WRT600N Datasheet
... The Dual-Band Wireless-N Gigabit Router is really four devices in one box. First, there’s the dual-band Wireless Access Point, which lets you connect to the network without wires. There’s also a built-in 4-port full-duplex 10/100/1000 Switch to connect your wired-Ethernet devices together at up to g ...
... The Dual-Band Wireless-N Gigabit Router is really four devices in one box. First, there’s the dual-band Wireless Access Point, which lets you connect to the network without wires. There’s also a built-in 4-port full-duplex 10/100/1000 Switch to connect your wired-Ethernet devices together at up to g ...
23-wrapup
... • Little on physical and data link layer • Little on undergraduate material • Supposedly you already know this, though some revisiting/overlap is unavoidable • Focus on the why, not the what ...
... • Little on physical and data link layer • Little on undergraduate material • Supposedly you already know this, though some revisiting/overlap is unavoidable • Focus on the why, not the what ...
bhoot pres1
... for high frequency wireless local area networks operating on the 802.11 standard. ...
... for high frequency wireless local area networks operating on the 802.11 standard. ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... "Hole196" is vulnerability in the WPA2 security protocol exposing WPA2-secured Wi-Fi networks to insider attacks. AirTight Networks uncovered a weakness in the WPA2 protocol, Central to this vulnerability is the group temporal key (GTK) that is shared among all authorized clients in a WPA2 network. ...
... "Hole196" is vulnerability in the WPA2 security protocol exposing WPA2-secured Wi-Fi networks to insider attacks. AirTight Networks uncovered a weakness in the WPA2 protocol, Central to this vulnerability is the group temporal key (GTK) that is shared among all authorized clients in a WPA2 network. ...
Session2
... Networking media can be defined simply as the means by which signals (data) are sent from one computer to another (either by cable or wireless means). Wireless Wired ...
... Networking media can be defined simply as the means by which signals (data) are sent from one computer to another (either by cable or wireless means). Wireless Wired ...
ch._1_-_guided_reading
... 35. What is a modem? What is its purpose? ______________________________________________________________________________________ ______________________________________________________________________________________ ____________________________________________________________________________________ ...
... 35. What is a modem? What is its purpose? ______________________________________________________________________________________ ______________________________________________________________________________________ ____________________________________________________________________________________ ...
5 G ppt - WordPress.com
... • It is developed in 1980s and completed in early 1990s. • It provides a speed up to 2.4kbps. • It is based on analog system. • It allows user to make call in one country. • It has low capacity, unreliable handoff, poor voice links , and no security at all since voice calls were played back in radio ...
... • It is developed in 1980s and completed in early 1990s. • It provides a speed up to 2.4kbps. • It is based on analog system. • It allows user to make call in one country. • It has low capacity, unreliable handoff, poor voice links , and no security at all since voice calls were played back in radio ...
Networking | computer Network | TCP/IP
... • Little on physical and data link layer • Little on undergraduate material • Supposedly you already know this, though some revisiting/overlap is unavoidable • Focus on the why, not the what ...
... • Little on physical and data link layer • Little on undergraduate material • Supposedly you already know this, though some revisiting/overlap is unavoidable • Focus on the why, not the what ...
Wired (Ethernet) Instructions for Windows XP
... Have a valid HuskyNetID and password Windows XP Service Pack 2 For wireless: Have a built-in or installed wireless adapter in your computer. Note: Although most should work, we cannot guarantee compatibility with all wireless adapters. ...
... Have a valid HuskyNetID and password Windows XP Service Pack 2 For wireless: Have a built-in or installed wireless adapter in your computer. Note: Although most should work, we cannot guarantee compatibility with all wireless adapters. ...
PPT network components
... Additional Information about Firewalls • Most home network routers have built in firewall. • The term “firewall” originated from firefighting, where a firewall is a barrier established to prevent the spread of a fire. • A firewall works with the proxy server making request on behalf of workstation ...
... Additional Information about Firewalls • Most home network routers have built in firewall. • The term “firewall” originated from firefighting, where a firewall is a barrier established to prevent the spread of a fire. • A firewall works with the proxy server making request on behalf of workstation ...
Extended Learning Module C
... Mobility and low installation cost Can be extended by adding access points Newer protocols in the 802.11 family offer security protocols (WEP, WPA, and WPA2) Down side Interference from other devices The Wi-Fi standard (802.11g is replacing 802.11b) is easily penetrated by outsiders with a ...
... Mobility and low installation cost Can be extended by adding access points Newer protocols in the 802.11 family offer security protocols (WEP, WPA, and WPA2) Down side Interference from other devices The Wi-Fi standard (802.11g is replacing 802.11b) is easily penetrated by outsiders with a ...
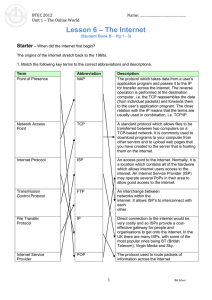
U1L6_The_Internet
... The protocol which takes data from a user’s application program and passes it to the IP for transfer across the internet. The reverse operation is performed at the destination computer, i.e. the TCP reassembles the data (from individual packets) and forwards them to the user’s application program. T ...
... The protocol which takes data from a user’s application program and passes it to the IP for transfer across the internet. The reverse operation is performed at the destination computer, i.e. the TCP reassembles the data (from individual packets) and forwards them to the user’s application program. T ...
Networks
... Network servers that manage the networks and host applications that are shared with client computers Two types: Two-tiered Three-tiered ...
... Network servers that manage the networks and host applications that are shared with client computers Two types: Two-tiered Three-tiered ...
Chapter 4 – Database management SystemsApplied Computer
... b. MAC address c. IP address d. USB address 17. Which of the following is used to select a wireless home network from a PC? a. SSID b. MAC address c. IP address d. USB address 18. Which of the following is used to access a router’s control panel from a PC? a. SSID b. MAC address c. IP address d. USB ...
... b. MAC address c. IP address d. USB address 17. Which of the following is used to select a wireless home network from a PC? a. SSID b. MAC address c. IP address d. USB address 18. Which of the following is used to access a router’s control panel from a PC? a. SSID b. MAC address c. IP address d. USB ...
Chapter 6 slides, Computer Networking, 3rd edition
... infrastructure mode base station connects mobiles into wired network handoff: mobile changes base station ...
... infrastructure mode base station connects mobiles into wired network handoff: mobile changes base station ...
Expanding coverage while preserving beauty in Vail.
... destination for thousands of recreational travelers; however, the challenging topography surrounding the Village and residential neighborhood makes it especially difficult to provide reliable wireless coverage. A few nearby towers and rooftop installations provided some coverage, but were inadequate ...
... destination for thousands of recreational travelers; however, the challenging topography surrounding the Village and residential neighborhood makes it especially difficult to provide reliable wireless coverage. A few nearby towers and rooftop installations provided some coverage, but were inadequate ...
Hardware Systems - Satcom Direct
... Allow us to provide you with a block diagram before prints are engineered ...
... Allow us to provide you with a block diagram before prints are engineered ...
Wireless-G - Computer Direct NZ
... organize your calls, and manage features easily with your own Personal Call Manager home page. And keep one phone number for life, regardless of where you move.** To protect your data and privacy, the Wireless-G Broadband Router can encode all wireless transmissions with up to 128-bit encryption, an ...
... organize your calls, and manage features easily with your own Personal Call Manager home page. And keep one phone number for life, regardless of where you move.** To protect your data and privacy, the Wireless-G Broadband Router can encode all wireless transmissions with up to 128-bit encryption, an ...
Unit E - Home - KSU Faculty Member websites
... Popular because of absence of cables Desirable for notebook and tablet computers ...
... Popular because of absence of cables Desirable for notebook and tablet computers ...
Abstract - PG Embedded systems
... In this analysis, we consider Wireless network, where nodes that have decoded the message at the previous hop cooperate in the transmission toward the next hop, realizing a distributed space-time coding scheme. Service delivery in a heterogeneous all-IP wireless network environment requires the sele ...
... In this analysis, we consider Wireless network, where nodes that have decoded the message at the previous hop cooperate in the transmission toward the next hop, realizing a distributed space-time coding scheme. Service delivery in a heterogeneous all-IP wireless network environment requires the sele ...
MetroFi Cupertino - Wireless Internet Institute
... consumer wireless Internet access. Using enhanced technology based on the popular Wi-Fi (802.11) standard, MetroFi combines a new level of affordability with the convenience of portability to offer highly competitive broadband access services. Cupertino’s Mission: • To ensure affordable broadband ac ...
... consumer wireless Internet access. Using enhanced technology based on the popular Wi-Fi (802.11) standard, MetroFi combines a new level of affordability with the convenience of portability to offer highly competitive broadband access services. Cupertino’s Mission: • To ensure affordable broadband ac ...
computer networks
... • high-resolution color photographs and video clips. • In the past, people have sued network operators. ...
... • high-resolution color photographs and video clips. • In the past, people have sued network operators. ...
Community Wireless Services: how to solve the business and
... • Insufficient information delivery system • Ubiquitous data access is costly • Limited emergency coordination ...
... • Insufficient information delivery system • Ubiquitous data access is costly • Limited emergency coordination ...
Computer Networking
... •As a networking and WLAN user and instructor I have my own thoughts which I will share. •If you are concerned, then research the information and come to your own conclusions. •The following information is from my own research and experience. Wireless Frequency ...
... •As a networking and WLAN user and instructor I have my own thoughts which I will share. •If you are concerned, then research the information and come to your own conclusions. •The following information is from my own research and experience. Wireless Frequency ...
Networking Equipment
... given its final destination (IP address). Usually, routers forward packets to other routers, but sometimes routers also forward to other pieces of network equipment. A router is usually used to connect a home computer to an “always-on” Internet connection through the home network. To appreciate wha ...
... given its final destination (IP address). Usually, routers forward packets to other routers, but sometimes routers also forward to other pieces of network equipment. A router is usually used to connect a home computer to an “always-on” Internet connection through the home network. To appreciate wha ...