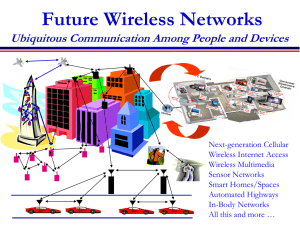
Week-13.1.1
... Well, nobody does. No single person or company owns the Internet or even controls it entirely. As a wide-area network, it is made up of many smaller networks. These smaller networks are often owned and managed by a person or organization. The Internet, then, is really defined by how connections can ...
... Well, nobody does. No single person or company owns the Internet or even controls it entirely. As a wide-area network, it is made up of many smaller networks. These smaller networks are often owned and managed by a person or organization. The Internet, then, is really defined by how connections can ...
Broadcast Channels
... Data flows to centralized location (joint compression) Low per-node rates but tens to thousands of nodes Intelligence is in the network rather than in the devices Similar ideas can be used to re-architect systems and networks to be green ...
... Data flows to centralized location (joint compression) Low per-node rates but tens to thousands of nodes Intelligence is in the network rather than in the devices Similar ideas can be used to re-architect systems and networks to be green ...
IntenetHardware - bridges to computing
... – Uses regular insulated cable TV cables. – Cable Devices (look a lot like modems) – Offers faster service than most DSL connections: 1–10 Mbps upload and 6–50+ Mbps download. • Variable bandwidth becoming more common. ...
... – Uses regular insulated cable TV cables. – Cable Devices (look a lot like modems) – Offers faster service than most DSL connections: 1–10 Mbps upload and 6–50+ Mbps download. • Variable bandwidth becoming more common. ...
Wireless LAN
... – Can be used with either Win95/98 or Win NT – Must be used on a computer with both Wireless and wired network connections – Can use remote administration to set parameters or monitor network ...
... – Can be used with either Win95/98 or Win NT – Must be used on a computer with both Wireless and wired network connections – Can use remote administration to set parameters or monitor network ...
wireless mesh networks
... One radio routing between mesh routers Another radio access to the network from end-users significantly improves the capacity of the network * These functionalities are performed in the same channel in ad-hoc networks performance affected ! ...
... One radio routing between mesh routers Another radio access to the network from end-users significantly improves the capacity of the network * These functionalities are performed in the same channel in ad-hoc networks performance affected ! ...
William Stallings Data and Computer Communications
... 1- computer networkes,Andrew S.Tanenbaum 2- Data Communications and Networking, 3rd Edition, Behrouz A. Forouzan ...
... 1- computer networkes,Andrew S.Tanenbaum 2- Data Communications and Networking, 3rd Edition, Behrouz A. Forouzan ...
Introduction
... Store and Forward or Packet-Switched When a packet is sent from one router to the other via one or more intermediate router in its entirety, stored there until the required output is free. Message divided into packets ...
... Store and Forward or Packet-Switched When a packet is sent from one router to the other via one or more intermediate router in its entirety, stored there until the required output is free. Message divided into packets ...
Class_3_-_Subarea_V
... needs of another program. File servers enable other programs to locate and extract files from databases • Port – A physical or virtual interface or connection between two pieces of hardware. USB is one of the most recognizable port protocols • RAM – Random Access Memory is a part of computer memory ...
... needs of another program. File servers enable other programs to locate and extract files from databases • Port – A physical or virtual interface or connection between two pieces of hardware. USB is one of the most recognizable port protocols • RAM – Random Access Memory is a part of computer memory ...
Six Degrees of Separation
... and Randomness. Princeton University Press. ISBN 0-691-00541-9 Watts, D.J. (2004). Six Degrees: the science of a connected age. W.W. Norton ...
... and Randomness. Princeton University Press. ISBN 0-691-00541-9 Watts, D.J. (2004). Six Degrees: the science of a connected age. W.W. Norton ...
Introduction to Mobile Computing CNT 5517-5564
... – wold-wide deregulation and spectrum auctions – standard communication systems and air link interfaces ...
... – wold-wide deregulation and spectrum auctions – standard communication systems and air link interfaces ...
apMn-Q551
... applications. The AirborneM2M™ Access Point multi-layer security approach addresses the requirements of Enterprise-class networks and corporate IT departments. These advanced security features include wireless security (802.11i/WAP2 enterprise), authentication security using WPA2 (AES-CCMP) and devi ...
... applications. The AirborneM2M™ Access Point multi-layer security approach addresses the requirements of Enterprise-class networks and corporate IT departments. These advanced security features include wireless security (802.11i/WAP2 enterprise), authentication security using WPA2 (AES-CCMP) and devi ...
FirstNet: Tech Terms 101
... Broadband: refers to the wide bandwidth characteristics of a transmission medium, such as coaxial cable, optical fiber, twisted pair, DSL local telephone networks or wireless, and its ability to transport multiple signals or traffic types simultaneously. Wireless: the transfer of information (e.g.: ...
... Broadband: refers to the wide bandwidth characteristics of a transmission medium, such as coaxial cable, optical fiber, twisted pair, DSL local telephone networks or wireless, and its ability to transport multiple signals or traffic types simultaneously. Wireless: the transfer of information (e.g.: ...
A Brief history of the Internet BY ZIYUN WANG
... regional networks of the NSFNET to seek commercial, non-academic customers. • Private, competitive networks such as PSI, UUNET, and later others emerged and grew. ...
... regional networks of the NSFNET to seek commercial, non-academic customers. • Private, competitive networks such as PSI, UUNET, and later others emerged and grew. ...
COMBO Introduction
... handle the traffic demands from data storage close to end users Scalable, simple and cost effective traffic management for local data storage in the cloud ...
... handle the traffic demands from data storage close to end users Scalable, simple and cost effective traffic management for local data storage in the cloud ...
Cradlepoint 4G LTE Parallel Networking
... creating “parallel networks” as an elegantly simple alternative. In this scenario, separate applications such as customer WiFi, employee devices, and Point-of-Sale systems are hosted on their own respective networks. Third party vendors, partners, and kiosks must “Bring Your Own Network” (BYON), red ...
... creating “parallel networks” as an elegantly simple alternative. In this scenario, separate applications such as customer WiFi, employee devices, and Point-of-Sale systems are hosted on their own respective networks. Third party vendors, partners, and kiosks must “Bring Your Own Network” (BYON), red ...
Networking and Security Handout
... The two most common home networks are wired Ethernet and wireless Ethernet. Modern power-line networks, boasting faster data throughput, are now a viable option in certain situations. The major difference in these networks is the transmission media by which the nodes are connected. ...
... The two most common home networks are wired Ethernet and wireless Ethernet. Modern power-line networks, boasting faster data throughput, are now a viable option in certain situations. The major difference in these networks is the transmission media by which the nodes are connected. ...
LANs and WLANs
... • Wireless networks are much more susceptible to unauthorized access and use than wired networks • LAN jacking, or war driving, is the practice of intercepting wireless signals by cruising through an area ...
... • Wireless networks are much more susceptible to unauthorized access and use than wired networks • LAN jacking, or war driving, is the practice of intercepting wireless signals by cruising through an area ...
Chapter 1 - William Stallings, Data and Computer Communications
... • The increasing use of optical fiber and high-speed wireless has brought transmission prices down and greatly increased capacity ...
... • The increasing use of optical fiber and high-speed wireless has brought transmission prices down and greatly increased capacity ...
DCC10e
... • The increasing use of optical fiber and high-speed wireless has brought transmission prices down and greatly increased capacity ...
... • The increasing use of optical fiber and high-speed wireless has brought transmission prices down and greatly increased capacity ...
Six Degrees of Separation - Olympus High Mathematics
... and Randomness. Princeton University Press. ISBN 0-691-00541-9 Watts, D.J. (2004). Six Degrees: the science of a connected age. W.W. Norton ...
... and Randomness. Princeton University Press. ISBN 0-691-00541-9 Watts, D.J. (2004). Six Degrees: the science of a connected age. W.W. Norton ...
Networks
... Often within a building Used for home networking Every device can communicate with every other device NMIT has a number of LANS for different reasons ...
... Often within a building Used for home networking Every device can communicate with every other device NMIT has a number of LANS for different reasons ...