10/100/1000 Mbps connectivity to workstations and servers and non
... switch/router capability that ensures subsecond fail-over. When deployed with Foundry’s optional IronWare routing services, FastIron II switches include Foundry Standby Router Protocol (FSRP) and industry-standard Virtual Router Redundancy Protocol (VRRP) to provide a fail-safe mechanism in routed e ...
... switch/router capability that ensures subsecond fail-over. When deployed with Foundry’s optional IronWare routing services, FastIron II switches include Foundry Standby Router Protocol (FSRP) and industry-standard Virtual Router Redundancy Protocol (VRRP) to provide a fail-safe mechanism in routed e ...
Protocol No: BR
... My own research protocol (Protocol no. ) Number of animals to be transferred to this protocol: Other NUS PI ‘s protocol (Protocol No: ) Number of animals to be transferred to this protocol: Other institution PI’s protocol (Protocol No: ) Name of PI and institution : Number of animals to be transferr ...
... My own research protocol (Protocol no. ) Number of animals to be transferred to this protocol: Other NUS PI ‘s protocol (Protocol No: ) Number of animals to be transferred to this protocol: Other institution PI’s protocol (Protocol No: ) Name of PI and institution : Number of animals to be transferr ...
PowerPoint
... link on shortest path back to source) then flood datagram onto all outgoing links else ignore datagram • But – generates lots of packets! • Pruning avoids sending packets to routers that don’t need them ...
... link on shortest path back to source) then flood datagram onto all outgoing links else ignore datagram • But – generates lots of packets! • Pruning avoids sending packets to routers that don’t need them ...
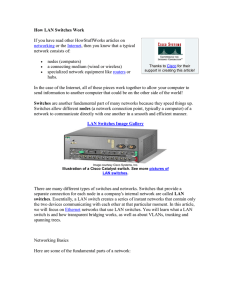
How LAN Switches Work
... on a different segment than Node B, the switch must connect the two segments to send the packet. This is known as forwarding. The next packet from Node A to Node B arrives at the switch. The switch now has the address of Node B, too, so it forwards the packet directly to Node B. Node C sends informa ...
... on a different segment than Node B, the switch must connect the two segments to send the packet. This is known as forwarding. The next packet from Node A to Node B arrives at the switch. The switch now has the address of Node B, too, so it forwards the packet directly to Node B. Node C sends informa ...
FCoE Overview - IEEE Entity Web Hosting
... FIP - Fibre Channel Initialization Protocol initiates Fabric Logins with FCoE switch (FCF) ...
... FIP - Fibre Channel Initialization Protocol initiates Fabric Logins with FCoE switch (FCF) ...
Ethernet
... ___________________ of the router has an _________________________________ Routing is the same as routing between any ...
... ___________________ of the router has an _________________________________ Routing is the same as routing between any ...
Module 8: Virtual LANs
... on the functions, project teams, or applications of the organization regardless of the physical location or connections to the network. All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connection or location. ...
... on the functions, project teams, or applications of the organization regardless of the physical location or connections to the network. All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connection or location. ...
Network Devices - courses.psu.edu
... • Provides message control and errorreporting services between two TCP/IP host and between a host server and gateway to the Internet • Routes periodically sends following messages – Destination unreachable – Buffer full – Hops – Pings – Traceroute ...
... • Provides message control and errorreporting services between two TCP/IP host and between a host server and gateway to the Internet • Routes periodically sends following messages – Destination unreachable – Buffer full – Hops – Pings – Traceroute ...
CCNA 3—Switching Basics and Intermediate Routing
... • Compare and contrast various forms of redundancy built into networks, and explain the advantages and disadvantages of redundancy incorporation ...
... • Compare and contrast various forms of redundancy built into networks, and explain the advantages and disadvantages of redundancy incorporation ...
Selecting Bridging, Switching, and Routing Protocols
... • Most common Ethernet environments • A transparent bridge (switch) connects one or more LAN segments so that end systems on different segments can communicate with each other transparently • Looks at the source address in each frame to learn location of network devices • It develops a switching tab ...
... • Most common Ethernet environments • A transparent bridge (switch) connects one or more LAN segments so that end systems on different segments can communicate with each other transparently • Looks at the source address in each frame to learn location of network devices • It develops a switching tab ...
VLANs - Lansing School District
... Require administrator to make changes Secure Easy to configure Straightforward to monitor Works well in which moves are controlled and managed ...
... Require administrator to make changes Secure Easy to configure Straightforward to monitor Works well in which moves are controlled and managed ...
Switches - Faculty - Genesee Community College
... Device needs to transmit. It “__________” for signals on the medium. If it finds signals – ______. If clear – __________. If the signals of one device are not detected by a second device, the second device may also start to ...
... Device needs to transmit. It “__________” for signals on the medium. If it finds signals – ______. If clear – __________. If the signals of one device are not detected by a second device, the second device may also start to ...
Routing
... • Routers do reverse path forwarding (RPF) check Explicit join (CBT, PIM-SM) • Receivers send join to rendezvous point (RP) • Senders send multicast data to RP, up the tree • RP fans out multicast data (its a meeting point) • Optimizations in PIM-SM to short-cut the RP • Shared tree versus source sp ...
... • Routers do reverse path forwarding (RPF) check Explicit join (CBT, PIM-SM) • Receivers send join to rendezvous point (RP) • Senders send multicast data to RP, up the tree • RP fans out multicast data (its a meeting point) • Optimizations in PIM-SM to short-cut the RP • Shared tree versus source sp ...
Document
... Ethernet bridges and switches can implement the IEEE 802.1D SpanningTree Protocol and use the spanning-tree algorithm to construct a loop free shortest path network. Radia Perlman “is the inventor of the spanning tree algorithm used by bridges (switches), and the mechanisms that make link state rout ...
... Ethernet bridges and switches can implement the IEEE 802.1D SpanningTree Protocol and use the spanning-tree algorithm to construct a loop free shortest path network. Radia Perlman “is the inventor of the spanning tree algorithm used by bridges (switches), and the mechanisms that make link state rout ...
University of California at Berkeley CS168, Homework 2
... 1e) [6 points] Consider the following network, with nodes A through J. The numbers indicate the link weights or costs (so shortest paths are paths with the lowest cumulative cost). In the following ...
... 1e) [6 points] Consider the following network, with nodes A through J. The numbers indicate the link weights or costs (so shortest paths are paths with the lowest cumulative cost). In the following ...
CCNA - College of DuPage
... all of its switch ports, where it reaches PC4 and S3. S3 does not forward the frame back to S2 over Trunk2 because of the blocked port. The Layer 2 loop is prevented. 1. PC1 sends a broadcast out onto the network. 2. The broadcast is then forwarded around the network, just as in the previous ani ...
... all of its switch ports, where it reaches PC4 and S3. S3 does not forward the frame back to S2 over Trunk2 because of the blocked port. The Layer 2 loop is prevented. 1. PC1 sends a broadcast out onto the network. 2. The broadcast is then forwarded around the network, just as in the previous ani ...
document
... • Interoperation among many different multipath routing protocols – Different switches and different networks may have different implementations ...
... • Interoperation among many different multipath routing protocols – Different switches and different networks may have different implementations ...
pptx - Cornell Computer Science
... Each pod consists of 12 racks with 48 machines each, and 48 individual 48-port GigE switches Place the 48 switches in a centralized rack Cables moves in sets of 12 from pod to pod and in sets of 48 from racks to pod switches opens additional opportunities for packing to reduce wiring ...
... Each pod consists of 12 racks with 48 machines each, and 48 individual 48-port GigE switches Place the 48 switches in a centralized rack Cables moves in sets of 12 from pod to pod and in sets of 48 from racks to pod switches opens additional opportunities for packing to reduce wiring ...
pdf,
... Each pod consists of 12 racks with 48 machines each, and 48 individual 48-port GigE switches Place the 48 switches in a centralized rack Cables moves in sets of 12 from pod to pod and in sets of 48 from racks to pod switches opens additional opportunities for packing to reduce wiring ...
... Each pod consists of 12 racks with 48 machines each, and 48 individual 48-port GigE switches Place the 48 switches in a centralized rack Cables moves in sets of 12 from pod to pod and in sets of 48 from racks to pod switches opens additional opportunities for packing to reduce wiring ...
PDF
... manager; and support for the Cisco FindIT Network Discovery Utility, all at a very affordable price. Its combination of business-class features, support for virtual networks that enable highly secure guest access, simple installation, and top-quality user experience takes basic connectivity for smal ...
... manager; and support for the Cisco FindIT Network Discovery Utility, all at a very affordable price. Its combination of business-class features, support for virtual networks that enable highly secure guest access, simple installation, and top-quality user experience takes basic connectivity for smal ...
lec6-L2-LAN
... when frame received, bridge “learns” location of sender: incoming LAN segment records sender/location pair in bridge table ...
... when frame received, bridge “learns” location of sender: incoming LAN segment records sender/location pair in bridge table ...
Parvus DuraNET 20-11
... out Ethernet, power, console, and zeroize signals, while integrated EMI/ power filtering is designed to meet power input voltage, spikes, surges, transients, and EMI/EMC compatibility requirements per MIL-STD-704F, MIL-STD-1275D, MIL-STD-461F, and RTCA/DO-160 compliance in civil and tactical ground ...
... out Ethernet, power, console, and zeroize signals, while integrated EMI/ power filtering is designed to meet power input voltage, spikes, surges, transients, and EMI/EMC compatibility requirements per MIL-STD-704F, MIL-STD-1275D, MIL-STD-461F, and RTCA/DO-160 compliance in civil and tactical ground ...
3rd Edition: Chapter 4
... flood and prune: reverse path forwarding, sourcebased tree RPF tree based on DVMRP’s own routing tables constructed by communicating DVMRP routers no assumptions about underlying unicast initial datagram to multicast group flooded everywhere via RPF ...
... flood and prune: reverse path forwarding, sourcebased tree RPF tree based on DVMRP’s own routing tables constructed by communicating DVMRP routers no assumptions about underlying unicast initial datagram to multicast group flooded everywhere via RPF ...
MEASUREMENT OF SPANNING TREE PERFORMANCE BETWEEN DIFFERENT PROTOCOLS
... for the process of optimization and fault tolerance to send data. STP is defined in the IEEE 802.1D (ZhangCun, 13). It is a link management protocol for network to provide path redundancy while preventing undesirable loops. To make Ethernet work better, it can only have one active path between two w ...
... for the process of optimization and fault tolerance to send data. STP is defined in the IEEE 802.1D (ZhangCun, 13). It is a link management protocol for network to provide path redundancy while preventing undesirable loops. To make Ethernet work better, it can only have one active path between two w ...
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is an older network protocol that ensures a loop-free topology for any bridged Ethernet local area network. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include spare (redundant) links to provide automatic backup paths if an active link fails, without the danger of bridge loops, or the need for manual enabling/disabling of these backup links.Spanning Tree Protocol (STP) was originally standardized as IEEE 802.1D, in 802.1d-1998, but much of the functionality (spanning tree, rapid spanning tree, multiple spanning tree) previously specified in 802.1D, 801.1s, 802.1w has been incorporated into IEEE 802.1Q-2014 which includes shortest path bridging, the IEEE sanctioned replacement for these spanning tree functions.As the name suggests, it creates a spanning tree within a network of connected layer-2 bridges (typically Ethernet switches), and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation.