Peer‐to‐peer systems and Distributed Hash Tables (DHTs) Mike Freedman
... – I.e. isomorphic under swaps of nodes – So rouUng from y to x looks just like rouUng from (y‐x) to 0 • The rouUng code at each node is the same • Moreover, under a random workload the rouUng responsibiliUes (congesUon) at each node are the same! ...
... – I.e. isomorphic under swaps of nodes – So rouUng from y to x looks just like rouUng from (y‐x) to 0 • The rouUng code at each node is the same • Moreover, under a random workload the rouUng responsibiliUes (congesUon) at each node are the same! ...
CS 5480/6480: Computer Networks – Spring 2012 Homework 4
... http://www.eng.utah.edu/~cs5480/rsvp_network_magazine.pdf. Answer the following questions that are based on this paper. (a) (2 points) Write two uses of reservation/path refresh messages. 1. Recover from an earlier lost reservation message. 2. Handle receiver/sender that goes away without teardown ( ...
... http://www.eng.utah.edu/~cs5480/rsvp_network_magazine.pdf. Answer the following questions that are based on this paper. (a) (2 points) Write two uses of reservation/path refresh messages. 1. Recover from an earlier lost reservation message. 2. Handle receiver/sender that goes away without teardown ( ...
Bandwidth Aided Topology Awareness in Unstructured P2p Networks
... The query is resent and forwarded until the minimum numbers of responses for the query are received from the nodes. Since a node can respond to not only its own data but also its neighbors the response is made with the identification of the node having the data. 1.4 Simulation This section provides ...
... The query is resent and forwarded until the minimum numbers of responses for the query are received from the nodes. Since a node can respond to not only its own data but also its neighbors the response is made with the identification of the node having the data. 1.4 Simulation This section provides ...
Cheese Factory
... • In the task distribution only the execution parameters i.e. configuration files are transferred • Also, currently the IP addresses of master nodes are restricted such that only certain IP addresses are allowed to start computations ...
... • In the task distribution only the execution parameters i.e. configuration files are transferred • Also, currently the IP addresses of master nodes are restricted such that only certain IP addresses are allowed to start computations ...
Grid: Scalable Ad Hoc Networking
... • Location proxies can communicate with each other using geographic forwarding and the local routing protocol • Nodes without location select proxies, and communicate through them using the local protocol • Nodes advertise proxy locations as their own • Proxies not special besides knowing locations ...
... • Location proxies can communicate with each other using geographic forwarding and the local routing protocol • Nodes without location select proxies, and communicate through them using the local protocol • Nodes advertise proxy locations as their own • Proxies not special besides knowing locations ...
Network
... • Datalink layer ensures reliable transfer of data across the physical medium. It also provides access control to the media in the case of local area networks. Examples are High-level Data Link Control (HDLC), LLC and SDLC • Network layer provides the upper layers with independence from the switchin ...
... • Datalink layer ensures reliable transfer of data across the physical medium. It also provides access control to the media in the case of local area networks. Examples are High-level Data Link Control (HDLC), LLC and SDLC • Network layer provides the upper layers with independence from the switchin ...
Anonymous Routing Protocol for Mobile Ad hoc Networks
... work in Sec. 2). It is clear that providing anonymity in ad hoc networks is important as users may wish to hide the fact that they are accessing some service or communicating with another user. Another application is hiding the location of users participating in the network. Hiding nodes that partic ...
... work in Sec. 2). It is clear that providing anonymity in ad hoc networks is important as users may wish to hide the fact that they are accessing some service or communicating with another user. Another application is hiding the location of users participating in the network. Hiding nodes that partic ...
Networked Systems
... o Point-to-point networks – transmission of lines connect pairs of hosts Main issues include topology of the network and routing of information from one node to another o Broadcast networks – all hosts share a single communication channel Satellite network – satellite provides a shared channel b ...
... o Point-to-point networks – transmission of lines connect pairs of hosts Main issues include topology of the network and routing of information from one node to another o Broadcast networks – all hosts share a single communication channel Satellite network – satellite provides a shared channel b ...
Chapter 11 Network Fundamentals
... of topology, ownership, geography and transmission technology? • What type of network does a grocery chain store needs in terms of topology, ownership, geography and transmission technology? ...
... of topology, ownership, geography and transmission technology? • What type of network does a grocery chain store needs in terms of topology, ownership, geography and transmission technology? ...
Computer Networks (CSC 345)
... into layers, each of which solves part of the network communication problem • These layers have several constraints, which ease the design problem • Network protocol designed to have a protocol or protocols for each layer ...
... into layers, each of which solves part of the network communication problem • These layers have several constraints, which ease the design problem • Network protocol designed to have a protocol or protocols for each layer ...
A Survey of Secure Wireless Ad Hoc Routing
... packet that includes the target D, its certificate (certS), a nonce N, and a timestamp t. 2. Each node that forwards this REQUEST checks the signature or signatures. Node C checks node B’s certificate certB, then checks the signature on the outer message. C then verifies the certificate certS for in ...
... packet that includes the target D, its certificate (certS), a nonce N, and a timestamp t. 2. Each node that forwards this REQUEST checks the signature or signatures. Node C checks node B’s certificate certB, then checks the signature on the outer message. C then verifies the certificate certS for in ...
MAC Part I - UCLA Computer Science
... Time is divided into equal size slots (= full packet size) a newly arriving station transmits a the beginning of the next slot if collision occurs (assume channel feedback, eg the receiver informs the source of a collision), the source retransmits the packet at each slot with probability P, until su ...
... Time is divided into equal size slots (= full packet size) a newly arriving station transmits a the beginning of the next slot if collision occurs (assume channel feedback, eg the receiver informs the source of a collision), the source retransmits the packet at each slot with probability P, until su ...
Part I: Introduction
... • After transmitting one or more packets (depending on the rules of the protocol), the node transmits a new token to the next node in one of 3 ways: 1.Single Packet Mode: Token is transmitted after receiving the last bit of ...
... • After transmitting one or more packets (depending on the rules of the protocol), the node transmits a new token to the next node in one of 3 ways: 1.Single Packet Mode: Token is transmitted after receiving the last bit of ...
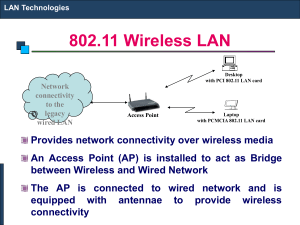
802.11 Wireless LAN
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
Communication Network Protocols ---
... taking care of any issues that might arise where data sent from one system needs to be viewed in a different way by the other system. It also takes care of any special processing that must be done to data from the time an application tries to send it until the time it is sent over the network. ...
... taking care of any issues that might arise where data sent from one system needs to be viewed in a different way by the other system. It also takes care of any special processing that must be done to data from the time an application tries to send it until the time it is sent over the network. ...
Slide 1
... Provides insight on the interplay between clustering and the small-world Captures the structure of many realistic networks Accounts for the high clustering of real networks ...
... Provides insight on the interplay between clustering and the small-world Captures the structure of many realistic networks Accounts for the high clustering of real networks ...
slides - Network and Systems Laboratory
... • Modify It to handle heterogeneity and robust to unexpected node departures • Two kinds of walks – OnlyInLinks – each node chooses uniformly randomly ...
... • Modify It to handle heterogeneity and robust to unexpected node departures • Two kinds of walks – OnlyInLinks – each node chooses uniformly randomly ...
3rd Edition: Chapter 4
... They look alike on the outside, but they’re very different on the inside. Each is designed to allow computers to connect to it. Each features a number of physical ports on the front or back of the unit that provide the connection points for these computers Hub - also known as a repeater, is a networ ...
... They look alike on the outside, but they’re very different on the inside. Each is designed to allow computers to connect to it. Each features a number of physical ports on the front or back of the unit that provide the connection points for these computers Hub - also known as a repeater, is a networ ...
MAC, Scheduling, IP …
... In CSMA, when there is a collision of two transmissions, it is detected only after the entire frames have been transmitted … irrespective of when the collision occurs CSMA/CD includes a collision detection mechanism that can detect collisions even as stations are transmitting Transmitting stations t ...
... In CSMA, when there is a collision of two transmissions, it is detected only after the entire frames have been transmitted … irrespective of when the collision occurs CSMA/CD includes a collision detection mechanism that can detect collisions even as stations are transmitting Transmitting stations t ...