* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network and Perimeter Security
Computer security wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Wireless security wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Airborne Networking wikipedia , lookup
Network tap wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
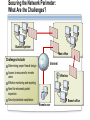
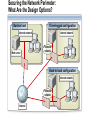
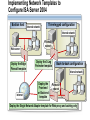
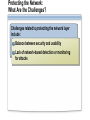
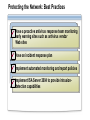
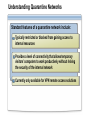
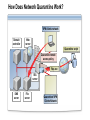
Network and Perimeter Security Paula Kiernan Senior Consultant Ward Solutions Session Overview Network Perimeter Security Protecting the Network Virtual Private Networking Purpose and Limitations of Perimeter Defenses Properly configured firewalls and border routers are the cornerstone for perimeter security The Internet and mobility increase security risks VPNs have exposed a destructive, pernicious entry point for viruses and worms in many organizations Traditional packet-filtering firewalls only block network ports and computer addresses Most modern attacks occur at the application layer Securing the Network Perimeter: What Are the Challenges? Business partner Main office Challenges Include: Determining proper firewall design Internet Access to resources for remote users Wireless Effective monitoring and reporting Need for enhanced packet inspection Security standards compliance Remote user Branch office What Firewalls Do NOT Protect Against Malicious traffic that is passed on open ports and not inspected by the firewall Any traffic that passes through an encrypted tunnel or session Attacks after a network has been penetrated Traffic that appears legitimate Users and administrators who intentionally or accidentally install viruses Administrators who use weak passwords Securing the Network Perimeter: What Are the Design Options? Bastion host Three-legged configuration Internal network Web server Internal network Perimeter network Back-to-back configuration Internal network Perimeter network Internet Firewall Requirements: Multiple-Layer Filtering Packet filtering: Filters packets based on information in the network and transport layer headers Enables fast packet inspection, but cannot detect higher-level attacks Stateful filtering: Filters packets based on the TCP session information Ensures that only packets that are part of a valid session are accepted, but cannot inspect application data Application filtering: Filters packets based on the application payload in network packets Can prevent malicious attacks and enforce user policies Configuring ISA Server to Secure the Network Perimeter Use ISA Server to: Provide firewall functionality Publish internal resources such as Web or Exchange servers Implement multilayer packet inspection and filtering Provide VPN access for remote users and sites Provide proxy and caching services LAN Web Server Web Server ISA Server VPN Server Internet User Exchange Server Remote User Implementing Network Templates to Configure ISA Server 2004 Bastion host Internal network Three-legged configuration Internal network Web server Deploy the Edge Firewall template Internet Perimeter network Deploy the 3-Leg Perimeter template Back-to-back configuration Internal network Deploy the Front end or Back end template Perimeter network Deploy the Single Network Adapter template for Web proxy and caching only Session Overview Network Perimeter Security Protecting the Network Virtual Private Networking Protecting the Network: What Are the Challenges? Challenges related to protecting the network layer include: Balance between security and usability Lack of network-based detection or monitoring for attacks Implementing Network-Based Intrusion-Detection Systems Network-based intrusion-detection system Provides rapid detection and reporting of external malware attacks Important points to note: Network-based intrusion-detection systems are only as good as the process that is followed once an intrusion is detected ISA Server 2004 provides network-based intrusiondetection abilities Implementing Application Layer Filtering Application layer filtering includes the following: Web browsing and e-mail can be scanned to ensure that content specific to each does not contain illegitimate data Deep content analyses, including the ability to detect, inspect, and validate traffic using any port and protocol Protecting the Network: Best Practices Have a proactive antivirus response team monitoring early warning sites such as antivirus vendor Web sites Have an incident response plan Implement automated monitoring and report policies Implement ISA Server 2004 to provide intrusiondetection capabilities Session Overview Network Perimeter Security Protecting the Network Virtual Private Networking Virtual Private Networking: What Are the Challenges? VPNs provide a secure option for communicating across a public network VPNS are used in two primary scenarios: Network access for remote clients Network access between sites VPN quarantine control provides an additional level of security by providing the ability to check the configuration of the VPN client machines before allowing them access to the organization’s network Understanding Quarantine Networks Standard features of a quarantine network include: Typically restricted or blocked from gaining access to internal resources Provides a level of connectivity that allows temporary visitors’ computers to work productively without risking the security of the internal network Currently only available for VPN remote access solutions How Does Network Quarantine Work? VPN VPN Clients clients network Network Domain Controller controller Web Server server Quarantine script Quarantine remote access policy RQC.exe Rqc.exe ISA Server server DNS Server server File Server server Quarantined VPN Quarantine VPN Clients Network Session Summary configured firewalls and border routers are the cornerstone Properly for perimeter security Use an appropriate firewall design Firewalls do not protect against bad security practices Implement a firewall that provides multiple layer filtering ISA Server 2004 provides network-based intrusion-detection abilities VPN quarantine control provides an additional level of security Next Steps Find additional security training events: http://www.microsoft.com/seminar/events/security.mspx Sign up for security communications: http://www.microsoft.com/technet/security/signup/default. mspx Get additional security information on ISA Server: http://www.microsoft.com/technet/security/prodtech/isa/ default.mspx Questions and Answers [email protected] www.ward.ie