* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Slide 1
Internet protocol suite wikipedia , lookup
Airborne Networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Network tap wikipedia , lookup
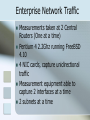
A First Look at Modern Enterprise Traffic Ruoming Pang, Mark Allman, Mike Bennett, Jason Lee, Vern Paxson, Brian Tierney Princeton University, International Computer Science Institute, Lawrence Berkeley National Laboratory (LBNL) IMC2005 http://www.usenix.org/events/imc05/tech/ Report by: Loizos Konomou EL933 Fall 2005 Prof: Yong Liu Enterprise Network Traffic Internet traffic has been studied a lot Not many studies regarding internal enterprise traffic Study of internal network traffic of an enterprise and compare it with the wide area traffic Enterprise Network Traffic Measurements taken at 2 Central Routers (One at a time) Pentium 4 2.2Ghz running FreeBSD 4.10 4 NIC cards, capture unidirectional traffic Measurement equipment able to capture 2 interfaces at a time 2 subnets at a time Enterprise Network Traffic Trace consists Over 100 Hours of packet traces 8000 Internal Hosts 47000 External Hosts Goals: Understand the makeup of internal network traffic (from the network layer to the application layer) Gain sense of the patterns of locality Characterize application traffic in terms of how intranet traffic differs from Internet traffic characteristics Characterize applications heavily used inside the enterprise but rarely outside Gain Understanding of the load being imposed on modern enterprise networks Overview of Traces Network Protocols detected in traces IP is the dominant Layer 3 Protocol Transport Layer Protocols TCP is dominant in Packets UDP is dominant in connections. Application Breakdown Other-udp Other-tcp Misc Net-mgmt Streaming Windows Interactive name Bulk Backup Net-file email WEB Other-udp Other-tcp Misc Net-mgmt Streaming Windows Interactive name Bulk Backup Net-file email WEB Unicast Payload and Connections Most traffic is internal. Most of the external traffic is web Most internal traffic in bytes is net-file and backup, but the number of connections for these categories are very small Name resolution traffic small, but large number of connections Origins and Destinations 71-79% of traffic is within the network 2-3% originates from inside with destination outside 6-11% originates from hosts outside with destination inside 5-10% is multicast sourced within the network, 4-7% is multicast sourced externally Applications Web traffic has more external traffic than internal Email also both internal and external SMTP and Secure IMAP dominate the email protocols used POP3, LDAP Name Services DNS, Netbios, Service Locator, RPC Handful of servers account for most of the DNS traffic. Application Enterprise Specific Traffic Windows Services SMB/CIFS NFS NCP DCE/RPC CIFS Breakdown Windows Services DCE/RPC Functions NFS Functions Backup Services Veritas Dantz Large volume of traffic between small number of hosts. Summary This study provides a broad view of the enterprise traffic Limitations: Data is specific to one Site Each Site is unique General Idea about internal traffic Sets the foundations for more deep studies of internal network traffic

















![[#MODULES-4428] Backup script try to backup sys database when](http://s1.studyres.com/store/data/005823897_1-f86b001551ca5e83ed406bca77a48421-150x150.png)









