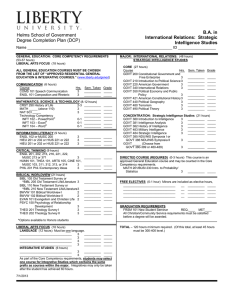
B.A. in International Relations: Strategic Intelligence Studies Helms
... FRSM 101 New Student Seminar REQ.____ MET____ All Christian/Community Service requirements must be satisfied before a degree will be awarded. ...
... FRSM 101 New Student Seminar REQ.____ MET____ All Christian/Community Service requirements must be satisfied before a degree will be awarded. ...
Introduction to MS Access
... table. This is known as entity integrity. • If you do not enter a value for a field, you have actually given the field a null value. You cannot give a null value to the primary key field. ...
... table. This is known as entity integrity. • If you do not enter a value for a field, you have actually given the field a null value. You cannot give a null value to the primary key field. ...
Principles of Auditing an Introduction to ISAs Ch. 9
... ? fixed vs. variable ? level of detail (aggregation) ? reliability of the data [Hayes, Dassen, Schilder and Wallage, Principles of Auditing An Introduction to ISAs, edition 2.1] © Pearson Education Limited 2007 ...
... ? fixed vs. variable ? level of detail (aggregation) ? reliability of the data [Hayes, Dassen, Schilder and Wallage, Principles of Auditing An Introduction to ISAs, edition 2.1] © Pearson Education Limited 2007 ...
data model
... 1) Conceptual (high-level, semantic) data models: Provide concepts that are close to the way many users perceive data. 2) Physical (low-level, internal) data models: Provide concepts that describe the details of how data is stored in the computer. 3) Implementation (representational) data models: Pr ...
... 1) Conceptual (high-level, semantic) data models: Provide concepts that are close to the way many users perceive data. 2) Physical (low-level, internal) data models: Provide concepts that describe the details of how data is stored in the computer. 3) Implementation (representational) data models: Pr ...
MUFG to exhibit at CEATEC Japan 2016
... to swiftly adopt Fintech and through Open Innovation create highly innovative financial services. ...
... to swiftly adopt Fintech and through Open Innovation create highly innovative financial services. ...
Transferring SAS Datasets from z/OS to SQL Server Databases
... ❷Note that ‘05’x is the tab character in EBCDIC code. Then we use the FTP tool to download the text file to our PC. We have chosen text files instead of SAS transportable files because (1) the file size is smaller for a text file compared against a SAS transportable file; (2) properly formatted text ...
... ❷Note that ‘05’x is the tab character in EBCDIC code. Then we use the FTP tool to download the text file to our PC. We have chosen text files instead of SAS transportable files because (1) the file size is smaller for a text file compared against a SAS transportable file; (2) properly formatted text ...
5.10.3. Storage Area Network
... Implemented via remote procedure calls (RPCs) between host and storage The remote procedure calls RPCs are carried via TCP or UDP over an IP network-usually the same local area network (LAN) that carries all data traffic to the clients. The NAS unit is usually implemented as a RAID array with softwa ...
... Implemented via remote procedure calls (RPCs) between host and storage The remote procedure calls RPCs are carried via TCP or UDP over an IP network-usually the same local area network (LAN) that carries all data traffic to the clients. The NAS unit is usually implemented as a RAID array with softwa ...
Citi® Commercial Cards
... management, and deliver critical business intelligence. Whether your business is a local, regional or global enterprise, success depends on knowing how, when and where your organisation spends its money. ...
... management, and deliver critical business intelligence. Whether your business is a local, regional or global enterprise, success depends on knowing how, when and where your organisation spends its money. ...
Enterprise Applications - Texas Tech University Departments
... Lecture 26: Enterprise Applications Enterprise Applications of GIS - enterprise applications of GIS are usually designed to manage assets and organization work flows Understanding the GIS Job Market - in 2004 the U.S. Department of Labor identified three new high-growth emerging technologies - they ...
... Lecture 26: Enterprise Applications Enterprise Applications of GIS - enterprise applications of GIS are usually designed to manage assets and organization work flows Understanding the GIS Job Market - in 2004 the U.S. Department of Labor identified three new high-growth emerging technologies - they ...
THE CFO`S 10-STEP GUIDE TO SLEEPING
... promise and over deliver. Failure to adequately prepare can result in misses from two sources. The first is finance and management not being on the same page regarding an investor relations communication philosophy. Entrepreneurs are born with aggressive DNA and this is one area where this trait can ...
... promise and over deliver. Failure to adequately prepare can result in misses from two sources. The first is finance and management not being on the same page regarding an investor relations communication philosophy. Entrepreneurs are born with aggressive DNA and this is one area where this trait can ...
Case study ADP AutomAting the technicAl SuPPort
... Platform,which is at the center of every SupportSoft solution. For example, the Resolution Suite can automatically provide the representative with comprehensive information about the customer’s technical issue at the time of the call, which can improve problem resolution and help reduce the need for ...
... Platform,which is at the center of every SupportSoft solution. For example, the Resolution Suite can automatically provide the representative with comprehensive information about the customer’s technical issue at the time of the call, which can improve problem resolution and help reduce the need for ...
Capping the Nation`s Broadband Future?
... platforms and rich content from voice-over-IP and video conferencing connect family and friends around the world at little or no cost, high quality video streams facilitate online learning and digital education along with new ways to view movies and TV shows, and a host of platforms and applications ...
... platforms and rich content from voice-over-IP and video conferencing connect family and friends around the world at little or no cost, high quality video streams facilitate online learning and digital education along with new ways to view movies and TV shows, and a host of platforms and applications ...
Quantitative modeling of operational risk losses when combining
... knowledge coming from external data. First, one has data that originate from other companies or even other branches (for instance, insurance companies have so few observations that they need to borrow information from banks) that are related to the internal operational risk data of interest—but only ...
... knowledge coming from external data. First, one has data that originate from other companies or even other branches (for instance, insurance companies have so few observations that they need to borrow information from banks) that are related to the internal operational risk data of interest—but only ...
Using CAM-equipped Mobile Phones for Procurement
... Agricultural procurement refers to the collection and processing of deliveries from individual producers. Akashganga is a project that automates the milk collection process at dairy cooperatives in India [18]. A digital scale is connected to a PC that maintains local transaction records and prints p ...
... Agricultural procurement refers to the collection and processing of deliveries from individual producers. Akashganga is a project that automates the milk collection process at dairy cooperatives in India [18]. A digital scale is connected to a PC that maintains local transaction records and prints p ...
PostgreSQL ORDBMS mod
... arguments they take are different. In other words, function names can be overloaded. When a query is executed, the server will determine which function to call from the data types and the number of the provided arguments. ...
... arguments they take are different. In other words, function names can be overloaded. When a query is executed, the server will determine which function to call from the data types and the number of the provided arguments. ...
No Slide Title
... – Small tiger team formed to study this issue and prototype at least one approach. – Prototyping OGC Web Map Server (WMS) and Web Coverage Server (WCS) on the Grid. – Will generate Cookbook page on putting WMS and WCS on the Grid. ...
... – Small tiger team formed to study this issue and prototype at least one approach. – Prototyping OGC Web Map Server (WMS) and Web Coverage Server (WCS) on the Grid. – Will generate Cookbook page on putting WMS and WCS on the Grid. ...
The metaphysics and epistemology of causality Prof. Jan
... reliable results. In this talk, I introduce Joint Causal Inference (JCI), a novel framework for causal discovery that elegantly unifies both approaches. JCI combines the best of two worlds, and thereby enables more reliable automatic causal discovery from big ...
... reliable results. In this talk, I introduce Joint Causal Inference (JCI), a novel framework for causal discovery that elegantly unifies both approaches. JCI combines the best of two worlds, and thereby enables more reliable automatic causal discovery from big ...
An Intelligent System for Retrieval and Mining of Audiovisual
... efficient search algorithms have been developed for either media, the need for abstract data presentation and summarization still exists [1]. Moreover, retrieval systems should be capable of providing the user with additional information related to the specific subject of the query, as well as sugge ...
... efficient search algorithms have been developed for either media, the need for abstract data presentation and summarization still exists [1]. Moreover, retrieval systems should be capable of providing the user with additional information related to the specific subject of the query, as well as sugge ...
A Marketing Authorisation Application (MAA) can be the same
... the acceptance of different approvable endpoints, which may or not be connected. There may also be differences in favoured analytical techniques, with the EMA statisticians tending to have a more flexible and pragmatic approach than their transatlantic cousins. FDA and EMA have for some years operat ...
... the acceptance of different approvable endpoints, which may or not be connected. There may also be differences in favoured analytical techniques, with the EMA statisticians tending to have a more flexible and pragmatic approach than their transatlantic cousins. FDA and EMA have for some years operat ...
Old Dominion Freight Lines
... competitive rates for new business that ensure profitability, especially in an environment of rapidly rising fuel costs. “When you have an accurate picture of all the costs associated with hauling LTL freight, you are more likely to be profitable for individual customers and loads. LTL/CIS provides ...
... competitive rates for new business that ensure profitability, especially in an environment of rapidly rising fuel costs. “When you have an accurate picture of all the costs associated with hauling LTL freight, you are more likely to be profitable for individual customers and loads. LTL/CIS provides ...
to get the file
... Digital spatial layers are already developed for watershed and MGNREGA in many States like Andhra Pradesh, Orissa, Karnataka, Rajasthan, Himachal Pradesh, Chhattisgarh, Maharashtra etc. State Govt. may assess the Availability of the above mentioned layers, which could be used for the GIS application ...
... Digital spatial layers are already developed for watershed and MGNREGA in many States like Andhra Pradesh, Orissa, Karnataka, Rajasthan, Himachal Pradesh, Chhattisgarh, Maharashtra etc. State Govt. may assess the Availability of the above mentioned layers, which could be used for the GIS application ...
Cluster Analysis vs. Market Segmentation
... • Help marketers discover distinct groups in their customer bases, and then use this knowledge to develop targeted marketing programs • The underlying definition of cluster analysis procedures mimic the goals of market segmentation: – to identify groups of respondents that minimizes differences amon ...
... • Help marketers discover distinct groups in their customer bases, and then use this knowledge to develop targeted marketing programs • The underlying definition of cluster analysis procedures mimic the goals of market segmentation: – to identify groups of respondents that minimizes differences amon ...
a MS Powerpoint version of "Cluster Analysis vs. Market
... • Help marketers discover distinct groups in their customer bases, and then use this knowledge to develop targeted marketing programs • The underlying definition of cluster analysis procedures mimic the goals of market segmentation: – to identify groups of respondents that minimizes differences amon ...
... • Help marketers discover distinct groups in their customer bases, and then use this knowledge to develop targeted marketing programs • The underlying definition of cluster analysis procedures mimic the goals of market segmentation: – to identify groups of respondents that minimizes differences amon ...























