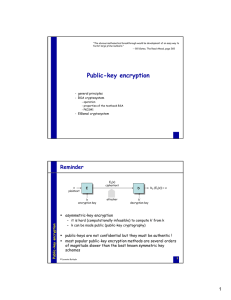
Public-key encryption
... – assume that the attacker wants to decrypt c = me mod n intended for Alice – assume that Alice will decrypt arbitrary ciphertext for the attacker, except c – the attacker can select a random number r and submit c⋅re mod n to Alice for decryption – since (c⋅re)d ≡ cd⋅red ≡ m⋅r (mod n), the attacker ...
... – assume that the attacker wants to decrypt c = me mod n intended for Alice – assume that Alice will decrypt arbitrary ciphertext for the attacker, except c – the attacker can select a random number r and submit c⋅re mod n to Alice for decryption – since (c⋅re)d ≡ cd⋅red ≡ m⋅r (mod n), the attacker ...
Section2.3
... alphabet is obtained by writing the letters of the resulting array column by column (starting with column 1) below the plaintext alphabet. ...
... alphabet is obtained by writing the letters of the resulting array column by column (starting with column 1) below the plaintext alphabet. ...
14-Wireless-Security - Communications Systems Center
... AirSnort is a wireless LAN (WLAN) tool which recovers encryption keys. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered. 802.11b, using the Wired Equivalent Protocol (WEP), is crippled with numerous security flaws. Most damn ...
... AirSnort is a wireless LAN (WLAN) tool which recovers encryption keys. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered. 802.11b, using the Wired Equivalent Protocol (WEP), is crippled with numerous security flaws. Most damn ...