* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download lesson13
Survey
Document related concepts
Transcript
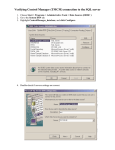
Permissions Lesson 13 Skills Matrix Security Modes • Maintaining data integrity involves creating users, controlling their access and limiting their ability to read, change, add or delete data. • SQL Server processes user names and passwords according to an authentication mode. SQL Server provides two such modes: – Windows Authentication. – Mixed. Windows Authentication Mode • With this mode, users can sit down at their computers, log in to the Windows domain, and gain access to SQL Server using the Kerberos security protocol. • Use Windows Authentication mode so users don’t have to remember multiple usernames and passwords. • Only users with Windows accounts can open a trusted connection to SQL Server. – This means others, such as Apple or Linux clients, can’t use Windows Authentication mode because they don’t have a Windows user account. Mixed Mode • Mixed mode allows both Windows Authentication and SQL Server Authentication (or Standard Authentication). • Anyone can gain access to SQL Server using Mixed mode. Mac users, Novell users, Unix users, and the like, can gain access using SQL Server authentication. Permissions • Now that you’ve created user accounts for everyone, you need to restrict what those users can do with the database. • You do so by assigning permissions directly to the users or adding the users to a database role with a predefined set of permissions. Permissions • These permissions control create, alter and drop actions on: – Databases – Tables – Views – Procedures – Indexes – Rules – Defaults Object Permissions • Once the structure exists to hold the data, you need to give users permission to start working with the data in the databases. • You accomplish this by granting object permissions to your users. • Using object permissions, you can control who may read from, write to, or otherwise manipulate your data. Object Permissions • Alter • Control • Create • Delete • Execute • Impersonate • Insert • References • Select • Take Ownership • Update • View Definition Permission States • All the permissions in SQL Server can exist in one of three states: – Granted – Revoked – Denied Using Impersonation • SQL Server supports the ability to impersonate another principal either explicitly by using the stand-alone EXECUTE AS statement, or implicitly by using the EXECUTE AS clause on modules. • The stand-alone EXECUTE AS statement can be used to impersonate server-level principals, or logins, by using the EXECUTE AS LOGIN statement. – The stand-alone EXECUTE AS statement can also be used to impersonate database level principals, or users, by using the EXECUTE AS USER statement. Using Impersonation • Implicit impersonations that are performed through the EXECUTE AS clause on modules impersonate the specified user or login at the database or server level. – This impersonation depends on whether the module is a database-level module, such as a stored procedure or function, or a serverlevel module, such as a server-level trigger. Cross-Database Ownership • SQL Server can be configured to allow ownership chaining between specific databases or across all databases inside a single instance of SQL Server. • Cross-database ownership chaining is disabled by default. • When multiple database objects access each other sequentially, the sequence is known as a chain. • Ownership chaining enables managing access to multiple objects, such as multiple tables, by setting permissions on one object, such as a view. Summary • SQL Server has a sophisticated security system that allows you to carefully implement your security plan. – SQL Server can operate in Mixed security mode, which means Windows users and groups can be given access directly to SQL Server; or you can create separate, unique accounts that reside only in SQL Server. – If SQL Server runs in Windows Authentication mode, every user must first connect with a preauthorized Windows account. Summary • Each database in SQL Server has its own independent permissions. • You looked at the two types of user permissions: statement permissions, which are used to create or change the data structure, and object permissions, which manipulate data. • Remember that statement permissions can’t be granted to other users. Summary • This lesson examined the processes of creating and managing logins, groups, and users. • You learned how to create a Standard login and a Windows user or group login using SQL Server Management Studio or T-SQL, and you learned the appropriate use of each. • If you have a well-designed security plan that incorporates growth, managing your user base can be a painless task. Summary for Certification Examination • Know the differences in authentication modes. • Know when to use Mixed mode versus Windows Authentication mode. • Mixed mode allows users who do not have an Active Directory account, such as Novell or Unix users, to access the SQL Server. • Windows Authentication mode allows only users with Active Directory accounts to access SQL Server. Summary for Certification Examination • Understand permissions. Know what the permissions are, what they are for, as well as how to assign them. • Don’t forget that two types of permissions exist, object and statement. • Object permissions control a user’s ability to create or modify database objects, such as tables and views. • Statement permissions control a user’s ability to manipulate data using statements such as SELECT or INSERT.



















![Did You Know? SQL Server 2008 * [Feature]](http://s1.studyres.com/store/data/002454547_1-127f1f83c4aa125339e9dfae02309208-150x150.png)