(EPB) Enterprise Planning and Budgeting
... Control each plan’s time frame and level of detail Pick process tasks from a library Define process schedule and versions to retain Integrate to all data sources using open interface tables Create multidimensional crosstabs and graphs, covering historical, current and projected data Rota ...
... Control each plan’s time frame and level of detail Pick process tasks from a library Define process schedule and versions to retain Integrate to all data sources using open interface tables Create multidimensional crosstabs and graphs, covering historical, current and projected data Rota ...
Blood Donor Database
... give delhi in different forms like , DELHI, delhi, Delhi . So the query to search on the basis of region should be made case sensitive by using available functions. (Extra points on using xml functions) x.Non-members can also look for blood donors or Bloods in any particular banks and then do quick ...
... give delhi in different forms like , DELHI, delhi, Delhi . So the query to search on the basis of region should be made case sensitive by using available functions. (Extra points on using xml functions) x.Non-members can also look for blood donors or Bloods in any particular banks and then do quick ...
Temporal Data Management
... of the most current version of the database. The dominant approach is one of data being updated, deleted, and inserted in order to maintain the current version. In reality, many applications need to maintain a complete record of operations over the database. This is quite obvious in most business ap ...
... of the most current version of the database. The dominant approach is one of data being updated, deleted, and inserted in order to maintain the current version. In reality, many applications need to maintain a complete record of operations over the database. This is quite obvious in most business ap ...
Data integration and transformation o How to change the data from
... then we get distinct classes, two groups, and then in each group attribute a1 is used to determine the class label. Whereas n other group attribute a6is used to determine the class label, so therefore if we combine all the attribute in this tree we get a set of three attributea1, a4,a6, which is a r ...
... then we get distinct classes, two groups, and then in each group attribute a1 is used to determine the class label. Whereas n other group attribute a6is used to determine the class label, so therefore if we combine all the attribute in this tree we get a set of three attributea1, a4,a6, which is a r ...
INTRODUCTION OF 3D INFORMATION IN URBAN GIS : A CONCEPTUAL...
... applications are classified in two categories : the first one includes applications already studied in 3D (few town planning studies) and new applications where 3D is a crucial parameters (mobile phone propagation signal); the second one gathers other applications. The former one allows the formalis ...
... applications are classified in two categories : the first one includes applications already studied in 3D (few town planning studies) and new applications where 3D is a crucial parameters (mobile phone propagation signal); the second one gathers other applications. The former one allows the formalis ...
2015-16 Pre-Approved Electives for MS in Applied Economics and Finance
... 2015-16 Pre-Approved Electives for MS in Applied Economics and Finance Winter 2016 Economics ...
... 2015-16 Pre-Approved Electives for MS in Applied Economics and Finance Winter 2016 Economics ...
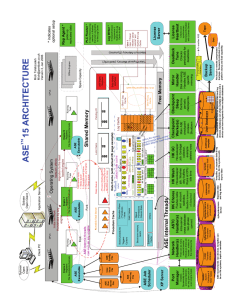
Shared Memory ASE Internal Threads
... devices. Databases can share multiple devices and a device can have fragments from multiple databases ...
... devices. Databases can share multiple devices and a device can have fragments from multiple databases ...
Web Map Layers for insurance
... Web Map Layers for Insurance has been designed for insurance companies wishing to improve their business processes by sharing location intelligence throughout their organisation via the web. It not only provides a valuable geographical window into insurance data, but also provides powerful analysis ...
... Web Map Layers for Insurance has been designed for insurance companies wishing to improve their business processes by sharing location intelligence throughout their organisation via the web. It not only provides a valuable geographical window into insurance data, but also provides powerful analysis ...
Recruitment - Job Description Template
... University from non-core teaching and research activities. It builds on, and includes, the successful London Artscom Ltd (short course), UAL Awarding Body, Language Centre, college and research based enterprise, business and innovation operations. Academic Enterprise not only integrates and bolsters ...
... University from non-core teaching and research activities. It builds on, and includes, the successful London Artscom Ltd (short course), UAL Awarding Body, Language Centre, college and research based enterprise, business and innovation operations. Academic Enterprise not only integrates and bolsters ...
Lecture 21 - The University of Texas at Dallas
... is not sufficient to say, our data is correct, because we store all interactions in a separate audit log.“ The integrity of the audit log itself must also be guaranteed. This paper proposes mechanisms within a database management system (DBMS), based on cryptographically strong one-way hash function ...
... is not sufficient to say, our data is correct, because we store all interactions in a separate audit log.“ The integrity of the audit log itself must also be guaranteed. This paper proposes mechanisms within a database management system (DBMS), based on cryptographically strong one-way hash function ...
DOE06Proposal25Sep2006CMS
... The faculty members of the Relativistic Heavy Ion group at Vanderbilt are Professor Charles Maguire, Professor Victoria Greene (promoted to full professor in spring, 2006), and Assistant Professor Julia Velkovska. In addition, the current members of the Relativistic Heavy Ion group at Vanderbilt inc ...
... The faculty members of the Relativistic Heavy Ion group at Vanderbilt are Professor Charles Maguire, Professor Victoria Greene (promoted to full professor in spring, 2006), and Assistant Professor Julia Velkovska. In addition, the current members of the Relativistic Heavy Ion group at Vanderbilt inc ...
SAS Text Miner: Introduction and Case Study
... One of the data items collected from customers is their job titles. This information is entered into the database; on the basis of the job title, the company uses an in-house procedure to create a text variable referred to as the Key Player Description. For example, a job title such as “Director of ...
... One of the data items collected from customers is their job titles. This information is entered into the database; on the basis of the job title, the company uses an in-house procedure to create a text variable referred to as the Key Player Description. For example, a job title such as “Director of ...
Arizona Education Technology Standards
... foolproof means for enforcing the provisions of local acceptable use policies. ...
... foolproof means for enforcing the provisions of local acceptable use policies. ...
HHU at SemEval-2017 Task 5: Fine-Grained Sentiment Analysis on
... one vector. Instead, every word vector is represented by a line of a matrix with a fixed count so that every matrix for a message has the same shape. This representation is optimized for the recurrent neural network because it can process one line at a single time step. To use the matrix features in ...
... one vector. Instead, every word vector is represented by a line of a matrix with a fixed count so that every matrix for a message has the same shape. This representation is optimized for the recurrent neural network because it can process one line at a single time step. To use the matrix features in ...
Bank of England Inflation Report November 2007
... Percentage of the working-age population. This measure weights together the different types of non-employed by a proxy of their likelihood of finding work based on transition rates into employment derived from the Labour Force Survey (LFS). Weights are backward-looking four-quarter moving averages o ...
... Percentage of the working-age population. This measure weights together the different types of non-employed by a proxy of their likelihood of finding work based on transition rates into employment derived from the Labour Force Survey (LFS). Weights are backward-looking four-quarter moving averages o ...
Image Management Software / Image Cataloging Tool
... Most systems seem to keep only keywords or categories, as they serve similar organizational purposes. Some, which employ a hierarchical structure use both as an image can only belong to one category (only be placed in one folder) but the user may desire to assign multiple keywords. The simple soluti ...
... Most systems seem to keep only keywords or categories, as they serve similar organizational purposes. Some, which employ a hierarchical structure use both as an image can only belong to one category (only be placed in one folder) but the user may desire to assign multiple keywords. The simple soluti ...
new method of variable selection for binary data cluster analysis
... In stage 2 we have to use some kind of partitioning algorithm because the data sets are too big for agglomerative algorithms. The most popular and applied in virtually any comparative simulation study is the k-means clustering. However, in the case of binary data sets, it cannot be used under no pre ...
... In stage 2 we have to use some kind of partitioning algorithm because the data sets are too big for agglomerative algorithms. The most popular and applied in virtually any comparative simulation study is the k-means clustering. However, in the case of binary data sets, it cannot be used under no pre ...
Information Sensitivity Policy
... disclosure could adversely impact YourCause or its customers, suppliers, business partners, or employees. YourCause Internal Data is internal operating procedures, manuals, memos, emails, as well as sensitive financial and technical information that is proprietary or produced only for use by members ...
... disclosure could adversely impact YourCause or its customers, suppliers, business partners, or employees. YourCause Internal Data is internal operating procedures, manuals, memos, emails, as well as sensitive financial and technical information that is proprietary or produced only for use by members ...
Monitoring and Assessing the Condition of Aquatic Resources: Role
... (convey results) 3. Objectives for monitoring are not clearly, precisely stated and understood (monitoring objectives) 4. Monitoring program not viewed/implemented as an information system (data management, overall) 5. Monitoring measurement protocols, survey design, and statistical analysis become ...
... (convey results) 3. Objectives for monitoring are not clearly, precisely stated and understood (monitoring objectives) 4. Monitoring program not viewed/implemented as an information system (data management, overall) 5. Monitoring measurement protocols, survey design, and statistical analysis become ...
Chapter 10
... • Bulletin-board style allows for participation on respondents schedule • More available in certain places than telephone conferencing facilities • Can be used to corroborate findings from in-person groups—done in only one or two markets ...
... • Bulletin-board style allows for participation on respondents schedule • More available in certain places than telephone conferencing facilities • Can be used to corroborate findings from in-person groups—done in only one or two markets ...
RXR-1 - SoCalGas
... of the years referred to in Q1. As part of this information, please include (a) a brief narrative on each annual storage auction, (b) the number of initial bidders for each of the 3 storage products, (c) the total demand for each of the 3 storage products as reflected in the initial round of bidding ...
... of the years referred to in Q1. As part of this information, please include (a) a brief narrative on each annual storage auction, (b) the number of initial bidders for each of the 3 storage products, (c) the total demand for each of the 3 storage products as reflected in the initial round of bidding ...
Year 8 Mathematics Term 1a Numbers and the number system
... • round numbers and measures to an appropriate degree of accuracy (e.g. to a specified number of decimal places or significant figures) • interpret standard form A × 10n, where 1 ≤ A < 10 and n is an integer ...
... • round numbers and measures to an appropriate degree of accuracy (e.g. to a specified number of decimal places or significant figures) • interpret standard form A × 10n, where 1 ≤ A < 10 and n is an integer ...
Business Development and its information needs
... Current head of the Laboratory of Mycobacterial Immunity and Pathogenesis, The Public Health Research Institute, ...
... Current head of the Laboratory of Mycobacterial Immunity and Pathogenesis, The Public Health Research Institute, ...