Lesson 8
... Maintenance-out-of-service (MOS) – this feature allows maintenance personnel to place a line out of service for maintenance. If a line is placed MOS while it is in operation, the PBX may terminate its signaling communication with the instrument and leave the instrument’s voice channel connection act ...
... Maintenance-out-of-service (MOS) – this feature allows maintenance personnel to place a line out of service for maintenance. If a line is placed MOS while it is in operation, the PBX may terminate its signaling communication with the instrument and leave the instrument’s voice channel connection act ...
Slide 1
... Encryption transforms a message so that its contents are hidden from unauthorized readers – Plaintext has not yet been encrypted – An encrypted message is referred to as ciphertext Decryption is the opposite of encryption ...
... Encryption transforms a message so that its contents are hidden from unauthorized readers – Plaintext has not yet been encrypted – An encrypted message is referred to as ciphertext Decryption is the opposite of encryption ...
Position Description
... The NIRSA member serving as the Member Network Regional Representative is elected by majority vote through the Regional Representative Elections Process, which is initiated and conducted by the Regional Nominations and Appointments Committee. Term of appointment is two years, beginning May 1 with Re ...
... The NIRSA member serving as the Member Network Regional Representative is elected by majority vote through the Regional Representative Elections Process, which is initiated and conducted by the Regional Nominations and Appointments Committee. Term of appointment is two years, beginning May 1 with Re ...
Designing a PXI Instrument for Testing & Simulation of Avionics
... terms of the protocol stacks used between the network interface and the client applications using the network services. For example, Avionics applications typically don’t utilize services like Dynamic Host Confi ...
... terms of the protocol stacks used between the network interface and the client applications using the network services. For example, Avionics applications typically don’t utilize services like Dynamic Host Confi ...
ready to `software define` your Wide area network?
... SD-WAN, its ability to support a hybrid WAN is not based on a new technology. “Smart people were always trying to use whatever bandwidth they had available,” says ipSpace.net’s Ivan Pepelnjak. “There was no hype around it because it was just network engineers doing our stuff, but the concept of usin ...
... SD-WAN, its ability to support a hybrid WAN is not based on a new technology. “Smart people were always trying to use whatever bandwidth they had available,” says ipSpace.net’s Ivan Pepelnjak. “There was no hype around it because it was just network engineers doing our stuff, but the concept of usin ...
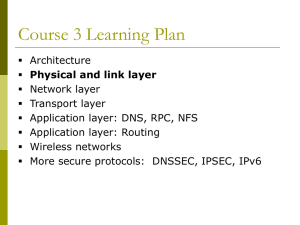
Tutorial on QoS In WLAN
... • Provides service differentiation. • Classifies the traffic into 8 different ...
... • Provides service differentiation. • Classifies the traffic into 8 different ...
Translation
... – 1. Original: Ethernet defines a number of wiring and signaling standards for the physical layer, through means of network access at the Media Access Control (MAC)/Data Link Layer and a common addressing format. – Translation: – 2. Original Adapters generally come programmed with a globally unique ...
... – 1. Original: Ethernet defines a number of wiring and signaling standards for the physical layer, through means of network access at the Media Access Control (MAC)/Data Link Layer and a common addressing format. – Translation: – 2. Original Adapters generally come programmed with a globally unique ...
Kumar`s Security Slides
... Wired Equivalent Privacy (WEP) * “ Wired Equivalent Privacy” * Part of 802.11 Link layer protocol * Security Goals: » prevent link layer eavesdropping » Secondary Goal: prevent network access » Essentially equivalent to wired access point security ...
... Wired Equivalent Privacy (WEP) * “ Wired Equivalent Privacy” * Part of 802.11 Link layer protocol * Security Goals: » prevent link layer eavesdropping » Secondary Goal: prevent network access » Essentially equivalent to wired access point security ...
EEE449 Computer Networks - Universiti Sains Malaysia
... – can adjust, over wide ranges, to changes in delay and throughput across an internet and still meet the needs of its applications. – This is the traditional type of traffic supported on TCP/IP-based internets and is the type of traffic for which internets were designed. – Applications that can be c ...
... – can adjust, over wide ranges, to changes in delay and throughput across an internet and still meet the needs of its applications. – This is the traditional type of traffic supported on TCP/IP-based internets and is the type of traffic for which internets were designed. – Applications that can be c ...
What is Leased Line
... • A leased line is a service contract between a provider and a customer, whereby the provider agrees to deliver a symmetric telecommunications line connecting two or more locations in exchange for a monthly rent (hence the term lease). • It is sometimes known as a "private circuit" or "data line" in ...
... • A leased line is a service contract between a provider and a customer, whereby the provider agrees to deliver a symmetric telecommunications line connecting two or more locations in exchange for a monthly rent (hence the term lease). • It is sometimes known as a "private circuit" or "data line" in ...
1.Physical Layer & Data Link Layer
... Computer responds to ARP requests even if the request is not for itself As above, but file entries marked "pub" The server may foil some attacks on other computers if the requests are broadcast ...
... Computer responds to ARP requests even if the request is not for itself As above, but file entries marked "pub" The server may foil some attacks on other computers if the requests are broadcast ...
PPT - apnic
... – …when NAT deployment started in earnest. – In today’s retail market one public IPv4 address can cost as much as Mbit DSL ...
... – …when NAT deployment started in earnest. – In today’s retail market one public IPv4 address can cost as much as Mbit DSL ...
Internet & Web Protocols - University of Liverpool
... • Web server only knows the contents of the GET request message this request is automatically generated by browser when you select a URL could also come from a link checker, a search engine robot, … can come directly from a telnet connection using port 80 ...
... • Web server only knows the contents of the GET request message this request is automatically generated by browser when you select a URL could also come from a link checker, a search engine robot, … can come directly from a telnet connection using port 80 ...
appendix a: wlan-related terminology - University of Houston
... privacy” [7]. IEEE specifications for wired LANs do not include data encryption as a requirement. This is because approximately all of these LANs are secured by physical means such as walled structures and controlled entrance to buildings, etc. However no such physical boundaries can be provided in ...
... privacy” [7]. IEEE specifications for wired LANs do not include data encryption as a requirement. This is because approximately all of these LANs are secured by physical means such as walled structures and controlled entrance to buildings, etc. However no such physical boundaries can be provided in ...
Chapter 32 Security in the Internet: IPSec, SSL/TLS, PGP
... Under ideal circumstances, we would integrate IPSec’s protocols directly into IP itself. No extra headers or architectural layers are needed. 2- Bump in the stack: IPSec is made a separate layer between IP and data link layer. ...
... Under ideal circumstances, we would integrate IPSec’s protocols directly into IP itself. No extra headers or architectural layers are needed. 2- Bump in the stack: IPSec is made a separate layer between IP and data link layer. ...
2. Advantages of Wireless LANs
... real-time information anywhere in their organization. This mobility supports productivity and service opportunities not possible with wired networks Installation speed and simplicity: Installing a wireless LAN system can be fast and easy and can eliminate the need to pull cable through walls and ...
... real-time information anywhere in their organization. This mobility supports productivity and service opportunities not possible with wired networks Installation speed and simplicity: Installing a wireless LAN system can be fast and easy and can eliminate the need to pull cable through walls and ...
Network Deployment Guide for NovoPRO
... A) Ethernet – NovoPRO can be plugged into your Ethernet via its RJ45 port. Namely, you can connect NovoPRO to your organization’s backbone network. It is recommended to use Ethernet connection (when possible) since it gives you better robustness and higher performance. B) WiFi – NovoPRO’s built-in 8 ...
... A) Ethernet – NovoPRO can be plugged into your Ethernet via its RJ45 port. Namely, you can connect NovoPRO to your organization’s backbone network. It is recommended to use Ethernet connection (when possible) since it gives you better robustness and higher performance. B) WiFi – NovoPRO’s built-in 8 ...
Fiber optic cable
... • Wireless devices might allow for central connectivity of client computers and handheld devices. • Or, they might offer an extension of connectivity to a pre-existing wireless network and could be used to connect entire local area networks to the Internet. • In addition, some wireless devices can b ...
... • Wireless devices might allow for central connectivity of client computers and handheld devices. • Or, they might offer an extension of connectivity to a pre-existing wireless network and could be used to connect entire local area networks to the Internet. • In addition, some wireless devices can b ...
2 Network topology
... This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associ ...
... This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associ ...
Lecture 25: Introduction to Network Security
... …but with Public Key Encryption anyone can get the public key, so you don’t know if the message really came from Alice, even it is says it did. i.e. can’t do authentication ...
... …but with Public Key Encryption anyone can get the public key, so you don’t know if the message really came from Alice, even it is says it did. i.e. can’t do authentication ...
internet2 network
... • Internet2 will have complete control of the optical layer and highly granular lightpath services that can be provisioned dynamically • The network will provide short-term and long-term waves, as well as on-demand or advanced reservation “lightpath” scheduling • Waves come with Service Level guaran ...
... • Internet2 will have complete control of the optical layer and highly granular lightpath services that can be provisioned dynamically • The network will provide short-term and long-term waves, as well as on-demand or advanced reservation “lightpath” scheduling • Waves come with Service Level guaran ...
Sample – Firewall PowerPoint
... • Test the installation/configuration to see if it is doing what you expect it to do. • Consider having the test conducted by someone other than the person/group responsible for the installation, configuration & operation of the firewall. • What do you want to test? – The firewall? – The system conf ...
... • Test the installation/configuration to see if it is doing what you expect it to do. • Consider having the test conducted by someone other than the person/group responsible for the installation, configuration & operation of the firewall. • What do you want to test? – The firewall? – The system conf ...
datasheet
... The product is supplied with its own Line Monitor that allows the user to record, display and store line traffic with WAN protocol decoding for fast debugging. ...
... The product is supplied with its own Line Monitor that allows the user to record, display and store line traffic with WAN protocol decoding for fast debugging. ...
Windows Vista networking technologies
In computing, Microsoft's Windows Vista and Windows Server 2008 introduced in 2007/2008 a new networking stack named Next Generation TCP/IP stack,to improve on the previous stack in several ways.The stack includes native implementation of IPv6, as well as a complete overhaul of IPv4. The new TCP/IP stack uses a new method to store configuration settings that enables more dynamic control and does not require a computer restart after a change in settings. The new stack, implemented as a dual-stack model, depends on a strong host-model and features an infrastructure to enable more modular components that one can dynamically insert and remove.