IOSR Journal of Computer Engineering (IOSR-JCE)
... reasons. Most important is that attacks are not traceable and the whole network is exposed to all public spoofing and sniffing. There was never been enough identification of the potential vulnerability to danger of devices communicating on the Internet makes security threats commonplace. This signif ...
... reasons. Most important is that attacks are not traceable and the whole network is exposed to all public spoofing and sniffing. There was never been enough identification of the potential vulnerability to danger of devices communicating on the Internet makes security threats commonplace. This signif ...
Internet Control Message Protocol
... host using ICMP echo requests and some manipulation of the TTL value in the IP header. Traceroute starts by sending a UDP datagram to the destination host with the TTL field set to 1. If a router finds a TTL value of 1 or 0, it drops the datagram and sends back an ICMP Time-Exceeded message to the ...
... host using ICMP echo requests and some manipulation of the TTL value in the IP header. Traceroute starts by sending a UDP datagram to the destination host with the TTL field set to 1. If a router finds a TTL value of 1 or 0, it drops the datagram and sends back an ICMP Time-Exceeded message to the ...
Segment Routing - Technology and Use Cases
... © 2010 Cisco and/or its affiliates. All rights reserved. ...
... © 2010 Cisco and/or its affiliates. All rights reserved. ...
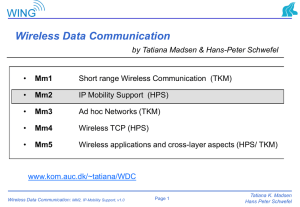
Wireless Data Communication
... – point of attachment to the fixed network can be changed – continuation of communication after handover possible (transparent to transport layer in mobile node as well as to correspondent node) ...
... – point of attachment to the fixed network can be changed – continuation of communication after handover possible (transparent to transport layer in mobile node as well as to correspondent node) ...
LISPmob: Mobile Networking through LISP
... The current Internet architecture was not designed to easily accommodate mobility because IP addresses are used both to identify and locate the hosts. The fact that separating identity from routing location is an important design principle of inter-domain networks was known even before the Internet ...
... The current Internet architecture was not designed to easily accommodate mobility because IP addresses are used both to identify and locate the hosts. The fact that separating identity from routing location is an important design principle of inter-domain networks was known even before the Internet ...
NEST Counter-Sniper Planning Meeting
... 1. Any system with a non-zero Pfa per sensor node 2. Any non-robust system that requires multiple touches per sensor 3. Any system with performance that can be degraded by a malfunctioning, poorly placed, or imperfect node. 4. Any system that creates a disproportionate response to stimuli 5. Any sys ...
... 1. Any system with a non-zero Pfa per sensor node 2. Any non-robust system that requires multiple touches per sensor 3. Any system with performance that can be degraded by a malfunctioning, poorly placed, or imperfect node. 4. Any system that creates a disproportionate response to stimuli 5. Any sys ...
The Internet and Its Uses
... layer 3 address are divided into a network level and then the host level. –Layer 3 addresses supply the network portion of the address. Routers forward packets between networks by referring only to the part of the Network layer address that is required to direct the packet toward the destination net ...
... layer 3 address are divided into a network level and then the host level. –Layer 3 addresses supply the network portion of the address. Routers forward packets between networks by referring only to the part of the Network layer address that is required to direct the packet toward the destination net ...
A Traffic-aware Power Management Protocol for
... routing, reactive routing consumes far less bandwidth for maintaining the routing tables at each node when only a small subset of all available routes is in use at any time, at the expense of high overhead and delay in setting up the route. Proposed reactive routing protocols include DSR [7], [8], A ...
... routing, reactive routing consumes far less bandwidth for maintaining the routing tables at each node when only a small subset of all available routes is in use at any time, at the expense of high overhead and delay in setting up the route. Proposed reactive routing protocols include DSR [7], [8], A ...
Network Layer Functions Network Service Model
... Network-level The most important Service model circuit provided abstraction Ø or by network layer. Determines end-to-end Datagram Characteristics of transporting Data between network edges Network Layer ...
... Network-level The most important Service model circuit provided abstraction Ø or by network layer. Determines end-to-end Datagram Characteristics of transporting Data between network edges Network Layer ...
mobile ip - BWN-Lab
... point of attachment to the Internet, when the MN is not attached to the home network. Home Agent (HA): is the anchor in the home network for the MN. All packets addressed to the MN reach the HA first, unless the MN is located in its home network. In other words, a router on the home network that e ...
... point of attachment to the Internet, when the MN is not attached to the home network. Home Agent (HA): is the anchor in the home network for the MN. All packets addressed to the MN reach the HA first, unless the MN is located in its home network. In other words, a router on the home network that e ...
Open Source Routing, Firewalls and Traffic Shaping
... tc filter add dev eth0 parent 1:0 protocol all prio 1 handle 1:0:1 u32 ht 1:0:0 match u16 0x50 0xffff at 2 ...
... tc filter add dev eth0 parent 1:0 protocol all prio 1 handle 1:0:1 u32 ht 1:0:0 match u16 0x50 0xffff at 2 ...
Laura Protocol v0.1
... This is the central point of the Star-only type network. It sits at the center and acts as the central point of communication for all of the nodes. Encrypted transactions flow through and are facilitated by the Gateway. Any buffered or queued messages are stored in a section of it's encrypted storag ...
... This is the central point of the Star-only type network. It sits at the center and acts as the central point of communication for all of the nodes. Encrypted transactions flow through and are facilitated by the Gateway. Any buffered or queued messages are stored in a section of it's encrypted storag ...
Link-State Routing With Hop-by-Hop Forwarding Can Achieve Optimal Traffic Engineering
... COMPARISON OF VARIOUS TE SCHEMES (NEW CONTRIBUTIONS IN ITALICS) ...
... COMPARISON OF VARIOUS TE SCHEMES (NEW CONTRIBUTIONS IN ITALICS) ...
lecture04-arp
... to a datagram carrying an ICMP error message. ❏ No ICMP error message will be generated for a fragmented datagram that is not the first fragment. ❏ No ICMP error message will be generated for a datagram having a multicast address. ❏ No ICMP error message will be generated for a datagram having a spe ...
... to a datagram carrying an ICMP error message. ❏ No ICMP error message will be generated for a fragmented datagram that is not the first fragment. ❏ No ICMP error message will be generated for a datagram having a multicast address. ❏ No ICMP error message will be generated for a datagram having a spe ...
MAC intelligence for adaptive multimedia in 802.11
... concept in this paragraph and refer for more detail to [12]. “AB-probe” is based on a new method for sampling available bandwidth from Packet pair dispersion. It assumes that the minimum path available bandwidth link (tight link) is found at the bottleneck link. It keeps an estimate of two additiona ...
... concept in this paragraph and refer for more detail to [12]. “AB-probe” is based on a new method for sampling available bandwidth from Packet pair dispersion. It assumes that the minimum path available bandwidth link (tight link) is found at the bottleneck link. It keeps an estimate of two additiona ...
NWM_ch_7
... • Octet 6-12 is IP address • Examples: IBM host IP address 10.10.10.10 SNMPv1: 00 00 00 02 01 0A 0A 0A 0A 00 00 00 SNMPv3: 10 00 00 02 02 00 00 00 00 00 00 00 0A 0A 0A 0A Network Management: Principles and Practice © Mani Subramanian 2000 ...
... • Octet 6-12 is IP address • Examples: IBM host IP address 10.10.10.10 SNMPv1: 00 00 00 02 01 0A 0A 0A 0A 00 00 00 SNMPv3: 10 00 00 02 02 00 00 00 00 00 00 00 0A 0A 0A 0A Network Management: Principles and Practice © Mani Subramanian 2000 ...
Network Configuration Example Adding a New Routing Device to
... This network configuration example describes how to configure a new Juniper Networks routing device with a single Routing Engine or dual Routing Engines. You will learn how to log in to the router management console interface for the first time, how to log in to your routing device’s management Ethe ...
... This network configuration example describes how to configure a new Juniper Networks routing device with a single Routing Engine or dual Routing Engines. You will learn how to log in to the router management console interface for the first time, how to log in to your routing device’s management Ethe ...
Chapter 4: Network Layer
... VC numbers, one number for each link along path entries in forwarding tables in routers along path ...
... VC numbers, one number for each link along path entries in forwarding tables in routers along path ...
We apply the shortest augmenting path algorithm for our
... We observe that the maximum flow using the flow augmenting path algorithm is 45 at the moment while the optimum is 65. We now have to divert flows in existing paths and effectively consider additional paths (which we could not consider earlier). 1. We consider the path 1-3-2-5-6. This appears as an ...
... We observe that the maximum flow using the flow augmenting path algorithm is 45 at the moment while the optimum is 65. We now have to divert flows in existing paths and effectively consider additional paths (which we could not consider earlier). 1. We consider the path 1-3-2-5-6. This appears as an ...
Ch. 9 – Basic Router Troubleshooting
... • Not the best path, but the best source of routing information. • “The administrative distance of the route is the key information that the router uses in deciding (which is the best path to a particular destination) –> what is the best source of routing information to a particular destination.” Ri ...
... • Not the best path, but the best source of routing information. • “The administrative distance of the route is the key information that the router uses in deciding (which is the best path to a particular destination) –> what is the best source of routing information to a particular destination.” Ri ...
Chapter6
... • Using subinterfaces for inter-VLAN routing results in a less complex physical configuration (less cables) than using separate physical interfaces. • On the other hand, using subinterfaces with a trunk port results in a more complex software configuration, which can be difficult to troubleshoot. • ...
... • Using subinterfaces for inter-VLAN routing results in a less complex physical configuration (less cables) than using separate physical interfaces. • On the other hand, using subinterfaces with a trunk port results in a more complex software configuration, which can be difficult to troubleshoot. • ...
Characterizing Online Discussions in Microblogs Using Network Analysis Veronika Strnadova David Jurgens
... than those for sports teams, due to the participants focus and even geographic location. Understanding what the quantitative differences are between types of discussions can enable the categorization of a novel topic, based on the dynamics of the online conversation discussing it. As a part of our i ...
... than those for sports teams, due to the participants focus and even geographic location. Understanding what the quantitative differences are between types of discussions can enable the categorization of a novel topic, based on the dynamics of the online conversation discussing it. As a part of our i ...
Automatic Clustering of Grid Nodes
... Iso-bar [4] is a scalable overlay distance monitoring system, which clusters hosts based on the similarity of their perceived network distance from designated landmarks. Basically, the objective of using a Traccer/Landmark/mServer is to allow scalability of large-scale network measurements and analy ...
... Iso-bar [4] is a scalable overlay distance monitoring system, which clusters hosts based on the similarity of their perceived network distance from designated landmarks. Basically, the objective of using a Traccer/Landmark/mServer is to allow scalability of large-scale network measurements and analy ...
“Disruption Tolerant Shell,”
... Because of poor links and other disruptions, end-to-end performance in this network falls off rapidly as the number of hops increases. This has led us to use DTN techniques for data transfer rather than multiple parallel end to end connections. The sensor data is buffered, stored into bundles, and tra ...
... Because of poor links and other disruptions, end-to-end performance in this network falls off rapidly as the number of hops increases. This has led us to use DTN techniques for data transfer rather than multiple parallel end to end connections. The sensor data is buffered, stored into bundles, and tra ...