Document
... We’re making these slides freely available to all (faculty, students, readers). They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
Chapter 4 slides
... We’re making these slides freely available to all (faculty, students, readers). They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
ppt
... • UDP is one of the two major transport-layer protocols used in the Internet, the other being TCP. • UDP is the only connectionless transport service. • UDP is less compelx than TCP. “The device at one end of the communication transmits data to the other, without first ensuring that the recipient is ...
... • UDP is one of the two major transport-layer protocols used in the Internet, the other being TCP. • UDP is the only connectionless transport service. • UDP is less compelx than TCP. “The device at one end of the communication transmits data to the other, without first ensuring that the recipient is ...
On the Construction of Data Aggregation Tree with Minimum Energy
... We first illustrate the network model in Section II-A. Subsequently, our problem is described and shown to be NPcomplete in Section II-B. A. The Network Model We model a network as a connected graph G = (V, E) with weights s(v) ∈ Z+ and 0 associated with each node v ∈ V \ {r} and r, respectively, wh ...
... We first illustrate the network model in Section II-A. Subsequently, our problem is described and shown to be NPcomplete in Section II-B. A. The Network Model We model a network as a connected graph G = (V, E) with weights s(v) ∈ Z+ and 0 associated with each node v ∈ V \ {r} and r, respectively, wh ...
Sensor Networks for Medical Care
... low data rates, with a focus on best-effort data collection at a central base station. By contrast, medical monitoring requires relatively high data rates, reliable communication, and multiple receivers (e.g. PDAs carried by doctors and nurses). Moreover, unlike many sensor network applications, med ...
... low data rates, with a focus on best-effort data collection at a central base station. By contrast, medical monitoring requires relatively high data rates, reliable communication, and multiple receivers (e.g. PDAs carried by doctors and nurses). Moreover, unlike many sensor network applications, med ...
A Feedback Based Scheme For Improving TCP Performance in Ad-Hoc Wireless Networks.
... h1 needs to send a packet to h2 and h2 is not within the range of h1 , then the packet must be sent to one of h1's neighbors, say hi, and hi will forward that packet to its neighbor, and so on, until it reaches the destination, h2. In this example, hi acts as a router. The topology of an ad-hoc netw ...
... h1 needs to send a packet to h2 and h2 is not within the range of h1 , then the packet must be sent to one of h1's neighbors, say hi, and hi will forward that packet to its neighbor, and so on, until it reaches the destination, h2. In this example, hi acts as a router. The topology of an ad-hoc netw ...
沒有投影片標題 - National Tsing Hua University
... Distributed routing algorithms, first used in APPANET until 1979. Used in RIP (Routing Information Protocol) and BGP (Border Gateway Protocol) ...
... Distributed routing algorithms, first used in APPANET until 1979. Used in RIP (Routing Information Protocol) and BGP (Border Gateway Protocol) ...
Towards Complete Node Enumeration in a Peer-to
... these VM environments [8]. With either bare-metal machines or virtual machines, it is very hard to enumerate the Storm network: (i) only a few of the Storm nodes are controlled, and (ii) only a partial view of the network is obtained. ...
... these VM environments [8]. With either bare-metal machines or virtual machines, it is very hard to enumerate the Storm network: (i) only a few of the Storm nodes are controlled, and (ii) only a partial view of the network is obtained. ...
Manual
... is when to terminate FTP/GENERIC during the simulation.
If is set to 0, FTP/GENERIC will run until the specified or until the end of the simulation, which ever comes first.
If is set to 0, FTP/GENERIC will run until all is
transmitted ...
...
Chapter 9: Introduction to Metropolitan Area Networks and Wide
... communications lines (various types of telephone lines). When a data packet enters a router, the router examines the IP address encapsulated in the network layer of the packet and determines where the packet should go next. When there are multiple routes through a network such as the Internet, how i ...
... communications lines (various types of telephone lines). When a data packet enters a router, the router examines the IP address encapsulated in the network layer of the packet and determines where the packet should go next. When there are multiple routes through a network such as the Internet, how i ...
IP Multicasting in HF Radio Networks - NMSU TraceBase
... Traffic flowing from an originating node is delivered more or less simultaneously to multiple receivers. In some applications, only one node originates traffic to its multicast group, while in others any member of a multicast group can originate traffic that is sent to all members of the group. The ...
... Traffic flowing from an originating node is delivered more or less simultaneously to multiple receivers. In some applications, only one node originates traffic to its multicast group, while in others any member of a multicast group can originate traffic that is sent to all members of the group. The ...
Our Brochure - Basic Commerce and Industries
... heartbeat function is used to recognize system level failures allowing for automatic switchover of ATN Router operations from the Primary Processor to the Standby Processor. The switchover process for X.25 connectivity uses a remotely controlled A/B switch manufactured by Electro Standards Laborator ...
... heartbeat function is used to recognize system level failures allowing for automatic switchover of ATN Router operations from the Primary Processor to the Standby Processor. The switchover process for X.25 connectivity uses a remotely controlled A/B switch manufactured by Electro Standards Laborator ...
21. + 24. P2P (21.4.+28.4.) - ole unibz
... Structured P2P architectures • When looking for a piece of data, it is important to return the id of the node responsible for that piece of data. • This is achieved by performing routing of the request from the node that originated the request to the node responsible for the key associated to the da ...
... Structured P2P architectures • When looking for a piece of data, it is important to return the id of the node responsible for that piece of data. • This is achieved by performing routing of the request from the node that originated the request to the node responsible for the key associated to the da ...
Topic 16: Routing in IP over ATM networks
... The basic function of LANE is to carry out the MAC address to ATM address resolving. Once the resolving is done, it is the native ATM layer job to create the path between end systems. Additional complexity comes from the need to create separate LAN’s into one ATM network, called emulated LAN’s (ELAN ...
... The basic function of LANE is to carry out the MAC address to ATM address resolving. Once the resolving is done, it is the native ATM layer job to create the path between end systems. Additional complexity comes from the need to create separate LAN’s into one ATM network, called emulated LAN’s (ELAN ...
Distance Vector Routing Protocols
... Incorrectly configured route redistribution Slow convergence Incorrectly configured discard routes ...
... Incorrectly configured route redistribution Slow convergence Incorrectly configured discard routes ...
Design Philosophy
... sufficiently flexible to accommodate all major potential options. These are described in the section of this document on “Wide Area Connectivity.” That section also describes the networks that will be used for management, control and data planes and for WAN resources used as part of experimental env ...
... sufficiently flexible to accommodate all major potential options. These are described in the section of this document on “Wide Area Connectivity.” That section also describes the networks that will be used for management, control and data planes and for WAN resources used as part of experimental env ...
show ip route
... A single high-level route entry with a subnet mask less than the classful mask can be used to represent many lowerlevel routes. This results in fewer entries in the routing table. The static route on R2 is using a /16 mask to summarize all 256 networks ranging from 192.168.0.0/24 to 192.168.25 ...
... A single high-level route entry with a subnet mask less than the classful mask can be used to represent many lowerlevel routes. This results in fewer entries in the routing table. The static route on R2 is using a /16 mask to summarize all 256 networks ranging from 192.168.0.0/24 to 192.168.25 ...
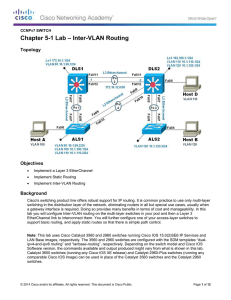
Lab 5-1 Inter-VLAN Routing
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
PPT - Electrical and Computer Engineering
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
Group Address
... • Broadcast-and-prune protocols for the source-based trees include all network segments to start with. When the first multicast datagram arrives at a router, the router may realise whether there is/is not any member in its leaf. In latter case it will send a prune message to the upstream router. • D ...
... • Broadcast-and-prune protocols for the source-based trees include all network segments to start with. When the first multicast datagram arrives at a router, the router may realise whether there is/is not any member in its leaf. In latter case it will send a prune message to the upstream router. • D ...
Practical Network-Wide Compression of IP Routing Tables
... routers select the longest matching prefix when there are multiple choices. However, longest prefix matching significantly complicates aggregation, i.e., the ability to take two prefixes with the same next-hop information and combine them into a single, larger prefix. An example of such a complicati ...
... routers select the longest matching prefix when there are multiple choices. However, longest prefix matching significantly complicates aggregation, i.e., the ability to take two prefixes with the same next-hop information and combine them into a single, larger prefix. An example of such a complicati ...
ppt - UW Courses Web Server
... and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) I ...
... and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) I ...
Network Layer
... and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) I ...
... and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) I ...