Repeaters and Hubs
... o Flexible • Ports from multiple switches or segments • Use any end node type o Reasons for using VLAN • Separating user groups • Isolating connections • Identifying priority device groups • Grouping legacy protocol devices • Separating large network into smaller subnets ...
... o Flexible • Ports from multiple switches or segments • Use any end node type o Reasons for using VLAN • Separating user groups • Isolating connections • Identifying priority device groups • Grouping legacy protocol devices • Separating large network into smaller subnets ...
6.2 Networks (AQA)
... Internet has a unique IP address Each computer on the Internet has to have TCP/IP ...
... Internet has a unique IP address Each computer on the Internet has to have TCP/IP ...
Securing Mobile Ad Hoc Networks Using Spread Spectrum Tech
... inject or reply control and data traffic, generate flooding or spurious messages and avoid complying with the employed protocols. The impact of such a behavior can be extremely severe, especially since the cooperation of all the nodes is somehow replacing the functionality of the non-existing fixed ...
... inject or reply control and data traffic, generate flooding or spurious messages and avoid complying with the employed protocols. The impact of such a behavior can be extremely severe, especially since the cooperation of all the nodes is somehow replacing the functionality of the non-existing fixed ...
Chapter 07 slides
... Reliability is assured through the additional fields contained within the TCP header that offer flow control, acknowledgments of successful receipt of packets after error checking, retransmission of packets as required, and proper sequencing of packets ...
... Reliability is assured through the additional fields contained within the TCP header that offer flow control, acknowledgments of successful receipt of packets after error checking, retransmission of packets as required, and proper sequencing of packets ...
Small-College Supercomputing: Building A Beowulf
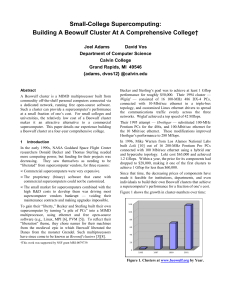
... x86 CPUs (e.g., Intel, AMD) that were current when the clusters were built. The clock speeds of the CPUs have increased over the years, in keeping with CPU evolution. Main and secondary memory sizes have also increased over the years, as the price/bit has dropped. Many clusters use the processor far ...
... x86 CPUs (e.g., Intel, AMD) that were current when the clusters were built. The clock speeds of the CPUs have increased over the years, in keeping with CPU evolution. Main and secondary memory sizes have also increased over the years, as the price/bit has dropped. Many clusters use the processor far ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... Communication technology has become constraint for future requirement as the growth of the communication industry is larger and growing complex. Different modes as mobile, wired, wireless, adhoc, supports growth of the communication industry but with certain limits. Mobility plays a vital role in wi ...
... Communication technology has become constraint for future requirement as the growth of the communication industry is larger and growing complex. Different modes as mobile, wired, wireless, adhoc, supports growth of the communication industry but with certain limits. Mobility plays a vital role in wi ...
Systematic Design of Space-Time Trellis Codes for Wireless
... Provides the “virtual network” image of an internet (this layer shields the higher levels from the physical network architecture below it). ...
... Provides the “virtual network” image of an internet (this layer shields the higher levels from the physical network architecture below it). ...
The OSI Model - Barry University, Miami Shores, Florida
... • Error control. The data link layer adds reliability to the physical layer by adding mechanisms to detect and retransmit damaged or lost frames. Error control is normally achieved through a trailer to the end of the frame. • Access Control. When two or more devices are connected to the same link, d ...
... • Error control. The data link layer adds reliability to the physical layer by adding mechanisms to detect and retransmit damaged or lost frames. Error control is normally achieved through a trailer to the end of the frame. • Access Control. When two or more devices are connected to the same link, d ...
II. General presentation of Voice over IP
... Analog/Digital (A/D) converter. And then submitted to a multiple compression process. There are various techniques to do this. The most popular ones are standardized in the ITU-T G-series. The most commonly used codecs in VOIP systems are: G.711 PCM [7], G.726 ADPCM [7], G.728 LD-CELP [8], and G. 72 ...
... Analog/Digital (A/D) converter. And then submitted to a multiple compression process. There are various techniques to do this. The most popular ones are standardized in the ITU-T G-series. The most commonly used codecs in VOIP systems are: G.711 PCM [7], G.726 ADPCM [7], G.728 LD-CELP [8], and G. 72 ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... In this paper, we examine the possibility of deploying an intelligent and real-time adaptive traffic signal controller, which receives information from vehicles, such as the vehicle’s position and speed, and then utilizes this information to optimize the traffic signal scheduling at the intersection ...
... In this paper, we examine the possibility of deploying an intelligent and real-time adaptive traffic signal controller, which receives information from vehicles, such as the vehicle’s position and speed, and then utilizes this information to optimize the traffic signal scheduling at the intersection ...
R3-010121 Flow Classification
... In DRNC and Node B, such a classification can be envisaged if relevant RNL information is available. However QoS requirements as extensive as RAB parameters may not be available in those nodes. RNL information is assumed to be unreachable in intermediate transport nodes that are UTRAN agnostic. In t ...
... In DRNC and Node B, such a classification can be envisaged if relevant RNL information is available. However QoS requirements as extensive as RAB parameters may not be available in those nodes. RNL information is assumed to be unreachable in intermediate transport nodes that are UTRAN agnostic. In t ...
HotViewTM HotView™
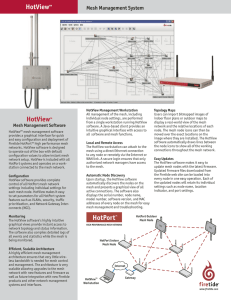
... The main HotView screen provides a graphical view of the mesh network, displaying an icon for each of the nodes with lines showing the various connections among the nodes. Icons can be moved to any position on the screen, allowing users to place them in their relative positions over the background i ...
... The main HotView screen provides a graphical view of the mesh network, displaying an icon for each of the nodes with lines showing the various connections among the nodes. Icons can be moved to any position on the screen, allowing users to place them in their relative positions over the background i ...
Protocols and Interaction Models for Web Services
... Computers connect to a shared coaxial cable through NICs Packets transmitted by one NIC can be received by all others: broadcast communication But, since packets have destination addresses, only destination NIC will (typically) copy the packet to the computer’s main memory ...
... Computers connect to a shared coaxial cable through NICs Packets transmitted by one NIC can be received by all others: broadcast communication But, since packets have destination addresses, only destination NIC will (typically) copy the packet to the computer’s main memory ...
Formal description and analysis of a distributed
... In this paper, we define a distributed abstract state machine (DASM) model [14,17] of the network or routing layer protocol for mobile ad hoc networks. In conjunction with the chosen routing strategy, we propose a distributed logical topology based location service (LTLS) protocol and give a formal d ...
... In this paper, we define a distributed abstract state machine (DASM) model [14,17] of the network or routing layer protocol for mobile ad hoc networks. In conjunction with the chosen routing strategy, we propose a distributed logical topology based location service (LTLS) protocol and give a formal d ...
Binary Soliton-Like Rateless Coding for the Y
... Introduction In today’s telecommunication applications, content can originate ...
... Introduction In today’s telecommunication applications, content can originate ...
ppt
... ARP tables are stored in RAM memory, where the cached information is maintained automatically on each of the devices. Each device on a network maintains its own ARP table. >arp -a When a network device wants to send data across the network, it uses information provided by the ARP table. When a sourc ...
... ARP tables are stored in RAM memory, where the cached information is maintained automatically on each of the devices. Each device on a network maintains its own ARP table. >arp -a When a network device wants to send data across the network, it uses information provided by the ARP table. When a sourc ...
ppt
... overlay participation (e.g., should not be O(N)) DHT mechanism should be fully distributed (no centralized point that bottlenecks throughput or can act as single point of failure) DHT mechanism should gracefully handle nodes joining/leaving the overlay need to repartition the range space over ...
... overlay participation (e.g., should not be O(N)) DHT mechanism should be fully distributed (no centralized point that bottlenecks throughput or can act as single point of failure) DHT mechanism should gracefully handle nodes joining/leaving the overlay need to repartition the range space over ...
module_52
... Providing CL, best-effort delivery of datagrams through an internetwork; and – Fragmentation: Providing fragmentation and reassembly of datagrams to support data links with different maximum transmission unit (MTU) sizes. ...
... Providing CL, best-effort delivery of datagrams through an internetwork; and – Fragmentation: Providing fragmentation and reassembly of datagrams to support data links with different maximum transmission unit (MTU) sizes. ...
Banana Tree Protocol, an End-host Multicast Protocol
... bootstrap process to join the group, may not scale well beyond a few hundred users, and will likely use more network resources than IP Multicast. However, it does solve most of the problems with IP Multicast: it can be easily deployed since it can be implemented at the user level, the address space ...
... bootstrap process to join the group, may not scale well beyond a few hundred users, and will likely use more network resources than IP Multicast. However, it does solve most of the problems with IP Multicast: it can be easily deployed since it can be implemented at the user level, the address space ...