* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download ISA_673-android_presentation_(3) - eee
Survey
Document related concepts
Transcript
ISA 673
Operating Systems Security
Exploring the Android Platform
Battery Utilization Monitoring
• Project Goals
– Track usage by resource and process
– Modify resource scheduling to ensure fairness
• Approach
– Low-level (kernel level)
– High enough to associate processes to resource
requests
5/23/2017
ISA673 - Operating Systems Security
2
The Problem
• Resource monitoring mostly done in usermode
– Relies on system services and system calls for data
– Kernel-mode malware can easily subvert it
• Malware power usage largely unstudied
– Studies limited
– Full system instrumentation not available
5/23/2017
ISA673 - Operating Systems Security
3
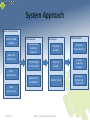
System Approach
Kernel Instrumentation
Services Table
Hooking
Wake Lock
Monitoring
Data Collection
Data Analysis
Modify Scheduler
Kernel-mode
Collection
Module
Statistical
Analysis
Real-time
Power Monitor
Procfs Bridge
to User-mode
Charts &
Graphs
Process
Queuing
Changes
Identify Trends
Security vs.
Battery Life
Trade-offs
Driver
Modification
Upload to PC
for Analysis
Other
(Undiscovered)
5/23/2017
ISA673 - Operating Systems Security
4
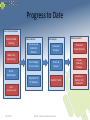
Progress to Date
Kernel Instrumentation
Services Table
Hooking
Wake Lock
Monitoring
Data Collection
Data Analysis
Modify Scheduler
Kernel-mode
Collection
Module
Statistical
Analysis
Real-time
Power Monitor
Procfs Bridge
to User-mode
Charts &
Graphs
Process
Queuing
Changes
Identify Trends
Security vs.
Battery Life
Trade-offs
Driver
Modification
Upload to PC
for Analysis
Other
(Undiscovered)
5/23/2017
ISA673 - Operating Systems Security
5
Design Philosophy
• System changes are dangerous without data
• Iterative approach allows for intelligent
refinement
• Modular design for flexibility
• Analysis built into the design
– Demonstrates success/failure of system changes
5/23/2017
ISA673 - Operating Systems Security
6
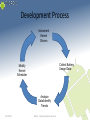
Development Process
Instrument
Kernel
Drivers
Collect Battery
Usage Data
Modify
Kernel
Scheduler
Analyze
Data/Identify
Trends
5/23/2017
ISA673 - Operating Systems Security
7
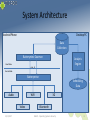
System Architecture
Android Phone
Desktop PC
Data
Collection
Batterymine Daemon
Analysis
Engine
User Mode
proc_fs
Kernel Mode
Batterymine
Scheduling
Data
Audio
WiFi
Video
5/23/2017
3G
Bluetooth
ISA673 - Operating Systems Security
8
Kernel Module
•
•
•
•
Records per-process usage of resources
Records per-interval usage of battery
Writes tab-separated data to proc_fs
Interface allows easy instrumentation of
kernel
• Supports multiple instrumentation strategies
5/23/2017
ISA673 - Operating Systems Security
9
Instrumentation Strategy
• Build Batterymine into Android kernel
• Modify code for most-used drivers
• Attribute device usage to process where
possible
• Attribute to “Idle” otherwise.
• Pros: Simple, allows for iterative development
• Cons:
– Requires intimate knowledge of driver code
– Hardware dependent
– Process ID not always available
5/23/2017
ISA673 - Operating Systems Security
10
Module Interface
enum power_consumer_type
{
idle = 0,
wifi,
bluetooth,
audio,
threeG,
video
};
void bm_logDeviceUsage(enum power_consumer_type devType,
struct timespec usageTime);
void bm_logProcDeviceUsage(enum power_consumer_type devType,
pid_t processID,
struct timespec usageTime);
#define BM_GET_START_TIME struct timespec ts = current_kernel_time()
#define BM_GET_DIFF_TIME timespec_sub(current_kernel_time(), ts)
5/23/2017
ISA673 - Operating Systems Security
11
Sample Instrumentation
void myAudioDeviceFunc(char *szPointer)
{
BM_GET_START_TIME();
if(NULL != szPointer)
{
bm_logDeviceUsage(audio, BM_GET_DIFF_TIME);
return;
}
// ...driver code...
bm_logDeviceUsage(audio, BM_GET_DIFF_TIME);
}
5/23/2017
ISA673 - Operating Systems Security
12
Statistical Analysis
• How much battery is used for each device?
• Collect device usage per process at a time
interval
• Execute Multiple Regression
5/23/2017
ISA673 - Operating Systems Security
13
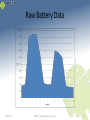
Raw Battery Data
5/23/2017
ISA673 - Operating Systems Security
14
Resource Usage Stats
5/23/2017
ISA673 - Operating Systems Security
15
Power Consumption Per Resource
5/23/2017
ISA673 - Operating Systems Security
16
Multiple Regression
• Y = a + b1*X1 + b2*X2 + ... + bn * Xn
where
Y : Battery Usage
N: Number of devices
bi: Coefficient of each device
Xi: usage(process time) of device Xi
5/23/2017
ISA673 - Operating Systems Security
17
Output
Coefficients
Intercept
2151.587317
Audio
256.8419143
Wifi
1017.472706
Audio Line Fit Plot
charge
6000
4000
charge
Predicted charge
2000
0
0
1
2
3
Audio
5/23/2017
ISA673 - Operating Systems Security
18
Wifi Output
Wifi Line Fit Plot
charge
6000
4000
charge
Predicted charge
2000
0
0
0.5
1
Wifi
1.5
Project Successes
• Wins
– Complete data collection and analysis engine
• Supports any instrumentation strategy
• Capable of comparing/contrasting instrumentation
techniques
– Partial instrumentation of kernel drivers
• Real-time data collection
• Minimal driver code change
– Gained knowledge of kernel architecture
5/23/2017
ISA673 - Operating Systems Security
20
Project Shortcomings
• Picked infeasible approach to kernel
instrumentation
– Requires too many driver changes
– Requires intimate knowledge of each driver
– Hardware dependent
• Cannot validate analysis
– Did not collect enough data
• Have not approached scheduler changes
– Last step in process
5/23/2017
ISA673 - Operating Systems Security
21
How to Find More Info
• Project hosted on Google Code
– http://code.google.com/p/batterymine
• Code
– Subversion support
– Full source of modified kernel
• Wiki
– Build and Install instructions
– Culmination of research
• Downloads
– Latest build of binaries
– Slides
5/23/2017
ISA673 - Operating Systems Security
22