* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download slides - Computer Science
Survey
Document related concepts
Mobile operating system wikipedia , lookup
Copland (operating system) wikipedia , lookup
Spring (operating system) wikipedia , lookup
Process management (computing) wikipedia , lookup
Distributed operating system wikipedia , lookup
Linux kernel wikipedia , lookup
Transcript
Dancing with Giants: Wimpy Kernels
for On-demand Isolated I/O
Presenter: Probir Roy
Computer Science Department
College of William & Mary
Isolated security-sensitive
application
Towards Application Security on Untrusted Operating
Systems (by DRK Ports - 2008)
Isolated security-sensitive
application
Tamper-Resistant Execution in an Untrusted Operating
System Using A Virtual Machine Monitor (H Chen 2007)
AppShield: Protecting Applications
against Untrusted Operating
System (by Y Cheng - 2013)
TrustVisor: Efficient TCB Reduction and
Attestation (by JM McCune - 2010)
Isolated security-sensitive
application
MiniBox: A Two-Way Sandbox for x86 Native
Code (by Y Li - 2014)
Design, Implementation and Verification of an
eXtensible and Modular Hypervisor
Framework(by A Vasudevan - 2013)
Many More ...
Isolated application
Wimps
Giants
{
Limitations of Isolated application
Wimps
software
components
must be
verified
Giants
{
Wimps
Lack :
Small, simple, limited in
function
- persistent memory
- file system and network services,
- flexible trusted paths to users, and
- isolated I/O services
Limitations of Isolated application:
Example
Providing Trustworthy services
Approach 1: Restructure Giant for trust-worthy services
Problem: lacks scalable performance
Providing services to Isolated
application
Approach 2: Include basic services to TCB
Problem: Increases code base
Providing services to Isolated
application
Approach 3: Wimps reuse giant-provided services but only after efficiently
verifying their results
Requires:
P1: On-demand isolated
I/O Channel
P2: Complete Mediation
of time-multiplexed
accesses to devices
P3: Minimization of the Trusted
Codebase
Giants can use Wimp services for protection against persistent threats
Wimpy Kernels for On-demand
Isolated I/O
Adversary Model
2) Malicious wimp application may escalate its
privilege by manipulating the interfaces with the I/O
isolation system or configuring the wimp app’s devices
1) Compromised OS can attack
wimp apps or intentionally control
or mis-configure any device
3) Wimp Apps can break application isolation or even
compromise OS execution and corrupt its data
Security requirements
P1. I/O Channel
Isolation.
P2. Complete
Mediation.
P3. Minimization of the Trusted Codebase.
(1) the code base of
a trusted I/O kernel must be minimized to facilitate formal
verification; and (2) the underlying TCB must be
unaffected
by the addition of a trusted I/O kernel
System Component
Implementing Security
Properties: Wimpy kernel
Wimpy kernel is an add-on trustworthy component,
Dynamically controls hardware resources necessary to establish isolated I/O
channels between wimp apps and I/O devices (P1: I/O Channel Isolation)
On-demand Isolated I/O
Four significant
advantages
Enables wimp applications to obtain isolated I/O
channels to any subset of a system’s commodity
devices needed during a session
Enables trusted audit and control of physical
devices without stopping and restarting
applications,
Allows unmodified commodity OSes to have unfettered
access to all hardware resources and preserve the entire
application ecosystem unchanged
Offers a significant opportunity for the
reduction of the trusted I/O kernel size and
complexity
Implementing Security
Properties
Wimple Kernel compose with three other system
components
MHV: To maintain memory integrity and address space
separation (P3-II:TCB must be unaffected)
Untrusted OS: wimpy kernel outsources its most complex
functions to the untrusted OS (P3-I: Small and simple
Code base)
Wimp apps: minimize wimp kernel code base
by de-privileging and exporting some of its
code to wimp applications (P3-I: Small and
simple Code base)
Wimp kernel mediates all accesses of
the exported code to I/O devices and channels under its
control
(P2: Complete Mediation.)
Implementing Security
Properties: Details
Outsource-and-Verify& Export-and-Mediate
Implementing Security
Properties: Details
P1 & 3-I: I/O Channel Isolation & Small and simple Code base: Outsource-and-Verify
1) Untrusted OS initializes the USB hierarchy
Outsource
2) wimpy kernel verifies their correct configuration and initialization.
Implementing Security
Properties: Details
P1 & 3-I: I/O Channel Isolation & Small and simple Code base: Outsource-and-Verify
1) Untrusted OS initializes the USB hierarchy
2) wimpy kernel verifies their correct configuration and initialization.
Resolve the threat of USB address overlap and remote wake-up attacks
Implementing Security
Properties: Details
Outsource-and-Verify& Export-and-Mediate
Implementing Security
Properties: Details
P2 & 3-I: Complete Mediation & Small and simple Code base: Export-and-Mediate
1) Bus subsystem code exported by the wimpy kernel to a wimp app
2) WK verifies the behavior of the wimp apps that may affect wimp app
isolation from the OS
Implementing Security
Properties: Details
P2 & 3-I: Complete Mediation & Small and simple Code base: Export-and-Mediate
1) Bus subsystem code exported by the wimpy kernel to a wimp app
2) WK verifies the behavior of the wimp apps that may affect wimp app
isolation from the OS
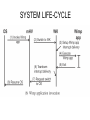
SYSTEM LIFE-CYCLE
SYSTEM LIFE-CYCLE
EVALUATION
EVALUATION
Scanning
Process
Contribution
Introduce the notion of on-demand isolated I/O channels for security-sensitive
applications on unmodified commodity platforms
Present a security architecture based on a minimal wimpy kernel, without
affecting the underlying TCB.
how the classic outsource-and-verify and export-and-mediate methods
are used to minimize the wimpy kernel, and report on the minimization
results in detail.
Implement and Evaluate the wimpy kernel for the USB subsystem
Questions