Duplicate Address Detection in IPv6 Mobile Ad Hoc Network
... Unicasts RREP towards A C can allow D to set up a path towards S with Gratuitous RREP. KRnet2004 - MANET Implementation & Test ...
... Unicasts RREP towards A C can allow D to set up a path towards S with Gratuitous RREP. KRnet2004 - MANET Implementation & Test ...
OSI layers
... It standardizes network components to allow multiple vendor development and support. It allows different types of network hardware and software to communicate with each other. It prevents changes in one layer from affecting other layers. It divides network communication into smaller parts to make le ...
... It standardizes network components to allow multiple vendor development and support. It allows different types of network hardware and software to communicate with each other. It prevents changes in one layer from affecting other layers. It divides network communication into smaller parts to make le ...
Introducing the Specifications of the MEF
... • MEF 10.2 specifies three levels of Bandwidth Profile compliance for each individual Service Frame – Green: Service Frame subject to SLA performance guarantees – Yellow: Service Frame not subject to SLA performance guarantees, but will be forwarded on a “best effort” basis. They have lower priority ...
... • MEF 10.2 specifies three levels of Bandwidth Profile compliance for each individual Service Frame – Green: Service Frame subject to SLA performance guarantees – Yellow: Service Frame not subject to SLA performance guarantees, but will be forwarded on a “best effort” basis. They have lower priority ...
21CN PSTN – Separating speech and control
... • Offer exciting new services for end user faster than before • Reduce costs and grow cash cost savings - expected to amount to £1 billion per annum by 2008/9 ...
... • Offer exciting new services for end user faster than before • Reduce costs and grow cash cost savings - expected to amount to £1 billion per annum by 2008/9 ...
INS/Twine: A Scalable Peer-to-Peer Architecture for
... The architecture of INS/Twine has three layers, as shown in Figure 2. The top-most layer, the Resolver, interfaces with a local AVTree storage and query engine, which holds resource descriptions and implements query processing, returning sets of name-records corresponding to (partial) queries. When ...
... The architecture of INS/Twine has three layers, as shown in Figure 2. The top-most layer, the Resolver, interfaces with a local AVTree storage and query engine, which holds resource descriptions and implements query processing, returning sets of name-records corresponding to (partial) queries. When ...
Where is the collision domain?
... Connection to the hub consists of two pairs of twisted pair wire one for transmission and the other for receiving. Hub receives a bit from an adapter and sends it to all the other adapters without implementing any access method. does not do filtering (forward a frame into a specific destination or d ...
... Connection to the hub consists of two pairs of twisted pair wire one for transmission and the other for receiving. Hub receives a bit from an adapter and sends it to all the other adapters without implementing any access method. does not do filtering (forward a frame into a specific destination or d ...
cis185-ROUTE-lecture2-EIGRP-Part2
... Use the label to determine the next-hop for the packet. Do not need to examine the packet’s IP header Forwards packets based on the label. After a path has been established: Packets destined to the same endpoint with the same requirements can be forwarded based on these labels without a ro ...
... Use the label to determine the next-hop for the packet. Do not need to examine the packet’s IP header Forwards packets based on the label. After a path has been established: Packets destined to the same endpoint with the same requirements can be forwarded based on these labels without a ro ...
IPv6 basics pdf
... Stateless address auto-configuration (SLAAC) provides a convenient method to assign IP addresses to IPv6 nodes. This method does not require any human intervention from an IPv6 user. If you want to use IPv6 SLAAC on an IPv6 node, then it is important to connect that IPv6 node to a network with at le ...
... Stateless address auto-configuration (SLAAC) provides a convenient method to assign IP addresses to IPv6 nodes. This method does not require any human intervention from an IPv6 user. If you want to use IPv6 SLAAC on an IPv6 node, then it is important to connect that IPv6 node to a network with at le ...
Functional Requirements for Transport API
... ©2016 Open Networking Foundation. All rights reserved. Open Networking Foundation, the ONF symbol, and OpenFlow are registered trademarks of the Open Networking Foundation, in the United States and/or in other countries. All other brands, products, or service names are or may be trademarks or servic ...
... ©2016 Open Networking Foundation. All rights reserved. Open Networking Foundation, the ONF symbol, and OpenFlow are registered trademarks of the Open Networking Foundation, in the United States and/or in other countries. All other brands, products, or service names are or may be trademarks or servic ...
Mobile Communications
... 802.20 (Mobile Broadband Wireless Access) Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/ ...
... 802.20 (Mobile Broadband Wireless Access) Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/ ...
Data - WordPress.com
... 802.20 (Mobile Broadband Wireless Access) Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/ ...
... 802.20 (Mobile Broadband Wireless Access) Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/ ...
MPLS
... connectionless IP-based Internet providing the foundation for sophisticated and reliable QoS traffic ...
... connectionless IP-based Internet providing the foundation for sophisticated and reliable QoS traffic ...
Routing - La Salle University
... TCP/IP protocol, the number of hops a packet is allowed to make is kept in the packet header (in the TTL time-to-live field). Each router reduces the number by one. When the TTL reaches 0, the ...
... TCP/IP protocol, the number of hops a packet is allowed to make is kept in the packet header (in the TTL time-to-live field). Each router reduces the number by one. When the TTL reaches 0, the ...
5 Home network resource management
... framework may be null and directly have an interface with OSI application layer. Also some of the OSI layers may be null or some particular implementation can have little or no functionality at one or more of the following layers: transport, session and presentation layer. ...
... framework may be null and directly have an interface with OSI application layer. Also some of the OSI layers may be null or some particular implementation can have little or no functionality at one or more of the following layers: transport, session and presentation layer. ...
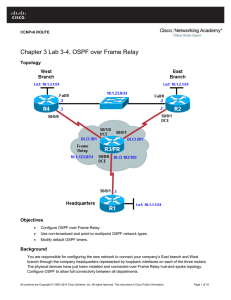
Chapter 3 Lab 3-4, OSPF over Frame Relay
... a. Configure the routers to send five hellos a second. __________________________________________________________________________________ __________________________________________________________________________________ ...
... a. Configure the routers to send five hellos a second. __________________________________________________________________________________ __________________________________________________________________________________ ...
AVT-84x User`s Manual Volume 1 - Advanced Vehicle Technologies
... AVT-843 CONNECTION TO HOST COMPUTER .......................................................................................................10 4.3.1 Ethernet Setup.......................................................................................................................................... ...
... AVT-843 CONNECTION TO HOST COMPUTER .......................................................................................................10 4.3.1 Ethernet Setup.......................................................................................................................................... ...
(Backup) MDR
... there exists a bidirectional neighbor that does not satisfy condition (a) or (b). If a Backup MDR receives a new LSA, it waits BackupWaitInterval seconds, and then floods the LSA back out the receiving interface if there exists a bidirectional neighbor that does not satisfy condition (a) or (b). An ...
... there exists a bidirectional neighbor that does not satisfy condition (a) or (b). If a Backup MDR receives a new LSA, it waits BackupWaitInterval seconds, and then floods the LSA back out the receiving interface if there exists a bidirectional neighbor that does not satisfy condition (a) or (b). An ...
Chapter 5 - Ethernet
... • If a data signal is absent, indicating that the media is free, the device transmits the data • If signals are then detected that show another device was transmitting at the same time, all devices stop sending and try again later • While Ethernet networks are designed with CSMA/CD technology, with ...
... • If a data signal is absent, indicating that the media is free, the device transmits the data • If signals are then detected that show another device was transmitting at the same time, all devices stop sending and try again later • While Ethernet networks are designed with CSMA/CD technology, with ...
VINEA: A Policy-based Virtual Network Embedding Architecture
... candidates [51, 63]. Consider for example solutions ignoring the resource discovery mechanism: the lifetime of a virtual network can range from few seconds to several months; assuming complete knowledge of the network state, and ignoring the overhead of resource discovery and the embedding time, may ...
... candidates [51, 63]. Consider for example solutions ignoring the resource discovery mechanism: the lifetime of a virtual network can range from few seconds to several months; assuming complete knowledge of the network state, and ignoring the overhead of resource discovery and the embedding time, may ...
discus - Cordis
... DISCUS aims to deliver core network bandwidth capability to the access edge so that direct connection to the core network is available from any access terminal fitted with the appropriate technology The ...
... DISCUS aims to deliver core network bandwidth capability to the access edge so that direct connection to the core network is available from any access terminal fitted with the appropriate technology The ...
Asynchronous Transfer Mode
... Cells are switched using either input or output queuing 5 bytes header – 4 bytes for Virtual Circuit and control info & 1 for HEC (Header Error Control) HEC is limited to the first 4 bytes of the header, due to the high reliability of fiber optics ...
... Cells are switched using either input or output queuing 5 bytes header – 4 bytes for Virtual Circuit and control info & 1 for HEC (Header Error Control) HEC is limited to the first 4 bytes of the header, due to the high reliability of fiber optics ...
Window Query Processing in Highly Dynamic Geo
... queries in HDSNs. In this paper, we use the following query execution plan as a vehicle to examine various research issues. 1. Routing the query towards an area specified by the query window; 2. Propagating the query within the query window; 3. Collecting and aggregating the data sensed in the query ...
... queries in HDSNs. In this paper, we use the following query execution plan as a vehicle to examine various research issues. 1. Routing the query towards an area specified by the query window; 2. Propagating the query within the query window; 3. Collecting and aggregating the data sensed in the query ...