Transfer Program in the 1997 Cohort of the NLSY
... Spells: An Analysis Using Flow and Stock Samples,” Review of Economics and Statistics November 1998 80(4) 667-674. ...
... Spells: An Analysis Using Flow and Stock Samples,” Review of Economics and Statistics November 1998 80(4) 667-674. ...
News from ISIS Papyrus Software
... As more and more companies rely on the World Wide Web to serve customers, agents, and their own employees, Papyrus WebPortal, another featured product at AIIM/OnDemand expo, will become invaluable. Papyrus WebPortal provides a unified document interface and single entry point for any kind of busines ...
... As more and more companies rely on the World Wide Web to serve customers, agents, and their own employees, Papyrus WebPortal, another featured product at AIIM/OnDemand expo, will become invaluable. Papyrus WebPortal provides a unified document interface and single entry point for any kind of busines ...
Why Your Library Should Move to Ex Libris Alma
... For local needs and unique collections, Alma’s hybrid model of metadata management supports both community and local data. Libraries working with Alma can benefit from shared data while still retaining full control when it supports the needs of their users. To describe unique digital collections, Al ...
... For local needs and unique collections, Alma’s hybrid model of metadata management supports both community and local data. Libraries working with Alma can benefit from shared data while still retaining full control when it supports the needs of their users. To describe unique digital collections, Al ...
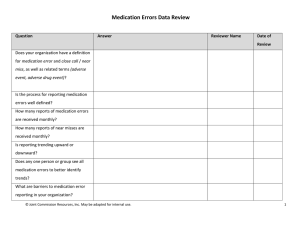
Medication Errors Data Review
... How many reports of medication errors are received monthly? How many reports of near misses are received monthly? Is reporting trending upward or downward? Does any one person or group see all medication errors to better identify trends? What are barriers to medication error reporting in your organi ...
... How many reports of medication errors are received monthly? How many reports of near misses are received monthly? Is reporting trending upward or downward? Does any one person or group see all medication errors to better identify trends? What are barriers to medication error reporting in your organi ...
Multi-Drive Libraries, Virtual Tape Libraries (VTL
... For as long as there has been data stored on computers, the people responsible for managing those computers have been aware that backup copies of the data were important. Magnetic tape has always been the defacto standard for making and storing those copies. Relative high capacity, removability, and ...
... For as long as there has been data stored on computers, the people responsible for managing those computers have been aware that backup copies of the data were important. Magnetic tape has always been the defacto standard for making and storing those copies. Relative high capacity, removability, and ...
Powerpoint
... available flights on corporate jets – Companies phone in available seats • They want to know about interested passengers ...
... available flights on corporate jets – Companies phone in available seats • They want to know about interested passengers ...
Moving to a fourth generation: SPC that lets you
... has set the stage for the next leap forward. Before thinking about that leap, it is instructive to consider how the use of SPC has evolved. While none of this may be new information, it is important to view the sometimes small changes that have moved SPC forward and to understand the “big picture” o ...
... has set the stage for the next leap forward. Before thinking about that leap, it is instructive to consider how the use of SPC has evolved. While none of this may be new information, it is important to view the sometimes small changes that have moved SPC forward and to understand the “big picture” o ...
Executive Summary
... The Cisco e-discovery system architecture can be grown easily in response to future needs. A SAN management application allows users to “see” data as one large volume that can be increased in size by simply adding data disks. The system is highly secure. The entire fabric of the SAN is smoothly inte ...
... The Cisco e-discovery system architecture can be grown easily in response to future needs. A SAN management application allows users to “see” data as one large volume that can be increased in size by simply adding data disks. The system is highly secure. The entire fabric of the SAN is smoothly inte ...
Compile-time meta
... the complete BTC data set : 39h •The resulting index & data: 1TB. •One simple entity search: 16s. •The complete process of property-based data access may take up to hours as multiple queries, entity and property retrievals are being performed. •Computing the quality, principal components, latent typ ...
... the complete BTC data set : 39h •The resulting index & data: 1TB. •One simple entity search: 16s. •The complete process of property-based data access may take up to hours as multiple queries, entity and property retrievals are being performed. •Computing the quality, principal components, latent typ ...
How to design your MDDB
... One of the most valuable add-ons to SAS6.12 is the introduction of the multi-dimensional database (MDDB). Although the advantages of the MDDB are clear to all, i.e. better performance while accessing enormous detailed data, still a lot of people fail to bring them in practice. This can mainly be put ...
... One of the most valuable add-ons to SAS6.12 is the introduction of the multi-dimensional database (MDDB). Although the advantages of the MDDB are clear to all, i.e. better performance while accessing enormous detailed data, still a lot of people fail to bring them in practice. This can mainly be put ...
Chap 6: DB Security File - e
... users into various security classes (or levels) then implementing the appropriate security policy. For example User at Level 1 can see data in level 1 and lower (level 0), but not higher (Level 2) An extension of this is role-based security Typical security classes are top secret (TS), sec ...
... users into various security classes (or levels) then implementing the appropriate security policy. For example User at Level 1 can see data in level 1 and lower (level 0), but not higher (Level 2) An extension of this is role-based security Typical security classes are top secret (TS), sec ...
caCORE Runtime Architecture
... The caCORE SDK is based on a software development paradigm that starts with an abstract model of the entities represented in a particular application. Real-world examples of such entities include identified peptides in an MS2 run or microarray test results. Entities are usually related to other enti ...
... The caCORE SDK is based on a software development paradigm that starts with an abstract model of the entities represented in a particular application. Real-world examples of such entities include identified peptides in an MS2 run or microarray test results. Entities are usually related to other enti ...
CChandler_data_update
... Ocean Carbon and Biogeochemistry • OCB collaboratory one year proposal funded by NSF in May 2005 • PIs: Dave Glover, Ken Buesseler, Scott Doney • original proposal was entitled “Coordination and Data Management for Ocean Carbon Cycle Research » data management support for targeted programs to impro ...
... Ocean Carbon and Biogeochemistry • OCB collaboratory one year proposal funded by NSF in May 2005 • PIs: Dave Glover, Ken Buesseler, Scott Doney • original proposal was entitled “Coordination and Data Management for Ocean Carbon Cycle Research » data management support for targeted programs to impro ...
ZR Reporting
... Dashboard and visualisation tools are essential for providing a common view of what’s important to your organization or team. These tools enhance visibility into organizational strategy, align actions with strategy and allow users to track KPIs, assign goals and collaborate and share knowledge. ...
... Dashboard and visualisation tools are essential for providing a common view of what’s important to your organization or team. These tools enhance visibility into organizational strategy, align actions with strategy and allow users to track KPIs, assign goals and collaborate and share knowledge. ...
intergraph® vegetation management
... across the Northeast U.S. and Southeast Canada lost power. ...
... across the Northeast U.S. and Southeast Canada lost power. ...
GLMOUT - A SAS Program to Read PROC GLM Output
... a temporary data set and concatenated back into the stream of SAS code. In this way we avoid having too many or too few variables to hold the information or asking the user to follow detailed instructions for modifying code. Separate data sets are used to hold analysis of variance, ordinary means, l ...
... a temporary data set and concatenated back into the stream of SAS code. In this way we avoid having too many or too few variables to hold the information or asking the user to follow detailed instructions for modifying code. Separate data sets are used to hold analysis of variance, ordinary means, l ...
Advanced Database Management Systems
... Any changes made to the syllabus shall be clearly documented with a change history log. This shall include the latest version number, date of the amendment and the changes made. The purpose is to identify quickly what changes have been made. Version Number V1.0 V 2.0 ...
... Any changes made to the syllabus shall be clearly documented with a change history log. This shall include the latest version number, date of the amendment and the changes made. The purpose is to identify quickly what changes have been made. Version Number V1.0 V 2.0 ...
A Citizen Oriented E-government Maturity Model
... 1. Phase 1: The cultivation: shelters horizontal and vertical integration within government, limited use of front-end systems for customer services, and adoption and use of Intranet within government. There can be elements of self-service but most often in the form of PDF files that can be download ...
... 1. Phase 1: The cultivation: shelters horizontal and vertical integration within government, limited use of front-end systems for customer services, and adoption and use of Intranet within government. There can be elements of self-service but most often in the form of PDF files that can be download ...
Introduction to SAS/ACCESS Software
... descriptors and can specifY a subset of the columns specified in an ACCESS descriptor. They can define different SAS variable names and formats than what is prescribed In the ACCESS descriptor. View descriptors are referenced as if they were a SAS data set and can specify the order which the informa ...
... descriptors and can specifY a subset of the columns specified in an ACCESS descriptor. They can define different SAS variable names and formats than what is prescribed In the ACCESS descriptor. View descriptors are referenced as if they were a SAS data set and can specify the order which the informa ...
Introducing Enterprise NoSQL
... universal index, range index, geospatial index, and triple index—all designed so that developers can ask harder questions and get faster responses. Handle historical data along two different timelines, making it possible to rewind the information “as it actually was” in combination with “as it was r ...
... universal index, range index, geospatial index, and triple index—all designed so that developers can ask harder questions and get faster responses. Handle historical data along two different timelines, making it possible to rewind the information “as it actually was” in combination with “as it was r ...
Rendering scenes
... Models are stored in flat files With thanks to Andrew Borley, Jonathan Davies, Neil Hardman and George Hicken of IBM UK. ...
... Models are stored in flat files With thanks to Andrew Borley, Jonathan Davies, Neil Hardman and George Hicken of IBM UK. ...
METHODS IN BEHAVIORAL RESEARCH
... over a period of time, using a variety of techniques to collect information Used to describe and understand how people in a social or cultural setting live, work, and experience the setting Used to observe people involved with sports teams or other social settings, at work or animals in their natu ...
... over a period of time, using a variety of techniques to collect information Used to describe and understand how people in a social or cultural setting live, work, and experience the setting Used to observe people involved with sports teams or other social settings, at work or animals in their natu ...