Chapter 5 : The Internet: Addressing & Services
... Allows for subdivision of internets within an organization Each LAN can have a subnet number, allowing routing among networks Host portion is partitioned into subnet and host numbers See Table 5.2 for method of calculating subnet masks ...
... Allows for subdivision of internets within an organization Each LAN can have a subnet number, allowing routing among networks Host portion is partitioned into subnet and host numbers See Table 5.2 for method of calculating subnet masks ...
Lesson 10
... Network • Routing protocol establish mutually consistent routing tables in every router • Characteristics of routing protocol: ...
... Network • Routing protocol establish mutually consistent routing tables in every router • Characteristics of routing protocol: ...
ASSIGNMENT #3
... Routers use a combination of hardware and software to forward data packets to their destination on the internet. They are more efficient and sophisticated than bridges and switches. They can divide large networks into logical segments called Subnets on the basis of IP addressing scheme. A router can ...
... Routers use a combination of hardware and software to forward data packets to their destination on the internet. They are more efficient and sophisticated than bridges and switches. They can divide large networks into logical segments called Subnets on the basis of IP addressing scheme. A router can ...
Ethernet Link SMS-800
... SMS-800 provides management features that are ideal for simple QoS/CoS applications and basic monitoring tools to improve network efficiency. Its security and management features, such as bandwidth control, and VLAN (IEEE 802.1Q VLAN tagging and port-based VLAN) to secure your network. Through a Web ...
... SMS-800 provides management features that are ideal for simple QoS/CoS applications and basic monitoring tools to improve network efficiency. Its security and management features, such as bandwidth control, and VLAN (IEEE 802.1Q VLAN tagging and port-based VLAN) to secure your network. Through a Web ...
Chapter 4 Review Questions
... 1. Datagram-based network layer: path determination; forwarding. Additional function of VC-based network layer: call setup. 2. ATM service models: CBR, VBR, ABR, UBR. See section 4.1.1 for the descriptioins. 3. Link state algorithms: Computes the least-cost path between source and destination using ...
... 1. Datagram-based network layer: path determination; forwarding. Additional function of VC-based network layer: call setup. 2. ATM service models: CBR, VBR, ABR, UBR. See section 4.1.1 for the descriptioins. 3. Link state algorithms: Computes the least-cost path between source and destination using ...
d - FSU Computer Science Department
... • Circuit means a path between the source and the destination. • Real circuit switching has a physical path set up between the source and the destination, like telephone network – When you dial, a request is sent to the network, network finds if there are free links on the path and reserve that link ...
... • Circuit means a path between the source and the destination. • Real circuit switching has a physical path set up between the source and the destination, like telephone network – When you dial, a request is sent to the network, network finds if there are free links on the path and reserve that link ...
1 It is desired to send a sequence of computer screen images over
... 10. Give two example computer applications for which connection-oriented service is appropriate. Now give two examples for which connectionless service is best. 11. Datagram subnets route each packet as a separate unit, independent of all others. Virtual-circuit subnets do not have to do this, since ...
... 10. Give two example computer applications for which connection-oriented service is appropriate. Now give two examples for which connectionless service is best. 11. Datagram subnets route each packet as a separate unit, independent of all others. Virtual-circuit subnets do not have to do this, since ...
$doc.title
... • D(v): current cost of path from source to node v – Ini.ally, D(v) = c(u,v) for all nodes v adjacent to u – … and D(v) = ∞ for all other nodes v – Con.nually update D(v) as shorter paths are learned ...
... • D(v): current cost of path from source to node v – Ini.ally, D(v) = c(u,v) for all nodes v adjacent to u – … and D(v) = ∞ for all other nodes v – Con.nually update D(v) as shorter paths are learned ...
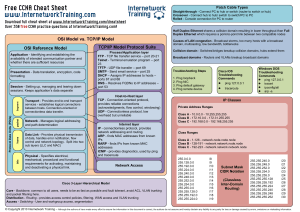
CCNA cheat sheet - Internetwork Training
... Half Duplex Ethernet shares a collision domain resulting in lower throughput than Full Duplex Ethernet which requires a point-to-point link between two compatible nodes ...
... Half Duplex Ethernet shares a collision domain resulting in lower throughput than Full Duplex Ethernet which requires a point-to-point link between two compatible nodes ...
Multicast with Network Coding in Application
... Main Results of Network Coding • If the capacity of any sink Ri ≥ C, then multicast rate of C is achievable, generally with network coding. ...
... Main Results of Network Coding • If the capacity of any sink Ri ≥ C, then multicast rate of C is achievable, generally with network coding. ...
Abstract - PG Embedded systems
... In this analysis, we consider Wireless network, where nodes that have decoded the message at the previous hop cooperate in the transmission toward the next hop, realizing a distributed space-time coding scheme. Service delivery in a heterogeneous all-IP wireless network environment requires the sele ...
... In this analysis, we consider Wireless network, where nodes that have decoded the message at the previous hop cooperate in the transmission toward the next hop, realizing a distributed space-time coding scheme. Service delivery in a heterogeneous all-IP wireless network environment requires the sele ...
CSE 461 - University of Washington
... • Bonus Question: How do you determine who gets to be the new active monitor? • Node with the highest MAC address wins. ...
... • Bonus Question: How do you determine who gets to be the new active monitor? • Node with the highest MAC address wins. ...
Producer-Consumer Problem
... • A node is intended to represent a physically identifiable object like a computer. (Don’t fail) • Individual computers may be running multiple processes, either by sharing a single processor or on multiple processors. • We assume that the local synchronization among processes in a node is accomplis ...
... • A node is intended to represent a physically identifiable object like a computer. (Don’t fail) • Individual computers may be running multiple processes, either by sharing a single processor or on multiple processors. • We assume that the local synchronization among processes in a node is accomplis ...
Control plane
... – State required to represent the paths – Efficiency of the resulting paths – Ability to support multiple paths – Complexity of computing the paths – Which nodes are in charge ...
... – State required to represent the paths – Efficiency of the resulting paths – Ability to support multiple paths – Complexity of computing the paths – Which nodes are in charge ...
Six Degrees of Separation
... Watts, D.J. (1999). Small Worlds: The Dynamics of Networks Between Order ...
... Watts, D.J. (1999). Small Worlds: The Dynamics of Networks Between Order ...
ppt
... • Each router runs Dijkstra’s algorithm – To compute the shortest paths – … and construct the forwarding table ...
... • Each router runs Dijkstra’s algorithm – To compute the shortest paths – … and construct the forwarding table ...
Six Degrees of Separation - Olympus High Mathematics
... Watts, D.J. (1999). Small Worlds: The Dynamics of Networks Between Order ...
... Watts, D.J. (1999). Small Worlds: The Dynamics of Networks Between Order ...
CS 455: Computer Networks and Data Communication Sample Final Examination Points: 125
... to the internet using a single IP address (203.45.103.67) provided by its ISP. Show how packets sent from a specific WS (10.23.52.201) to another workstation (125.25.43.98) are handled by the NAT. (Use the specific data given. Don’t simply write some generic answer.) ...
... to the internet using a single IP address (203.45.103.67) provided by its ISP. Show how packets sent from a specific WS (10.23.52.201) to another workstation (125.25.43.98) are handled by the NAT. (Use the specific data given. Don’t simply write some generic answer.) ...
msb201073-sup
... centrality of each node is a number between 0 and 1. NetworkAnalyzer computes the closeness centrality of all nodes and plots it against the number of neighbors. The closeness centrality of isolated nodes is equal to 0. Closeness centrality is a measure of how fast information spreads from a given n ...
... centrality of each node is a number between 0 and 1. NetworkAnalyzer computes the closeness centrality of all nodes and plots it against the number of neighbors. The closeness centrality of isolated nodes is equal to 0. Closeness centrality is a measure of how fast information spreads from a given n ...