Chapter 13 Congestion in Data Networks
... • Can restrict to logical connections generating most traffic • Used in connection oriented networks that allow hop by hop congestion control (e.g. X.25) ...
... • Can restrict to logical connections generating most traffic • Used in connection oriented networks that allow hop by hop congestion control (e.g. X.25) ...
Click to add title
... Single optical wavelength must carry 100 Gb/s of information Complex T/R, but extremely efficient in terms of fiber utilization. Easier for carrier to manage as a single wavelength. If the T/R cost is reasonable, much easier to justify in a commercial network. ...
... Single optical wavelength must carry 100 Gb/s of information Complex T/R, but extremely efficient in terms of fiber utilization. Easier for carrier to manage as a single wavelength. If the T/R cost is reasonable, much easier to justify in a commercial network. ...
doc - Andrew.cmu.edu
... 6. In class we discussed fragmentation and reassembly as responsibilities of the network layer, but the MTU is a function of the link layer. Why doesn't the link layer just handle the fragmentation and reassemble itself? ...
... 6. In class we discussed fragmentation and reassembly as responsibilities of the network layer, but the MTU is a function of the link layer. Why doesn't the link layer just handle the fragmentation and reassemble itself? ...
Standards for multimedia communications
... • Unlike the H.322 standard which relates to LANS that offer a guaranteed bandwidth/QoS, the H.323 standard is intended for use with LANs that provide a nonguaranteed QoS which, in practice, applies to the majority of LANs. • The standard comprises components for the packetization and synchronizatio ...
... • Unlike the H.322 standard which relates to LANS that offer a guaranteed bandwidth/QoS, the H.323 standard is intended for use with LANs that provide a nonguaranteed QoS which, in practice, applies to the majority of LANs. • The standard comprises components for the packetization and synchronizatio ...
File - Learning@NDGTA
... listens to see whether any messages are being transmitted. If no message is being transmitted, a station can take control of the network and transmit its message. • This method is known as Carrier Sense Multiple Access (CSMA) ...
... listens to see whether any messages are being transmitted. If no message is being transmitted, a station can take control of the network and transmit its message. • This method is known as Carrier Sense Multiple Access (CSMA) ...
A. Introduction
... — concerned with issues like : • destination address provision • invoking specific services like priority • access to & routing data across a network link • allows layers above to ignore link specifics g. babic ...
... — concerned with issues like : • destination address provision • invoking specific services like priority • access to & routing data across a network link • allows layers above to ignore link specifics g. babic ...
Question Bank - Technical Symposium.
... 15. Discuss about any two methods of framing. 16. Compare virtual circuits and datagrams. 17. List the features of internetworking. 18. What is modern and codec? 19. What is flooding? What are its disadvantages? 20. What are the primary services offered by a computer network? 21. Mention the advanta ...
... 15. Discuss about any two methods of framing. 16. Compare virtual circuits and datagrams. 17. List the features of internetworking. 18. What is modern and codec? 19. What is flooding? What are its disadvantages? 20. What are the primary services offered by a computer network? 21. Mention the advanta ...
Network Address Translation (NAT)
... opportunity to qualify or authenticate the request or match it to a previous request. NAT also conserves on the number of global IP addresses that a company needs and it lets the company use a single IP addressin its communication with the world. NAT is included as part of a router and is often part ...
... opportunity to qualify or authenticate the request or match it to a previous request. NAT also conserves on the number of global IP addresses that a company needs and it lets the company use a single IP addressin its communication with the world. NAT is included as part of a router and is often part ...
Understanding Sociograms
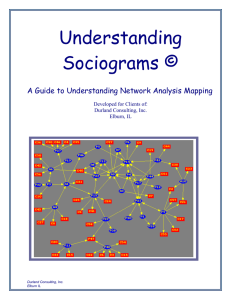
... Components indicate the overall connectedness of a network. Connectedness is an indication of how easily everyone can be reached, if you are studying people. Connectedness describes large subgroups within the larger network. Connectedness indicates major breaks or divisions in the network. Each isol ...
... Components indicate the overall connectedness of a network. Connectedness is an indication of how easily everyone can be reached, if you are studying people. Connectedness describes large subgroups within the larger network. Connectedness indicates major breaks or divisions in the network. Each isol ...
Slide 1
... Communications Software What is communications software? Programs that help users establish connection to Internet, other network, or another computer Programs that help users manage transmission of data, instructions, and information Programs that provide an interface for users to communicate with ...
... Communications Software What is communications software? Programs that help users establish connection to Internet, other network, or another computer Programs that help users manage transmission of data, instructions, and information Programs that provide an interface for users to communicate with ...
Chapter 1 Lecture Presentation
... NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
... NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
PLM & Digital Manufacturing - Industrial Engineering 2011
... • makes the decisions related to connecting any pair of nodes together. It therefore needs to be able to resolve any contentions that may arise. • responsible for tasks such as queuing requests for "link establishment" between nodes. Several advantages of Start Network: 1. The star node is transpare ...
... • makes the decisions related to connecting any pair of nodes together. It therefore needs to be able to resolve any contentions that may arise. • responsible for tasks such as queuing requests for "link establishment" between nodes. Several advantages of Start Network: 1. The star node is transpare ...
Chapter 18 Internet Protocols
... —Multiple higher-level connections share single lowerlevel connection • More efficient use of lower-level service • Provides several higher-level connections where only single lower-level connection exists ...
... —Multiple higher-level connections share single lowerlevel connection • More efficient use of lower-level service • Provides several higher-level connections where only single lower-level connection exists ...
William Stallings Data and Computer Communications
... Developed by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
... Developed by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
UMTS - MobiHealth
... entities which manage the resources of the access network and provides the user with a mechanism to access to Core Network Domain. In UMTS the access network is the UTRAN (Universal Terrestrial Radio Access Network). ...
... entities which manage the resources of the access network and provides the user with a mechanism to access to Core Network Domain. In UMTS the access network is the UTRAN (Universal Terrestrial Radio Access Network). ...
presentation source - CECS Multimedia Communications
... Otherwise, extensive buffering at each end system Many networks such as ISDN: CBR data transports Variable Bit-Rate Traffic: A data rate various with time in bursts or spurts Bursty traffic: Random periods of relative inactivity interspersed with bursts of data A bursty traffic source gene ...
... Otherwise, extensive buffering at each end system Many networks such as ISDN: CBR data transports Variable Bit-Rate Traffic: A data rate various with time in bursts or spurts Bursty traffic: Random periods of relative inactivity interspersed with bursts of data A bursty traffic source gene ...
What Advantages Does an Agile Network Bring (Issue
... the Cold War, but civilians have made wide use of IP. Basically, IP is reliable because every node on an IP communications path is intelligent. For example, when a serious typhoon assaulted the east coast of the U.S in 2008, all mobile phones and fixed phones were unavailable. The only available com ...
... the Cold War, but civilians have made wide use of IP. Basically, IP is reliable because every node on an IP communications path is intelligent. For example, when a serious typhoon assaulted the east coast of the U.S in 2008, all mobile phones and fixed phones were unavailable. The only available com ...
Chapter 18 Internet Protocols
... IPv6 Flow (2) • Router’s point of view —Packets that share attributes that affect how these packets are handled by the router —These attributes include path, resource allocation, discard requirements, accounting, and security attributes —Allocating different buffer sizes —Different precedence in te ...
... IPv6 Flow (2) • Router’s point of view —Packets that share attributes that affect how these packets are handled by the router —These attributes include path, resource allocation, discard requirements, accounting, and security attributes —Allocating different buffer sizes —Different precedence in te ...
Storage Aware Protocols For heterogeneous networks
... Transport layer consideration • Network layer store event may lead to • end-to-end transport layer timeout • Out of order data delivery at the destination • Storage aware routing was evaluated with a hop-by-hop ...
... Transport layer consideration • Network layer store event may lead to • end-to-end transport layer timeout • Out of order data delivery at the destination • Storage aware routing was evaluated with a hop-by-hop ...
doc - EECS: www-inst.eecs.berkeley.edu
... QueuingDelay: time the packet need to wait before being transmitted because the queue was not empty when it arrived. Queueing happens everywhere, switch, router, even in your network card! ...
... QueuingDelay: time the packet need to wait before being transmitted because the queue was not empty when it arrived. Queueing happens everywhere, switch, router, even in your network card! ...
Chapter 18 Internet Protocols
... —Multiple higher-level connections share single lowerlevel connection • More efficient use of lower-level service • Provides several higher-level connections where only single lower-level connection exists ...
... —Multiple higher-level connections share single lowerlevel connection • More efficient use of lower-level service • Provides several higher-level connections where only single lower-level connection exists ...
Lecture 01
... NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
... NICs listen to medium for frames with their address Transmitting NICs listen for collisions with other stations, and abort and reschedule retransmissions Transceivers ...
Chapter 10
... Accepts IP datagrams and transmits over a specific network Can be a device driver or a complex subsystem that uses own data link protocol ...
... Accepts IP datagrams and transmits over a specific network Can be a device driver or a complex subsystem that uses own data link protocol ...
Introduction to Communication Network
... Hierarchical structure; simplified routing; scalability ...
... Hierarchical structure; simplified routing; scalability ...
Windows Vista networking technologies
In computing, Microsoft's Windows Vista and Windows Server 2008 introduced in 2007/2008 a new networking stack named Next Generation TCP/IP stack,to improve on the previous stack in several ways.The stack includes native implementation of IPv6, as well as a complete overhaul of IPv4. The new TCP/IP stack uses a new method to store configuration settings that enables more dynamic control and does not require a computer restart after a change in settings. The new stack, implemented as a dual-stack model, depends on a strong host-model and features an infrastructure to enable more modular components that one can dynamically insert and remove.