* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download The Evolution of Operating Systems
Library (computing) wikipedia , lookup
Plan 9 from Bell Labs wikipedia , lookup
Security-focused operating system wikipedia , lookup
Spring (operating system) wikipedia , lookup
Distributed operating system wikipedia , lookup
Copland (operating system) wikipedia , lookup
Burroughs MCP wikipedia , lookup
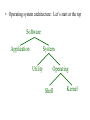
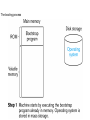
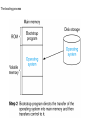
Operating Systems and Networks Fall 2013 What is an Operating System • An operating system is a software program that coordinates activities between the hardware and the user. • Unrelated activities should not interfere with each other and the user should be unaware of the details involved. The Evolution of Operating Systems • Simple means of program execution – Batch processing – Job queue • FIFO fashion (First-In First-Out) Batch processing • More complex -- Interactive Processing – Real-time processing • Now the machine runs programs in the context of a user environment, • the program can be responsive and can be directed during its execution. – Crucial to this is time-sharing • Dividing time into fixed-length intervals, or time slices. A job is only allowed to execute for a single time slice, then another is allowed to execute, then another, … • This allows the computer to do many things “at the same time” Interactive processing – Time sharing is usually manifest in what we call multitasking • Doing many things at once. • Multitasking can increase efficiency and productivity • Examples: – Cooking a meal on a one-burner stove (“serial”) versus cooking a meal on a 4-burner stove (“parallel”). When you cook on a multiburner stove you are multitasking and assigning time slices to different items being cooked. Stir one pot for a few seconds, then turn your attention to another pot and add some ingredients; then turn to check on a third pot, etc. Each pot is a different process. – Working on a computer:You finish a term paper and select “print”. While you are waiting for the paper to print you switch over to Netscape and surf the web for a while. This would not be possible without time sharing and multitasking. You would have to wait for the printer to finish before doing anything else! Operating System Architecture • Early on -- operating systems were used to coordinate and schedule batch processes. • With multiple users or the need to run different programs at the same time and handle many different user interfaces, operating systems became more complicated and more powerful. Now the operating system provides an environment in which applications run. • Operating system architecture: Let’s start at the top Software Application System Utility Operating Shell Kernel • Shell - the interface between the OS and the user – Modern shells implement a graphical user interface or GUI (“Gooey”) – Older shells used a command line interface • DOS, UNIX – The shell is merely an interface. Good ones are easy to use and increase productivity. Poor ones are hard to figure out, and require wasting time to figure out how to do something. • Apple Macintosh, Microsoft Windows, Gnome and KDE on Linux, Solaris, … • But this is what the user uses! So it is what most people associate with computers. The real heart of the computer, however, is the operating system and the kernel is the heart of the OS. The shell as an interface between users and the operating system The GUI had its roots in the 1950s but was not developed until the 1970s when a group at the Xerox Palo Alto Research Center (PARC) developed the Alto, a GUI-based computer. The Alto was the size of a large desk, and Xerox believed it unmarketable. [Steve] Jobs took a tour of PARC in 1979, and saw the future of personal computing in the Alto. … When Jobs accused Bill Gates of Microsoft of stealing the GUI from Apple and using it in Windows 1.0, Gates fired back: No, Steve, I think its more like we both have a rich neighbor named Xerox, and you broke in to steal the TV set, and you found out I'd been there first, and you said. "Hey that's no fair! I wanted to steal the TV set! -- www.apple-history.com • Kernel -- software which performs the most basic functions required to make a modern computer run – File manager • • • • Coordinates the use of the machine’s mass storage facilities. Files, directories and folders (hierarchical organization) path file descriptor (information needed to find and access a file) – Device drivers • Software units that communicate with the controllers of the devices. – Memory manager • Coordinates the machine’s use of main memory (including virtual memory) – Scheduler – Dispatcher • Booting a computer: – Boot strapping or booting • The first thing performed by the computer when it is turned on (or re-booted) • The computer is designed so that it’s program counter will always point to one particular address in ROM. This is where a permanent program resides which gets the computer going. It directs the computer to load a program, or programs, from mass storage (hard disk, floppy*, CD, …) into main memory and then execute them. These programs are the operating system binaries. The booting process The booting process Coordinating the Machine’s Activities • “One of the most fundamental concepts of modern operating systems is the distinction between a program and the activity of executing a program.” – A program -- a static set of directions – A process -- the dynamic activity of the machine whose properties change as time progresses. At any particular time the current status of the activity is called the process state. – The process state exactly and completely defines everything needed to run the program. (i.e. the address in the program counter, the contents of the registers, and the contents of main memory cells which are being used by the program. It is a snapshot of the machine at a particular time. • A program can have many processes associated with it: – A word processing program can have many different files open at the same time. It can also be printing a document and spell-checking another. These are all different processes with their own data. • All these processes (from one program or from many) compete for processor time (compete for time slices) – We must have an administrator to coordinate all this. • Process Administration – “Tasks associated with process coordination are handled by the scheduler and dispatcher within the operating system’s kernel.” – Scheduler -- The scheduler maintains a process table to organize the current processes. • The process table contains information about each process: – memory area assigned to the process (from the memory manager) – priority of the process (ready, waiting, …) – Dispatcher -- the part of the kernel that ensures that each scheduled process is actually executed. • Controls the time-sharing behavior • Handles interrupts. Time-sharing between process A and process B “Paramount to the success of a time-sharing system is the ability to stop, and later restart, a process.” You must be able to pick up exactly where you left off. Handling Competition Among Processes • The OS (here meaning kernel) must be able to allocate resources of the machine so that all the processes are executed smoothly, with no errors, and without time wasting conflicts. • A potential problem: – Two processes are competing for resources. One process holds access to the printer and is waiting for access to the hard drive. Another process holds access to the hard drive and is waiting for access to the printer. Deadlock Networks Two broad categories: • local area networks (LAN’s) • wide area networks (WAN’s) – These describe the physical arrangement of the network • The operation of the network can be either open or closed – Open -- operation is governed by an open standard of communication. Everyone can see how it works. – Closed -- proprietary; The details are hidden and are the exclusive property of a company. • Classification – – – – ring bus star irregular • The Internet can be understood in terms of collections of networks called domains. (See figure 3.11) – Each domain could be a University or a company. • Each domain is an autonomous system that is configured and administered by a local authority (maybe the “Network System Administrator”) • We must have a common addressing scheme within all networks so that we can locate a particular machine: – Each machine is assigned a 32 bit address called an IP address. Each computer is given a numerical address. – The IP address is broken down into a host address and a network identifier. 140.211.117.7 -- gilligan.wou.edu 140.211.117.7 Network identifier Host address Addresses go from: 0. 0. 0. 0 to 255.255.255.255 • Thinking about this in a simple way, how many machines can we put on the internet? – Total machines = 232 4.29 billion – Total domains = 224 16.8 million – Machines/domain = 28 256 • We are accustomed to the alpha-numeric form of the machine address: gilligan.wou.edu • This is not a web address. Rather it contains both the network identifier and the host address. This is the machine whose name is gilligan within the domain wou.edu. • Domain name: wou.edu • The domain name is also classified by type: – .com, .edu, .org, .mil, .gov, .uk, .de, . . . • E-mail: [email protected] locally assigned address for user Domain name • Domain name server – A directory system that performs conversions from mnemonic addresses to numeric addresses. – Responds to requests regarding addresses – All the Internet’s name servers make up an Internetwide directory system • New domain? – Must register with InterNIC • Internet Service Provider (ISP) – Companies which establish a domain and then sell addresses within the domain to users, who usually “dial in” with a modem. Provides access to the internet and email. • Peak, ProAxis, MSN, America Online (AOL), AT&T@Home, ... • WWW (World Wide Web) – A world-wide set of documents and files which can be publicly accessed and are linked together through hypertext links. – The web pages we see are written in a hypertext language. Today the standard is HTML or Hypertext Markup Language. There are others and this standard will continue to evolve. – We access these files with a browser. • Netscape Navigator, Microsoft Internet Explorer, Mosaic, Opera, . . . – Pages are accessed with a unique address called a uniform resource locator or URL. • Networks – Networks operate under protocols. (communication protocols) This way everyone is speaking the same language and is abiding by the same rules. • Security – password protection • NEVER use a birthday, your name, your initials, common words, etc. – Encryption • public-key encryption – public key -- used to encode messages (can’t decode) – private key -- used to decode messages • Monitoring – – – – – FBI Your employer This University Your ISP Your parents • Virus • Worm