* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Lecture2: Physical and data link layer
Asynchronous Transfer Mode wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Serial digital interface wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
IEEE 802.11 wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Code-division multiple access wikipedia , lookup
Internet protocol suite wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Physical Media
physical link:
transmitted data bit
propagates across link
guided media:
signals propagate in
solid media: copper,
fiber
unguided media:
signals propagate
freely, e.g., radio
Twisted Pair (TP)
two insulated copper
wires
Category 3: traditional
phone wires, 10 Mbps
ethernet
Category 5 TP:
100Mbps ethernet
1
Physical Media: coax, fiber
Coaxial cable:
wire (signal carrier)
within a wire (shield)
baseband: single channel
on cable
broadband: multiple
channel on cable
bidirectional
common use in 10Mbs
Fiber optic cable:
glass fiber carrying
light pulses
high-speed operation:
100Mbps Ethernet
high-speed point-to-point
transmission (e.g., 5 Gps)
very low error rate
Ethernet
2
Physical media: radio
signal carried in
electromagnetic
spectrum
no physical “wire”
bidirectional
propagation
environment effects:
reflection
obstruction by objects
interference
Radio link types:
microwave
e.g. up to 45 Mbps channels
LAN (e.g., 802.11b/g)
11/54 Mbps
wide-area (e.g., cellular)
e.g. CDPD, 10’s Kbps
satellite
up to 50Mbps channel (or
multiple smaller channels)
270 Msec end-end delay
geosynchronous versus
LEOS (low earth orbit)
3
The Data Link Layer
Our goals:
Overview:
understand principles
link layer services
behind data link layer
services:
error detection,
correction
sharing a broadcast
channel: multiple access
link layer addressing
error detection, correction
multiple access protocols and
LANs
link layer addressing
specific link layer technologies:
Ethernet
instantiation and
implementation of various
link layer technologies
4
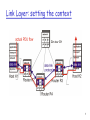
Link Layer: setting the context
5
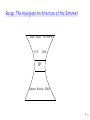
Recap: The Hourglass Architecture of the Internet
Telnet Email
TCP
FTP WWW
UDP
IP
Ethernet Wireless FDDI
6 6
Link Layer: setting the context
two physically connected devices:
host-router, router-router, host-host
unit of data: frame
M
Ht M
Hn Ht M
Hl Hn Ht M
application
transport
network
link
physical
data link
protocol
phys. link
network
link
physical
Hl Hn Ht M
frame
adapter card
7
Link layer: Context
Data-link layer has
responsibility of
transferring datagram
from one node to
another node over a link
Datagram transferred by
different link protocols
over different links, e.g.,
Ethernet on first link,
frame relay on
intermediate links
802.11 on last link
transportation analogy
trip from New Haven to
San Francisco
taxi: home to union
station
train: union station to
JFK
plane: JFK to San
Francisco airport
shuttle: airport to
hotel
8 8
Link Layer Services
Framing, link access:
encapsulate datagram into frame, adding header, trailer
implement channel access if shared medium,
‘physical addresses’ used in frame headers to identify
source, destination
• different from IP address!
Reliable delivery between two physically connected
devices:
seldom used on low bit error link (fiber, some twisted
pair)
wireless links: high error rates
• Q: why both link-level and end-end reliability?
9
Link Layer Services (more)
Flow Control:
pacing between sender and receivers
Error Detection:
errors caused by signal attenuation, noise.
receiver detects presence of errors:
• signals sender for retransmission or drops frame
Error Correction:
receiver identifies and corrects bit error(s)
without resorting to retransmission
10
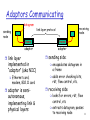
Adaptors Communicating
datagram
sending
node
frame
adapter
link layer
implemented in
“adaptor” (aka NIC)
Ethernet card,
modem, 802.11 card
adapter is semi-
autonomous,
implementing link &
physical layers
receiving
node
link layer protocol
frame
adapter
sending side:
encapsulates datagram in
a frame
adds error checking bits,
rdt, flow control, etc.
receiving side
looks for errors, rdt, flow
control, etc
extracts datagram, passes
to receiving node
11
Link Layer: Implementation
implemented in “adapter”
e.g., PCMCIA card, Ethernet card
typically includes: RAM, DSP chips, host bus
interface, and link interface
M
Ht M
Hn Ht M
Hl Hn Ht M
application
transport
network
link
physical
data link
protocol
phys. link
adapter card
network
link
physical
Hl Hn Ht M
frame
12
Error Detection
EDC= Error Detection and Correction bits (redundancy)
D = Data protected by error checking, may include header fields
• Error detection not 100% reliable! Q: why?
• protocol may miss some errors, but rarely
• larger EDC field yields better detection and correction
13
Parity Checking
Single Bit Parity:
Detect single bit errors
Two Dimensional Bit Parity:
Detect and correct single bit errors
Parity bit=1 iff
Number of 1’s even
0
0
14
Internet checksum
Goal: detect “errors” (e.g., flipped bits) in transmitted
segment (note: used at transport layer only)
Sender:
treat segment contents
as sequence of 16-bit
integers
checksum: addition (1’s
complement sum) of
segment contents
sender puts checksum
value into UDP checksum
field
Receiver:
compute checksum of received
segment
check if computed checksum equals
checksum field value:
NO - error detected
YES - no error detected.
But maybe errors nonetheless?
15
Checksumming: Cyclic Redundancy Check
view data bits, D, as a binary number
choose r+1 bit pattern (generator), G
goal: choose r CRC bits, R, such that
<D,R> exactly divisible by G (modulo 2)
receiver knows G, divides <D,R> by G. If non-zero remainder:
error detected!
can detect all burst errors less than r+1 bits
widely used in practice (ATM, HDCL)
16
CRC Example
Want:
D.2r XOR R = nG
equivalently:
D.2r = nG XOR R
equivalently:
if we divide D.2r by
G, want reminder R
R = remainder[
D.2r
G
]
17
Example G(x)
16 bits CRC:
CRC-16: x16+x15+x2+1,
CRC-CCITT: x16+x12+x5+1
both can catch
• all single or double bit errors
• all odd number of bit errors
• all burst errors of length 16
or less
• >99.99% of the 17 or 18 bits
burst errors
CRC-16 hardware implementation
Using shift and XOR registers
http://en.wikipedia.org/wiki/CRC-32#Implementation
18 18
Multiple Access Links and Protocols
Three types of “links”:
point-to-point (single wire, e.g. PPP, SLIP)
broadcast (shared wire or medium; e.g, Ethernet,
Wavelan, etc.)
switched (e.g., switched Ethernet, ATM etc)
19
Multiple Access protocols
single shared communication channel
two or more simultaneous transmissions by nodes:
interference
only one node can send successfully at a time
multiple access protocol:
distributed algorithm that determines how stations share
channel, i.e., determine when station can transmit
communication about channel sharing must use channel itself!
what to look for in multiple access protocols:
• synchronous or asynchronous
• information needed about other stations
• robustness (e.g., to channel errors)
• performance
20
Multiple Access protocols
claim: humans use multiple access protocols
all the time
class can "guess" multiple access protocols
multiaccess protocol
multiaccess protocol
multiaccess protocol
multiaccess protocol
1:
2:
3:
4:
21
MAC Protocols: a taxonomy
Three broad classes:
Channel Partitioning
divide channel into smaller “pieces” (time slots,
frequency)
allocate piece to node for exclusive use
Random Access
allow
collisions
“recover” from collisions
“Taking turns”
tightly coordinate shared access to avoid collisions
Goal: efficient, fair, simple, decentralized
22
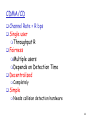
MAC Protocols: Measures
Channel Rate = R bps
Efficient:
Single
user: Throughput R
Fairness
N
users
Min. user throughput R/N
Decentralized
Fault tolerance
Simple
23
Channel Partitioning MAC protocols: TDMA
TDMA: time division multiple access
access to channel in "rounds"
each station gets fixed length slot (length = pkt
trans time) in each round
unused slots go idle
example: 6-station LAN, 1,3,4 have pkt, slots 2,5,6
idle
24
Channel Partitioning MAC protocols: FDMA
FDMA: frequency division multiple access
channel spectrum divided into frequency bands
each station assigned fixed frequency band
unused transmission time in frequency bands go idle
example: 6-station LAN, 1,3,4 have pkt, frequency
frequency bands
bands 2,5,6 idle
25
TDMA & FDMA: Performance
Channel Rate = R bps
Single user
Throughput
R/N
Fairness
Each
user gets the same allocation
Depends on maximum number of users
Decentralized
Requires resource division
Simple
26
Channel Partitioning (CDMA)
CDMA (Code Division Multiple Access)
unique “code” assigned to each user; ie, code set partitioning
used mostly in wireless broadcast channels (cellular,
satellite, etc)
all users share same frequency, but each user has own
“chipping” sequence (ie, code) to encode data
encoded signal = (original data) X (chipping sequence)
decoding: inner-product of encoded signal and chipping
sequence
allows multiple users to “coexist” and transmit
simultaneously with minimal interference (if codes are
almost “orthogonal”)
27
CDMA - Basics
Orthonormal codes:
<ci,cj> =0 i≠j
<ci,ci> =1
Encoding at user i:
Bit 1 send +ci
Bit 0 send -ci
Decoding (at user i):
Receive a vector ri
Compute t=<ri,ci>
If t=1 THEN bit=1
If t=-1 THEN bit=0
Correctness of decoding
Single user
Multiple users
• Assume additive channel.
• R = c1 – c2
• Output <R,c1> = <c1,c1> + <-c2,c1> = 1 + 0 = 1
28
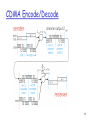
CDMA Encode/Decode
29
CDMA: two-sender interference
30
Random Access protocols
When node has packet to send
transmit at full channel data rate R.
no a priori coordination among nodes
two or more transmitting nodes -> “collision”,
random access MAC protocol specifies:
how to detect collisions
how to recover from collisions (e.g., via delayed
retransmissions)
Examples of random access MAC protocols:
slotted ALOHA
ALOHA
CSMA and CSMA/CD
31
Slotted Aloha [Norm Abramson]
time is divided into equal size slots (= pkt trans. time)
node with new arriving pkt: transmit at beginning of
next slot
if collision: retransmit pkt in future slots with
probability p, until successful.
Success (S), Collision (C), Empty (E) slots
32
Slotted Aloha efficiency
Q: what is max fraction slots successful?
A: Suppose N stations have packets to send
each transmits in slot with probability p
prob. successful transmission S is:
by single node:
S= p (1-p)(N-1)
by any of N nodes
S = Prob (only one transmits)
= N p (1-p)(N-1)
… choosing optimum p =1/N
as N -> infty ...
S≈ 1/e = .37 as N -> infty
At best: channel
use for useful
transmissions 37%
of time!
33
Goodput vs. Offered Load
Slotted Aloha
0.5
1.0
1.5
2.0
G = offered load = np
when p n < 1, as p (or n) increases
probability of empty slots reduces
probability of collision is still low, thus goodput increases
when p n > 1, as p (or n) increases,
probability of empty slots does not reduce much, but
probability of collision increases, thus goodput decreases
goodput is optimal when p n = 1
34
Maximum Efficiency vs. n
0.4
1/e = 0.37
maximum efficiency
0.35
0.3
0.25
0.2
At best: channel
use for useful
transmissions 37%
of time!
0.15
0.1
0.05
0
2
7
12
17
n
35 35
Pure (unslotted) ALOHA
unslotted Aloha: simpler, no synchronization
pkt needs transmission:
send without awaiting for beginning of slot
collision probability increases:
pkt sent at t0 collide with other pkts sent in [t0-1, t0+1]
36
Pure Aloha (cont.)
P(success by given node) = P(node transmits) .
P(no other node transmits in [t0-1,t0] .
P(no other node transmits in [t0,t0+1]
= p . (1-p)N-1 . (1-p)N-1
P(success by any of N nodes) = N p . (1-p)N-1 . (1-p)N-1
… choosing optimum p=1/(2N-1)
as N -> infty ... S≈ 1/(2e) = .18
0.4
0.3
Slotted Aloha
0.2
0.1
protocol constrains
effective channel
throughput!
Pure Aloha
0.5
1.0
1.5
2.0
G = offered load = Np
37
Aloha: Performance
Channel Rate = R bps
Single user
Throughput
R!
Fairness
Multiple
users
Combined throughput only 0.37*R
Decentralized
Slotted needs slot synchronization
Simple
38
CSMA: Carrier Sense Multiple Access
CSMA: listen before transmit:
If channel sensed idle: transmit entire pkt
If channel sensed busy, defer transmission
Persistent CSMA: retry immediately with
probability p when channel becomes idle
Non-persistent CSMA: retry after random interval
human analogy: don’t interrupt others!
39
CSMA collisions
spatial layout of nodes along ethernet
collisions can occur:
propagation delay means
two nodes may not yet
hear each other’s
transmission
collision:
entire packet transmission
time wasted
note:
role of distance and
propagation delay in
determining collision prob.
40
CSMA/CD: Collision Detection
spatial layout of nodes along Ethernet
spatial layout of nodes along Ethernet
C
D
A
t0
t0
time
B
time
A
B
C
B detects
collision,
aborts
D
D detects
collision,
aborts
instead of wasting the whole packet
transmission time, abort after detection.
41 41
CSMA/CD (Collision Detection)
CSMA/CD: carrier sensing, deferral as in CSMA
collisions detected within short time
colliding transmissions aborted, reducing channel
wastage
persistent or non-persistent retransmission
collision detection:
easy in wired LANs: measure signal strengths,
compare transmitted, received signals
difficult in wireless LANs: receiver shut off while
transmitting
human analogy: the polite conversationalist
42
CSMA/CD collision detection
43
Efficiency of CSMA/CD
Given collision detection, instead of wasting the
whole packet transmission time (a slot), we waste
only the time needed to detect collision.
P/C
P: packet size, e.g. 1000 bits
C: link capacity, e.g. 10Mbps
Use a contention slot of 2 T, where T is one-way
propagation delay (why 2 T ?)
When the transmission probability p is approximately
optimal (p = 1/N), we try approximately e times
before each successful transmission
44
44
Efficiency of CSMA/CD
The efficiency (the percentage of useful time) is
approximately
P
C
P e 2T
C
1
1 5PT
1
15 a
, where a
TC
P
C
The value of a plays a fundamental role in the
efficiency of CSMA/CD protocols.
Question: you want to increase the capacity of a link
layer technology (e.g., , 10 Mbps Ethernet to 100
Mbps, but still want to maintain the same efficiency,
what do you do?
45 45
CDMA/CD
Channel Rate = R bps
Single user
Throughput
Fairness
R
Multiple
users
Depends on Detection Time
Decentralized
Completely
Simple
Needs collision detection hardware
46
“Taking Turns” MAC protocols
channel partitioning MAC protocols:
share channel efficiently at high load
inefficient at low load: delay in channel access,
1/N bandwidth allocated even if only 1 active
node!
Random access MAC protocols
efficient at low load: single node can fully
utilize channel
high load: collision overhead
“taking turns” protocols
look for best of both worlds!
47
“Taking Turns” MAC protocols
Polling:
master node
“invites” slave nodes
to transmit in turn
Request to Send,
Clear to Send msgs
concerns:
polling overhead
latency
single point of
failure (master)
Token passing:
control token passed from
one node to next
sequentially.
token message
concerns:
token overhead
latency
single point of failure (token)
48
Reservation-based protocols
Distributed Polling:
time divided into slots
begins with N short reservation slots
reservation slot time equal to channel end-end propagation
delay
station with message to send posts reservation
reservation seen by all stations
after reservation slots, message transmissions ordered by
known priority
49
Summary of MAC protocols
What do you do with a shared media?
Channel Partitioning, by time, frequency or code
• Time Division,Code Division, Frequency Division
Random partitioning (dynamic),
• ALOHA, S-ALOHA, CSMA, CSMA/CD
• carrier sensing: easy in some technologies (wire), hard
in others (wireless)
• CSMA/CD used in Ethernet
Taking Turns
• polling from a central cite, token passing
• Popular in cellular 3G/4G networks where
base station is the master
50
LAN technologies
Data link layer so far:
services, error detection/correction, multiple
access
Next: LAN technologies
addressing
Ethernet
hubs, bridges, switches
802.11
PPP
ATM
51
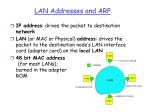
LAN Addresses
32-bit IP address:
network-layer address
used to get datagram to destination network
LAN (or MAC or physical) address:
used to get datagram from one interface to
another physically-connected interface (same
network)
48 bit MAC address (for most LANs)
burned in the adapter ROM
52
LAN Addresses
Each adapter on LAN has unique LAN address
53
LAN Address (more)
MAC address allocation administered by IEEE
manufacturer buys portion of MAC address space
(to assure uniqueness)
Analogy:
(a) MAC address: like ID number תעודת זהות
(b) IP address: like postal address כתובת מגורים
MAC flat address => portability
can move LAN card from one LAN to another
IP hierarchical address NOT portable
depends on network to which one attaches
ARP protocol translates IP address to MAC address
54
Comparison of IP address and MAC Address
IP address is
hierarchical for
routing scalability
IP address needs to be
globally unique (if no
NAT)
MAC address is flat
MAC address does not
need to be globally
unique, but the current
assignment ensures
uniqueness
IP address depends on
IP network to which an
interface is attached
NOT portable
MAC address is
assigned to a device
portable
55
ARP: Address Resolution Protocol
Each IP node (Host, Router)
on LAN has ARP table
ARP Table: IP/MAC address
mappings for some LAN
nodes
< IP address; MAC address; TTL>
[yry3@cicada yry3]$ /sbin/arp
Address
HWtype
zoo-gatew.cs.yale.edu
ether
artemis.zoo.cs.yale.edu ether
lab.zoo.cs.yale.edu
ether
Try
proc/net/arp
HWaddress
AA:00:04:00:20:D4
00:06:5B:3F:6E:21
00:B0:D0:F3:C7:A5
TTL (Time To Live): time
after which address
mapping will be forgotten
(typically 20 min)
Flags Mask
C
C
C
Iface
eth0
eth0
eth0
56
ARP Protocol
ARP is “plug-and-play”:
nodes create their ARP tables without
intervention from net administrator
A broadcast protocol:
A broadcasts query frame, containing queried
IP address
• all machines on LAN receive ARP query
destination D receives ARP frame, replies
• frame sent to A’s MAC address (unicast)
57
Ethernet
“dominant” LAN technology:
cheap $20 for 10/100/1000 Mbs!
first widely used LAN technology
Simpler, cheaper than token LANs and ATM
Kept up with speed race: 1, 10, 100, 1000 Mbps
Metcalfe’s Etheret
sketch
58
Ethernet Frame Structure
Sending adapter encapsulates IP datagram (or other
network layer protocol packet) in Ethernet frame
Preamble:
7 bytes with pattern 10101010 followed by one
byte with pattern 10101011
used to synchronize receiver, sender clock rates
59
Ethernet Frame Structure
(more)
Addresses: 6 bytes, frame is received by all
adapters on a LAN and dropped if address does
not match
Type: indicates the higher layer protocol, mostly
IP but others may be supported such as Novell
IPX and AppleTalk)
CRC: checked at receiver, if error is detected, the
frame is simply dropped
60
Ethernet: uses CSMA/CD
A: sense channel, if idle
then {
transmit and monitor the channel;
If detect another transmission
then {
abort and send jam signal;
update # collisions;
delay as required by exponential backoff algorithm;
goto A
}
else {done with the frame; set collisions to zero}
}
else {wait until ongoing transmission is over and goto A}
61
Ethernet’s CSMA/CD (more)
Jam Signal: make sure all other transmitters are
aware of collision; 48 bits;
Exponential Backoff:
Goal: adapt retransmission attempts to estimated
current load
heavy load: random wait will be longer
first collision: choose K from {0,1}; delay is K x 512
bit transmission times
after n-th collision: choose K from {0,1,…, 2n-1}
after ten or more collisions, choose K from
{0,1,2,3,4,…,1023}
62
Exponential Backoff (simplified)
N users
Interval of size 2n
Prob Node/slot is 1/2n
Prob of success N(1/2n)(1 – 1/2n)N-1
Average slot success N(1 – 1/2n)N-1
Intervals size: 1, 2, 4, 8, 16 …
Fraction (out of N) of success:
2n = N/8 -> 0.03 %
2n = N/4 -> 2%
2n = N/2 -> 15%
2n = N -> 37 %
2n = 2N -> 60%
63
Ethernet Technologies: 10Base2
10: 10Mbps; 2: under 200 meters max cable length
thin coaxial cable in a bus topology
repeaters used to connect up to multiple segments
repeater repeats bits it hears on one interface to
its other interfaces: physical layer device only!
64
10BaseT and 100BaseT
10/100 Mbps rate; latter called “fast ethernet”
T stands for Twisted Pair
Hub to which nodes are connected by twisted pair,
thus “star topology”
CSMA/CD implemented at hub
65
10BaseT and 100BaseT (more)
Max distance from node to Hub is 100 meters
Hub can disconnect “jabbering” adapter
Hub can gather monitoring information, statistics
for display to LAN administrators
66
Gbit Ethernet
use standard Ethernet frame format
allows for point-to-point links and shared
broadcast channels
in shared mode, CSMA/CD is used; short distances
between nodes to be efficient
uses hubs, called here “Buffered Distributors”
Full-Duplex at 1 Gbps for point-to-point links
67
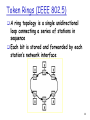
Token Rings (IEEE 802.5)
A ring topology is a single unidirectional
loop connecting a series of stations in
sequence
Each bit is stored and forwarded by each
station’s network interface
68
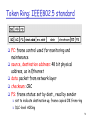
Token Ring: IEEE802.5 standard
4 Mbps (also 16 Mbps)
max token holding time: 10 ms, limiting frame length
SD, ED mark start, end of packet
AC: access control byte:
token bit: value 0 means token can be seized, value 1 means
data follows FC
priority bits: priority of packet
reservation bits: station can write these bits to prevent
stations with lower priority packet from seizing token
after token becomes free
69
Token Ring: IEEE802.5 standard
FC: frame control used for monitoring and
maintenance
source, destination address: 48 bit physical
address, as in Ethernet
data: packet from network layer
checksum: CRC
FS: frame status: set by dest., read by sender
set to indicate destination up, frame copied OK from ring
DLC-level ACKing
70