Layer 3 Multiprotocol Label Switching Vir-
... attracting customers as a result of its lower price and scalability which makes it superior regarding network routing size, routing performance, link bandwidth utilization and services. In case of traditional network layer packet forwarding like IP forwarding, packet travels from one router to the n ...
... attracting customers as a result of its lower price and scalability which makes it superior regarding network routing size, routing performance, link bandwidth utilization and services. In case of traditional network layer packet forwarding like IP forwarding, packet travels from one router to the n ...
Multicasting and Multicast Routing Protocols
... IGMP is not a multicasting routing protocol IGMP is a protocol that manages group membership The IGMP protocol gives the multicast routers information about the membership status of hosts (routers) connected to the network ...
... IGMP is not a multicasting routing protocol IGMP is a protocol that manages group membership The IGMP protocol gives the multicast routers information about the membership status of hosts (routers) connected to the network ...
Putting BGP on the Right Path: Better Performance via Next-Hop Routing
... be filtered (and hence eliminated from consideration) and assigns a “local preference”; ...
... be filtered (and hence eliminated from consideration) and assigns a “local preference”; ...
Traffic Engineering in Multi-Granularity, Heterogeneous, WDM
... The graph is divided into four layers, namely access layer, mux layer, grooming layer, and wavelength layer. • The access layer : the access point of a connection request, i.e., the point where a customer’s connection starts and terminates. It can be an IP router, an ATM switch, or any other client ...
... The graph is divided into four layers, namely access layer, mux layer, grooming layer, and wavelength layer. • The access layer : the access point of a connection request, i.e., the point where a customer’s connection starts and terminates. It can be an IP router, an ATM switch, or any other client ...
Trace Driven Analysis of the Long Term Evolution of Gnutella Peer
... and 2006 traffic. In 2003, messages travel 6.85 hops into the network. Messages required 4.46 hops to reach our logging client and arrived with a mean TTL left of 2.39. Similarly, in 2005, messages travel 6.31 hops into the network requiring 3.41 hops to reach our client and arriving with a TTL of 2 ...
... and 2006 traffic. In 2003, messages travel 6.85 hops into the network. Messages required 4.46 hops to reach our logging client and arrived with a mean TTL left of 2.39. Similarly, in 2005, messages travel 6.31 hops into the network requiring 3.41 hops to reach our client and arriving with a TTL of 2 ...
Taxonomy of communication networks
... Then the delay to transfer a message of 1 Kbits from A to B (from the beginning until host receives last bit) is: ...
... Then the delay to transfer a message of 1 Kbits from A to B (from the beginning until host receives last bit) is: ...
Detecting Wormhole Attacks in Wireless Sensor Networks
... in the network, forwards them through a wired or wireless link with less latency than the network links, and relays them to another point in the network. This paper describes a distributed wormhole detection algorithm for wireless sensor networks, which detects wormholes based on the distortions the ...
... in the network, forwards them through a wired or wireless link with less latency than the network links, and relays them to another point in the network. This paper describes a distributed wormhole detection algorithm for wireless sensor networks, which detects wormholes based on the distortions the ...
Introduction to Routing and Packet Forwarding
... A Metric is a numerical value used by routing protocols help determine the best path to a destination –The smaller the metric value the better the path ...
... A Metric is a numerical value used by routing protocols help determine the best path to a destination –The smaller the metric value the better the path ...
Industrial Application of Coloured Petri Nets for Protocol Verification
... The ERDP CPN model can have an arbitrary number of tokens on the packet buffers. An upper integer bound of 1 was imposed on each of the packet buffers (GWIn, GWOut, ERIn, EROut). This also prevents overtaking among the packets transmitted across the wireless link. The number of tokens simult ...
... The ERDP CPN model can have an arbitrary number of tokens on the packet buffers. An upper integer bound of 1 was imposed on each of the packet buffers (GWIn, GWOut, ERIn, EROut). This also prevents overtaking among the packets transmitted across the wireless link. The number of tokens simult ...
F. MILSA implementation considerations
... policy. For example, realm A trusts realm B, and realm B trusts realm C. Whether realm A should trust C through B, or require direct authentication of C depends on the operational policy of A. Every realm can set its internal policy for its subrealms and can set different external policy. More expli ...
... policy. For example, realm A trusts realm B, and realm B trusts realm C. Whether realm A should trust C through B, or require direct authentication of C depends on the operational policy of A. Every realm can set its internal policy for its subrealms and can set different external policy. More expli ...
1-network
... Here the first six digits are the manufacturers ID and the last six digits are the device ID As each packet arrives at the network interface card the mac address on the packet is compared to the mac address of the device If the addresses match the packet is accepted ...
... Here the first six digits are the manufacturers ID and the last six digits are the device ID As each packet arrives at the network interface card the mac address on the packet is compared to the mac address of the device If the addresses match the packet is accepted ...
Research Article Mobile Agent-Based Directed Diffusion in
... network architecture, which may be suitable for a wide range of sensor applications. Thus, we will consider MA in multihop environments with the absence of a clusterhead. Without clusterhead, we have to answer the following questions. (1) How is an MA routed from sink to source, from source to sourc ...
... network architecture, which may be suitable for a wide range of sensor applications. Thus, we will consider MA in multihop environments with the absence of a clusterhead. Without clusterhead, we have to answer the following questions. (1) How is an MA routed from sink to source, from source to sourc ...
An Overlay Protection Layer against Denial-of-Service Attacks
... controllers) [2]. In such an environment, the communication path among application sites needs to be kept clear of interferences such as DoS attacks: attacks that attempt to overwhelm the processing units or link capacity of the target site (or routers that are topologically close) by saturating wit ...
... controllers) [2]. In such an environment, the communication path among application sites needs to be kept clear of interferences such as DoS attacks: attacks that attempt to overwhelm the processing units or link capacity of the target site (or routers that are topologically close) by saturating wit ...
I41026670
... engineering. In MPLS TE, a Label Switched Path (LSP) is established for carrying traffic along an explicit traffic-engineered path, which can be different from the normal destination-based routing path. IP networks typically have multiple pathways that traffic can take to reach its destination. Rely ...
... engineering. In MPLS TE, a Label Switched Path (LSP) is established for carrying traffic along an explicit traffic-engineered path, which can be different from the normal destination-based routing path. IP networks typically have multiple pathways that traffic can take to reach its destination. Rely ...
Router R1 in Figure 6.8 receives a packet with destination address
... The result is 201.4.22.0, which does not match the corresponding network address (row 1). 2. The second mask (/25) is applied to the destination address. The result is 201.4.22.0, which does not match the corresponding network address (row 2). 3. The third mask (/24) is applied to the destination ad ...
... The result is 201.4.22.0, which does not match the corresponding network address (row 1). 2. The second mask (/25) is applied to the destination address. The result is 201.4.22.0, which does not match the corresponding network address (row 2). 3. The third mask (/24) is applied to the destination ad ...
Analyzing Router Responsiveness to Measurement Probes
... gives the percentage of anonymous nodes in the original data set. The next three columns give the classification of anonymous nodes as percentage values. The last two columns presents final topology size and percentage of anonymous routers after processing. According to the table, the ratio of path ...
... gives the percentage of anonymous nodes in the original data set. The next three columns give the classification of anonymous nodes as percentage values. The last two columns presents final topology size and percentage of anonymous routers after processing. According to the table, the ratio of path ...
PPT
... Proactive protocols may have lower latency since routes are maintained at all times Reactive protocols may have higher latency because a route from X to Y will be found only when X attempts to send to Y Reactive protocols may have lower overhead since routes are determined only if needed Proactive p ...
... Proactive protocols may have lower latency since routes are maintained at all times Reactive protocols may have higher latency because a route from X to Y will be found only when X attempts to send to Y Reactive protocols may have lower overhead since routes are determined only if needed Proactive p ...
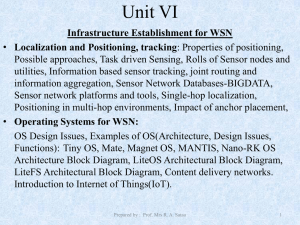
File - e-study
... • A sensor node that wakes up execute a protocol to discover which other nodes it can communicate with. (bidirectional) • At initial state each node try to connect with neighbors according to the radio link capacity of its own. ...
... • A sensor node that wakes up execute a protocol to discover which other nodes it can communicate with. (bidirectional) • At initial state each node try to connect with neighbors according to the radio link capacity of its own. ...
sensor networks - BWN-Lab
... RMST provides end-to-end data-packet transfer reliability Each RMST node caches the packets When a packet is not received before the so-called WATCHDOG timer expires, a NAK is sent backward The first RMST node that has the required packet along the path retransmits the packet RMST relies on Directed ...
... RMST provides end-to-end data-packet transfer reliability Each RMST node caches the packets When a packet is not received before the so-called WATCHDOG timer expires, a NAK is sent backward The first RMST node that has the required packet along the path retransmits the packet RMST relies on Directed ...
Network Bucket Testing.
... To avoid wasting many nodes on the construction of the fringe, therefore, we instead pursue approaches that try to build core sets C with the property that each u ∈ C has many neighbors in C. This way, we need to add fewer nodes to the fringe; for example, if each u ∈ C had at least d neighbors in C ...
... To avoid wasting many nodes on the construction of the fringe, therefore, we instead pursue approaches that try to build core sets C with the property that each u ∈ C has many neighbors in C. This way, we need to add fewer nodes to the fringe; for example, if each u ∈ C had at least d neighbors in C ...
Multi-domain Diagnosis of End-to
... exist for every node-to-node or end-to-end service that correspond to different types of failures that may be experienced by the service. Since causal relationships between nodeto-node and end-to-end service failures are difficult to determine due to their dynamic and unpredictable nature, the FPM i ...
... exist for every node-to-node or end-to-end service that correspond to different types of failures that may be experienced by the service. Since causal relationships between nodeto-node and end-to-end service failures are difficult to determine due to their dynamic and unpredictable nature, the FPM i ...
ROUTE10S03L05
... Task 1: Configure OSPF over LAN interfaces – What steps did you take to configure the OSPF routing protocol and advertise all of the specific IP subnets used in the network? – How can you change the configuration to prevent any network added to the router from being advertised? – How does this cha ...
... Task 1: Configure OSPF over LAN interfaces – What steps did you take to configure the OSPF routing protocol and advertise all of the specific IP subnets used in the network? – How can you change the configuration to prevent any network added to the router from being advertised? – How does this cha ...
Lecture 1: Course Introduction and Overview
... » Back-pressure: separate wires to tell to stop » Window: give original sender right to send N packets before getting permission to send more; overlapslatency of interconnection with overhead to send & receive packet (e.g., TCP), adjustable window – Choke packets: aka “rate-based”; Each packet recei ...
... » Back-pressure: separate wires to tell to stop » Window: give original sender right to send N packets before getting permission to send more; overlapslatency of interconnection with overhead to send & receive packet (e.g., TCP), adjustable window – Choke packets: aka “rate-based”; Each packet recei ...
ppt - CS-CSIF - University of California, Davis
... Integrating Cellular Networks, WLANs and MANETs: A Futuristic Heterogeneous Wireless Network”, In IEEE Wireless Communications Magazine, v12 i3. pp.30-41, June ...
... Integrating Cellular Networks, WLANs and MANETs: A Futuristic Heterogeneous Wireless Network”, In IEEE Wireless Communications Magazine, v12 i3. pp.30-41, June ...