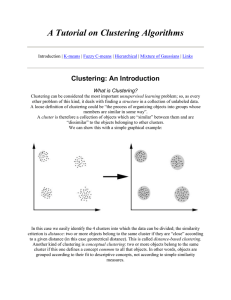
A Tutorial on Clustering Algorithms
... idea is to define k centroids, one for each cluster. These centroids shoud be placed in a cunning way because of different location causes different result. So, the better choice is to place them as much as possible far away from each other. The next step is to take each point belonging to a given d ...
... idea is to define k centroids, one for each cluster. These centroids shoud be placed in a cunning way because of different location causes different result. So, the better choice is to place them as much as possible far away from each other. The next step is to take each point belonging to a given d ...
Nuclear Knowledge Bases and Portals
... • Homogenization (avoid contradictions, but allow different views) Use Standards ...
... • Homogenization (avoid contradictions, but allow different views) Use Standards ...
The Evolution of Analytics
... Machine Learning in the Analytic Landscape Machine learning first appeared in computer science research in the 1950s. So why, after all these decades, has it become so popular? The easy answer is that both the data storage and the data process‐ ing capacities have grown tremendously, to the point w ...
... Machine Learning in the Analytic Landscape Machine learning first appeared in computer science research in the 1950s. So why, after all these decades, has it become so popular? The easy answer is that both the data storage and the data process‐ ing capacities have grown tremendously, to the point w ...
Semantic Web Architecture and Applications
... Third, Semantic Web database architecture is dynamic and automated. Each new document which is analyzed, extracted and stored in the Semantic Web expands the logical relationships in all earlier documents. These expanding logical relationships increase the understanding of content and context in eac ...
... Third, Semantic Web database architecture is dynamic and automated. Each new document which is analyzed, extracted and stored in the Semantic Web expands the logical relationships in all earlier documents. These expanding logical relationships increase the understanding of content and context in eac ...
May 2016 Factsheet Monthly
... Document and prospectus, together with the latest audited annual report (and subsequent unaudited semi-annual report, if published), copies of which can be obtained, free of charge, from Schroder Investment Management (Luxembourg) S.A. The Company is a Luxembourg-registered UCITS recognised in the U ...
... Document and prospectus, together with the latest audited annual report (and subsequent unaudited semi-annual report, if published), copies of which can be obtained, free of charge, from Schroder Investment Management (Luxembourg) S.A. The Company is a Luxembourg-registered UCITS recognised in the U ...
Slide 1
... partners to streamline business processes and to develop effective collaboration amongst them for utilizing the extended trading network to add value. ‘For effective collaboration, interoperability is the theme for standardization.’ ...
... partners to streamline business processes and to develop effective collaboration amongst them for utilizing the extended trading network to add value. ‘For effective collaboration, interoperability is the theme for standardization.’ ...
Queries and Updates in the coDB Peer to Peer Database System
... those tuples which are already in R, and get the set of tuples T ′ . If the conjunctive query in the head of the rule contains existential variables, then fresh new marked null values are used in tuples of T ′ . Then, T ′ is added to R. Incoming links, which are dependent on O, are computed by subst ...
... those tuples which are already in R, and get the set of tuples T ′ . If the conjunctive query in the head of the rule contains existential variables, then fresh new marked null values are used in tuples of T ′ . Then, T ′ is added to R. Incoming links, which are dependent on O, are computed by subst ...
An Investigation Into The Security Of Oracle 10g
... • A thorough knowledge and scrutiny of the four security layers. • Then find ways to break through these layers from the outer boundary to the pinnacle (in a good sense) • As well as finding possible ways to avoid penetration through these security layers • Finally make a well informed conclusion ba ...
... • A thorough knowledge and scrutiny of the four security layers. • Then find ways to break through these layers from the outer boundary to the pinnacle (in a good sense) • As well as finding possible ways to avoid penetration through these security layers • Finally make a well informed conclusion ba ...
Lesson 1: Access Basics
... View This Presentation to Answer the Following Questions: • How do I open a database? • What are the parts of the Access screen? • How can Access save my data? • How can I print data from a database? • What should I do before I close a database? ...
... View This Presentation to Answer the Following Questions: • How do I open a database? • What are the parts of the Access screen? • How can Access save my data? • How can I print data from a database? • What should I do before I close a database? ...
Computarised Accounting Practices
... are both defined and accurate, so that subsequent decisions based on the findings are valid. This stage provides both the baseline from which to measure, and a target on what to improve. Some types of data collection include census (data collection about everything in a group or statistical populati ...
... are both defined and accurate, so that subsequent decisions based on the findings are valid. This stage provides both the baseline from which to measure, and a target on what to improve. Some types of data collection include census (data collection about everything in a group or statistical populati ...
Synchronization and replication in the context of mobile applications
... There are many technical implications that come with resource replication, or data replication as it will also be referred to. The main requirement in data replication is, that replicas should functionally behave like servers, that are not replicated. This strict requirement can not always be fulfi ...
... There are many technical implications that come with resource replication, or data replication as it will also be referred to. The main requirement in data replication is, that replicas should functionally behave like servers, that are not replicated. This strict requirement can not always be fulfi ...
Application of High Performance Computing in Investment Banks
... affecting the recognition of gain or loss, the valuation of goodwill, the recognition of deferred tax assets and other matters; (xii) limitations on the effectiveness of UBS’s internal processes for risk management, risk control, measurement and modeling, and of financial models generally; (xiii) wh ...
... affecting the recognition of gain or loss, the valuation of goodwill, the recognition of deferred tax assets and other matters; (xii) limitations on the effectiveness of UBS’s internal processes for risk management, risk control, measurement and modeling, and of financial models generally; (xiii) wh ...
Silicon Photonics Market by Product
... Silicon Photonics Market by Product (Photonic Wavelength, Optical Modulators, Optical Interconnects, WDMF, LED, and Others), Application (Telecommunication, Data Communication, and Others) and by Geography - Global Trends and Forecasts to 2014 - 2020 The silicon photonics market report analyzes the ...
... Silicon Photonics Market by Product (Photonic Wavelength, Optical Modulators, Optical Interconnects, WDMF, LED, and Others), Application (Telecommunication, Data Communication, and Others) and by Geography - Global Trends and Forecasts to 2014 - 2020 The silicon photonics market report analyzes the ...
A Historical Dataset of Software Engineering Conferences
... to which conferences to submit their work. To facilitate such tasks, we have included a number of example metrics and queries in the repository7 , out of which we illustrate two. Both are computed using a sliding window, to better control for differences in conference age. 1) PC Turnover: computed f ...
... to which conferences to submit their work. To facilitate such tasks, we have included a number of example metrics and queries in the repository7 , out of which we illustrate two. Both are computed using a sliding window, to better control for differences in conference age. 1) PC Turnover: computed f ...
Database and Database Users Databases and Database Users
... Flexibility: It may be necessary to change the structure of a database as requirements change. Modern DBMSs allow certain types of evolutionary changes to the structure of the database without affecting the stored data and the existing application programs. Availability of Up-to-Date Information: A ...
... Flexibility: It may be necessary to change the structure of a database as requirements change. Modern DBMSs allow certain types of evolutionary changes to the structure of the database without affecting the stored data and the existing application programs. Availability of Up-to-Date Information: A ...
7PRO presentation template - Knowledge Engineering Group
... Relational data mining The knowledge base describes large amount of items, along with their associated information: documents, design sequences, etc Structured engineering data about the company products RDM algorithms are aimed to find nontrivial relations between these data, making implicit knowl ...
... Relational data mining The knowledge base describes large amount of items, along with their associated information: documents, design sequences, etc Structured engineering data about the company products RDM algorithms are aimed to find nontrivial relations between these data, making implicit knowl ...
PostgreSQL vs NoSQL Why structure matters Cybertec, 2013 Hans-Jürgen Schönig
... => did you ever get caught speeding? => do you always separate your waste before you throw it away? ...
... => did you ever get caught speeding? => do you always separate your waste before you throw it away? ...
Australian Bureau of Statistics (ABS): Submission to the House
... Collection and compilation of foreign investment in real estate The ABS maintains transparency in its compilation practices in order to make aware of assumptions and the limitations of usability of its published data. As there is no appropriate source for the collection of data on foreign investment ...
... Collection and compilation of foreign investment in real estate The ABS maintains transparency in its compilation practices in order to make aware of assumptions and the limitations of usability of its published data. As there is no appropriate source for the collection of data on foreign investment ...
Lab1-Dimensional
... level of detail in the process. In this next step we will circle back through our dimensions and facts and put together a quick list of Attributes and Metrics that we require for our dimensional model this list allows you to get more specific about the needs of your dimensional model. Completing the ...
... level of detail in the process. In this next step we will circle back through our dimensions and facts and put together a quick list of Attributes and Metrics that we require for our dimensional model this list allows you to get more specific about the needs of your dimensional model. Completing the ...
Introduction to Databases
... • Why is that useful…? – Data becomes information – Information becomes knowledge – Knowledge becomes wisdom RHS – 2009 ...
... • Why is that useful…? – Data becomes information – Information becomes knowledge – Knowledge becomes wisdom RHS – 2009 ...
StorageTek T9840D Tape Drive Data sheet
... The robust cartridge loader mechanism is designed to operate in the industry’s leading library, the StorageTek SL8500 modular library system, and other StorageTek libraries. Protect Sensitive Data with Encryption and WORM Choose one or both—encryption and/or write-once, read-many (WORM) technology—t ...
... The robust cartridge loader mechanism is designed to operate in the industry’s leading library, the StorageTek SL8500 modular library system, and other StorageTek libraries. Protect Sensitive Data with Encryption and WORM Choose one or both—encryption and/or write-once, read-many (WORM) technology—t ...
Chapter 2: Making Statements with Precision: Con
... resampling is done at random. More details on this are given in Sec. ??.) The researcher writes up another memo to marketing: “The lifetime of any one bulb is random, but our best information is that the mean of 10 bulbs selected randomly from our production line will be between 1770 and 2840 hours, ...
... resampling is done at random. More details on this are given in Sec. ??.) The researcher writes up another memo to marketing: “The lifetime of any one bulb is random, but our best information is that the mean of 10 bulbs selected randomly from our production line will be between 1770 and 2840 hours, ...
Legal Disclaimer Geneva Bioinformatics (GeneBio)
... Geneva Bioinformatics (GeneBio) S.A. (hereinafter known as GeneBio) has been granted exclusive rights by the SIB Swiss Institute of Bioinformatics (hereinafter known as SIB) for the licensing of the SIB Licensed Databases PROSITE, SWISS-2DPAGE and SWISSSIDECHAIN databases to all entities accessing t ...
... Geneva Bioinformatics (GeneBio) S.A. (hereinafter known as GeneBio) has been granted exclusive rights by the SIB Swiss Institute of Bioinformatics (hereinafter known as SIB) for the licensing of the SIB Licensed Databases PROSITE, SWISS-2DPAGE and SWISSSIDECHAIN databases to all entities accessing t ...
ERP System and Enterprise Architecture
... the majority of business rules. This will require communication with the storage logic to retrieve additional data. Business transactions are processed in this component. Results from the processing are written to the storage logic. ...
... the majority of business rules. This will require communication with the storage logic to retrieve additional data. Business transactions are processed in this component. Results from the processing are written to the storage logic. ...