
Electrical Engineering and Computer Science Department Technical
... hybrid runtimes (HRTs), runtimes that run as kernels, and that enjoy full hardware access and control over abstractions to the machine. The primary claim of this dissertation is that the hybrid runtime model can provide significant benefits to parallel runtimes and the applications that run on top ...
... hybrid runtimes (HRTs), runtimes that run as kernels, and that enjoy full hardware access and control over abstractions to the machine. The primary claim of this dissertation is that the hybrid runtime model can provide significant benefits to parallel runtimes and the applications that run on top ...
The Architecture of a Worldwide Distributed System
... Although my advisor, Andy Tanenbaum, thinks otherwise, I view a Ph.D. as a period of learning as much as you can in as many different subjects that are interesting. In this respect I took full advantage of my Ph.D.: I did work ranging from programming my own EEPROMs, to secure network objects, digit ...
... Although my advisor, Andy Tanenbaum, thinks otherwise, I view a Ph.D. as a period of learning as much as you can in as many different subjects that are interesting. In this respect I took full advantage of my Ph.D.: I did work ranging from programming my own EEPROMs, to secure network objects, digit ...
A Virtual Machine Introspection Based Architecture for Intrusion
... /dev/kmem, [42, 40] and direct writes from I/O devices. Disabling these interfaces results in a loss of functionality, such as the inability to run programs, such as X11, that rely on them. We must also contend with the issue of exploitable bugs in the OS, a serious problem in our world of complex o ...
... /dev/kmem, [42, 40] and direct writes from I/O devices. Disabling these interfaces results in a loss of functionality, such as the inability to run programs, such as X11, that rely on them. We must also contend with the issue of exploitable bugs in the OS, a serious problem in our world of complex o ...
Dancing with Giants: Wimpy Kernels for On-demand Isolated I/O
... sensitive applications (i.e., wimps) to dynamically connect to diverse peripheral devices of unmodified commodity OSes. Central to on-demand isolation of I/O channels is the notion of the wimpy kernel, which constructs these channels without affecting the underlying TCB; i.e., without modifying its ...
... sensitive applications (i.e., wimps) to dynamically connect to diverse peripheral devices of unmodified commodity OSes. Central to on-demand isolation of I/O channels is the notion of the wimpy kernel, which constructs these channels without affecting the underlying TCB; i.e., without modifying its ...
Design Tradeoffs For Software
... The virtual to physical address translation operation sits on the critical path between the CPU and the cache. If every request for a memory location out from the processor required one or more accesses to main memory (to read page table entries), then the processor would be very slow. ...
... The virtual to physical address translation operation sits on the critical path between the CPU and the cache. If every request for a memory location out from the processor required one or more accesses to main memory (to read page table entries), then the processor would be very slow. ...
Application of Software Components in Operating System Design
... Abstract: This thesis describes the primary goal of the HelenOS microkernel multiserver operating system. The primary goal of the HelenOS project is to create a comprehensive research and development platform in the domain of general-purpose operating systems that would support state-of-the-art appr ...
... Abstract: This thesis describes the primary goal of the HelenOS microkernel multiserver operating system. The primary goal of the HelenOS project is to create a comprehensive research and development platform in the domain of general-purpose operating systems that would support state-of-the-art appr ...
Denali: Lightweight Virtual Machines
... technical challenges. One challenge is scale: for costefficiency and convenience, infrastructure providers will need to multiplex many services on each server machine, as it would be prohibitively expensive to dedicate a separate machine to each service. A second challenge is security: infrastructur ...
... technical challenges. One challenge is scale: for costefficiency and convenience, infrastructure providers will need to multiplex many services on each server machine, as it would be prohibitively expensive to dedicate a separate machine to each service. A second challenge is security: infrastructur ...
Proceedings of the 5th Symposium on Operating Systems Design and Implementation USENIX Association
... technical challenges. One challenge is scale: for costefficiency and convenience, infrastructure providers will need to multiplex many services on each server machine, as it would be prohibitively expensive to dedicate a separate machine to each service. A second challenge is security: infrastructur ...
... technical challenges. One challenge is scale: for costefficiency and convenience, infrastructure providers will need to multiplex many services on each server machine, as it would be prohibitively expensive to dedicate a separate machine to each service. A second challenge is security: infrastructur ...
Singularity: Rethinking the Software Stack
... architecture based on software isolation of processes. Our programming language, Sing# [8], is an extension of C# that provides verifiable, first-class support for OS communication primitives as well as strong support for systems programming and code factoring. The sound verification tools detect pr ...
... architecture based on software isolation of processes. Our programming language, Sing# [8], is an extension of C# that provides verifiable, first-class support for OS communication primitives as well as strong support for systems programming and code factoring. The sound verification tools detect pr ...
Singularity: Rethinking the Software Stack
... architecture based on software isolation of processes. Our programming language, Sing# [8], is an extension of C# that provides verifiable, first-class support for OS communication primitives as well as strong support for systems programming and code factoring. The sound verification tools detect pr ...
... architecture based on software isolation of processes. Our programming language, Sing# [8], is an extension of C# that provides verifiable, first-class support for OS communication primitives as well as strong support for systems programming and code factoring. The sound verification tools detect pr ...
Proceedings of the General Track: 2003 USENIX Annual Technical Conference
... the platform upon which they are built [Goldberg73]. Type I VMMs such as IBM’s VM/370, Disco, and VMware’s ESX Server are implemented directly on the physical hardware. Type II VMMs are built completely on top of a host operating system. SimOS, User-Mode Linux, and UMLinux are all implemented comple ...
... the platform upon which they are built [Goldberg73]. Type I VMMs such as IBM’s VM/370, Disco, and VMware’s ESX Server are implemented directly on the physical hardware. Type II VMMs are built completely on top of a host operating system. SimOS, User-Mode Linux, and UMLinux are all implemented comple ...
Operating System Support for Virtual Machines
... the platform upon which they are built [Goldberg73]. Type I VMMs such as IBM’s VM/370, Disco, and VMware’s ESX Server are implemented directly on the physical hardware. Type II VMMs are built completely on top of a host operating system. SimOS, User-Mode Linux, and UMLinux are all implemented comple ...
... the platform upon which they are built [Goldberg73]. Type I VMMs such as IBM’s VM/370, Disco, and VMware’s ESX Server are implemented directly on the physical hardware. Type II VMMs are built completely on top of a host operating system. SimOS, User-Mode Linux, and UMLinux are all implemented comple ...
Operating System Support for Virtual Machines
... the platform upon which they are built [Goldberg73]. Type I VMMs such as IBM’s VM/370, Disco, and VMware’s ESX Server are implemented directly on the physical hardware. Type II VMMs are built completely on top of a host operating system. SimOS, User-Mode Linux, and UMLinux are all implemented comple ...
... the platform upon which they are built [Goldberg73]. Type I VMMs such as IBM’s VM/370, Disco, and VMware’s ESX Server are implemented directly on the physical hardware. Type II VMMs are built completely on top of a host operating system. SimOS, User-Mode Linux, and UMLinux are all implemented comple ...
SafeDrive: Safe and Recoverable Extensions Using Language-Based Techniques
... allocated by the driver and unregistering any name space entries registered by the driver (e.g., new device entries or file system entries), both of which we will refer to as updates. In order to undo updates during fault recovery, we track them using wrappers for the relevant API calls. Because Saf ...
... allocated by the driver and unregistering any name space entries registered by the driver (e.g., new device entries or file system entries), both of which we will refer to as updates. In order to undo updates during fault recovery, we track them using wrappers for the relevant API calls. Because Saf ...
The Application Kernel Approach - a Novel Approach for Adding
... Like systems which use coarse-grained locking, master-slave systems (refer to Chapter 9 in [38]) allow only one processor in the kernel at a time. The difference is that in master-slave systems, one processor is dedicated to handling kernel operations (the “master” processor) whereas the other proce ...
... Like systems which use coarse-grained locking, master-slave systems (refer to Chapter 9 in [38]) allow only one processor in the kernel at a time. The difference is that in master-slave systems, one processor is dedicated to handling kernel operations (the “master” processor) whereas the other proce ...
VirtuOS: an operating system with kernel virtualization
... Architectural approaches for increasing the reliability of kernel software and reducing the impact of faults often rely on decomposition. Microkernel-based system design moves device drivers and other system critical code from the kernel into separate user space processes. Microkernels have been suc ...
... Architectural approaches for increasing the reliability of kernel software and reducing the impact of faults often rely on decomposition. Microkernel-based system design moves device drivers and other system critical code from the kernel into separate user space processes. Microkernels have been suc ...
Process - Tufts Computer Science
... The less the OS constrains what goes on in a process or device driver, the more flexible it can be in supporting new programming languages, I/O devices, etc. However: we’ll see in a minute that the OS has a few features to help common languages with procedure calls and shareable libraries run effici ...
... The less the OS constrains what goes on in a process or device driver, the more flexible it can be in supporting new programming languages, I/O devices, etc. However: we’ll see in a minute that the OS has a few features to help common languages with procedure calls and shareable libraries run effici ...
Helios: Heterogeneous Multiprocessing with Satellite Kernels
... that provide slower CPUs and far less RAM than general purpose CPUs should not be prevented from running Helios. • Avoid unnecessary local IPC. Local message-passing is slower than a system call. Therefore, resources private to a process (e.g., memory) should be managed by a satellite kernel and acc ...
... that provide slower CPUs and far less RAM than general purpose CPUs should not be prevented from running Helios. • Avoid unnecessary local IPC. Local message-passing is slower than a system call. Therefore, resources private to a process (e.g., memory) should be managed by a satellite kernel and acc ...
an introduction to solaris
... Sun’s UNIX operating environment began life as a port of BSD UNIX to the Sun-1 workstation. The early versions of Sun’s UNIX were known as SunOS, which is the name used for the core operating system component of Solaris. SunOS 1.0 was based on a port of BSD 4.1 from Berkeley labs in 1982. At that ti ...
... Sun’s UNIX operating environment began life as a port of BSD UNIX to the Sun-1 workstation. The early versions of Sun’s UNIX were known as SunOS, which is the name used for the core operating system component of Solaris. SunOS 1.0 was based on a port of BSD 4.1 from Berkeley labs in 1982. At that ti ...
OS Portal: an economic approach for making an embedded kernel
... The goal of the server-side module linking is to make a resource-limited embedded kernel extensible, while keeping the imposed overheads minimal. As mentioned above, the OS Portal process on the server machine receives requests from client kernels and performs tasks according to those requests. Ther ...
... The goal of the server-side module linking is to make a resource-limited embedded kernel extensible, while keeping the imposed overheads minimal. As mentioned above, the OS Portal process on the server machine receives requests from client kernels and performs tasks according to those requests. Ther ...
Microkernels Meet Recursive Virtual Machines
... problems by defining the architecture to avoid them. Although some existing hypervisors export a virtual architecture that differs slightly from the architecture on which they are based, they generally try to minimize such divergence, changing the architecture only enough to address “showstopping” p ...
... problems by defining the architecture to avoid them. Although some existing hypervisors export a virtual architecture that differs slightly from the architecture on which they are based, they generally try to minimize such divergence, changing the architecture only enough to address “showstopping” p ...
Adopting and Commenting the Old Kernel Source Code for Education
... first read into the cache area from the block device. When a task needs to output the data to a block device, the data is put into the cache area first and then is written into the block device by the hardware driver in due time. The last part of the physical memory is the main area used dynamically ...
... first read into the cache area from the block device. When a task needs to output the data to a block device, the data is put into the cache area first and then is written into the block device by the hardware driver in due time. The last part of the physical memory is the main area used dynamically ...
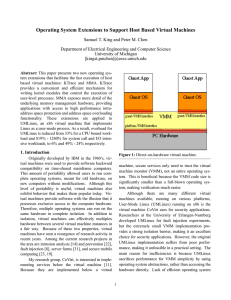
Operating System Extensions to Support Host Based Virtual Machines
... VMware is the most prevalent x86 virtual machine today. By providing a complete implementation of the x86 ISA at the guest-VMM interface, VMware is a useful tool with many different applications. Although this complete guest-VMM interface is extremely general, it leads to a more complicated VMM. Bec ...
... VMware is the most prevalent x86 virtual machine today. By providing a complete implementation of the x86 ISA at the guest-VMM interface, VMware is a useful tool with many different applications. Although this complete guest-VMM interface is extremely general, it leads to a more complicated VMM. Bec ...
[slides] Case study: Linux
... a system call to signal, modify, or wait for another process Credentials. Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personality. Not traditionally found on UNIX systems, but under Linux each pro ...
... a system call to signal, modify, or wait for another process Credentials. Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personality. Not traditionally found on UNIX systems, but under Linux each pro ...
Kernel (operating system)
In computing, the kernel is a computer program that manages I/O requests from software, and translates them into data processing instructions for the central processing unit and other electronic components of a computer. The kernel is a fundamental part of a modern computer's operating system.The critical code of the kernel is usually loaded into a protected area of memory, which prevents it from being overwritten by other, less frequently used parts of the operating system or by applications. The kernel performs its tasks, such as executing processes and handling interrupts, in kernel space, whereas everything a user normally does, such as writing text in a text editor or running programs in a GUI (graphical user interface), is done in user space. This separation prevents user data and kernel data from interfering with each other and thereby diminishing performance or causing the system to become unstable (and possibly crashing). When a process makes requests of the kernel, the request is called a system call. Various kernel designs differ in how they manage system calls and resources. For example, a monolithic kernel executes all the operating system instructions in the same address space in order to improve the performance of the system. A microkernel runs most of the operating system's background processes in user space, to make the operating system more modular and, therefore, easier to maintain.The kernel's interface is a low-level abstraction layer.
















![[slides] Case study: Linux](http://s1.studyres.com/store/data/008426094_1-33a53a235a0b160ad065c81f93e7bd9c-300x300.png)