QuickSpecs
... collects, maintains, and distributes dynamic public addresses through the VPN Address Management (VAM) protocol, making VPN establishment available between enterprise branches that use dynamic addresses to access the public network; compared to traditional VPN technologies, DVPN technology is more f ...
... collects, maintains, and distributes dynamic public addresses through the VPN Address Management (VAM) protocol, making VPN establishment available between enterprise branches that use dynamic addresses to access the public network; compared to traditional VPN technologies, DVPN technology is more f ...
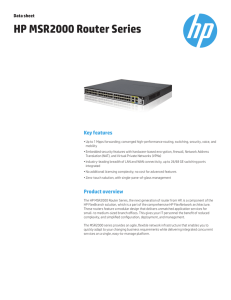
HP MSR2000 Router Series data sheet
... Ships with new Comware v7 Operating System delivering the latest in virtualization and routing Connectivity • Virtual eXtensible LAN (VXLAN) VXLAN is an IP-based network, using the “MAC in UDP” package of Layer VPN technology. VXLAN can be based on an existing ISP or enterprise IP networks for decen ...
... Ships with new Comware v7 Operating System delivering the latest in virtualization and routing Connectivity • Virtual eXtensible LAN (VXLAN) VXLAN is an IP-based network, using the “MAC in UDP” package of Layer VPN technology. VXLAN can be based on an existing ISP or enterprise IP networks for decen ...
BCMSN-Module6-Lesson4-WLANClients_edited
... 2. What is the Aironet System Tray Utility (ASTU)? 3. What is the Cisco Compatible Extensions (CCX) program? ...
... 2. What is the Aironet System Tray Utility (ASTU)? 3. What is the Cisco Compatible Extensions (CCX) program? ...
PDF
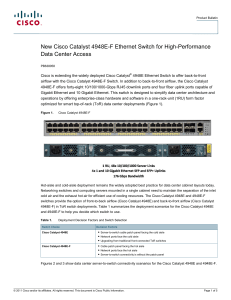
... Cisco IOS Software Cisco IOS Software is a proven network OS that offers best-in-class availability, manageability, and scalability. The Cisco Catalyst 4948E and 4948E-F support three levels of Cisco IOS Software. The basic level is LAN Base, developed for deployments that require data center-class ...
... Cisco IOS Software Cisco IOS Software is a proven network OS that offers best-in-class availability, manageability, and scalability. The Cisco Catalyst 4948E and 4948E-F support three levels of Cisco IOS Software. The basic level is LAN Base, developed for deployments that require data center-class ...
Networking Overview
... TCP/IP, Our Hero Layers from TCP/IP’s perspective… Application Layer --- Program trying to communicate using TCP/IP ...
... TCP/IP, Our Hero Layers from TCP/IP’s perspective… Application Layer --- Program trying to communicate using TCP/IP ...
PDF
... Communications 500 Series sites to be networked together in a full-mesh data and voice virtual private network (VPN). ...
... Communications 500 Series sites to be networked together in a full-mesh data and voice virtual private network (VPN). ...
CCNPv5 Module 5 Lesson 10
... The system clock can be set from a number of sources and can be used to distribute the current time through various mechanisms to other systems When a router with a system calendar is initialised or rebooted, the system clock is set based on the time in the internal batterypowered system calenda ...
... The system clock can be set from a number of sources and can be used to distribute the current time through various mechanisms to other systems When a router with a system calendar is initialised or rebooted, the system clock is set based on the time in the internal batterypowered system calenda ...
PDF
... Sizing Guidelines The Cisco IWAN App can support up to 500 sites simultaneously contacting the server and being provisioned, and up to 1000 network devices managed in the Cisco IWAN application for APIC-EM. See the Release Notes for Cisco Application Policy Infrastructure Controller Enterprise Modul ...
... Sizing Guidelines The Cisco IWAN App can support up to 500 sites simultaneously contacting the server and being provisioned, and up to 1000 network devices managed in the Cisco IWAN application for APIC-EM. See the Release Notes for Cisco Application Policy Infrastructure Controller Enterprise Modul ...
Cisco Application Centric Infrastructure and Cisco Application Virtual
... separate the organizational and forwarding requirements of a tenant. Within each VRF instance, a bridge domain is created. A bridge domain is a Layer 2 namespace in which you define the various subnets. You assign all the subnets and default gateways within the bridge domain. By using separate forwa ...
... separate the organizational and forwarding requirements of a tenant. Within each VRF instance, a bridge domain is created. A bridge domain is a Layer 2 namespace in which you define the various subnets. You assign all the subnets and default gateways within the bridge domain. By using separate forwa ...
IAS Router Common Criteria Operator Guidance
... avoided. Password strength is a function of length and complexity. Longer passwords provide more protection against brute-force attacks. We recommend to use as long and as complex of a password that can be remembered. In CSfC mode, the minimum requirement is for a fifteen character password containi ...
... avoided. Password strength is a function of length and complexity. Longer passwords provide more protection against brute-force attacks. We recommend to use as long and as complex of a password that can be remembered. In CSfC mode, the minimum requirement is for a fifteen character password containi ...
Cisco TrustSec How-To Guide: Segmenting Clients and Servers in
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
RoamAbout 802.11 Wireless Networking Guide
... Signal Level .............................................................................................................................................. 3-6 Noise Level ................................................................................................................................ ...
... Signal Level .............................................................................................................................................. 3-6 Noise Level ................................................................................................................................ ...
PDF
... dynamically learned during IKE Mode Configuration exchange, and inserted into the routing table pointing to the virtual access interface. This configuration allows for split tunneling. With split tunneling, remote users can send traffic destined for the Internet directly, without going onto the IPSe ...
... dynamically learned during IKE Mode Configuration exchange, and inserted into the routing table pointing to the virtual access interface. This configuration allows for split tunneling. With split tunneling, remote users can send traffic destined for the Internet directly, without going onto the IPSe ...
OSPF
... the command ip ospf hello-interval. RouterDeadInterval - The period in seconds that the router will wait to hear a Hello from a neighbor before declaring the neighbor down. Cisco ...
... the command ip ospf hello-interval. RouterDeadInterval - The period in seconds that the router will wait to hear a Hello from a neighbor before declaring the neighbor down. Cisco ...
Cisco Discovery Protocol (CDP)
... device to detect neighboring devices that are also running CDP. CDP runs over the data link layer and allows the two systems to learn about each other. ...
... device to detect neighboring devices that are also running CDP. CDP runs over the data link layer and allows the two systems to learn about each other. ...
Ch11
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
Document
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
Cisco PIX 515E Security Appliance
... next-generation, three-tier management solution that includes the following features: • Comprehensive configuration and software image management • Device hierarchy with “Smart Rules”-based configuration inheritance • Customizable administrative roles and access privileges • Comprehensive enterprise ...
... next-generation, three-tier management solution that includes the following features: • Comprehensive configuration and software image management • Device hierarchy with “Smart Rules”-based configuration inheritance • Customizable administrative roles and access privileges • Comprehensive enterprise ...
Cisco PIX 535 Security Appliance
... Additional integrated event management and inventory solutions are also available as part of the CiscoWorks VMS network management suite. The integrated Cisco PIX Device Manager provides an intuitive, Web-based management interface for remotely configuring, monitoring, and troubleshooting a Cisco PI ...
... Additional integrated event management and inventory solutions are also available as part of the CiscoWorks VMS network management suite. The integrated Cisco PIX Device Manager provides an intuitive, Web-based management interface for remotely configuring, monitoring, and troubleshooting a Cisco PI ...
slides - network systems lab @ sfu
... •Using this protocol, peers can advertise their own resources, network service, identity, and discover the resources from other peers • Peer resources are published using XML-based metadata format ...
... •Using this protocol, peers can advertise their own resources, network service, identity, and discover the resources from other peers • Peer resources are published using XML-based metadata format ...
PDF
... multiple Radio Access Networks (RANs), back-end billing systems, and content-filtering and compression solutions. Mobile operators can install and deploy Cisco Mobile SEF solutions without disrupting any services. The Cisco CSG2 is an application deployed on the Cisco Service and Application Module ...
... multiple Radio Access Networks (RANs), back-end billing systems, and content-filtering and compression solutions. Mobile operators can install and deploy Cisco Mobile SEF solutions without disrupting any services. The Cisco CSG2 is an application deployed on the Cisco Service and Application Module ...
Coding and Error Control
... • Manages various aspects of the radio link between a master and a slave • Involves the exchange LMP PDUs (protocol data units) • Procedures defined for LMP are grouped into 24 ...
... • Manages various aspects of the radio link between a master and a slave • Involves the exchange LMP PDUs (protocol data units) • Procedures defined for LMP are grouped into 24 ...
Ch07 ver 1
... Service type. Originally, this field was referred to as type of service (TOS). Part of the field was used to define the precedence of the datagram; the rest defined the type of service (low delay, high throughput, and so on). IETF has changed the interpretation of this 8-bit field. It now defines a ...
... Service type. Originally, this field was referred to as type of service (TOS). Part of the field was used to define the precedence of the datagram; the rest defined the type of service (low delay, high throughput, and so on). IETF has changed the interpretation of this 8-bit field. It now defines a ...
CCNP 1 - University of Wolverhampton
... Checksum Link count 0x80000005 0x00D5B0 5 0x80000006 0x009F91 5 ...
... Checksum Link count 0x80000005 0x00D5B0 5 0x80000006 0x009F91 5 ...