* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download 14-Wireless-Security - Communications Systems Center
Survey
Document related concepts
Transcript
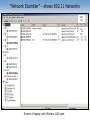
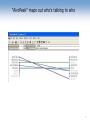
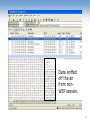
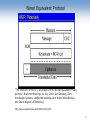
Security Issues Raised by Wireless LANs Dr. John A. Copeland* Communications Systems Center Georgia Tech Electrical & Computer Engineering www.csc.gatech.edu [email protected] *Dr. Copeland is also a founder of Lancope, Inc., www.lancope.com Network Tunnels Modems Internet VPNs Wireless Hubs 2 Network Tunnels http://www.telecommagazine.com/default.asp?journalid=3&func=articles&page=0203t11&year=2002&month=3 3 Network Tunnels Anyone can convert their cube or office Ethernet jack into a Wireless Hub for their Laptop (and a public entry point into the Network) IEEE 802.11b Wireless PC Card - $ 19.99 Linksys Etherfast Wireless AP + Cable/DSL Router with 4-Port Switch - $ 44.99 4 [ The Atlanta Journal-Constitution: 3/31/02 ] Wireless systems are simple to hack Terrorists could use techniques to attack airliners By DON PLUMMER Atlanta Journal-Constitution Staff Writer (Bill Corbitt) sits in his car in the short-term parking lot at an airport eating a sandwich, a Pringles can balanced on the dashboard. After Corbitt left Hartsfield Airport, he located more than 100 wireless networks in an hour of driving around Atlanta. He did not actually break into any of them but later demonstrated how he could by intercepting signals from several wireless systems in use at The Atlanta JournalConstitution. "Some of these people are even transmitting their names and the exact locations of the wireless portals,” Corbitt said, pointing out the identifiers as they appeared on the screen of his laptop. Of the 120 wireless systems located, only 32 had activated the encryption protection included with the wireless software. Bill Corbitt, Bulwarkz Defensive Solutions http://www.accessatlanta.com/ajc/news/0302/31wireless.html 5 “Network Stumbler” - shows 802.11 Networks WEP ON No No Screen of laptop with Wireless LAN card “AiroPeek” maps out who’s talking to who 7 Data sniffed off the air from nonWEP session. 8 AirSnort - a tool for Cracking WEP Messages AirSnort is a wireless LAN (WLAN) tool which recovers encryption keys. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered. 802.11b, using the Wired Equivalent Protocol (WEP), is crippled with numerous security flaws. Most damning of these is the weakness described in " Weaknesses in the Key Scheduling Algorithm of RC4 " by Scott Fluhrer, Itsik Mantin and Adi Shamir. Adam Stubblefield was the first to implement this attack, but he has not made his software public. AirSnort, along with WEPCrack, which was released about the same time as AirSnort, are the first publicly available implementaions of this attack. AirSnort requires approximately 5-10 million encrypted packets to be gathered. Once enough packets have been gathered, AirSnort can guess the encryption password in under a second. http://airsnort.sourceforge.net 9 How Does “Wired Equivalent Protocol (WEP) Work” What’s wrong with it? 10 Wired Equivalent Protocol “The Insecurity of 802.11, an analysis of the Wired Equivalent Privacy protocol”, Black Hat Briefings, 11 July, 2001, Ian Goldberg, ZeroKnowledge Systems, [email protected] 9with Nikita Borisov and David Wagner, UC Berkeley). http://www.cypherpunks.ca/bh2001/index.html 11 The One-Time Pad The most secure encryption technique is a “One-Time Pad.” WEP uses the RC4 encryption algorithm (with a 40 or 80 bit key) to generate a stream of random looking bits, Pi. These are XORed with the message bits, Mi, to produce the cyphertext bits, Ci Ci = Mi (+) Pi The receiver has the same key, and can generate a duplicate “pad”, Pi, and recover the original plaintext message, Mi. Ci (+) Pi = Mi (+) Pi (+) Pi = Mi since Pi (+) Pi = 1 and Mi (+) 1 = Mi 12 “Two-Time” Pad Problem The least secure encryption technique is a “One-Time Pad” used twice (or repeatedly). Consider two intercepted messages (C and D are encrypted M and N) encrypted with the same pad: C = M (+) P and D = N (+) P The cracker can XOR these together to get M (+) N: C (+) D = M (+) P (+) N (+) P = M (+) N Whenever a byte in M (+) N is zero, M & N have the same byte. One of six bytes in English text is “space”. so one in 36 bytes in M+N is zero indicating both text strings have spaces there. Given several thousand characters of M+N, the messages can be deciphered. Then the key sequence can be found: P = N (+) D. 13 “Two-Time” Pad Problem The pad, or keystream, for WEP is RC4(v,k) which depends only on v and k. “k” is a shared secret that changes rarely, if ever (in most systems every user uses the same value of k). So the keystream depends only on the 24-bit value of v. Since v is transmitted in the clear, the Cracker collects messages until he has two with the same value of v, then he is “in.” There are 2^24 = 16 million different values of v, but because of the “Birthday Effect,” he is likely to have two that match after collecting only about 6,000 messages. Number of pairs = 6000 x 5999 / 2 Even worse, Goldberg reports that all the 802.11 cards observed reset their random number generator for v each time they are activated, meaning they reuse the same sequence of v values (2002). 14 Defense Use the 112-bit key mode, rather than no key or 56-bit key. Use an access list of MAC (Ethernet) addresses at the hub. Use a new hub that has WPA, or IEEE 802.11i, and only network cards that are fully compatible. Use RADIUS authentication. Use a vendor’s equipment that has a proprietary security feature. 15 Wi-Fi Protected Access (WPA replaces WEP) IEEE 802.1x authentication is required. TKIP encryption is used (unique unicast key) 8-bit “Michael” Message Integrity Check (MIC) Frame counter prevents replay attacks AES is optional. Some card CPU’s can not manage. Can support older WEP cards (but no dynamic keys) 802.11 Beacon Frames contain a WEP info element. WPA is currently supported by Windows XP and Apple 16 Process Application Defense - Higher Level Secure Protocols Router Buffers Packets that need to be forwarded (based on IP address). Network Layer (IP) IPsec 802.11 Link Layer 802.11 Phys. Layer WEP Application SSL SSL Transport Layer (TCP,UDP) Process Transport Layer (TCP,UDP) Network Layer (IP) Network Layer 802.11 Link Layer Network Layer Ethernet Data Link Layer WEP Ethernet 802.11 Phys. Layer Phys. Layer IPsec Ethernet Data-Link Layer Ethernet Phys. Layer 17 Defense - War Driving Patrol the Premises Frequently looking for Rogue Wireless Signals Purchase only 802.11 Hubs and PC Cards that have the soon-to-be improved Security standards, or flash memory and can be field upgraded. 18 Wireless Sub-Nets can Safely be part of Corporate Networks - if Properly Isolated IDS Wireless Hub Wireless Subnets should be treated like attachments to the Web, isolated by Firewalls and Intrusion Detection Systems 19