Chapter 8: Advanced Routing Protocols
... – Allow EIGRP to discover neighbors and keep track of their status – EIGRP must be able to keep updates bounded, sent only to those peers that need the information – EIGRP must build a neighbor table of directly connected peers CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
... – Allow EIGRP to discover neighbors and keep track of their status – EIGRP must be able to keep updates bounded, sent only to those peers that need the information – EIGRP must build a neighbor table of directly connected peers CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
Peer
... Conceived by Sun Microsystems + designed by a small number of experts from academic institutions and industry • team identified a number of shortcomings in many existing peer-to-peer systems and set up project JXTA in order to address these. • their 3 main objectives of were to achieve interoperabil ...
... Conceived by Sun Microsystems + designed by a small number of experts from academic institutions and industry • team identified a number of shortcomings in many existing peer-to-peer systems and set up project JXTA in order to address these. • their 3 main objectives of were to achieve interoperabil ...
DYNAMIX Wi-Fi VoIP Gateway DW 3512 Technical Manaul
... Copyright © 2007 Dynamix Pro., Ltd. All right reserved. ...
... Copyright © 2007 Dynamix Pro., Ltd. All right reserved. ...
ipv6 ospf - AfNOG 2017 Workshop on Network Technology
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
Powerpoint
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
... External route Routes imported into OSPF from another routing protocol by an ASBR ...
User`s Manual
... Complies with IEEE 802.11b/g standard for 2.4GHz Wireless LAN. Supports bridging, routing, VPN, WISP functions between wireless and wired Ethernet interfaces. Supports 64-bit and 128-bit WEP, WPA, WPA2 encryption/decryption function to protect the wireless data transmission. Supports IEEE 802.1x Aut ...
... Complies with IEEE 802.11b/g standard for 2.4GHz Wireless LAN. Supports bridging, routing, VPN, WISP functions between wireless and wired Ethernet interfaces. Supports 64-bit and 128-bit WEP, WPA, WPA2 encryption/decryption function to protect the wireless data transmission. Supports IEEE 802.1x Aut ...
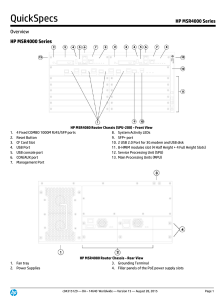
HP MSR4000 Series
... incorrect inbound interface; prevents source spoofing and distributed attacks Network login allows authentication of multiple users per port RADIUS eases security access administration by using a user/password authentication server Network address translation (NAT) supports one-to-one NAT, many-to-m ...
... incorrect inbound interface; prevents source spoofing and distributed attacks Network login allows authentication of multiple users per port RADIUS eases security access administration by using a user/password authentication server Network address translation (NAT) supports one-to-one NAT, many-to-m ...
PRODUCT CATALOG
... • Advanced security through 64-bit/128-bit WEP encryption, IEEE 802.1x authentication, and Wi-Fi Protected Access (WPA) to protect your information and to ensure secure data transmissions • Instant access to shared information without the need to plug in • Network managers can set up, move, or expan ...
... • Advanced security through 64-bit/128-bit WEP encryption, IEEE 802.1x authentication, and Wi-Fi Protected Access (WPA) to protect your information and to ensure secure data transmissions • Instant access to shared information without the need to plug in • Network managers can set up, move, or expan ...
MIS framework
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
Slide 1
... BOOTP • The bootstrap protocol (BOOTP) operates in a client-server environment and only requires a single packet exchange to obtain IP information. • However, unlike RARP, BOOTP packets can include the IP address, as well as the address of a router, the address of a server, and vendorspecific inform ...
... BOOTP • The bootstrap protocol (BOOTP) operates in a client-server environment and only requires a single packet exchange to obtain IP information. • However, unlike RARP, BOOTP packets can include the IP address, as well as the address of a router, the address of a server, and vendorspecific inform ...
start slide: headline arial bold 38 pt, 0 pt leading
... One common MAC supporting multiple PHYs Two configurations – “Independent” (ad hoc) and “Infrastructure” ...
... One common MAC supporting multiple PHYs Two configurations – “Independent” (ad hoc) and “Infrastructure” ...
IPSec
... • A combination of characters entered at each endpoint of the IPSec connection • Authentication – Both endpoints know the same secret, and no one else has been told – Advantage • Simplicity • Authentication occurs as long as the preshared key is typed in correctly on each device ...
... • A combination of characters entered at each endpoint of the IPSec connection • Authentication – Both endpoints know the same secret, and no one else has been told – Advantage • Simplicity • Authentication occurs as long as the preshared key is typed in correctly on each device ...
Ch03
... The backbone networks in the Internet can be switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, mu ...
... The backbone networks in the Internet can be switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, mu ...
Underlying Technologies
... The backbone networks in the Internet can be switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, mu ...
... The backbone networks in the Internet can be switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, mu ...
Parallel Dispatch Queue: A Queue-Based
... software locks around individual resources would incur prohibitively high overheads and may result in busy-waiting in these systems, thereby offsetting the gains from parallel handler execution. As such, executing fine-grain protocol handlers in parallel requires efficient synchronization support [ ...
... software locks around individual resources would incur prohibitively high overheads and may result in busy-waiting in these systems, thereby offsetting the gains from parallel handler execution. As such, executing fine-grain protocol handlers in parallel requires efficient synchronization support [ ...
CISCO GIGABIT ETHERNET NETWORK MODULE
... Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Empowering the Internet Generation, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, FormShare, GigaDrive, GigaStack, HomeLink, Internet Quotient, ...
... Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Empowering the Internet Generation, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, FormShare, GigaDrive, GigaStack, HomeLink, Internet Quotient, ...
SAML Whitepaper
... authenticated users. The adoption of the SAML standard will enable application and infrastructure vendors to provide these interactions in standards-based ways, thereby making them much quicker and simpler for organizations to deploy. This capability will allow companies to be more responsive to the ...
... authenticated users. The adoption of the SAML standard will enable application and infrastructure vendors to provide these interactions in standards-based ways, thereby making them much quicker and simpler for organizations to deploy. This capability will allow companies to be more responsive to the ...
AirLive AP60 Manual
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
AirLive AP60 Manual
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
IPv6 - DePaul University
... [0] The IPv6 address management function was formally delegated to IANA in December 1995 [RFC1881]. [1] The "unspecified address", the "loopback address", and the IPv6 Addresses with Embedded IPv4 Addresses are assigned out of the 0000::/8 address block. [2] 0200::/7 was previously defined as an OSI ...
... [0] The IPv6 address management function was formally delegated to IANA in December 1995 [RFC1881]. [1] The "unspecified address", the "loopback address", and the IPv6 Addresses with Embedded IPv4 Addresses are assigned out of the 0000::/8 address block. [2] 0200::/7 was previously defined as an OSI ...
USER MANUAL PROLiNK® Wireless
... powerful high-speed wireless connection for compatible wireless-enabled devices into the network with the freedom to roam. With web-based UI, this Access Point is easy to be setup and maintained. All functions can be configured within the easy and friendly user interface via web browser. Via the fas ...
... powerful high-speed wireless connection for compatible wireless-enabled devices into the network with the freedom to roam. With web-based UI, this Access Point is easy to be setup and maintained. All functions can be configured within the easy and friendly user interface via web browser. Via the fas ...
WLAN
... rogue AP and configures it with the same SSID as a legitimate AP. Locations offering free Wi-Fi, such as airports, cafes, and restaurants, are hotbeds for this type of attack due to the open authentication. Connecting wireless clients would see two APs offering wireless access. Those near the ro ...
... rogue AP and configures it with the same SSID as a legitimate AP. Locations offering free Wi-Fi, such as airports, cafes, and restaurants, are hotbeds for this type of attack due to the open authentication. Connecting wireless clients would see two APs offering wireless access. Those near the ro ...
ITP630_U4_Karloff_Boris_IT_ APA format
... algorithms are also known as Bellman-Ford routing algorithms and Ford-Fulkerson routing algorithms. (HowStuffWorks.com, 2003). The following are a few examples of this type of protocol. ...
... algorithms are also known as Bellman-Ford routing algorithms and Ford-Fulkerson routing algorithms. (HowStuffWorks.com, 2003). The following are a few examples of this type of protocol. ...
BootP and DHCP
... In the picture above you see the BOOTP message format. One line is 4 bytes long. Note the 64-octet vendor specific area at the bottom of the frame. This space can be used for various additional messages and will be extended by DHCP. In the middle part (red) the most important information is carried, ...
... In the picture above you see the BOOTP message format. One line is 4 bytes long. Note the 64-octet vendor specific area at the bottom of the frame. This space can be used for various additional messages and will be extended by DHCP. In the middle part (red) the most important information is carried, ...