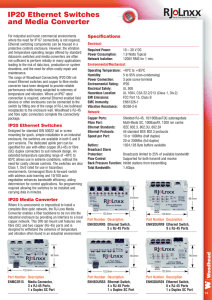
IP20 Ethernet Switches and Media Converter
... converter have been designed to provide reliable performance while being subjected to extremes of temperature and vibration. Where an IP67 rated connection is required, external Ethernet enabled field devices or other enclosures can be connected to the switch by fitting one of the range of RJ-Lnxx b ...
... converter have been designed to provide reliable performance while being subjected to extremes of temperature and vibration. Where an IP67 rated connection is required, external Ethernet enabled field devices or other enclosures can be connected to the switch by fitting one of the range of RJ-Lnxx b ...
Addressing - Punjab University College of Information
... IEEE as G/L bit IEEE sets G/L = 0 when giving out the blocks of addresses Addresses with G/L = 1 can be used without paying IEEE but the network administrator is responsible to assign addresses such that there is no collision This leaves with 222 unique OUIs ...
... IEEE as G/L bit IEEE sets G/L = 0 when giving out the blocks of addresses Addresses with G/L = 1 can be used without paying IEEE but the network administrator is responsible to assign addresses such that there is no collision This leaves with 222 unique OUIs ...
NIH PCKD/Emory University
... • 2 Patients Scanned with NIH Protocol • Both: Comparison with “Old Protocol” ...
... • 2 Patients Scanned with NIH Protocol • Both: Comparison with “Old Protocol” ...
3rd Edition: Chapter 4 - Southern Adventist University
... group members no need to forward datagrams down subtree “prune” msgs sent upstream by router with no downstream group members LEGEND ...
... group members no need to forward datagrams down subtree “prune” msgs sent upstream by router with no downstream group members LEGEND ...
Chapter 15 Local Area Networks
... • Link between LAN hub and mobile data terminal —Laptop or notepad computer —Enable employee returning from trip to transfer data from portable computer to server ...
... • Link between LAN hub and mobile data terminal —Laptop or notepad computer —Enable employee returning from trip to transfer data from portable computer to server ...
Getting the most out of Virtual Host
... ignored. This will prevent unsecured remote access to the IP cameras (which will typically employ the default login ID and password) when it is not required for configuration purposes. ...
... ignored. This will prevent unsecured remote access to the IP cameras (which will typically employ the default login ID and password) when it is not required for configuration purposes. ...
Treating Software-Defined Networks Like Disk Arrays.
... networks perform loop elimination and spanning tree construction by running a distributed algorithm such as the Spanning Tree Protocol (STP) or the improved Rapid Spanning Tree Protocol (RSTP) [19]. In STP and RSTP, Ethernet switches in the same network segment collaborate and agree on which networ ...
... networks perform loop elimination and spanning tree construction by running a distributed algorithm such as the Spanning Tree Protocol (STP) or the improved Rapid Spanning Tree Protocol (RSTP) [19]. In STP and RSTP, Ethernet switches in the same network segment collaborate and agree on which networ ...
Q-LAN Networking Overview
... Q-SYS devices, which depend upon multi cast packets for device discovery and sample clock, will cease to function. This is because the IGMP Snooping filters in switches belonging to this VLAN will restrict multi cast transmissions to any switch ports for which it has not detected a Membership Group ...
... Q-SYS devices, which depend upon multi cast packets for device discovery and sample clock, will cease to function. This is because the IGMP Snooping filters in switches belonging to this VLAN will restrict multi cast transmissions to any switch ports for which it has not detected a Membership Group ...
Slide 1 - ECE Users Pages
... - Membership is determined by the host’s MAC address. Administrator has to create a database with MAC addresses and VLAN mappings ...
... - Membership is determined by the host’s MAC address. Administrator has to create a database with MAC addresses and VLAN mappings ...
ppt
... multicast group concept: use of indirection hosts addresses IP datagram to multicast group routers forward multicast datagrams to hosts that have “joined” that multicast group ...
... multicast group concept: use of indirection hosts addresses IP datagram to multicast group routers forward multicast datagrams to hosts that have “joined” that multicast group ...
PDF
... High availability is a vital requirement for networks that transport mission-critical data. The IE 2000U supports dual connections for power supplies, SFP modules, and the connected grid swap drive, which increases network uptime and reduces redeployment time in the field. In addition, external alar ...
... High availability is a vital requirement for networks that transport mission-critical data. The IE 2000U supports dual connections for power supplies, SFP modules, and the connected grid swap drive, which increases network uptime and reduces redeployment time in the field. In addition, external alar ...
Meiden Review 2013 No.3 (Series No.159)
... factors, the hub or a communication channel may fail. In such a case, monitoring and control can be continued without being affected by this failure if the hub can automatically switch the failed link to redundant link. The Ethernet is generally constructed in a star topology. It will be either in a ...
... factors, the hub or a communication channel may fail. In such a case, monitoring and control can be continued without being affected by this failure if the hub can automatically switch the failed link to redundant link. The Ethernet is generally constructed in a star topology. It will be either in a ...
Floodless in SEATTLE: A Scalable Ethernet Architecture for Large Enterprises
... • Floods when frame arrives with unfamiliar destination or broadcast address – Forward the frame out all of the interfaces – … except for the one where the frame arrived – Hopefully, this case won’t happen very often B When in doubt, shout! ...
... • Floods when frame arrives with unfamiliar destination or broadcast address – Forward the frame out all of the interfaces – … except for the one where the frame arrived – Hopefully, this case won’t happen very often B When in doubt, shout! ...
Ch02 - Computer Systems Technology Internet Site
... functions as a standard AP only and does not communicate with other remote wireless bridges. Root Mode - In root mode the bridge, called the root bridge, can only communicate with other bridges that are not in root mode. A root bridge cannot communicate with another root bridge or any wireless cli ...
... functions as a standard AP only and does not communicate with other remote wireless bridges. Root Mode - In root mode the bridge, called the root bridge, can only communicate with other bridges that are not in root mode. A root bridge cannot communicate with another root bridge or any wireless cli ...
Chapter 15 Local Area Networks
... • Link between LAN hub and mobile data terminal —Laptop or notepad computer —Enable employee returning from trip to transfer data from portable computer to server ...
... • Link between LAN hub and mobile data terminal —Laptop or notepad computer —Enable employee returning from trip to transfer data from portable computer to server ...
Chapter 15 Local Area Networks
... • Link between LAN hub and mobile data terminal —Laptop or notepad computer —Enable employee returning from trip to transfer data from portable computer to server ...
... • Link between LAN hub and mobile data terminal —Laptop or notepad computer —Enable employee returning from trip to transfer data from portable computer to server ...
Minimax Open Shortest Path First Routing Algorithms in
... public, high-speed, connectionless (datagram), packet switched data service that the Regional Bell Operating companies (RBOCs) have offered. • Provides LAN-like performance and features over a wide area. • Regarded as the first phase of B-ISDN • High-speed access (1.5 Mbps to 45 Mbps) • Multicast ca ...
... public, high-speed, connectionless (datagram), packet switched data service that the Regional Bell Operating companies (RBOCs) have offered. • Provides LAN-like performance and features over a wide area. • Regarded as the first phase of B-ISDN • High-speed access (1.5 Mbps to 45 Mbps) • Multicast ca ...
Minimax Open Shortest Path First Routing Algorithms in Networks
... public, high-speed, connectionless (datagram), packet switched data service that the Regional Bell Operating companies (RBOCs) have offered. • Provides LAN-like performance and features over a wide area. • Regarded as the first phase of B-ISDN • High-speed access (1.5 Mbps to 45 Mbps) • Multicast ca ...
... public, high-speed, connectionless (datagram), packet switched data service that the Regional Bell Operating companies (RBOCs) have offered. • Provides LAN-like performance and features over a wide area. • Regarded as the first phase of B-ISDN • High-speed access (1.5 Mbps to 45 Mbps) • Multicast ca ...
Controller
... 2. Packet header forwarded to controller (pkt_in) 3. Controller does a “lookup” based on pkt: Any metadata about src and dst (e.g. tenant)? Are src and dst on same L2 network? What is the best path from src to dst? Any ACLs resolving to ‘drop’? ...
... 2. Packet header forwarded to controller (pkt_in) 3. Controller does a “lookup” based on pkt: Any metadata about src and dst (e.g. tenant)? Are src and dst on same L2 network? What is the best path from src to dst? Any ACLs resolving to ‘drop’? ...
aasg3_1
... An IP address is the address of a computer on a network. An IP address is an identifier for a computer or device on a TCP/IP network. An IP address is either a 32-bit or 128-bit unsigned number used by the internet protocol. IP addresses is made up of four whole numbers (4 bytes) between 0 and 255 a ...
... An IP address is the address of a computer on a network. An IP address is an identifier for a computer or device on a TCP/IP network. An IP address is either a 32-bit or 128-bit unsigned number used by the internet protocol. IP addresses is made up of four whole numbers (4 bytes) between 0 and 255 a ...
EEE449 Computer Networks
... – Considerable overhead in passing turns when only few stations transmit ...
... – Considerable overhead in passing turns when only few stations transmit ...
CIS 1140 Network Fundamentals
... whatever comes in on one port, gets amplified and send out to ALL other ports, so any network transmission 'fills up/flows into' ALL cable-segments of the network, so only ONE network connection can be active at a time on the complete network ! ...
... whatever comes in on one port, gets amplified and send out to ALL other ports, so any network transmission 'fills up/flows into' ALL cable-segments of the network, so only ONE network connection can be active at a time on the complete network ! ...
ZyXEL`s 10GbE L2+ Managed Switch Offers Line-rate
... Faster speeds, increased bandwidth and enhanced reliability are a must for any business network undergoing data center consolidation and virtualization. The XS3700-24’s built-in 10GbE aggregation capabilities allow the device to deliver 480 Gbps switching capacity and 357.14 Mpps forwarding rates wi ...
... Faster speeds, increased bandwidth and enhanced reliability are a must for any business network undergoing data center consolidation and virtualization. The XS3700-24’s built-in 10GbE aggregation capabilities allow the device to deliver 480 Gbps switching capacity and 357.14 Mpps forwarding rates wi ...
DuraNET 3000
... With software built on the Cisco IOS Catalyst architecture, the DuraNET 3000 offers ease of use and can be configured and managed using a web-based GUI Cisco Device Manager, plus network management tools like Cisco Network Assistant and CiscoWorks. The Layer 2+ version features a specialized Catalys ...
... With software built on the Cisco IOS Catalyst architecture, the DuraNET 3000 offers ease of use and can be configured and managed using a web-based GUI Cisco Device Manager, plus network management tools like Cisco Network Assistant and CiscoWorks. The Layer 2+ version features a specialized Catalys ...
Bridges - s3.amazonaws.com
... Not recommended for two reasons: - single point of failure at Computer Science hub - all traffic between EE and SE must path over CS segment 5: DataLink Layer 5c-13 ...
... Not recommended for two reasons: - single point of failure at Computer Science hub - all traffic between EE and SE must path over CS segment 5: DataLink Layer 5c-13 ...
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is an older network protocol that ensures a loop-free topology for any bridged Ethernet local area network. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include spare (redundant) links to provide automatic backup paths if an active link fails, without the danger of bridge loops, or the need for manual enabling/disabling of these backup links.Spanning Tree Protocol (STP) was originally standardized as IEEE 802.1D, in 802.1d-1998, but much of the functionality (spanning tree, rapid spanning tree, multiple spanning tree) previously specified in 802.1D, 801.1s, 802.1w has been incorporated into IEEE 802.1Q-2014 which includes shortest path bridging, the IEEE sanctioned replacement for these spanning tree functions.As the name suggests, it creates a spanning tree within a network of connected layer-2 bridges (typically Ethernet switches), and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation.























