lec1
... systems lead to the refinement of the concept of process. A process can be defined by its attributes and behaviors : it can be viewed as an Abstract Data Type (ADT). When instances of this ADT co-exist we have concurrent ...
... systems lead to the refinement of the concept of process. A process can be defined by its attributes and behaviors : it can be viewed as an Abstract Data Type (ADT). When instances of this ADT co-exist we have concurrent ...
CS9222 Advanced Operating Systems Mr.N.M. BalaMurugan
... Requests, Consumable Resources, Reusable Resources. Objective: To teach the basic concepts, phases and types of various operation systems along with several representations, specification and Phase management. ...
... Requests, Consumable Resources, Reusable Resources. Objective: To teach the basic concepts, phases and types of various operation systems along with several representations, specification and Phase management. ...
The Operating System
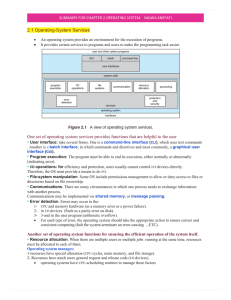
... Coordinates all software activity within a computer system: The master control program that runs the computer. The first program loaded when the computer is turned on, its main part, the "kernel," resides in memory at all times. The operating system sets the standards for all application programs th ...
... Coordinates all software activity within a computer system: The master control program that runs the computer. The first program loaded when the computer is turned on, its main part, the "kernel," resides in memory at all times. The operating system sets the standards for all application programs th ...
Plan 9 from Bell Labs
... to the X server to start running, a remote 8½ application sees the mouse, bitblt, and cons files for the window as usual in /dev; it does not know whether the files are local. It just reads and writes them to control the window; the network connection is already there and multiplexed. The intended s ...
... to the X server to start running, a remote 8½ application sees the mouse, bitblt, and cons files for the window as usual in /dev; it does not know whether the files are local. It just reads and writes them to control the window; the network connection is already there and multiplexed. The intended s ...
Lecture1
... Saves time and money Retraining is avoided Programs written in one Unix system can be run on any other system supporting Unix ...
... Saves time and money Retraining is avoided Programs written in one Unix system can be run on any other system supporting Unix ...
Chapter 3: Operating
... Program execution – system capability to load a program into memory and to run it. I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delet ...
... Program execution – system capability to load a program into memory and to run it. I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delet ...
OPERATING SYSTEM
... system, on-line help, and application integration. The recent trend has been toward increasingly integrated graphical user interfaces that encompass the activities of multiple processes on networks of computers. ...
... system, on-line help, and application integration. The recent trend has been toward increasingly integrated graphical user interfaces that encompass the activities of multiple processes on networks of computers. ...
Operating Systems - Cardiff University
... • It separates the machine-independent parts from the machine-dependent parts – Kernel is machine-dependent. It contains the basic component of OS. User Space ...
... • It separates the machine-independent parts from the machine-dependent parts – Kernel is machine-dependent. It contains the basic component of OS. User Space ...
system call
... all operating system data structures are visible to all operating system code code in procedures are dependent upon knowledge of structure/operation of other ...
... all operating system data structures are visible to all operating system code code in procedures are dependent upon knowledge of structure/operation of other ...
Lecture-1
... System Calls (Windows Win32 API) • Process Management – CreateProcess- new process (combined work of fork and execve in UNIX) • In Windows – no process hierarchy, event concept implemented ...
... System Calls (Windows Win32 API) • Process Management – CreateProcess- new process (combined work of fork and execve in UNIX) • In Windows – no process hierarchy, event concept implemented ...
Lecture 22 File-System Interface
... collection of similar records treated as a single entity have unique file names may restrict access ...
... collection of similar records treated as a single entity have unique file names may restrict access ...
02_OperatingSystemOverview
... – Developments Leading to Modern Operating Systems – Microsoft Windows Overview – UNIX Systems – Linux ...
... – Developments Leading to Modern Operating Systems – Microsoft Windows Overview – UNIX Systems – Linux ...
PPT - Duke Database Devils
... allocates memory to store its code and data. It may establish a new context and/or thread. ...
... allocates memory to store its code and data. It may establish a new context and/or thread. ...
1. design principle
... can support Windows NT on a given system can be expressed with the formula (RAM - 10M) + pagefile = 22M. This formula can be simplified to (pagefile size) = 32M - RAM. Therefore, on a computer with 24M of RAM, the minimum pagefile size should be no less than 8M. To modify page file settings, open th ...
... can support Windows NT on a given system can be expressed with the formula (RAM - 10M) + pagefile = 22M. This formula can be simplified to (pagefile size) = 32M - RAM. Therefore, on a computer with 24M of RAM, the minimum pagefile size should be no less than 8M. To modify page file settings, open th ...
UNIX/Linux Environment
... History of developing UNIX OS • The original Bell Labs UNIX: • 1969/70 Ken Thompson - UNiplexed Information and Computing Service (the spelling of UNICS was later changed to UNIX) • 1973 Ken Thompson and Dennis Ritchie (the author of C language) rewrote the system in C ...
... History of developing UNIX OS • The original Bell Labs UNIX: • 1969/70 Ken Thompson - UNiplexed Information and Computing Service (the spelling of UNICS was later changed to UNIX) • 1973 Ken Thompson and Dennis Ritchie (the author of C language) rewrote the system in C ...
Introduction
... • In UNIX the mounted file system is used to deal with removable media (mount). • Two kinds of special files exist in UNIX under the /dev directory: block special files (disks) and character special files (printers, modems). • A pipe is a sort of pseudo file that can be used to connect two processes ...
... • In UNIX the mounted file system is used to deal with removable media (mount). • Two kinds of special files exist in UNIX under the /dev directory: block special files (disks) and character special files (printers, modems). • A pipe is a sort of pseudo file that can be used to connect two processes ...
CSc 352: Systems Programming & Unix
... lists the files in a directory one screenful at a time How this works: • ls writes its output to its stdout • more’s input stream defaults to its stdin • the pipe connects ls’s stdout to more’s stdin • the piped commands run “in parallel” ...
... lists the files in a directory one screenful at a time How this works: • ls writes its output to its stdout • more’s input stream defaults to its stdin • the pipe connects ls’s stdout to more’s stdin • the piped commands run “in parallel” ...
Presentación de PowerPoint
... File system: mecanism to access the file using its symbolic name Directory: data structure that groups a set of files File operations: open, close, read, write, append, ... UNIX file management is implemented using ...
... File system: mecanism to access the file using its symbolic name Directory: data structure that groups a set of files File operations: open, close, read, write, append, ... UNIX file management is implemented using ...
and more
... Operating System (cont’d) In general, there is one narrow usage and a broader usage Narrow usage: Only the parts that deal directly with the hardware, and very low level features (i.e. the kernel) Broader usage: Also includes system software. What is “system software” depends on the nature of ...
... Operating System (cont’d) In general, there is one narrow usage and a broader usage Narrow usage: Only the parts that deal directly with the hardware, and very low level features (i.e. the kernel) Broader usage: Also includes system software. What is “system software” depends on the nature of ...
slides
... Command-line interface (CLI): require a program to allow entering and editing of text commends. Graphics user interface (GUI): a window system with a pointing device and a keyboard to enter commends. Batch: commands and directives are entered into files to be ...
... Command-line interface (CLI): require a program to allow entering and editing of text commends. Graphics user interface (GUI): a window system with a pointing device and a keyboard to enter commends. Batch: commands and directives are entered into files to be ...
Slides - Bilkent University Computer Engineering Department
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
lec01
... Approached Bill Gates to see if he can build one Gates approached Seattle computer products, bought 86DOS and created MS-DOS Goal: finish quickly and run existing CP/M software OS becomes subroutine library and command executive ...
... Approached Bill Gates to see if he can build one Gates approached Seattle computer products, bought 86DOS and created MS-DOS Goal: finish quickly and run existing CP/M software OS becomes subroutine library and command executive ...
Chapter 1: Introduction
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
Summary for chapter 2 OPERATING SYSTEM nAJWA kNEFATI
... A programmer accesses an API via a library of code provided by the operating system (In C language, the library is called libc). Each operating system has its own name for each system call. The functions that make up an API typically invoke the actual system calls . EX: Function CreateProcess () (cr ...
... A programmer accesses an API via a library of code provided by the operating system (In C language, the library is called libc). Each operating system has its own name for each system call. The functions that make up an API typically invoke the actual system calls . EX: Function CreateProcess () (cr ...
Plan 9 from Bell Labs
.png?width=300)
Plan 9 from Bell Labs is a distributed operating system, originally developed by the Computing Sciences Research Center at Bell Labs between the mid-1980s and 2002. It takes some of the principles of Unix, developed in the same research group, but extends these to a networked environment with graphics terminals.In Plan 9, virtually all computing resources, including files, network connections, and peripheral devices, are represented through the file system rather than specialized interfaces. A unified network protocol called 9P ties a network of computers running Plan 9 together, allowing them to share all resources so represented.The name Plan 9 from Bell Labs is a reference to the Ed Wood 1959 cult science fiction Z-movie Plan 9 from Outer Space. Also, Glenda, the Plan 9 Bunny, is presumably a reference to Wood's film Glen or Glenda. The system continues to be used and developed by operating system researchers and hobbyists.