission by a signal that is transmitted to it The tag has a digital memory with a unique EPC ...
... for transmission by a signal that is transmitted to it The tag has a digital memory with a unique EPC ...
Gelman, Alex - Panasonic - IEEE-SA
... Wireless: UWB, Bluetooth, IEEE 802.11 Wireline: HPNA, HomePlug ...
... Wireless: UWB, Bluetooth, IEEE 802.11 Wireline: HPNA, HomePlug ...
Telecommunications and Networking - University of Baltimore Home
... configuration table. A configuration table is a collection of information, including: Information on which connections lead to particular groups of addresses Priorities for connections to be used Rules for handling both routine and special cases of traffic A router, then, has two separate but ...
... configuration table. A configuration table is a collection of information, including: Information on which connections lead to particular groups of addresses Priorities for connections to be used Rules for handling both routine and special cases of traffic A router, then, has two separate but ...
C o n t e n t s
... The original Internet was ARPANET(Advanced Research Projects Agency Network),which was established by U.S. Department of Defense in1969.The ARPANET was used to share data between some separated military institutes and universities in region. By 1972 the network had expanded to incorporate 40 nodes. ...
... The original Internet was ARPANET(Advanced Research Projects Agency Network),which was established by U.S. Department of Defense in1969.The ARPANET was used to share data between some separated military institutes and universities in region. By 1972 the network had expanded to incorporate 40 nodes. ...
第2讲无线通信与网络
... Use diffused Infrared, without line-of-sight. Can connect to LAN. Standard not updated for a while. Signal can be swamped by sunlight. Bandwidth is still limited. ...
... Use diffused Infrared, without line-of-sight. Can connect to LAN. Standard not updated for a while. Signal can be swamped by sunlight. Bandwidth is still limited. ...
Slide 1
... Solution: Buffer packets using PSM at APs for IS networks, and end hosts for AH networks. ...
... Solution: Buffer packets using PSM at APs for IS networks, and end hosts for AH networks. ...
Chapter 1 notes
... send and receive e-mail messages and access the internet. Some smartphones have digital cameras, mp3 players, and color display capabilities. • Wearable computer- vary greatly in size and application. ...
... send and receive e-mail messages and access the internet. Some smartphones have digital cameras, mp3 players, and color display capabilities. • Wearable computer- vary greatly in size and application. ...
Proposal Presentation
... intruders and take counter measures Detection of Netstumbler Blocking / Jamming Netstumbler without affecting network performance Product will be open source and will integrate several available technologies ...
... intruders and take counter measures Detection of Netstumbler Blocking / Jamming Netstumbler without affecting network performance Product will be open source and will integrate several available technologies ...
Chapter 4 Computer Networks – Part 2
... A router is used to connect multiple networks ( such as two LANs, two WANs, or a LAN and the Internet) Routers pass data on to the intended recipient only and can plan a path through the network to ensure the data reaches its destination in the most efficient manner possible Are used to route traffi ...
... A router is used to connect multiple networks ( such as two LANs, two WANs, or a LAN and the Internet) Routers pass data on to the intended recipient only and can plan a path through the network to ensure the data reaches its destination in the most efficient manner possible Are used to route traffi ...
Internet and World Wide Web: Amazing Developments
... Fiber-optic cable- Transmits information using beams of light through small strands of glass (fastest and most expensive connection). ...
... Fiber-optic cable- Transmits information using beams of light through small strands of glass (fastest and most expensive connection). ...
rural access in Nepal
... IEEE 802.11 standard - most promising wireless technology. Wireless Fidelity (Wi-Fi) based on IEEE 802.11b standard ...
... IEEE 802.11 standard - most promising wireless technology. Wireless Fidelity (Wi-Fi) based on IEEE 802.11b standard ...
Internetworking: Concepts, Architecture, and Protocols
... Inevitable • No single networking technology best for all needs. ...
... Inevitable • No single networking technology best for all needs. ...