Regulatory Reporting System Technical White
... The system provides a variety of reports to assist the user with the task review process. These reports can be run within the context of an individual task, as noted above, or can be used as general query tools with input parameters specified by the user. The subjects of the reports include historic ...
... The system provides a variety of reports to assist the user with the task review process. These reports can be run within the context of an individual task, as noted above, or can be used as general query tools with input parameters specified by the user. The subjects of the reports include historic ...
Understanding Precious Metal Pricing
... OTC Markets: OTC markets are computer and telephone-linked networks of dealers who do not physically meet. Clients in OTC markets trade on a principal-to-principal basis, which means that all risks, including those of credit, are taken on by the transaction’s two parties. Financial institutions act ...
... OTC Markets: OTC markets are computer and telephone-linked networks of dealers who do not physically meet. Clients in OTC markets trade on a principal-to-principal basis, which means that all risks, including those of credit, are taken on by the transaction’s two parties. Financial institutions act ...
MySpacePoster
... databases, and other transient files. The novel feature of the MySpace system is that the scratch space is geographically dispersed, typically with stores at the various sites hosting AstroGrid services. Users can access and navigate MySpace seamlessly and easily, the network details of the individu ...
... databases, and other transient files. The novel feature of the MySpace system is that the scratch space is geographically dispersed, typically with stores at the various sites hosting AstroGrid services. Users can access and navigate MySpace seamlessly and easily, the network details of the individu ...
Review For Exam 2
... delete Marketing-2, but you want to keep all the files that are currently in the folder. You plan to copy all the files in Marketting-2 into the Marketing folder before deleting Marketing-2. You want these files to remain compressed. However, you do not want to compress any existing files in Marketi ...
... delete Marketing-2, but you want to keep all the files that are currently in the folder. You plan to copy all the files in Marketting-2 into the Marketing folder before deleting Marketing-2. You want these files to remain compressed. However, you do not want to compress any existing files in Marketi ...
Towards Social Webtops Using Semantic Wiki
... applications. For example, TW Wiki may need to hide internal group meeting notes from non-group members while keeping all publication publicly visible. In what follows, we discuss three important personalization issues with some initial solutions: • Ontology Personalization. A nice feature offered b ...
... applications. For example, TW Wiki may need to hide internal group meeting notes from non-group members while keeping all publication publicly visible. In what follows, we discuss three important personalization issues with some initial solutions: • Ontology Personalization. A nice feature offered b ...
- Physik Instrumente
... Some years ago, silicon-photonics was already an important topic with regard to fast telecommunication solutions, today the focus lies more on datacom, implying that optical interconnect is not only used for long-haul data transmission, but also for on-chip communication, chip-to-chip, chip-toboard, ...
... Some years ago, silicon-photonics was already an important topic with regard to fast telecommunication solutions, today the focus lies more on datacom, implying that optical interconnect is not only used for long-haul data transmission, but also for on-chip communication, chip-to-chip, chip-toboard, ...
Slide 1
... WHAT IS PLAN FREEZING? • Plan freezing creates a plan guide: • Plan guide contains hints or a full query plan • Plan guide is attached to a specific Transact-SQL statement ...
... WHAT IS PLAN FREEZING? • Plan freezing creates a plan guide: • Plan guide contains hints or a full query plan • Plan guide is attached to a specific Transact-SQL statement ...
4.1
... Higher education sector Abroad • Business enterprise: • Enterprises within the same group ...
... Higher education sector Abroad • Business enterprise: • Enterprises within the same group ...
Investigation Report Unfair collection of personal data by the use of
... 27. Recruitment media are not data users, and hence the Commissioner has no jurisdiction to impose any requirement on them in managing the privacy issue of Blind Ads. However, they are in the best position to act as gatekeepers to prevent unfair collection of personal data through Blind Ads. Indeed, ...
... 27. Recruitment media are not data users, and hence the Commissioner has no jurisdiction to impose any requirement on them in managing the privacy issue of Blind Ads. However, they are in the best position to act as gatekeepers to prevent unfair collection of personal data through Blind Ads. Indeed, ...
Full Packet Inspection - TERENA Networking Conference 2005
... succeed in representing or expressing something intangible; "capture the essence of Spring"; "capture an idea" attract; cause to be enamored; "She captured all the men's hearts" the act of forcibly dispossessing an owner of property a process whereby a star or planet holds an object in its gravitati ...
... succeed in representing or expressing something intangible; "capture the essence of Spring"; "capture an idea" attract; cause to be enamored; "She captured all the men's hearts" the act of forcibly dispossessing an owner of property a process whereby a star or planet holds an object in its gravitati ...
Paper_Biosytems_2002
... particle; the movement of those particles is The experimental evidence that is currently available described in n-dimensional space, where n is the requires further, in-depth analysis in order to extract number of spike trains under investigation. All inherent information. Analysis of multi-dimensio ...
... particle; the movement of those particles is The experimental evidence that is currently available described in n-dimensional space, where n is the requires further, in-depth analysis in order to extract number of spike trains under investigation. All inherent information. Analysis of multi-dimensio ...
Draft CL
... Paper on Marine Knowledge which raises several issues regarding EMODnet. In his presentation, Iain Shepherd highlighted some of them. The consultation will end on 15th December 2012. Implementation of Marine Knowledge 2020 will depend on the budget envelope for the European Maritime and Fisheries Fu ...
... Paper on Marine Knowledge which raises several issues regarding EMODnet. In his presentation, Iain Shepherd highlighted some of them. The consultation will end on 15th December 2012. Implementation of Marine Knowledge 2020 will depend on the budget envelope for the European Maritime and Fisheries Fu ...
p2p
... • One of the main problem at the heart of any P2P system is the cost of data placement • The cost associated with data placement is more like the issue of view materialization in database (warehouses) which is an hotly research topic in the database community. P2P system design would benefit greatly ...
... • One of the main problem at the heart of any P2P system is the cost of data placement • The cost associated with data placement is more like the issue of view materialization in database (warehouses) which is an hotly research topic in the database community. P2P system design would benefit greatly ...
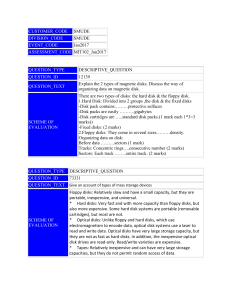
CUSTOMER_CODE SMUDE DIVISION_CODE SMUDE
... remainder of x divided by N is what is returned. Once this hash value has been determined, the whole piece of data is then sorted into a bucket with a number of other data entries with the same hash value. These buckets usually have a static size as well and they each have overflow buckets in case t ...
... remainder of x divided by N is what is returned. Once this hash value has been determined, the whole piece of data is then sorted into a bucket with a number of other data entries with the same hash value. These buckets usually have a static size as well and they each have overflow buckets in case t ...
CMX831 - Teleste
... remote controlled systems. The unit can be installed into standard 19-inch installation cabinet. Stand-alone installation directly to a wall is also possible. SETTINGS BEFORE INSTALLATION The unit has several settings for video, audio, data and current loop/contact closure operations that must be de ...
... remote controlled systems. The unit can be installed into standard 19-inch installation cabinet. Stand-alone installation directly to a wall is also possible. SETTINGS BEFORE INSTALLATION The unit has several settings for video, audio, data and current loop/contact closure operations that must be de ...
AD4301161166
... discount increases number of product sold also is growing fast, and with this growth companies are increases but at some point when product discount willing to spend more on improving the online increases too much, product sale automatically experience, our research work helps the executive decrease ...
... discount increases number of product sold also is growing fast, and with this growth companies are increases but at some point when product discount willing to spend more on improving the online increases too much, product sale automatically experience, our research work helps the executive decrease ...
SAP R/3`s ability to support a number of different databases
... a lot of tasks normally associated with an MVS environment. For example, SAP provides a security model within the application, negating the need to maintain security beyond what is necessary for systems staff and the tasks and processes involved. This in itself is quite simple and straightforward, a ...
... a lot of tasks normally associated with an MVS environment. For example, SAP provides a security model within the application, negating the need to maintain security beyond what is necessary for systems staff and the tasks and processes involved. This in itself is quite simple and straightforward, a ...
Building an Effective Stress Testing Process
... lending, risk, retail, etc. Captured data should be disseminated between all departments for monitoring and use. Lending should have quick access to credit data and risk should communicate frequently with lending and retail to develop appropriate frameworks. ...
... lending, risk, retail, etc. Captured data should be disseminated between all departments for monitoring and use. Lending should have quick access to credit data and risk should communicate frequently with lending and retail to develop appropriate frameworks. ...
Program Planning for Maximum Impact
... • Knowing the unit of analysis • Understanding how accurate the data are • Understanding what the stats you’ve created mean and imply (e.g., population % change ’90-’00: represents in-migration or changes to the birth and death rates?) • Understanding the strengths and limitations of the stats ...
... • Knowing the unit of analysis • Understanding how accurate the data are • Understanding what the stats you’ve created mean and imply (e.g., population % change ’90-’00: represents in-migration or changes to the birth and death rates?) • Understanding the strengths and limitations of the stats ...
PDF of this page
... This course deals with modern technologies for data analysis. Handson exercises for data retrieval, data visualization and predictive analytics will be carried out using up-to-date methodologies and software tools. The full data mining life cycle will be covered from recognizing business problems an ...
... This course deals with modern technologies for data analysis. Handson exercises for data retrieval, data visualization and predictive analytics will be carried out using up-to-date methodologies and software tools. The full data mining life cycle will be covered from recognizing business problems an ...
The promise of graph databases in public health is web-scale discovery.
... 1 Structured query language, or SQL, is the dominant query language associated with relational databases. NoSQL stands for not only structured query language. In practice, the term NoSQL is used loosely to refer to non-relational databases designed for distributed environments, rather than the ass ...
... 1 Structured query language, or SQL, is the dominant query language associated with relational databases. NoSQL stands for not only structured query language. In practice, the term NoSQL is used loosely to refer to non-relational databases designed for distributed environments, rather than the ass ...
Title: RePEc and Socionet - Open Library Society, Inc.
... During ten years in Russia, because of economic crisis, there was a permanent problem with accessing new research publications and materials. Libraries as many other organizations in Russia could not provide cheap and qualitative services for academic institutions. In situation of crisis researchers ...
... During ten years in Russia, because of economic crisis, there was a permanent problem with accessing new research publications and materials. Libraries as many other organizations in Russia could not provide cheap and qualitative services for academic institutions. In situation of crisis researchers ...
JV3118261831
... 1. Name of the relation say R 2. Number of attributes in R 3. Set of functional dependencies of R. A provision is made to find the set of all the possible candidate keys of R, Primary key and Super key. The tool computes Prime and Non-Prime attributes of R based on the CKs generated [5]. 5.2.1 Advan ...
... 1. Name of the relation say R 2. Number of attributes in R 3. Set of functional dependencies of R. A provision is made to find the set of all the possible candidate keys of R, Primary key and Super key. The tool computes Prime and Non-Prime attributes of R based on the CKs generated [5]. 5.2.1 Advan ...
PDF 181 KB - Ingenico Group
... merchants are now able to accept EMV debit transactions. Without Common AID, EMV debit transactions process as signature-based transactions, which can significantly impact interchange costs. “EMV tip adjust and Common AID are critical features for restaurants and other merchants, as they’re providin ...
... merchants are now able to accept EMV debit transactions. Without Common AID, EMV debit transactions process as signature-based transactions, which can significantly impact interchange costs. “EMV tip adjust and Common AID are critical features for restaurants and other merchants, as they’re providin ...
'How Do I Love Thee? Let Me Count the Ways.' SAS® Software as a Part of the Corporate Information Factory
... External data is that which originates outside the organization. An example is proprietary data provided by a credit-reporting agency such as Experian. External data usually requires modification or addition of a key structure to make it meaningful within the CIF. Reference data is generated interna ...
... External data is that which originates outside the organization. An example is proprietary data provided by a credit-reporting agency such as Experian. External data usually requires modification or addition of a key structure to make it meaningful within the CIF. Reference data is generated interna ...