Setup Eduroam Access
... Connecting to the eduroam wireless Network: Wireless Connection Guide for Apple Mac 1. Select The “Airport” icon at the top of your screen ...
... Connecting to the eduroam wireless Network: Wireless Connection Guide for Apple Mac 1. Select The “Airport” icon at the top of your screen ...
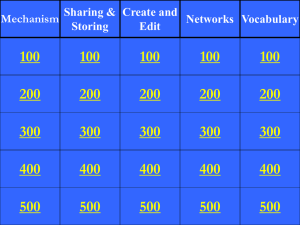
Printed_Networks and Protocols CE00997-3 WEEK 6..
... near the client (customer) which results in greatly increased range and throughput. Mobile WiMAX networks are usually made of indoor "customer premises equipment" (CPE) such as desktop modems, laptops with integrated Mobile WiMAX or other Mobile WiMAX devices. •Mobile WiMAX devices typically have an ...
... near the client (customer) which results in greatly increased range and throughput. Mobile WiMAX networks are usually made of indoor "customer premises equipment" (CPE) such as desktop modems, laptops with integrated Mobile WiMAX or other Mobile WiMAX devices. •Mobile WiMAX devices typically have an ...
Network Topologies Network Topologies
... • All computers/devices connect to a central device called hub or switch. • Each device requires a single cable • point-to-point connection between the device and hub. ...
... • All computers/devices connect to a central device called hub or switch. • Each device requires a single cable • point-to-point connection between the device and hub. ...
3.01a_Network Technology - fitslm
... Definition • Able to connect computers to other computers and printers the same way a wired network is, but without wires. Features: • Range (Depends on factors such as wireless card, access point, and obstacles in between) • Cost (Wireless price is dependent upon the complexity of the setup.) • Eas ...
... Definition • Able to connect computers to other computers and printers the same way a wired network is, but without wires. Features: • Range (Depends on factors such as wireless card, access point, and obstacles in between) • Cost (Wireless price is dependent upon the complexity of the setup.) • Eas ...
Plum
... across a large area such as a country, a continent or even the world. The Internet is an example of a WAN. ...
... across a large area such as a country, a continent or even the world. The Internet is an example of a WAN. ...
Network Connection Guide
... Make sure your network is not setup as a Guest Network. Guest Networks will not allow device-to-device communication. If you have more than 1 network, make sure you iOS Device or PC did not automatically connect to the wrong network. The iOS Device or PC must be connected to the same network that yo ...
... Make sure your network is not setup as a Guest Network. Guest Networks will not allow device-to-device communication. If you have more than 1 network, make sure you iOS Device or PC did not automatically connect to the wrong network. The iOS Device or PC must be connected to the same network that yo ...
Networks
... - Computers are daisy chained together in a linear bus - Data packets are sent along the coax cables - All computers hear data sent out ...
... - Computers are daisy chained together in a linear bus - Data packets are sent along the coax cables - All computers hear data sent out ...
No Slide Title
... All devices are connected to one another in the shape of a closed loop, so that each device is connected directly to two other devices, one on either side of it. ...
... All devices are connected to one another in the shape of a closed loop, so that each device is connected directly to two other devices, one on either side of it. ...
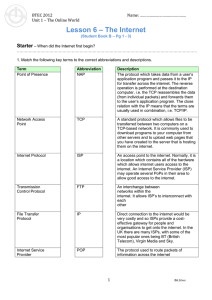
The Internet
... The protocol which takes data from a user’s application program and passes it to the IP for transfer across the internet. The reverse operation is performed at the destination computer, i.e. the TCP reassembles the data (from individual packets) and forwards them to the user’s application program. T ...
... The protocol which takes data from a user’s application program and passes it to the IP for transfer across the internet. The reverse operation is performed at the destination computer, i.e. the TCP reassembles the data (from individual packets) and forwards them to the user’s application program. T ...
CSCI 1200 / ASSC 1000
... – server fulfils client requests – high speed, high capacity computer is the server – hierarchical structure, server is essential ...
... – server fulfils client requests – high speed, high capacity computer is the server – hierarchical structure, server is essential ...
A Brief History of the Internet: The Timeline
... - 1440, "the tilling of land," from L. cultura, from pp. stem of colere "tend, guard, cultivate, till" (see cult). Meaning "the intellectual side of civilization" is from 1805; that of "collective customs and achievements of a people" is from 1867. Culture shock first recorded 1940. ...
... - 1440, "the tilling of land," from L. cultura, from pp. stem of colere "tend, guard, cultivate, till" (see cult). Meaning "the intellectual side of civilization" is from 1805; that of "collective customs and achievements of a people" is from 1867. Culture shock first recorded 1940. ...
Chapter 2
... Internet addresses expressed as 32-bit numbers appear as 201.61.186.227 -- each of the four numbers range from 0 to 255 allowing for up to 4 billion addresses In the next generation IP 128-bit addresses will allow about one quadtrillion addresses ...
... Internet addresses expressed as 32-bit numbers appear as 201.61.186.227 -- each of the four numbers range from 0 to 255 allowing for up to 4 billion addresses In the next generation IP 128-bit addresses will allow about one quadtrillion addresses ...
lecture 17
... People had to physically copy data from machine to machine using a disk. Networks offer many advantages for a business including: Sharing resources Providing opportunities Reducing travel There have been many network security problems - networks are a tempting target for mischief and fraud An organi ...
... People had to physically copy data from machine to machine using a disk. Networks offer many advantages for a business including: Sharing resources Providing opportunities Reducing travel There have been many network security problems - networks are a tempting target for mischief and fraud An organi ...
Wireless and Mobile Networks Part I
... wireless link typically used to connect mobile(s) to base station also used as backbone link multiple access protocol coordinates link access various data rates, ...
... wireless link typically used to connect mobile(s) to base station also used as backbone link multiple access protocol coordinates link access various data rates, ...
Document
... Small antenna services for data gathering, such as smart grid, solar farm, utility companies, etc. ...
... Small antenna services for data gathering, such as smart grid, solar farm, utility companies, etc. ...
ICT Solution for Small Manufacturing Campus Quick Reference for
... of unified planning and standards, providing great support for rapid network information transmission and construction of various application systems. Network design follows the overall roadmap of high performance, standard openness, manageability, security, flexibility, and scalability, compatibili ...
... of unified planning and standards, providing great support for rapid network information transmission and construction of various application systems. Network design follows the overall roadmap of high performance, standard openness, manageability, security, flexibility, and scalability, compatibili ...
Beyond ad-hoc networking
... Terminal diversity increases with devices that today are not generally thought of as Internetcapable, such as tiny and embedded or semi-embedded devices that make their claim for first-class Internet citizenship. Internet-capable nodes become so small and so low-cost and so little power-demanding ...
... Terminal diversity increases with devices that today are not generally thought of as Internetcapable, such as tiny and embedded or semi-embedded devices that make their claim for first-class Internet citizenship. Internet-capable nodes become so small and so low-cost and so little power-demanding ...
Chapter 7: Computer Networks, the Internet, and the World Wide Web
... Users must purchase telecommunications services from an external ...
... Users must purchase telecommunications services from an external ...
Director III - Networks
... MARGINAL FUNCTIONS 1. Educate users in the rational and correct application of network standards. ...
... MARGINAL FUNCTIONS 1. Educate users in the rational and correct application of network standards. ...