* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download LAN / WAN / Extranet และ Network Topology แบบต่าง ๆ
Survey
Document related concepts
Computer security wikipedia , lookup
Bus (computing) wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
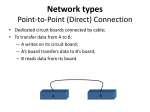
Deep packet inspection wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Transcript
LAN / WAN / Extranet and Network Topology 1 Motivation Local Area Networks (LAN) were motivated by: – Decreasing computer size – Decreasing computer cost – Realizing computers could help with many tasks 2 Interchangeable Media The first data transfers: – Used: • Magnetic tapes • Disks Data transferred between computers in a method similar to using floppy disks. 3 LAN Generations First – CSMA/CD and token ring – Terminal to host and client server – Moderate data rates Second – FDDI – Backbone – High performance workstations Third – ATM – Aggregate throughput and real time support for 4 multimedia applications Third Generation LANs Support for multiple guaranteed classes of service – Live video may need 2Mbps – File transfer can use background class Scalable throughput – Both aggregate and per host Facilitate LAN/WAN internetworking 5 LAN technologies MAC protocols used in LANs, to control access to the channel Token Rings: IEEE 802.5 (IBM token ring), for computer room, or Department connectivity, up to 16Mbps; FDDI (Fiber Distributed Data Interface), for Campus and Metro connectivity, up to 200 stations, at 100Mbps. Ethernets: employ the CSMA/CD protocol; 10Mbps (IEEE 802.3), Fast E-net (100Mbps), Giga E-net (1,000 Mbps); by far the most popular LAN technology 6 A Computer Consists Of Circuit Boards Inside a computer are electronic components on circuit boards. – Containing electronic components – Containing wires Computers having different circuit boards for external devices. 7 Circuit Boards Plug Into A Computer Computers are built so it contains a set of sockets. – Using wires to connect sockets together – Using wires to carry power and data – Plugging circuit boards into sockets to control external devices 8 Illustrations of the components visible in a computer when the cover has been removed. A circuit board can plug into each socket; wires connect the sockets to other components. 9 Connecting Computers In Early Systems Transferring data between two computers consisted of two circuit boards connected by a cable. Figure 7.2 Illustration of an early computer communication system formed using two circuit boards plugged into sockets in two computers. 10 Early Systems The computers use cables to transfer data electronically. – Operating like an I/O device – Writing data to circuit board Figure 7.3 Two pairs of interface boards connecting three computers. Each new computer added to the set requires a new pair of interface boards and an 11 additional cable. Early Systems Advantage of early LANs were speed. Disadvantages of early LANs were inconvenience and cost. Requiring effort to: – Add a new computer – Connect incompatible hardware 12 Connecting A Computer to A LAN A computer needs additional hardware to connect it to a LAN. The speed of the LAN does not depend on the speed of the computer attached to it. – Communication by heterogeneous computers 13 • In many LAN systems, a cable connects each computer to a hub. Computers connected to a LAN. Each computer attaches to the hub with a cable; the computers can 14 then communicate directly. NIC A computer needs network interface hardware and a cable that connects to the LAN. A computer uses the network interface to send and receive data. 15 The Importance Of LAN Technology LANs changed the way people used computer networks. – Sharing resources – Connecting machines within a building 16 Relationship To The Internet Xerox gave universities a prototype of a new LAN technology. – Beginning of Ethernet – Developing the idea of inexpensive and widely available LANs 17 Many Independent Networks By late 1970s, many organizations began installing Local Area Networks because they: – Were inexpensive. – Were easy to install – Could operate them independently of a central administration. 18 The Proliferation of LANs Advantages Disadvantages – An organization can: – Independent groups can: • budget funds • decide who has access • Encourage proliferation of different LAN technologies • devise policies for use 19 Facts About LANs Engineers have devised many LAN technologies LAN performance determines cost. LAN technology may only work with specific computers. 20 LANs Are Incompatible Various LAN technologies are completely incompatible. – Connecting multiple LANs is not possible • Engineered to operate over limited distance • May be electrically incompatible • Encoding information may not make sense to another LAN 21 IEEE802.3 Medium Access Control Random Access – Stations access medium randomly Contention – Stations content for time on medium 22 IEEE 802.3 Frame Format 23 10Mbps Specification (Ethernet) <data rate><Signaling method><Max segment length> 10Base5 10Base2 10Base-T 10Base-FP Medium Coaxial Coaxial UTP 850nm fiber Signaling Baseband Baseband Baseband Manchester Manchester Manchester Manchester On/Off Topology Bus Bus Star Star Nodes 100 30 - 33 24 100Mbps (Fast Ethernet) 100Base-TX 100Base-FX 100Base-T4 2 pair, STP 2 pair, Cat 5UTP 2 optical fiber 4 pair, cat 3,4,5 MLT-3 4B5B,NRZI 8B6T,NRZ MLT-3 25 Gigabit Ethernet Configuration 26 Gigabit Ethernet - Differences Carrier extension At least 4096 bit-times long (512 for 10/100) Frame bursting 27 Gigabit Ethernet - Physical 1000Base-SX – Short wavelength, multimode fiber 1000Base-LX – Long wavelength, Multi or single mode fiber 1000Base-CX – Copper jumpers <25m, shielded twisted pair 1000Base-T – 4 pairs, cat 5 UTP Signaling - 8B/10B 28 Wide Area Technologies Exist WAN technology includes an additional special-purpose computer at each site that: – Connects to the transmission lines – Keeps communication independent of the computer 29 Few WANs, Many WANs WANs cost much more than LANs. – Require more planning – Require more hardware Only a few companies build their own WAN. 30 WANs And LANs Are Incompatible Many Wide Area Networks and Local Area Networks exist. – Cannot connect a WAN to a LAN – Cannot interconnect the wires from two different networks 31 WANs for Voice Requires very small and nonvariable delays for natural conversation--difficult to provide this with packet-switching As a result, the preferred method for voice transmission is circuit-switching Most businesses use public telephone networks, but a few organizations have implemented private voice networks 32 WANs for Data Public packet-switched networks (X.25) Private packet-switched networks Leased lines between sites (non-switched) Public circuit-switched networks Private circuit-switched networks (interconnected digital PBXs) ISDN (integrated X.25 and traditional circuitswitching) 33 WAN Considerations Nature of traffic – stream generally works best with dedicated circuits – bursty better suited to packet-switching Strategic and growth control--limited with public networks Reliability--greater with packet-switching Security--greater with private networks 34 Wireless LANs IEEE 802.11 Basic service set (cell) – Set of stations using same MAC protocol – Competing to access shared medium – May be isolated – May connect to backbone via access point (bridge) Extended service set – Two or more BSS connected by distributed system – Appears as single logic LAN to LLC level 35 Wireless LAN—links clients within the vicinity of each other. A network adapter card that is connected to a transmitter, called an access point, via a cable. The transmitter located on a wall gives the signal an uninterrupted path to a wall-mounted receiver on the far side of the room. Data packets are transmitted over the airwaves to the receiver, which is also connected to network clients by a cable. Wireless Extended LAN—connections to clients a couple of miles away. Similar connectivity is an Extended LAN. Transmitter and receiver are typically located outside the buildings. Forms an electronic data communication bridge called a wireless bridge. Data packets up to 25 miles away from the transmitter use spread spectrum radio technology. 36 Wireless LAN - Physical Infrared – 1Mbps and 2Mbps – Wavelength 850-950nm Direct sequence spread spectrum – 2.4GHz ISM band – Up to 7 channels – Each 1Mbps or 2Mbps Frequency hopping spread spectrum – 2.4GHz ISM band – 1Mbps or 2Mbps Others under development 37 Wireless LANs Mobility Flexibility Hard to wire areas Reduced cost of wireless systems Improved performance of wireless systems 38 LAN Extension Buildings with large open areas – Manufacturing plants – Warehouses Historical buildings Small offices May be mixed with fixed wiring system 39 Single Cell Wireless LAN 40 Multi Cell Wireless LAN 41 Client/Server Architecture Combines advantages of distributed and centralized computing Cost-effective, achieves economies of scale Flexible, scalable approach 42 Intranets Uses Internet-based standards & TCP/IP Content is accessible only to internal users A specialized form of client/server architecture 43 Extranets Similar to intranet, but provides access to controlled number of outside users – Vendors/suppliers – Customers 44 Every computer network has the same basic components: • Cables or wireless connection • Network adapter cards that transmit and receive information • Client software that makes all these components work together Topology: The way in which components are assembled. There are six topologies used in the design of a computer network: • Bus • Star • Ring • Token Passing • Hubs • Hybrid 45 Topologies Tree Bus – Special case of tree • One trunk, no branches Ring Star 46 LAN Topologies 47 A bus topology requires: • Clients are connected to the same cable known as a trunk, segment, or backbone. • All data packets are received by every client regardless of whether the data packet is addressed. • Data packets not addressed to the client are ignored. • Data packets addressed to the client are accepted and processed by the client. • Data packets travel the complete length of the cable, then bounce back. • This is called signal bounce and continues until the signal loses energy and dissipates. • The network operating system has the responsibility to keep the transmission moving along the cable. • A client can malfunction and the network continues to operate, which is called a passive topology. • A passive topology is easy to construct, highly reliable, and susceptible to slow performance during heavy network traffic. • A break in the cable is commonly caused by an improper network connection. • Breaks are hard to track down because every client and device on the network could be suspect. • A network outage does not shut down a client's operation. Clients work as a stand-alone. 48 Frame Transmission - Bus LAN 49 Bus and Tree Multipoint medium Transmission propagates throughout medium Heard by all stations – Need to identify target station • Each station has unique address Full duplex connection between station and tap – Allows for transmission and reception Need to regulate transmission – To avoid collisions – To avoid hogging • Data in small blocks - frames Terminator absorbs frames at end of medium 50 • Clients connect to a central device called a concentrator or hub. • Clients transmit and receive data packets to and from the concentrator. • It is the job of the concentrator to redirect data packets to the appropriate client. • Clients only receive data packets addressed to them. • Star topology reduces the network traffic clients must handle. • The concentrator detects if a client is not connected to the network and returns data packets to the sender. • Failure of one client does not disable the entire network. • Network services become unavailable if the concentrator malfunctions. • Clients use 10BaseT network adapter cards that automatically detect trouble with the concentrator. • The client then stops any transmission of data packets and operates as a stand-alone computer until the concentrator becomes operational. 51 Ring Topology Repeaters joined by point to point links in closed loop – Receive data on one link and retransmit on another – Links unidirectional – Stations attach to repeaters Data in frames – Circulate past all stations – Destination recognizes address and copies frame – Frame circulates back to source where it is removed Media access control determines when station can insert frame 52 Frame Transmission Ring LAN 53 • Each client is connected consecutively to the single cable. • There are no ends to the ring network that must be sealed with a terminator. • Data packets pass clockwise from one client to the next. • If the data packet isn't addressed to the client, the client resends the data packet to the next client. • The client strengthens the signal, allowing the data packet to travel a further distance. • Clients connect to a hub. Within the hub is the ring. • If one client is not working properly, there is a good chance the entire network will fail. • This depends on the network operating system. • IBM token ring automatically ignores inactive clients. 54 • A token ring is a ring-like topology. • Clients are connected together to form a ring. • Each data packet is transmitted to each client on the network. • A special packet, called a token, is used to control transmissions on the network. • The token packet is delivered to a client clockwise along the network. • The client can accept the token and transmit a data packet. • Addresses, data, and other necessary information are added to the token packet. • The modified token packet becomes the new data packet and is sent to the hub for delivery to the destination. • The destination client acknowledges the data packet. • The client that sent the data packet creates a new token packet and passes it to the next client. • The client can ignore the token packet, which is then passed along to the next client on the ring. • This is called token passing. • Token packets can travel more than 10,000 times around the network per second. 55 Star Topology Each station connected directly to central node – Usually via two point to point links Central node can broadcast – Physical star, logical bus – Only one station can transmit at a time Central node can act as frame switch 56 Hubs • A hub is a central processing device on a network. • A hub is used with the star and ring topologies as a concentrator for network traffic. • Hub topology is used to divide large network requirements into smaller, serviceable LANs called segments. • A hub enables a network administrator to monitor and manage network traffic. • A hub is used to link segments together; cabling used by various clients can be mixed and matched. Types of Hubs • Networks use one of two kinds of hubs: • Passive hubs • Active hubs Passive Hubs • A passive hub acts as a connector box known as a wiring panel. • A passive hub connects cables from all clients. • A passive hub only provides connectivity among network clients. It does not interrupt transmissions on the network. Active Hubs • An active hub ID known as a multi-port repeater. • An active hub joins together clients. • An active hub boosts the signal along the network like a repeater. • An active hub can, in some cases, redirect data packets to the appropriate client. 57 Hybrid Topology • The disadvantage of each topology is reduced by combining topologies. • The combined topology is called a hybrid network. • There are two common hybrid networks: star bus and star ring topology. Star Bus Topology • The star bus topology combines the star topology and the bus topology. • Clients of the smaller networks use the star topology to connect to its network concentrator. • Network concentrators are linked together in a bus topology. • The star bus topology controls traffic flow on the network. • Traffic between concentrators is less demanding than traffic among clients. • The bus topology is a more direct and efficient design for connecting concentrators. • The star topology avoids transmission conflicts among clients. • The star bus topology enables network expansion. • If network response time is slow because of an increase in traffic, clients can be transferred to a different segment with its own concentrator. 58 • The star ring topology combines the best of the star and ring topologies. • The star ring topology is referred to as the star wired ring topology. • The star ring topology divides the network into smaller networks each having a concentrator or hub used to connect clients. • Concentrators are joined together using a master concentrator (sometimes called the main hub) in the form of a ring. • The advantage is that network traffic is handled by a topology that best suits the volume of traffic. • The network is scalable. • A hybrid network reduces the chance that a complete network failure will occur. • Only clients directly linked to a concentrator will lose access to network services if the concentrator malfunctions. 59 Question ??? 60