3GPP TS 23.401
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented. This Specificati ...
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented. This Specificati ...
General Information
... General Information............................................................................................................. 168 Bridge Interface Setup..........................................................................................................170 Port S ............................ ...
... General Information............................................................................................................. 168 Bridge Interface Setup..........................................................................................................170 Port S ............................ ...
5.4.1 Using IPsec to Secure Autoconfiguration
... The authors, Sheila Frankel of the National Institute of Standards and Technology (NIST), Richard Graveman of RFG Security, John Pearce of Booz Allen Hamilton and Mark Rooks of L-1 Identity Solutions (formerly of Booz Allen Hamilton) wish to thank their colleagues who reviewed drafts of this documen ...
... The authors, Sheila Frankel of the National Institute of Standards and Technology (NIST), Richard Graveman of RFG Security, John Pearce of Booz Allen Hamilton and Mark Rooks of L-1 Identity Solutions (formerly of Booz Allen Hamilton) wish to thank their colleagues who reviewed drafts of this documen ...
General Information
... General Information ............................................................................................................... 6 Ethernet.................................................................................................................................. 6 Wireless................. ...
... General Information ............................................................................................................... 6 Ethernet.................................................................................................................................. 6 Wireless................. ...
Brocade 5600 vRouter LAN Interfaces Reference Guide, v3.5R6
... Communications Systems, Inc., in the United States and/or in other countries. Other brands, products, or service names mentioned may be trademarks of others. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, ...
... Communications Systems, Inc., in the United States and/or in other countries. Other brands, products, or service names mentioned may be trademarks of others. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, ...
Animation - Cisco Communities
... OTV encapsulates packets into an IP header and where it sets the Don't Fragment (DF) bit for all OTV control and data packets crossing the transport network. The encapsulation adds 42 bytes to the original IP maximum transition unit (MTU) size. So it is a best practice to configure the join interfac ...
... OTV encapsulates packets into an IP header and where it sets the Don't Fragment (DF) bit for all OTV control and data packets crossing the transport network. The encapsulation adds 42 bytes to the original IP maximum transition unit (MTU) size. So it is a best practice to configure the join interfac ...
Routing Configuration Guide
... States and/or in other countries. Other brands, products, or service names mentioned may be trademarks of others. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, equipment feature, or service offered or to ...
... States and/or in other countries. Other brands, products, or service names mentioned may be trademarks of others. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, equipment feature, or service offered or to ...
Animation - Cisco Communities
... OTV encapsulates packets into an IP header and where it sets the Don't Fragment (DF) bit for all OTV control and data packets crossing the transport network. The encapsulation adds 42 bytes to the original IP maximum transition unit (MTU) size. So it is a best practice to configure the join interfac ...
... OTV encapsulates packets into an IP header and where it sets the Don't Fragment (DF) bit for all OTV control and data packets crossing the transport network. The encapsulation adds 42 bytes to the original IP maximum transition unit (MTU) size. So it is a best practice to configure the join interfac ...
Running IPv6 2006
... Copyright © 2006 by Iljitsch van Beijnum All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the ...
... Copyright © 2006 by Iljitsch van Beijnum All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the ...
PDF - Complete Book (4.43 MB)
... Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of act ...
... Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of act ...
PDF version
... Application Example with Masquerading.............................................................................................20 Application Example with Bandwidth Management.............................................................................20 Application Example with NAT.............. ...
... Application Example with Masquerading.............................................................................................20 Application Example with Bandwidth Management.............................................................................20 Application Example with NAT.............. ...
D) none of the above
... 33. The ________ address, also known as the link address, is the address of a node as defined by its LAN or WAN. ...
... 33. The ________ address, also known as the link address, is the address of a node as defined by its LAN or WAN. ...
PDF - Complete Book (4.57 MB)
... (permit or deny) and a filter element based on criteria such as source address, destination address, protocol, and protocol-specific parameters. Prefix lists are used in route maps and route filtering operations and can be used as an alternative to access lists in many Border Gateway Protocol (BGP) ...
... (permit or deny) and a filter element based on criteria such as source address, destination address, protocol, and protocol-specific parameters. Prefix lists are used in route maps and route filtering operations and can be used as an alternative to access lists in many Border Gateway Protocol (BGP) ...
HERE - Lobometrics High Power Outdoor/Indoor Wireless
... OSB provides powerful command-line configuration interface. You can also manage the router through WinBox - the easy-to-use remote configuration GUI for Windows -, which provides all the benefits of the command-line interface, without the actual "command-line", which may scare novice users. Web-base ...
... OSB provides powerful command-line configuration interface. You can also manage the router through WinBox - the easy-to-use remote configuration GUI for Windows -, which provides all the benefits of the command-line interface, without the actual "command-line", which may scare novice users. Web-base ...
General Information - HauteSpot Networks
... 802.1q Trunk extension over Wireless P2P Link ...................................................................................................................76 Access and bandwidth limitation ........................................................................................................ ...
... 802.1q Trunk extension over Wireless P2P Link ...................................................................................................................76 Access and bandwidth limitation ........................................................................................................ ...
The Second Internet
... http://creativecommons.org/licenses/by-nd/3.0/us/. In short, the terms of this license are as follows: You can share (copy, distribute and/or transmit) machine readable copies of this work. At most there should be minimal copying costs associated with any such sharing. We will be providing it for do ...
... http://creativecommons.org/licenses/by-nd/3.0/us/. In short, the terms of this license are as follows: You can share (copy, distribute and/or transmit) machine readable copies of this work. At most there should be minimal copying costs associated with any such sharing. We will be providing it for do ...
ipv6 technology and dns setup
... report first introduces some Internet standards-based IPv6 concepts: the features of IPv6, IPv6 addressing, IPv6 address autoconfiguration. Then it describes proposed transition strategies from IPv4 to IPv6: Dual IP Layer Operation for communication between IPv6 and IPv4 nodes, some proposed tunneli ...
... report first introduces some Internet standards-based IPv6 concepts: the features of IPv6, IPv6 addressing, IPv6 address autoconfiguration. Then it describes proposed transition strategies from IPv4 to IPv6: Dual IP Layer Operation for communication between IPv6 and IPv4 nodes, some proposed tunneli ...
Cisco ASR 5x00 Packet Data Serving Node Administration Guide Version 15.0
... Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner ...
... Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner ...
Lawrence E. Hughes - The Second Internet
... http://creativecommons.org/licenses/by-nd/3.0/us/ In short, the terms of this license are as follows: You can share (copy, distribute and/or transmit) machine readable copies of this work. At most there should be minimal copying costs associated with any such sharing. We will be providing it for dow ...
... http://creativecommons.org/licenses/by-nd/3.0/us/ In short, the terms of this license are as follows: You can share (copy, distribute and/or transmit) machine readable copies of this work. At most there should be minimal copying costs associated with any such sharing. We will be providing it for dow ...
TCP/IP Illustrated - UTN
... This provides the required background for later chapters for readers who aren't familiar with TCP/IP or networking in general. This book also uses a functional approach instead of following a strict bottom-to-top order. For example, Chapter 3 describes the IP layer and the IP header. But there are n ...
... This provides the required background for later chapters for readers who aren't familiar with TCP/IP or networking in general. This book also uses a functional approach instead of following a strict bottom-to-top order. For example, Chapter 3 describes the IP layer and the IP header. But there are n ...
29061-bc0
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specificati ...
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specificati ...
29061-ae0
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specificati ...
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specificati ...
22COMM-UM004 - Rockwell Automation
... The EtherNet/IP adapter features the following: • The adapter is mounted in the PowerFlex 40 drive. It receives the required power from the drive. • A switch lets you select between Single or Multi-Drive mode of operation. In Single mode (default), the adapter represents a single drive on one node. ...
... The EtherNet/IP adapter features the following: • The adapter is mounted in the PowerFlex 40 drive. It receives the required power from the drive. • A switch lets you select between Single or Multi-Drive mode of operation. In Single mode (default), the adapter represents a single drive on one node. ...
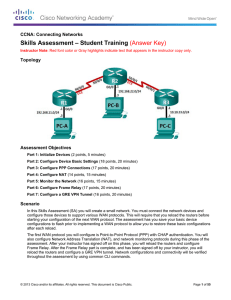
Skills Assessment – Student Training (Answer Key)
... In this Skills Assessment (SA) you will create a small network. You must connect the network devices and configure those devices to support various WAN protocols. This will require that you reload the routers before starting your configuration of the next WAN protocol. The assessment has you save yo ...
... In this Skills Assessment (SA) you will create a small network. You must connect the network devices and configure those devices to support various WAN protocols. This will require that you reload the routers before starting your configuration of the next WAN protocol. The assessment has you save yo ...
Advanced CCIE Routing & Switching
... tunnel source FastEthernet0/0 tunnel mode gre multipoint end Actually we can see two problems in the above configuration, the first problem is that the configuration does not provide support for Multicast traffic. The second problem is that the wrong IPv6 address is mapped to the NBMA-IP. In IPv6, t ...
... tunnel source FastEthernet0/0 tunnel mode gre multipoint end Actually we can see two problems in the above configuration, the first problem is that the configuration does not provide support for Multicast traffic. The second problem is that the wrong IPv6 address is mapped to the NBMA-IP. In IPv6, t ...
I²C
I²C (Inter-Integrated Circuit), pronounced I-squared-C, is a multi-master, multi-slave, single-ended, serial computer bus invented by Philips Semiconductor (now NXP Semiconductors). It is typically used for attaching lower-speed peripheral ICs to processors and microcontrollers. Alternatively I²C is spelled I2C (pronounced I-two-C) or IIC (pronounced I-I-C). Since October 10, 2006, no licensing fees are required to implement the I²C protocol. However, fees are still required to obtain I²C slave addresses allocated by NXP.Several competitors, such as Siemens AG (later Infineon Technologies AG, now Intel mobile communications), NEC, Texas Instruments, STMicroelectronics (formerly SGS-Thomson), Motorola (later Freescale), and Intersil, have introduced compatible I²C products to the market since the mid-1990s.SMBus, defined by Intel in 1995, is a subset of I²C that defines the protocols more strictly. One purpose of SMBus is to promote robustness and interoperability. Accordingly, modern I²C systems incorporate policies and rules from SMBus, sometimes supporting both I²C and SMBus, requiring only minimal reconfiguration.