ERP System and Enterprise Architecture
... the majority of business rules. This will require communication with the storage logic to retrieve additional data. Business transactions are processed in this component. Results from the processing are written to the storage logic. ...
... the majority of business rules. This will require communication with the storage logic to retrieve additional data. Business transactions are processed in this component. Results from the processing are written to the storage logic. ...
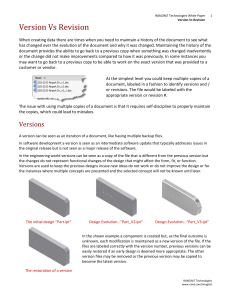
Version vs Revision - IMAGINiT | Autodesk | AutoCAD | Design
... When creating data there are times when you need to maintain a history of the document to see what has changed over the evolution of the document and why it was changed. Maintaining the history of the document provides the ability to go back to a previous copy when something was changed inadvertentl ...
... When creating data there are times when you need to maintain a history of the document to see what has changed over the evolution of the document and why it was changed. Maintaining the history of the document provides the ability to go back to a previous copy when something was changed inadvertentl ...
Tender Document
... There is a growing body of research related to this topic. In our database of empirical studies of the price effects of environmental or energy certification on property prices, we have documented over 20 papers that have been put into the public domain since 2008 (see Appendix 1 for a review of rel ...
... There is a growing body of research related to this topic. In our database of empirical studies of the price effects of environmental or energy certification on property prices, we have documented over 20 papers that have been put into the public domain since 2008 (see Appendix 1 for a review of rel ...
A Historical Dataset of Software Engineering Conferences
... to which conferences to submit their work. To facilitate such tasks, we have included a number of example metrics and queries in the repository7 , out of which we illustrate two. Both are computed using a sliding window, to better control for differences in conference age. a) PC turnover: computed f ...
... to which conferences to submit their work. To facilitate such tasks, we have included a number of example metrics and queries in the repository7 , out of which we illustrate two. Both are computed using a sliding window, to better control for differences in conference age. a) PC turnover: computed f ...
Multi-Domain Integration with MOF and extended Triple
... requirements document contains information on includes and extends relationships which is needed by the use case document. In the class diagram document we represent both relationships as aggregations. Thus, the class diagram document does not provide this information. We avoid the problems from Fig ...
... requirements document contains information on includes and extends relationships which is needed by the use case document. In the class diagram document we represent both relationships as aggregations. Thus, the class diagram document does not provide this information. We avoid the problems from Fig ...
Do we need the closed-world assumption in knowledge
... data de nition languages corresponding to the relational or object-oriented model. In the late eighties inference in kl-one was shown to be undecidable [Schmidt-Schauss,1989]. Since then the emphasis in research has been on developing and investigating systems that are computationally well behaved, ...
... data de nition languages corresponding to the relational or object-oriented model. In the late eighties inference in kl-one was shown to be undecidable [Schmidt-Schauss,1989]. Since then the emphasis in research has been on developing and investigating systems that are computationally well behaved, ...
Fast Prefix Matching of Bounded Strings
... numbers that maps prefixes to nested intervals so that computing the longest prefix matching a string is equivalent to finding the shortest interval containing its corresponding integer value. We then present retries, a fast and compact data structure for LPM on general alphabets. Performance result ...
... numbers that maps prefixes to nested intervals so that computing the longest prefix matching a string is equivalent to finding the shortest interval containing its corresponding integer value. We then present retries, a fast and compact data structure for LPM on general alphabets. Performance result ...
ACC - Access Denied!
... consistency of processes and interfaces for information sharing. This portfolio management construct is used to influence investments, requirements, and acquisitions related to IT and NSS systems. Domains ensure necessary capabilities are planned (e.g., metadata catalogs, metadata registries, etc.) ...
... consistency of processes and interfaces for information sharing. This portfolio management construct is used to influence investments, requirements, and acquisitions related to IT and NSS systems. Domains ensure necessary capabilities are planned (e.g., metadata catalogs, metadata registries, etc.) ...
KTH | IV2038 Web-mining 7.5 credits
... The course intends to give an insight into techniques for data mining applied on Internet related data, and for what they can be used. After the course is finished the student should be able to: 1. Identify and differentiate between application areas for web content mining, web structure mining and ...
... The course intends to give an insight into techniques for data mining applied on Internet related data, and for what they can be used. After the course is finished the student should be able to: 1. Identify and differentiate between application areas for web content mining, web structure mining and ...
Difference Between Financial and Managerial Accounting (Financial
... for internal use the manager wants information that is relevant even if it is not completely objective or verifiable. By relevant, we mean appropriate for the problem at hand. For example, it is difficult to verify estimated sales volumes for a proposed new store at good Vibrations, Inc., but this i ...
... for internal use the manager wants information that is relevant even if it is not completely objective or verifiable. By relevant, we mean appropriate for the problem at hand. For example, it is difficult to verify estimated sales volumes for a proposed new store at good Vibrations, Inc., but this i ...
Quick Recovery For MS Backup
... If my computer is not booting, then how can QUICK RECOVERY access it? QUICK RECOVERY is to be run after booting the computer using a bootable floppy. Then QUICK RECOVERY bypasses the system area of the disk and physically searches for data Why cannot QUICK RECOVERY recover 100% data from large delet ...
... If my computer is not booting, then how can QUICK RECOVERY access it? QUICK RECOVERY is to be run after booting the computer using a bootable floppy. Then QUICK RECOVERY bypasses the system area of the disk and physically searches for data Why cannot QUICK RECOVERY recover 100% data from large delet ...
ppt
... • Handling multiple dimension rows that preserve history – 1st approach: Mapping table contains surrogate key for most current dimension row – 2nd approach: Mapping table lists all surrogate keys that were ever used for each natural key • Add additional columns to mapping table: ...
... • Handling multiple dimension rows that preserve history – 1st approach: Mapping table contains surrogate key for most current dimension row – 2nd approach: Mapping table lists all surrogate keys that were ever used for each natural key • Add additional columns to mapping table: ...
View File - UET Taxila
... storage, ensuring that all changes made prior to taking checkpoint have been written to long-term storage. DBMS may perform checkpoints automatically or in response to user application programs. Checkpoints should be taken frequently (several times an hour). In case of failures, it is often possible ...
... storage, ensuring that all changes made prior to taking checkpoint have been written to long-term storage. DBMS may perform checkpoints automatically or in response to user application programs. Checkpoints should be taken frequently (several times an hour). In case of failures, it is often possible ...
Using information about personal outcomes: Examples from the
... while touching on the third (which will be covered in more detail in a subsequent paper). In so doing, it demonstrates how the views of people using services can be applied to decisionmaking, while also including practitioner perspectives. Some uses of information, or changed understandings about th ...
... while touching on the third (which will be covered in more detail in a subsequent paper). In so doing, it demonstrates how the views of people using services can be applied to decisionmaking, while also including practitioner perspectives. Some uses of information, or changed understandings about th ...
Review on Video Mining
... it, and summarize the relationships identified between them. Technically, data mining is the method of finding correlations between information and patterns among dozens of fields in relational databases. [10]. Data warehousing is defined as a system of centralized data management and retrieval of i ...
... it, and summarize the relationships identified between them. Technically, data mining is the method of finding correlations between information and patterns among dozens of fields in relational databases. [10]. Data warehousing is defined as a system of centralized data management and retrieval of i ...
Ch18
... • Costs that are difficult to quantify, either because of the difficulty in precisely anticipating outcomes or the impossibility of predicting ultimate consequences. • Example: Work disruption due to changes in procedures. © 2001 South-Western Publishing ...
... • Costs that are difficult to quantify, either because of the difficulty in precisely anticipating outcomes or the impossibility of predicting ultimate consequences. • Example: Work disruption due to changes in procedures. © 2001 South-Western Publishing ...
Risk-Free Storage for the VMware View Mobile
... IT can’t be burdened with managing each VDI component separately. With VMware View, IT administrators can provision, protect, monitor, and manage desktops effortlessly. In addition, Nimble Storage proactive wellness features help IT preemptively avoid failures by providing real-time health analysis, ...
... IT can’t be burdened with managing each VDI component separately. With VMware View, IT administrators can provision, protect, monitor, and manage desktops effortlessly. In addition, Nimble Storage proactive wellness features help IT preemptively avoid failures by providing real-time health analysis, ...
Learning from the Past for Future Policy: Approaches to
... unit of catch. The catch rate in the Eritrean shark fishery decreased even more drastically than the Sudanese artisanal fisheries (Fig. 3b). Sharks are highly vulnerable to fishing because the high value of fins encourages fishers to keep fishing even when their abundance diminishes. Sharks also mat ...
... unit of catch. The catch rate in the Eritrean shark fishery decreased even more drastically than the Sudanese artisanal fisheries (Fig. 3b). Sharks are highly vulnerable to fishing because the high value of fins encourages fishers to keep fishing even when their abundance diminishes. Sharks also mat ...
Special Issue - Security
... threats from MFPs are often ignored entirely. While most companies might recognise some of the risks, these frequently are simply neglected, especially where sensitive documents and information are concerned. This is especially risky for any MFP or printer located in a public area, as this can be ac ...
... threats from MFPs are often ignored entirely. While most companies might recognise some of the risks, these frequently are simply neglected, especially where sensitive documents and information are concerned. This is especially risky for any MFP or printer located in a public area, as this can be ac ...
Lecture 19 - The University of Texas at Dallas
... Combine collections of data and infer information that is private Disease information from prescription data Military Action from Pizza delivery to pentagon Need to protect the associations and correlations between the data that are sensitive or private ...
... Combine collections of data and infer information that is private Disease information from prescription data Military Action from Pizza delivery to pentagon Need to protect the associations and correlations between the data that are sensitive or private ...
History of SQL
... sequential values which can be used to create primary key values. Finally XML is a format which is important because of its usefulness over the internet. It is widely used for the representation of data structures over the internet. The next revision of SQL was in 2006, and is known as SQL:2006. The ...
... sequential values which can be used to create primary key values. Finally XML is a format which is important because of its usefulness over the internet. It is widely used for the representation of data structures over the internet. The next revision of SQL was in 2006, and is known as SQL:2006. The ...
Informatica Data Quality - 10.1.1 - Using Random Sampling Option
... sampling of data, then the Data Integration Service pushes the SQL query to the database. For example, to select the random rows in the Customers table for profiling, a sample query is Select * from Customers SAMPLE (X) statement, where X is the approximate percentage of random rows. The query retur ...
... sampling of data, then the Data Integration Service pushes the SQL query to the database. For example, to select the random rows in the Customers table for profiling, a sample query is Select * from Customers SAMPLE (X) statement, where X is the approximate percentage of random rows. The query retur ...
1 Chapter 4 Data Analytics Introduction Sports teams have been
... Bears, employ specialists in areas such as sponsorship development analysis—to provide sponsorship ROI analytics to support the sponsorship sales staff. Others take advantage of consulting agencies, such as Turnkey Sports, for periodic projects and analyses. The point is that someone needs to be abl ...
... Bears, employ specialists in areas such as sponsorship development analysis—to provide sponsorship ROI analytics to support the sponsorship sales staff. Others take advantage of consulting agencies, such as Turnkey Sports, for periodic projects and analyses. The point is that someone needs to be abl ...