* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download HUAWEI USG Product Pre-sales Specialist Training
Survey
Document related concepts
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Wireless security wikipedia , lookup
Transcript
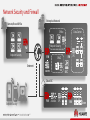
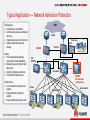
HUAWEI NGFW USG6000 Series Products Pre-sales Specialist Training Version: V1.1(20130801) Contents 1 2 3 4 5 Click toand addPositioning Title Market Summary Product Highlights Click to add Title Product Comparisons Click to add Title Success Stories Quotations &Click Configurations to add Title 2 Global Security Products Market Annual Revenue Statistics of Global Security Products - Infonetics Market Shares of Security Vendors- Infonetics 5.8 billion Unit: Million dollars Cisco 1824.2 McAfee 460.4 Checkpoint 786.8 Fortinet 262.3 Juniper 705.2 Huawei 229.0 In 2011, the global security products revenue reached $5.8 billion, increased 3.3% compared with 2010 revenue. Huawei accounts for 3.9% in the global market and ranks No.6. 3 Middle and Low-End Security Gateway Market Analysis Infonetics Forecast of the Global Security Device Market 1. In 2014, the global firewall, VPN, and UTM markets are expected to reach $3.1 billion. 2. Middle-range and low-end security gateways will account for 71% of the global security gateway market with $2.2 billion. Note: $0 to $5000 security gateways are low-end. $5000 to $30,000 security gateways are middle-range. Security Device Market Forecast — Infonetics Million dollars Low-end and middle-range firewalls $30,000 $10,000 $5,000 $1500 $500 4 Network Security and Firewall Enterprise Network Remote/Branch Office Data Center Office Endpoint Security FW Endpoint Security FW IPS FW DMZ Internet WAF SSL VPN IPS SOC Cloud DC FW Endpoint Security 5 Anti-DDoS IPS FW VFW Typical Application — Security Protection of Private Government Network Existing Issues Private government networks are not isolated. Governmental intranet and Internet communication is not protected. Multiple internal service systems have vulnerabilities. Private province government network USG6000 Solution Add antivirus (AV) isolation at borders for security. Manage unified network security. Solution Values Private government networks are isolated securely. The solution prevents viruses professionally and effectively. The solution controls the range of security events effectively. The solution upgrades vulnerabilities and patches with unified management. … USG6000 City 1 City N … District/County 1 6 Municipal governments … District/County N District/County 1 District/County governments USG6000 District/County N Typical Application — Security Isolation of the Data Center Existing Issues Unsecure heavy traffic isolation Not guaranteed service continuity No anti-DDoS defense No visualized application management Core switch USG6000 WAN Data center switch Solution 10-GB device for security isolation of the data center Hot standby deployment Solution Values Security isolation of 32 Gbit/s traffic on one host Professional 10 Gbit/s anti-DDoS capability Microsecond-level delay and hot standby Zero packet loss ratio to ensure service continuity Visualized service management Application server IP SAN Database server FC SAN Network redundancy and virtualized device: VIS6000 NAS node IP switching plane Backup device: S2600T/S5500T /VIS6600T FC switching plane Redundancy array: S5500 Unified storage device: N8500 NAS IP SAN FC SAN 7 Main data center Geographic redundancy center Typical Application — Network Admission Protection WAN Existing Issues Terminals have vulnerabilities. Authorized users access unauthorized resources. Unauthorized access is not controlled. Numerous terminals are hard to manage. Router Server area Switch USG6000 Terminal security management system Solution Provide a professional gateway solution with excellent adaptability. Manage devices centrally with quick deployment. Support comprehensive terminals. Provide HA and flexible control. Solution Values Forces terminals to protect service systems. Improves network security and usability. Improves efficiency and saves costs. USG6000 IDS NIP1000 Core switch USG6000 Terminal access control gateway Access switch 8 Access switch Access switch Typical Application — Secure VPN Access to Branches Headquarters RADIUS & CA Intranet Existing Issues Unsecure access for branches and mobile working Unsecure data transmission on the Internet VSM management system USG6000 USG6000 VPN Solution Multiple VPN technologies, such as IPSec, L2TP, GRE, SSL, and MPLS Online expansion of the number of tunnels Carrier-class reliability Solution Values Secure, flexible, and reliable VPN access Centralized service management Internet USG6000 Branch USG6000 Branch Remote site 9 Contents 1 2 3 4 5 Click toand addPositioning Title Market Summary Product Highlights Click to add Title Product Comparisons Click to add Title Success Stories Quotations &Click Configurations to add Title 10 NGFW Needs Optimization… Upgrade Management Optimization Traffic Control Security Scope Performance APP Definition Basic FW/VPN 11 Application-aware Integrated IPS For Large Enterprise 1 Fine-granular Access Control 12 Applications Identification No.1 Applications Identification 13 No.1 in Industry Comprehensive Coverage, Fine-grained Control Games Huawei 6000 ALL P2P GAME 450 422 Half-life Freenet Games WeChat Voice/ Text ✔ ✔ ✔ ✘ ✘ ✘ LINE RapidShare Great Wisdom Voice/ Text Upload/ Download Browsing/ Exchange App Only App Only App Only App Only CheckPoint ALL P2P GAME Cisco ALL P2P GAME 1181 75 62 ✔ ✔ ✘ App Only App Only App Only App Only PAN ALL P2P GAME ALL P2P GAME 1600 120 56 ✘ ✔ ✘ App Only App Only App Only App Only 3133 214 148 ✘ ✘ ✔ Fortinet 5000 321 183 14 Voice/ Text Voice/ Text Upload/ Download No Application Awareness: Better Service Visibility & More Refined Control Applications are described in three dimensions: client-server: applications, such as client-side games browser-based: applications, such as browser games Networking: network applications, such as HTTP peer-to-peer: P2P applications, such as Thunder and BT … 5 Categories and 33 Sub-categories Business Systems: Finance: E-bank and stock software • Database: database, such as Mysql • … Entertainment: • Game: Game software, such as Warcraft • Social Networking: social software, such as Facebook • … General Internet: • Web Browsing: web browsing • Search Engines: Search engine, such as Google • File Sharing: file sharing software • … … Data Transmission Mode • Risk Types and Levels Identify 6000+ network applications. Cover main application protocols. Support popular encrypted P2P protocols, Web2.0 applications, mobile apps, and micro-apps. Customize to meet individual needs. Exploitable: applications that have known vulnerabilities Evasive: applications, such as proxy applications, that attempt to evade firewall inspections Data leak: applications that can transmit files or upload text Infected by malicious software: applications infected by malicious software Tunneling protocol: Applications that can use a tunneling protocol to transmit other applications … Risk types risk levels 15 Value of Application awareness? Access Control Service Acceleration Working in conjunction with other defence 16 User Awareness: I Know Who You Are Facing Changing User IP Addresses 8 authentication modes: • Local, RADIUS, LDAP, AD domain, SecureID, TSM, and HWTACACS authentication Values: 17 • Following the mobile working trend • User-based security policies • User-based bandwidth management policies • User-based online behavior management Location Awareness: Where Attacks Are IP Location Identification granularity: • • • • China: city U.S.: state Others: country Support for IP segment-based location definition Application scenarios: • • • Traffic map: location-based application statistical analysis report Attack map: location-based attack statistical analysis report Location policy: access permissions varying according to locations For example: • 18 Some data can be accessed at headquarters, not at branches. Policy Integration: simplify management and improve efficiency Access Control Area Access control policy and content security policies, such as IPS, AV configured in a single interface. Content Security Area 19 2 Easy Security Management 20 Traditional Security Management ? Administrator IT New deployment is difficult. NMS CLI policies never change ? Applied regardless of traffic changes. Web UI Policy ? Security Features 21 Polices become more redundant and difficult to streamline. Smart Policy Management Optimization 22 Quick Deployment Built-in Policy Templates 23 Built-in Application Categories Policy tuning Original Policies Optimization Based On Applications Optimization Based On Security Automatic Traffic Analysis and Security Evaluation Validation Check Manual Optimization Based On Bandwidth New Policies 24 Policy Simplification Finding long-term unused policies: Finding redundant policies: 25 3 Comprehensive Prevention of Threats 26 Comprehensive Security Application security Comprehensive context awareness • • • Awareness of applications, content, time, users, attacks, and locations 8 user authentication modes • Data security Email security • • • 6000+ application protocol identification 5,000,000+ virus detection • Real-time anti-spam Content and keyword filtering • Attachment virus detection and notification 27 30+ file reassembly and content filtering 120+ file type filtering Intrusion prevention • 3500+ attack detection • 90+% false alarm detection rate Web security • • 85,000,000+ URLs in the database 80+ categories Network security Routing • Anti-DDoS • VPN (IPSec/SSL/L2TP/MPLS/GRE …) • • IPv4: static routing, RIP, OSPF, BGP, and IS-IS IPv6: RIPng, OSPFv3, BGP4+, IPv6 IS-IS, IPv6 RD, and ACL6 Intrusion Prevention: 5500+ signatures Detect and defend against over 5500 vulnerabilities 28 Anti-Virus: faster scanning and more fresh signatures • Rich protocols of flow-based antivirus scanning. • Signature database is updated daily. • faster scanning than appliance of competitors. 29 File filtering & Content filtering: Data Loss prevention XXXXXX price XXXX… credit card number :XXXX XXXXXXXXX Bidding material XXXXXX Able to identify actual file types and filtering sensitive content, even it was hidden in compressed files, or it’s extension was modified. 30 URL filtering:Control web browsing activity • 80+URL category • 85,000,000 URLs in database • 20 Language • 500,000 malicious URLs Legitimate websites URL whitelist Illegal /Malicious websites URL blacklist 31 SSL encryption traffic security More and more website use https Content security over SSL decryption URL filtering Anti-virus Instruction prevention SSL traffic:blind spot of security Content filtering File filtering Activity control 32 Bandwidth Management Bandwidth guarantee for key services Connection limit Bandwidth limit QoS tag remark 33 Anti-DDOS Defend against over 10 types of DDoS Automatically set threshold by learning traffic. 34 Dynamic Smart Virtual Private Network (DSVPN) Advantage of DSVPN: Effective IPSec communication between spokes。 simplifies configuration maintenance。 35 Virtualized Security Protection Border Security of Cloud Data Centers Virtual system border defense: Border protection for up to 1000 virtual systems Application identification, IPS, antivirus, and URL filtering C B •Session: XX •Bandwidth: XX •Security: B •Policy Num: X A •Session: XX •Bandwidth: XX •Security: A •Policy Num: X 36 •Session: XX •Bandwidth: XX •Security: C •Policy Num: X Virtualized security protection Resource virtualization Virtualized floating for security policies Tenant-specific management: Customized security management for tenants Customized QoS management for tenants 4 Excellent Performance 37 Unified Performance Experience for NGFW Huawei UNIFIED App/Threat Description Language UNIFIED Security Scan Intrusion Trojan horse IPS Identification Parsing AV UNIFIED Pattern Match UNIFIED PM UNIFIED Scan UNIFIED DL Separate Definitions URL Trojan horse Exploit 38 AV URL 3G 8G 10G 6G / NA 8G 5G Software Only Approach / IPS 8.8G App 20G 20G 12G FW 20G 20G 15G Data IPS Identification Parsing 2.5G Result One By One Detection Intrusion 4G Hardware VS Industry Everything UNIFIED For High Performance Full Protection Software Regular MT DL Exploit 15G Non-regular Data Response Handling VPN Response Handling Data Software Hardware Result Result 20G What is IAE? Web Security URL Categorization Intrusion Prevention File Security Intelligent Awareness Engine Application Classification Application Signatures DLP Scan Virus Definitions Intrusion Signatures 39 Web Attack Signatures Anti-virus DLP Signatures URL Database Everything UNIFIED UNIFIED Security Scan General Contents DLP Scan Routing & Switching URL Scan UNIFIED Response Basic Firewall Features Application Identification IAE UNIFIED Protocol Dissector Intrusion Detection Web Security Scan URL DLP Scan Intrusion Detection File Typer NIC File Stream Virus Scan DLP Scan Intrusion Detection UNIFIED Threat/Application Description Language 40 UNIFIED Pattern Match and Hash Algorithm UNIFIED Decomposition Hardware Acceleration Small/Singleton Requests Bulk/Stream Requests Hardware Based Pattern Match Utilize Utilize Software Based Pattern Match Response Protocol Dissector DLP Scan Intrusion Detection Utilize Utilize Application Identification Security Scan Synchronous Result Asynchronous Result UNIFIED Pattern Match 41 Stream-based File Processing Traditional File Processing Receiving Virus Scan DLP Scan Transmitting Elapsed Time Receiving Huawei NGFW's Stream-based New Approach Virus Scan DLP Scan Transmitting t2 t1 e Segm e Segm Decomposition 42 nts me nts nts Security Scan Response nts File Dissector Se g File Typer Se g me nts Se g me nts me Se g Protocol Dissector Application Identification UNIFIED Security Scan NGFW Appliance USG6300/USG6600 series has 14 models Provides 1G to 40G performance when application identification USG6680, 40Gbps 3U, 4*10GE+16GE+8SFP USG6670, 35Gbps 3U, 4*10GE+16GE+8SFP is enabled. Provides a minimum of 8 GE ports and scalable to a maximum of 64*GE+14*10GE ports USG6660, 25Gbps 3U, 2*10GE+8GE+8SFP USG6650, 20Gbps 3U,2*10GE+8GE+8SFP USG6630, 16Gbps,1U,8GE+4SFP USG6620, 12Gbps,1U,8GE+4SFP USG6390, 8Gbps, 1U,8GE+4SFP USG6380, 6Gbps, 1U,8GE+4SFP USG6370, 4Gbps ,1U,8GE+4SFP Expansion modules USG6360, 3Gbps,1U,4GE+2Combo USG6350, 2Gbps,1U,4GE+4Combo USG6330, 1Gbps,1U,4GE+4Combo USG6320, 2Gbps,Desktop,8GE WSIC-2SFP+&8GE WSIC-8GE WSIC-8SFP USG6310, 1Gbps,Desktop,8GE 43 WSIC-4GE-BYPASS SAS-300GB Contents 1 2 3 4 5 Click toand addPositioning Title Market Summary Product Highlights Click to add Title Product Comparisons Click to add Title Success Stories Quotations &Click Configurations to add Title 44 How to Beat Overview Huawei Vendor Palo Alto CheckPoint Cisco Fortinet Hardware Software Feature Price Palo Alto NGFWs have comprehensive functions and advanced Huawei is stronger than Palo Alto technologies. but Huawei NGFWs deliver more comprehensive in interface quantity and reliability. performance than their counterparts. The host price is low, and the price is more competitive than the vendor if a license is sold together. Huawei is stronger than Check Point NGFWs have comprehensive functions and advanced CheckPoint in interface quantity technologies. but Huawei NGFWs deliver more comprehensive and availability. performance than their counterparts. The host price is low, and the price is more competent than the vendor if a license is sold together. Cisco NGFWs are incompetent in technologies. Huawei has more Huawei is stronger than Cisco in comprehensive software features than Cisco. Therefore, Huawei interface quantity and availability. NGFWs are stronger than Cisco's in both performance and functions. The host price is low, and the price is more competent than the vendor if a license is sold together. Fortinet NGFWs have comprehensive functions. Therefore, The firewall Huawei is stronger than Fortinet The host price is nearly the same, but throughput is relatively weaker but other performance indicators, such in interface quantity and Huawei NGFWs can be more competent if a as new connections per second and concurrent connections are availability. license is sold together. stronger than Fortinet NGFWs. Notes: 1. To beat all vendors, emphasize the number of interfaces and the price advantage with license sold together. 2. Emphasize the high availability and 10G interfaces to increase the price of vendors' devices. 45 Competitiveness Map of USG6000 NGFW Firewall Huawei Throughput Cisco Check Point Fortinet Palo Alto PA-200 1G(desk)* USG6310 30D 60C 2G(desk) USG6320 1140 1180 2200 60D 90D 1G * USG6330 ASA 5512-X 2G * USG6350 ASA 5515-X 3G * USG6360 ASA 5545-X 4G USG6370 ASA 5555-X 6G USG6380 8G USG6390 12G * USG6620 16G * USG6630 20G USG6650 25G USG6660 12400 35G USG6670 12600 1240B 40G USG6680 PA-500 ASA 5525X PA-2050 4200 100D ASA 5585X(SSP10) 200D PA-3020 240D 4400 PA-4060 PA-4050 ASA 5585-X(SSP40) 46 PA-4020 PA-5020 4600 4800 12200 600C ASA 5585-X(SSP60) 280D PA-3050 300C ASA 5585-X(SSP20) PA-2020 800C 1000C 3240C PA-5060 PA5050 Fortinet: FW&UTM Market Leader • Fortinet is the first vendor that launches a UTM device. The annual compound growth rate is greater than 48%. • Ranks No. 1 in the UTM sales market and No. 3 in the global security hardware market. • Provides comprehensive product functions and third-party authentication. With low prices, the cost-effectiveness of Fortinet devices is the major promotion point. • Fortinet claims to help customers invest less (cheap) and protect more (comprehensive functions). 47 How To Beat Fortinet (FortiGate Series) Three methods for winning Key 1. Hardware: Emphasize the use of non-X86 multi-core architecture, use hardware bypass and redundant power supplies, and try your best to configure 10G interfaces. 2. Price: Guide the bidding based on the number of fixed ports on Huawei NGFWs and try your best to configure security function licenses to relatively increase the price of Fortinet NGFWs. 3. Function: Guide the use of application-layer defense functions (the FortiGate series deliver poor performance in this aspect), such as IPS, AV, and DLP, and emphasize the Smart Policy feature, which features scenario template-based policy making, intelligent tuning, and policy simplification. 1. The FortiGate series does not support hardware bypass or dual-power redundancy. 2. Only the 20G or higher products support 10G interfaces, and the maximum number of interfaces is small. 3. Compared with counterparts, the FortiGate series lag behind in new connections per second, concurrent connections, and VPN throughput. beating points 1. The FortiGate series identifies only over 3100 applications, which is far less than that of Huawei (identifies over 6000 applications). 2. The FortiGate series does not support MPLS or application-layer attack defense, such as HTTP, DNS, or SIP attack defense. 3. The FortiGate series neither support security policy intelligent tuning nor redundancy analysis. 48 Palo Alto: Leading the NGFW Industry in Technologies The first NGFW vendor and long-term leader in the Gartner FW quadrant The annual income reaches $400 million in 2013 and increases 30 times in the last five years. Palo Alto ranks No. 5 in the global security hardware market and increases the fastest. Palo Alto developed more than 4800 customers in 2013 and has over 13500 customers in over 120 countries and regions, with 1250 channel partners. Palo Alto NGFWs have comprehensive functions and lead the industry in technologies. It has a good brand in the NGFW market, but the firewall price is high. 49 How To Beat Palo Alto (PA-XXXX Series) Three methods for winning 1. Hardware: Emphasize power redundancy and hardware bypass. 2. Price: Guide the bidding based on the number of fixed ports on Huawei NGFWs and try your best to configure security function licenses to relatively increase the price of Palo Alto NGFWs. 3. Function: Emphasize the Smart Policy feature that features scenario template-based policy making, intelligent tuning, and policy cleanup. 1. Palo Alto NGFWs do not support interface expansion, and only the PA-5060, 5050, and 4060 support 10G interfaces. 2. The PA3000 series and lower supports neither power redundancy nor hardware bypass, delivering poor availability. 3. Compared with counterparts, Palo Alto NFGWs lag behind in all key indicators, such as new connections per second, concurrent connections, VPN throughput, IPS throughput, and AV throughput. Key beating points 1. Palo Alto NGFWs identify only 1600+ applications (Huawei 6000+), support 47 million URLs (Huawei 85 million), and identify 60+ file types in DLP (Huawei 120+), but do not support application-layer anti-DDoS, such as HTTP, DNS, or SIP attack defense. 2. Palo Alto NGFWs do not support mail filtering, CA or SecurID authentication mode, or AV email declaration. 3. Palo Alto NGFWs supports neither security policy intelligent tuning nor redundancy analysis. 4. Palo Alto NGFWs do not support logging or auditing on Internet access behaviors or email sending and receiving. 50 CheckPoint: A Leader in Technology and Market CheckPoint is a long-term leader in the FW quadrant of Gartner, and its security hardware market share ranks No. 2 on the globe. Quote software blades in over ten groups to meet the requirements of different procurement scenarios, in which way CheckPoint delivers a great sum of products. CheckPoint NGFWs provide comprehensive functions, lead in technology, and are good brands in the NGFW market. However, the software blade combinations have high prices. 51 How To Beat CheckPoint (NGFW Series) Three methods for winning Key beating points 1. Hardware: Emphasize power redundancy. For Gigabit high-end models, emphasize the 10G interfaces. 2. Price: Guide the bidding based on the number of fixed ports on Huawei NGFWs and try your best to configure security function licenses to relatively increase the price of CheckPoint NGFWs. 3. Function: Emphasize the Smart Policy feature, which features scenario template-based policy making, intelligent tuning, and policy simplification. 1. Only the 4800 and high support 10G interfaces, whereas all Huawei NGFWs support 10G interfaces except only the desktop devices. 2. The 4200/4400/4600 series supports neither power redundancy not hardware bypass, delivering poor availability. 3. Compared with counterparts, CheckPoint NFGWs lag behind in all key indicators, such as new connections per second, concurrent connections, VPN throughput, IPS throughput, and AV throughput. 1. CheckPoint NGFWs support neither security policy intelligent tuning nor redundancy analysis. 2. CheckPoint NGFWs support neither MPLS/NAT64 nor DSVPN. 3. CheckPoint NGFWs do not provide open XML interfaces, manage only some policies, (Huawei provide at 2014.11) 52 Cisco: A Traditional Tycoon Lacking Visions Ranks No. 1 in the network security hardware market. Mainly sells the ASA-X series firewall and lacks features and visions in the NGFW field. The sales relies on network supporting projects that focus less on security. Acquired Sourcefire in October 2013, but the integration of products takes time. The ASA-X series lag behind in technology, deliver poor competitiveness, and have high prices. 53 How To Beat Cisco (ASA5500-X Series) Three methods for winning 1. Hardware: Emphasize the non-X86 multi-core architecture and configure redundant power supplies and fan modules. 2. Price: Guide the bidding based on the number of fixed ports on Huawei NGFWs and try your best to configure security function licenses to relatively increase the price of Cisco NGFWs. 3. Function: Guide the use of IPS, AV, and DLP together and emphasize the Smart Policy feature, which features scenario templatebased policy making, intelligent tuning, and policy simplification. 1. Only the ASA5585-X series support 10G interfaces. All NGFWs do not support hardware bypass, and the ASA5512/15/25-X do not support dual-power redundancy. 2. The ASA5585-X has only two expansion slots, and the IPS and CX functions require separate hardware support and fail to implement full service processing (FW+IPS+CX). 3. Compared with counterparts, Cisco NFGWs lag behind in all key indicators, such as new connections per second, concurrent connections, VPN throughput, and IPS throughput. 4. ASA5585-X DC power modules are not redundant, the redundant AC power modules cannot coexist with the independent fan module, which easily cause heat dissipation problems, delivering bad reliability. Key beating points 1. Cisco firewalls identify only over 1000 applications, which is far behind that of Huawei (identifies over 6000 applications). Besides, Cisco firewalls do not support user-defined applications. 2. Bad security capability: All series do not support file blocking or data filtering. The ASA5500-X series does not have any AV engine and does not support Chinese encryption algorithms. 3. Cisco firewalls do not support GRE, GRE over IPSec, IPSec over GRE, IPSec IPv6, 6RD, or DS-Lite, and fail to implement smooth IPv4-IPv6 transition. 4. Cisco firewalls neither support security policy intelligent tuning nor redundancy analysis. The FW and CX modules are independent NEs, and FW/VPN functions cannot be managed using the same management software that is used to manage CX functions. The management is complicated. 5. The CX module provides only simple rate limiting and does not support application-specific policy routing. 54 Contents 1 2 3 4 5 Click toand addPositioning Title Market Summary Product Highlights Click to add Title Product Comparisons Click to add Title Success Stories Quotations &Click Configurations to add Title 55 Lots of Commercial Use 6052 pieces Alibaba Cloud Computing 国家超级计算中心 112858 pieces Note: the shipment was collected until 2013 Dec. 56 Dortmund Signal Iduna Park stadium Huawei end-to-end stadium solutions Security Solution Dortmund Signal Iduna Park stadium is Germany's largest, the world's ninthlargest football field, can accommodate more than 80000 viewers watch the game. As a security solution for the WIFI system. Huawei NGFW developed a intelligent identification management based on URL. In the whole ICT solution, Huawei NGFW provided fine-grained control, all threat high performance prevention, integrated IPS, URL filtering features, ensuring the best network experience for customer. 57 ICITA public cloud network in Australia Sydney ·Australia • Serving more than 100 large enterprises • 6 dimensional fine-grained control • Full Threat Protection 10+ Gbps “USG6000 takes all the box to get ability to build on infrastructure network to provide multi -tenancy for our partners. It could complete separation, so each partner can build their own virtual data center. In fact it has module, so we can expand as our requirements. The cost is also very effective. We don't have specific security engineer in the infrastructure, but we can provide security support as a service for our customers.” Public cloud service provider in Australia 58 Damien Stephens, CEO of ICITA Opole OSTO, Poland The City of Opole ·Poland Security Solution The project includes delivery of 3 core routers, 3 edge routers, 5 firewalls, 69 access switches. HUAWEI USG6000s are deployed at the edge of the optical telecommunication network after HUAWEI NE40E routers to secure the internal network and enhance data transmission security. HUAWEI USG6000s cooperate with Policy Center to perform secure access. Customer Values The City of Opole 59 Huawei USG6600 series demonstrated its good firewall performance at layer 7. The success is a good reference for the Government network security expansion. Guangdong Smart Grid Network Huawei's Security Solution Huawei deploys its USG6650 products at the Internet egress and comprehensive information network border. The USG6650 provides 10 Gbps all threat defense performance and a powerful NAT function for the Internet egress. In addition, Huawei's solution manages devices on the entire network through a unified management center to implement power dispatching management and report display, helping China Southern Power Grid build a simplified, highly efficient security protection system. Customer Benefits Feature- and sandbox-based all threat defense methods, guaranteeing smooth office services for China Southern Power Grid When the all threat defense feature is enabled, the performance decrease is less than 50%. High-performance security protection and high-quality user experience support large volumes of service traffic. Automatic policy management based on traffic learning reduces the Total Cost of Ownership (TCO) by over 30%. 60 Beijing University of Posts and Telecommunications Security Solution Deploy a USG6600 at the network egress and access the WAN via multiple ISP links. Implement application identification, traffic management, and comprehensive inspection Customer feedback “Huawei NGFW can automatically learn the traffic patterns and provide detailed suggestions for policy fine tuning. These functions provide good visibility into applications on our network so that we can determine which applications need to be protected and which need to be controlled. We can easily fine tune the policies based on the suggestions.” 61 Jie An Deputy director of the information network center Ministry of education in Portugal Construct a public government affairs platform for the ministry of education in Portugal, meeting the requirements on high-performance, high availability, and comprehensive security. This platform supports real-time online visits and public affairs query from users in the entire country 。 Customer challenges • 20G performance to carry real-time services and ensure service continuity and availability • No effective defense against frequent attacks in various forms Solution • Deploy a USG6680 at the service border to provide 20G bidirectional service protection, ensuring service continuity. • Enable service protection against DDoS and application-layer attacks and deploy Huawei cloud sandbox to defend against unknown threats. 62 Contents 1 2 3 4 5 Click toand addPositioning Title Market Summary Product Highlights Click to add Title Product Comparisons Click to add Title Success Stories Quotations &Click Configurations to add Title 63 USG6000 Marketing Patterns FW (include App, Anti-spam) IPS AV URL License Bundle FW (include App, Anti-spam) IPS AV URL VSYS (10 default) SSL (100 default) x 10 x 100 x 20 x 200 x 50 x 500 x 100 x 1000 x 200 x 2000 x 500 x 5000 Device + License Bundle(1 Year) FW (include App, Anti-spam) IPS AV URL 1 year or 3 years x 1000 Device Update License 64 Function License USG Configuration Guide 1. Select a appliance device Bundles device 2 Select expansion interfaces (optional) Layer-3 Ethernet interfaces: WSIC/1FE/1GE/4FE/2FE2FEC. HDD: Used for report and Smart Policy feather. 3. Value-added functions (optional) SSL VPN license (100/200/500/1000/2000/ 5000) VFW license (10/20/50/100/200/500/10 00) 4. Materials Optical module Optical fiber connector Cable Security license (1/3/YS) References: 1. Network throughput 2. Number of users 3. Interfaces IPS license AV license URL Filtering license Three-in-one bundle license 65 HUAWEI ENTERPRISE ICT SOLUTIONS A BETTER WAY Copyright©2012 Huawei Technologies Co., Ltd. All Rights Reserved. The information in this document may contain predictive statements including, without limitation, statements regarding the future financial and operating results, future product portfolio, new technology, etc. There are a number of factors that could cause actual results and developments to differ materially from those expressed or implied in the predictive statements. Therefore, such information is provided for reference purpose only and constitutes neither an offer nor an acceptance. Huawei may change the information at any time without notice.