ppt - Carnegie Mellon School of Computer Science
... Tools to help us build secure communication channels that provide: 1) Authentication 2) Integrity 3) Confidentiality ...
... Tools to help us build secure communication channels that provide: 1) Authentication 2) Integrity 3) Confidentiality ...
NETGEAR Wireless Router Setup Manual
... Routing Information Protocol ................................................................................... B-2 IP Addresses and the Internet ....................................................................................... B-2 Netmask ..................................................... ...
... Routing Information Protocol ................................................................................... B-2 IP Addresses and the Internet ....................................................................................... B-2 Netmask ..................................................... ...
IEEE 802 March 2011 workshop - LMSC, LAN/MAN Standards
... • One of the frame types defined in 802.11 is “Action” sub-type “Management” • Management frames were previously less well protected than data frames. • The objective of this was to improve the security by providing data confidentiality of action management frames, deauthentication and disassociatio ...
... • One of the frame types defined in 802.11 is “Action” sub-type “Management” • Management frames were previously less well protected than data frames. • The objective of this was to improve the security by providing data confidentiality of action management frames, deauthentication and disassociatio ...
DHCP - Personal Web Pages
... originating device in order to select an IP address from the correct pool DHCP server then sends the DHCP OFFER back to the router via unicast Router converts the DHCP OFFER back to a broadcast, sent out on the interface of the original device ...
... originating device in order to select an IP address from the correct pool DHCP server then sends the DHCP OFFER back to the router via unicast Router converts the DHCP OFFER back to a broadcast, sent out on the interface of the original device ...
DHCP - Personal Web Pages
... originating device in order to select an IP address from the correct pool DHCP server then sends the DHCP OFFER back to the router via unicast Router converts the DHCP OFFER back to a broadcast, sent out on the interface of the original device ...
... originating device in order to select an IP address from the correct pool DHCP server then sends the DHCP OFFER back to the router via unicast Router converts the DHCP OFFER back to a broadcast, sent out on the interface of the original device ...
oneM2M-TR-0009-Protocol_Analysis-V0_4_0
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
plug and play server load balancing and global server load
... Managers, network layer anycast can be easily deployed. Each SLB Manager will inject the anycast VIP address into the OSPF routing tables from their dispersed locations. The OSPF routing protocol will be used to automatically connect clients to the closest server. This simplifies server location iss ...
... Managers, network layer anycast can be easily deployed. Each SLB Manager will inject the anycast VIP address into the OSPF routing tables from their dispersed locations. The OSPF routing protocol will be used to automatically connect clients to the closest server. This simplifies server location iss ...
configuring dynamic multipoint vpn spoke router in full mesh
... Multipoint VPN (DMVPN). DMVPN allows users to scale large and small IPsec VPNs more effectively by combining generic routing encapsulation (GRE) tunnels, IPsec encryption, and Next Hop Resolution Protocol (NHRP). Security Device Manager ...
... Multipoint VPN (DMVPN). DMVPN allows users to scale large and small IPsec VPNs more effectively by combining generic routing encapsulation (GRE) tunnels, IPsec encryption, and Next Hop Resolution Protocol (NHRP). Security Device Manager ...
WRC-1000 Wireless Routing Center
... unauthorized modification of the TOSHIBA Wireless Routing Center WRC-1000, or the substitution or attachment of connecting cables and equipment other than specified by TOSHIBA. The correction of interference caused by such unauthorized modification, substitution or attachment will be the responsibil ...
... unauthorized modification of the TOSHIBA Wireless Routing Center WRC-1000, or the substitution or attachment of connecting cables and equipment other than specified by TOSHIBA. The correction of interference caused by such unauthorized modification, substitution or attachment will be the responsibil ...
CCNA Concentrations
... confident their staff has the skills needed for basic wireless networking on a Cisco WLAN in SMB and enterprise networks. Presentation_ID ...
... confident their staff has the skills needed for basic wireless networking on a Cisco WLAN in SMB and enterprise networks. Presentation_ID ...
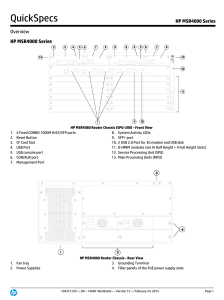
HP MSR4000 Series
... part of the comprehensive HP FlexNetwork architecture. These routers feature a modular design that delivers unmatched application services for extra-large branch offices, headquarters, and campuses. This gives your IT personnel the benefit of reduced complexity, and simplified configuration, deploym ...
... part of the comprehensive HP FlexNetwork architecture. These routers feature a modular design that delivers unmatched application services for extra-large branch offices, headquarters, and campuses. This gives your IT personnel the benefit of reduced complexity, and simplified configuration, deploym ...
Protocol Analysis
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
TR-M2M-0009v0.7.0 oneM2M Protocol Analysis
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
MSI RG54SE Wireless 11g Broadband Router
... Complies with IEEE 802.11b/g standard for 2.4GHz Wireless LAN. Supports 64-bit and 128-bit WEP, WPA, WPA2 encryption/decryption function to protect the wireless data transmission. Supports IEEE 802.1x Authentication. Support Wi-Fi Protected Access Authentication with Radius and Pre-Shared Key mode. ...
... Complies with IEEE 802.11b/g standard for 2.4GHz Wireless LAN. Supports 64-bit and 128-bit WEP, WPA, WPA2 encryption/decryption function to protect the wireless data transmission. Supports IEEE 802.1x Authentication. Support Wi-Fi Protected Access Authentication with Radius and Pre-Shared Key mode. ...
Napster and Gnutella - Department of Computer Science and
... Free internet provided by universities was being abused. Result Napster was banned in most universities and public facilities. P2P file sharing did not stop. Protocols such as Gnutella got rid of the central server. This reduces the legal liability. Later protocols allowed the users to share all typ ...
... Free internet provided by universities was being abused. Result Napster was banned in most universities and public facilities. P2P file sharing did not stop. Protocols such as Gnutella got rid of the central server. This reduces the legal liability. Later protocols allowed the users to share all typ ...
CCNA Concentrations
... confident their staff has the skills needed for basic wireless networking on a Cisco WLAN in SMB and enterprise networks. Presentation_ID ...
... confident their staff has the skills needed for basic wireless networking on a Cisco WLAN in SMB and enterprise networks. Presentation_ID ...
Router R1 in Figure 6.8 receives a packet with destination address
... Figure 6.18 shows a simple example of searching in a routing table using the longest match algorithm. Although there are some more efficient algorithms today, the principle is the same. When the forwarding algorithm gets the destination address of the packet, it needs to delve into the mask column. ...
... Figure 6.18 shows a simple example of searching in a routing table using the longest match algorithm. Although there are some more efficient algorithms today, the principle is the same. When the forwarding algorithm gets the destination address of the packet, it needs to delve into the mask column. ...
SWIM: Scalable Weakly-consistent Infection-style Process Group Membership Protocol
... does clared as failed by a non-faulty member not receive heartbeats from for some consecutive heartbeat periods. Distributed heartbeating schemes guarantee that a faulty member is always detected as such at any non-faulty member (within a time interval after its failure) , since a member that has cr ...
... does clared as failed by a non-faulty member not receive heartbeats from for some consecutive heartbeat periods. Distributed heartbeating schemes guarantee that a faulty member is always detected as such at any non-faulty member (within a time interval after its failure) , since a member that has cr ...
ARP Spoofing Prevention ................................44
... use within your home, business or public access wireless networks. D-Link wireless products provides you with access to the data you want, whenever and wherever you want it. Enjoy the freedom that wireless networking can bring to you. WLAN use is not only increasing in both home and office environme ...
... use within your home, business or public access wireless networks. D-Link wireless products provides you with access to the data you want, whenever and wherever you want it. Enjoy the freedom that wireless networking can bring to you. WLAN use is not only increasing in both home and office environme ...
Wireless Sniffing With Wireshark
... Before we start wireless sniffing using Wireshark, it is helpful to understand the different operating modes supported by wireless cards. Most wireless users only use their wireless cards as a station to an AP. In managed mode, the wireless card and driver software rely on a local AP to provide conn ...
... Before we start wireless sniffing using Wireshark, it is helpful to understand the different operating modes supported by wireless cards. Most wireless users only use their wireless cards as a station to an AP. In managed mode, the wireless card and driver software rely on a local AP to provide conn ...
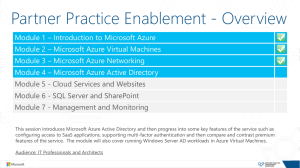
Azure AD
... Module 5 - Cloud Services and Websites Module 6 - SQL Server and SharePoint Module 7 - Management and Monitoring This session introduces Microsoft Azure Active Directory and then progress into some key features of the service such as configuring access to SaaS applications, supporting multi-factor a ...
... Module 5 - Cloud Services and Websites Module 6 - SQL Server and SharePoint Module 7 - Management and Monitoring This session introduces Microsoft Azure Active Directory and then progress into some key features of the service such as configuring access to SaaS applications, supporting multi-factor a ...
Addendum A - NPTF Principles
... traffic by destination service provider (Cogent vs Qwest vs Abilene/Internet2), and much more. ...
... traffic by destination service provider (Cogent vs Qwest vs Abilene/Internet2), and much more. ...