* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Context Based Access Control Lists (CBAC)
Net neutrality law wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Airborne Networking wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Computer security wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
TCP congestion control wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Internet protocol suite wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cisco IOS Firewall
(CBAC-Context Based Access Control)
Cisco IOS Firewall
(CBAC-Context Base Access Control)
Introduction
• Basic Definition
Benefits
• Monitor Traffic
• (NAT)
Methods of Attack
•
•
•
•
•
Port Scans, ping sweeps
Packet Sniffers
IP spoofing
Application Level Attacks
Denial of Service Attacks
Types of Firewalls
• Basic Router Security
• Packet Filtering Firewalls
• Stateful Inspection Firewalls
Cisco IOS Feature Set
• Security specific option for IOS software.
• Version of the Cisco IOS with an add-on
feature set that can be run on several router
platforms.
• Affordability
Router Requirements
• Cisco IOS software release IOS 11.2(11)P and
above.
• Generally requires more memory, both in terms
of flash and RAM.
Secure Cisco Router
• Ability to configure a Cisco router in a fairly
secure fashion using plain old ACLs
• ACLs provide granular packet filtering at layers
2, 3, and 4 only.
• IOS firewall provides this level of traffic
filtering and more.
What CBAC Does
•
•
•
•
Traffic Filtering
Traffic Inspection
Alerts and Audit Trails
Intrusion detection
Traffic Filtering
• Context-Based Access Control intelligently filters TCP
and UDP packets.
• Without CBAC, traffic filtering is limited to access-list
iplementations that examine packets at the network
layer.
• CBAC examines not only network and transport layer
info, but also examines appication layer protocol info,
such as FTP connection info.
Traffic Inpsection
• CBAC inspects traffic that travels through the
firewall to discover and manage state
information for TCP and UDP sessions.
• This creates temporary openings in the firewall
ACLs to allow return traffic originating from
within the internal network.
• Prevents SYN-flood and DoS attacks.
Alerts and Audit Trails
• Generates real-time alerts and audit trails on
events tracked by the firewall.
• Uses SYSLOG to track all network transactions
Intrusion Detection
• Cisco IOS IDS identifies 59 of the most
common attacks using signatures to detect
patterns of misuse in network traffic.
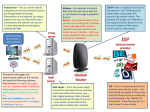
CBAC Opens Temporary Holes in
Firewall Access Lists
Configuring CBAC
• A common setup is to configure ACLs and
CBAC inbound on the external interface of an
internet router to protect a private network from
harmful traffic initiated from the internet.
• You’re main concern is to allow in only return
traffic from sessions initiated internally.
Cont. Config
• Router (config)# Access-list 105 deny tcp
any any
• Router (config)# Access-list 105 deny udp
any any
• Router (config)# Interface serial 0/0
• Router (config)# Ip address-group 105 in
• The previous statements block all TCP and UDP traffic
when applied inbound on the external interface. This
provides a blanket form of inspection across all TCP
and UDP traffic.
By applying access list 105 to the external interface, we
ensured that Internet traffic was intercepted as soon as
it reached the Internet router. we could also exercise a
more granular level of control by specifying certain
application protocols, as this example demonstrates:
• Router (config)# Access-list 105 deny tcp any any
eq smtp
• This statement blocks all SMTP traffic to the internal
network. It would need to occur in the access list before
the previous TCP blanket statements or it would have
little effect.
•
The next step in this process is to define the
timeout and threshold values for CBAC to use
when tracking sessions. You can configure
several values to enhance CBAC’s ability to
defend against network attacks. Most of the
timeout and threshold settings have default
values that will generally suffice in a startup
scenario. Many of the timeouts and thresholds
control how the router responds to DoS attacks.
(we’ll save a more in-depth discussion of
timer/threshold configuration for another time.)
• Keep in mind that CBAC does not inspect
ICMP, only TCP and UDP. Accordingly, you’ll
need to add inbound ACL entries for
appropriate ICMP restrictions. Consider adding
these ICMP entries to your ACL. They’ll make it
possible for those inside your network to ping
hosts on the Internet, as well as allow your
router to respond to proper ICMP traffic.
• Up to this point, we’ve shown you how to
configure entries for the extended access list and
apply that configuration to the inbound traffic
on the external interface. The ACL has entries to
block all the traffic we want to inspect with
CBAC. Rather than modify the timeout and
threshold settings, we went with the defaults. we
recommend starting with the defaults and tuning
these as you go. It’s not a good idea to make
changes to these settings if you don’t understand
how those changes will affect firewall operation.
Next, we defined the actual inspection rule that
governs which application layer protocols are
examined.
• Inspection rule command structure
• ip inspect name inspection-name
protocol [alert {on | off}] [audit-trail
{on | off}] [timeout seconds]
• This is a global config mode command. It
requires that you specify a name, protocol, alert
setting, auditing, and the timeout value in
seconds
• Applying the inspect command
– Router (config)# ip inspect name myfw
tcp alert on audit-trail on
• We’ve named the rule myfw, specified TCP as the
protocol to inspect, and activated the alert and auditing
options. Notice the alert and audit-trail options. This
requires a Syslog system to send the information to.
Although that configuration is beyond the scope of this
article, I do recommend using auditing for logging all
firewall activity. At this point, I’ll apply the rule to the
external interface, Serial0, with the following:
Router (config)# Interface serial0/0
Router (config-if)# ip inspect myfw out
• Notice that we have applied the inspection rule
outbound on the external interface. It will track
sessions started internally and heading out
through the external interface, bound for the
Internet or some other external network.
• If you have difficulty during CBAC configuration, you
can disable and reset all related settings using the
following global mode command. This won’t remove
your extended access list configured on the outside
interface. If you turn off inspection, keep in mind that
it will most likely halt all traffic entering your private
network because the access list is filtering most, if not
all, inbound traffic at the external interface. Turning off
inspection is as simple as:
• Router (config)# no ip inspect
• That command will remove all the inspection
information from the configuration, including
the filter statements and command line that
applies it to the interface.
• Now that the basic configuration details are out of the
way, let’s look at an
• Configuration with ACLs and CBAC inspection
activated
!generic inspection of UDP and TCP, and application
inspection for http, smtp, ftp
ip inspect name myfw tcp alert on audit-trail on
ip inspect name myfw udp alert on audit-trail on
ip inspect name myfw http
ip inspect name myfw smtp
ip inspect name myfw ftp
access list applied inbound to external interface
access-list 105 deny tcp any any
access-list 105 deny udp any any
access-list 105 permit icmp any any unreachable
access-list 105 permit icmp any any echo-reply
access-list 105 permit icmp any any packet-too-big
access-list 105 permit icmp any any time-exceeded
access-list 105 permit icmp any any traceroute
access-list 105 permit icmp any any administrativelyprohibited
access-list 105 permit icmp any any echo
access-list 105 deny icmp any any
!external interface interface serial0
ip access-group 105 in
ip inspect myfw out
• This basic CBAC configuration will allow only
limited ICMP information through the firewall
router because access list 101 is applied
incoming to the external interface. The
inspection rule, filter1, will allow internal users
to start outbound WWW sessions via HTTP and
track the sessions, opening return points in the
static, extended access list. This is also true for
FTP and SMTP. If, in the future, I choose to
allow users RealAudio or NetMeeting access, I
would simply add ip inspect name statements,
using filter1 as the name.
• To change the inspection rule, you can easily add
or remove line items. To add statements, simply
use the ip inspect name command, using the
same user-defined rule name. If you need to
remove a line, use the no form of the ip inspect
name command, as follows:
Router (config)# ip inspect myfw tcp
Router (config)# no ip inspect myfw tcp
• If at any point you want to check the
configuration, you can get CBAC setup details
using the show ip inspect command, as in the
following:
Router# show ip inspect all
• The all parameter will display information such
as current configuration of inspection, as well as
current sessions traversing the firewall.
General firewall configuration
recommendations
• Simply installing the IOS firewall software does
not fully ensure a secure network. The router
and CBAC must be configured properly to
secure the private network from unwanted
access. With this in mind, you’ll want to apply
other well-known protections to the firewall
router. Among these are broadcast protection
and antispoofing measures. Here are some
recommended measures:
General firewall configuration
recommendations
•
•
•
•
•
•
•
No ip directed-broadcast
No icmp redirect
No ip redirect
No service finger
No cdp run
No ip source-route
Access-list 100 deny ip {internal network range}
any
General firewall configuration
recommendations
• Don’t consider this to be a complete list of precautions.
This is merely a sample of the types of settings to
implement for a secure network environment. You’ll
also want to check the Cisco support Web site for
current security recommendations for edge routers. For
instance, Cisco recently acknowledged a rather serious
security issue for routers running the ip http service. I
recommend checking the security area of the Cisco
support Web site regularly to evaluate any potential
vulnerability in your router/IOS combination and
configuration attributes.
Summary
• Although the IOS firewall provides a higher level of
security than the standard access list approach, like
other firewalls, it shouldn’t be considered invulnerable.
A determined hacker may be able to find holes in the
most secure of systems. I’ve demonstrated the strong
security features of CBAC, but you may want to
consider a dual firewall approach if your security needs
are highly demanding.
Summary
• When implementing CBAC, consider its limitations
carefully. For instance, it will handle inspection of FTP
data channels only in the range of 1024 to 65535. Also,
if you’re using IPSec, carefully plan how it will interact
with the IOS firewall router. Keep in mind the
strengths and configuration options, which are plentiful.
For example, CBAC can be used as an extranet
protection method when your network is connected to
a business partner’s network. In this manner, it would
inspect traffic in both directions, protecting both
networks from unapproved access. You can also guard
against traffic leaving the network by applying
inspection to outbound traffic