An Enhanced Data Mining Technique for Energy Efficiency
... data communication should be done in the energy efficient manner. Centralized solutions for the data collection are not recommended. Obvious the drawbacks of this type of solutions include the hindering the network since the sink node becomes bottleneck, the bandwidth allocated is not efficiently us ...
... data communication should be done in the energy efficient manner. Centralized solutions for the data collection are not recommended. Obvious the drawbacks of this type of solutions include the hindering the network since the sink node becomes bottleneck, the bandwidth allocated is not efficiently us ...
PPT - CS.Duke
... • Establish multicast forwarding state – Flood to all destinations (reverse path flooding) • Key design challenge: loop-avoidance • Q: how many broadcast loop-avoidance mechanisms have we learned? – Prone those not in the group ...
... • Establish multicast forwarding state – Flood to all destinations (reverse path flooding) • Key design challenge: loop-avoidance • Q: how many broadcast loop-avoidance mechanisms have we learned? – Prone those not in the group ...
WIRE07-slide
... RCoA address change in another binding message so that the HA and CNs would know the MN by its new RCoA address; DMAP intercepts the packet destined for RCoA, inspects the address pair stored in the internal table, finds out MN’s CoA and forwards the packet to the MN through tunneling; ...
... RCoA address change in another binding message so that the HA and CNs would know the MN by its new RCoA address; DMAP intercepts the packet destined for RCoA, inspects the address pair stored in the internal table, finds out MN’s CoA and forwards the packet to the MN through tunneling; ...
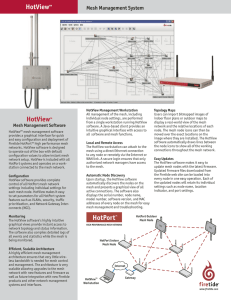
HotViewTM HotView™
... display a real-world view of the mesh network and the relative locations of each node. The mesh node icons can then be moved over the exact locations on the image where they are installed. The HotView software automatically draws lines between the node icons to show all of the working connections th ...
... display a real-world view of the mesh network and the relative locations of each node. The mesh node icons can then be moved over the exact locations on the image where they are installed. The HotView software automatically draws lines between the node icons to show all of the working connections th ...
Application of Mininet
... Learn about the usage of network tool traceroute. Based on your readings, answer the following questions. 1. Explain the difference between hub, bridge/switch and router. 2. Which is more suitable for a network with a high traffic load, hub or switch? Why? A hub is less expensive, less intelligent, ...
... Learn about the usage of network tool traceroute. Based on your readings, answer the following questions. 1. Explain the difference between hub, bridge/switch and router. 2. Which is more suitable for a network with a high traffic load, hub or switch? Why? A hub is less expensive, less intelligent, ...
Security of IP Routing Protocols
... Exploit #2 uses spoofed RIP packets. Variants of this attack could use ARP or IRDP instead. If other unauthenticated IGP or EGP protocols were used on the network, then they could be spoofed to achieve similar results. (See §5 below for a description of these protocols.) ...
... Exploit #2 uses spoofed RIP packets. Variants of this attack could use ARP or IRDP instead. If other unauthenticated IGP or EGP protocols were used on the network, then they could be spoofed to achieve similar results. (See §5 below for a description of these protocols.) ...
Online IP CIDR / VLSM Supernet Calculator
... Without CIDR, our routing table would need to maintain a seperate entry for each of the eight individual networks. As the eight example networks are contiguous, i.e. their address spaces follow numerically with no gaps, we can encapsulate all eight with a single CIDR route by simply changing the sub ...
... Without CIDR, our routing table would need to maintain a seperate entry for each of the eight individual networks. As the eight example networks are contiguous, i.e. their address spaces follow numerically with no gaps, we can encapsulate all eight with a single CIDR route by simply changing the sub ...
ceg790
... allocation method, with the steps: – Conduct simulation for any given network with complete wavelength conversion and any given traffic load and pattern. During simulation, record utilization matrix. – Based on recorded utilization matrix, execute Optimization Algorithm to optimize allocation of FWC ...
... allocation method, with the steps: – Conduct simulation for any given network with complete wavelength conversion and any given traffic load and pattern. During simulation, record utilization matrix. – Based on recorded utilization matrix, execute Optimization Algorithm to optimize allocation of FWC ...
Cisco Router Configuration Basics Presented By Mark Tinka
... Cannot reach a destination on another separate network without going through an intermediate device A device with at least 2 interfaces can route ...
... Cannot reach a destination on another separate network without going through an intermediate device A device with at least 2 interfaces can route ...
What is Wireless Mesh Network?
... Advantages of Mesh Networks • Decreased need for Internet gateways • Collaborative redundant backup technology, which insures data security in the event of disk failure • The ability to configure routes dynamically • Lower power requirements, which could potentially be met by low-cost or renewable ...
... Advantages of Mesh Networks • Decreased need for Internet gateways • Collaborative redundant backup technology, which insures data security in the event of disk failure • The ability to configure routes dynamically • Lower power requirements, which could potentially be met by low-cost or renewable ...
ITE PC v4.0 Chapter 1
... There are many key structures and performance-related characteristics referred to when discussing networks: topology, speed, cost, security, availability, scalability, and reliability. Cisco routers and Cisco switches have many similarities. They support a similar modal operating system, similar ...
... There are many key structures and performance-related characteristics referred to when discussing networks: topology, speed, cost, security, availability, scalability, and reliability. Cisco routers and Cisco switches have many similarities. They support a similar modal operating system, similar ...
modeling lane dynamics
... Emulation Clients (LECs). Four subnets are identified as having LECs in the network area. Each subnet consists of 5 LECs with traffic sources and sinks. ...
... Emulation Clients (LECs). Four subnets are identified as having LECs in the network area. Each subnet consists of 5 LECs with traffic sources and sinks. ...
- Rich`s Cabrillo College CIS Classes
... machine is set up, its RARP client program requests from the RARP server on the router to be sent its IP address. Assuming that an entry has been set up in the router table, the RARP server will return the IP address to the machine which can store it for future use. ...
... machine is set up, its RARP client program requests from the RARP server on the router to be sent its IP address. Assuming that an entry has been set up in the router table, the RARP server will return the IP address to the machine which can store it for future use. ...
Document
... Explicit Route Object (ERO) • A list of groups of nodes along the explicit route (generically called "source route") • Thinking: source routing is better for calls than hop-by-hop routing as it can take into account loading conditions • Constrained shortest path first (CSPF) algorithm executed at t ...
... Explicit Route Object (ERO) • A list of groups of nodes along the explicit route (generically called "source route") • Thinking: source routing is better for calls than hop-by-hop routing as it can take into account loading conditions • Constrained shortest path first (CSPF) algorithm executed at t ...
A Zero Burst Loss Architecture for star OBS Networks.
... of deflection and offset recalculation can happen several times along the journey of a burst. A core node on receiving a setup message looks at its routing table to determine the next hop based on the destination information the setup message carries. Since the node has knowledge about the current u ...
... of deflection and offset recalculation can happen several times along the journey of a burst. A core node on receiving a setup message looks at its routing table to determine the next hop based on the destination information the setup message carries. Since the node has knowledge about the current u ...
Forward-node-set-based broadcast in clustered mobile ad hoc
... within its vicinity (say within the 3-hop coverage area as shown in Figure 1a). A non-clusterhead node just relays the broadcast packet if it is selected as a forward node or else it does nothing. Information about the clusterheads that will receive the broadcast packet from the forwarding clusterhe ...
... within its vicinity (say within the 3-hop coverage area as shown in Figure 1a). A non-clusterhead node just relays the broadcast packet if it is selected as a forward node or else it does nothing. Information about the clusterheads that will receive the broadcast packet from the forwarding clusterhe ...
T201xxxx MM7 – Use Cases, Goals and Requirements
... RFC822 • RFC822 more convenient to use (e.g. [email protected]) than MSISDN; MSISDN would require to send a keyword identifying the desired service • Again, some billing issues – see below ...
... RFC822 • RFC822 more convenient to use (e.g. [email protected]) than MSISDN; MSISDN would require to send a keyword identifying the desired service • Again, some billing issues – see below ...
Internet Protocols - RPI ECSE - Rensselaer Polytechnic Institute
... Update interval: 30 sec. Every half minute, each router broadcasts it’s routing table in entirety to it’s neighbors. Invalid timer: 180 sec. If no update about the route is received in this time, it is marked as invalid and advertised unreachable. However, it continues to forward packets until flush ...
... Update interval: 30 sec. Every half minute, each router broadcasts it’s routing table in entirety to it’s neighbors. Invalid timer: 180 sec. If no update about the route is received in this time, it is marked as invalid and advertised unreachable. However, it continues to forward packets until flush ...
LAN - Temple CIS
... Multiple access protocols single shared broadcast channel two or more simultaneous transmissions by nodes: interference • collision if node receives two or more signals at the same time ...
... Multiple access protocols single shared broadcast channel two or more simultaneous transmissions by nodes: interference • collision if node receives two or more signals at the same time ...
Implementation of the Gnutella protocol in Python
... There is a project in SourceForge.net, for those who are willing to collaborate in the development. The project is at http://sf.net/projects/pygnutella. The last version of the library is available in the CVS repository of that project. As the protocol specification says [1], Gnutella is a protocol ...
... There is a project in SourceForge.net, for those who are willing to collaborate in the development. The project is at http://sf.net/projects/pygnutella. The last version of the library is available in the CVS repository of that project. As the protocol specification says [1], Gnutella is a protocol ...
ppt
... • Computation occurring at the network (IP) layer of the protocol stack capsule based approach • Programming can be done by any user • Source of most active debate © Srinivasan Seshan, 2002 ...
... • Computation occurring at the network (IP) layer of the protocol stack capsule based approach • Programming can be done by any user • Source of most active debate © Srinivasan Seshan, 2002 ...
Advanced Networking Concepts & Troubleshooting
... [output cut] Gateway of last resort is not set D 192.168.30.0/24 [90/2172] via 192.168.20.2,00:04:36, Serial0/0 C 192.168.10.0/24 is directly connected, FastEthernet0/0 D 192.168.40.0/24 [90/2681] via 192.168.20.2,00:04:36, Serial0/0 C 192.168.20.0/24 is directly connected, Serial0/0 D 192.168.50.0/ ...
... [output cut] Gateway of last resort is not set D 192.168.30.0/24 [90/2172] via 192.168.20.2,00:04:36, Serial0/0 C 192.168.10.0/24 is directly connected, FastEthernet0/0 D 192.168.40.0/24 [90/2681] via 192.168.20.2,00:04:36, Serial0/0 C 192.168.20.0/24 is directly connected, Serial0/0 D 192.168.50.0/ ...
tele - De Montfort University
... given different addresses. Thus it is the data entity that has an address. As ECUs are not assigned addresses, as in a traditional network, it follows that they can listen in to any message that they wish. CANBUS IS NOT A POINT TO POINT NETWORK, it is better thought of as a knowledge base. ECUs are ...
... given different addresses. Thus it is the data entity that has an address. As ECUs are not assigned addresses, as in a traditional network, it follows that they can listen in to any message that they wish. CANBUS IS NOT A POINT TO POINT NETWORK, it is better thought of as a knowledge base. ECUs are ...