* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network Security
Deep packet inspection wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Distributed firewall wikipedia , lookup
TCP congestion control wikipedia , lookup
Internet protocol suite wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Wireless security wikipedia , lookup
Computer security wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
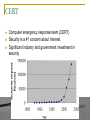
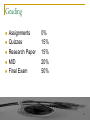
Network Security Lecture 1 Course Overview http://web.uettaxila.edu.pk/CMS/coeCCNbsSp09/index.asp Waleed Ejaz [email protected] 1 Overview Goal of this course Grading Prerequisites Tentative Schedule Security Goals 2 Goal of This Course Comprehensive course on network security Includes both theory and practice Theory: Cryptography, Hashes, key exchange, Email Security, Web Security Practice: Hacking and Anti-Hacker techniques Graduate course: (Advanced Topics) Lot of independent reading and writing Survey paper 3 CERT Computer emergency response team (CERT) Security is a #1 concern about Internet. Significant industry and government investment in security 4 Prerequisites Computer Communication & Networks 5 Prerequisites ISO/OSI reference model TCP/IP protocol stack Full-Duplex vs half-duplex UTP vs Wireless Cyclic Redundancy Check (CRC) CRC Polynomial Ethernet IEEE 802 MAC Addresses Bridging and Routing IEEE 802.11 LAN 6 Prerequisites (contd.) IP Address Subnets Private vs Public Addresses Address Resolution Protocol (ARP) Internet Control Message Protocol (ICMP) Routing - Dijkstra's algorithm Transport Control Protocol (TCP) User Datagram Protocol (UDP) TCP connection setup TCP Checksum Hypertext Transfer Protocol (HTTP) 7 Text Book Charlie Kaufman, Radia Perlman, and Mike Speciner, "Network Security: Private Communication in a Public World," 2nd Edition, Prentice Hall, 2002, ISBN: 0130460192. 8 Reference Book Cryptography and Network Security, by William Stallings, Prentice Hall, 4th Edition, 2006 Few topics from this book will be followed during this course. All relevant material will be provided as notes or as part of the class slides. 9 Course Outline Course Overview Security Concepts TCP/IP Security Attacks Security Key Cryptography (Chapter 3) Modes of Operation (Chapter 4) Hashes and Message Digest (Chapter 5) Public Key Cryptography (Chapter 6) Authentication: Passwords, Biometrics (Chapter 10) Kerberos (Chapter 14) Public Key Infrastructure (Chapter 15) IPSec (Chapter 17) 10 Course Outline (contd.) Internet Key Exchange (IKE) (Chapter 18) Web Security: SSL/TLS (Chapter 19) Email Security: PGP (Chapter 22) Firewalls (Chapter 23) VPNs DNS Security Network Access Controls: AAA Wireless Security Intrusion Detection DMZ (LAN->WAN) 11 Grading Assignments Quizzes Research Paper MID Final Exam 0% 15% 15% 20% 50% 12 Term Project A survey paper on a network security topic Wireless Network Security Key Exchange Protocols Comprehensive Survey: Technical Papers, Industry Standards, Products A real attack and protection exercise on the security of a system (web server, Mail server, …) – Groups of 2 students (Hacker and Administrator) Recent Developments: Last 5 to 10 years ⇒ Not in books Better ones may be submitted to magazines or journals 13 Project Schedule Week 3: Topic Selection/Proposal Week 6: References Due Week 9: Outline Due Week 13: First Draft/Demo Due Week 16: Final Report Due 14 Office Hours Monday: 1:00 PM to 3:00 PM Office: Room 9 Contact Office: +92-51-9047573 Best way to communicate with me in other then office hours is email: [email protected] Do mention MSc Student in Subject Field 15 FAQs Yes, I do use “curve”. Your grade depends upon the performance of the rest of the class. All exams are closed-book and extremely time limited. Exams consist of numerical and may be multiple-choice (truefalse) questions. 16 Quiz 0: Prerequisites 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. True or False? Subnet mask of 255.255.255.254 will allow 254 nodes on the LAN. Time to live (TTL) of 8 means that the packet can travel at most 8 hops. IP Address 128.256.210.12 is an invalid IP address CRC Polynomial x32+x15+1 will produce a 32 bit CRC. DHCP server is required for dynamic IP address assignment DNS helps translate an name to MAC address Port 80 is used for FTP. IPv6 addresses are 32 bits long. New connection setup message in TCP contains a syn flag. 192.168.0.1 is a public address. Marks = Correct Answers _____ - Incorrect Answers _____ = ______ 17 Quiz 0: Prerequisites (Solution) 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. True or False? Subnet mask of 255.255.255.254 will allow 254 nodes on the LAN. False Time to live (TTL) of 8 means that the packet can travel at most 8 hops. True IP Address 128.256.210.12 is an invalid IP address. True CRC Polynomial x32+x15+1 will produce a 32 bit CRC. True DHCP server is required for dynamic IP address assignment. True DNS helps translate an name to MAC address. False Port 80 is used for FTP. False IPv6 addresses are 32 bits long. False New connection setup message in TCP contains a syn flag. True 192.168.0.1 is a public address. False Marks = Correct Answers _____ - Incorrect Answers _____ = ______ 18 Network Security Lecture 1 TCP/IP Security Attacks http://web.uettaxila.edu.pk/CMS/coeCCNbsSp09/index.asp Waleed Ejaz [email protected] 19 Overview TCP Segment Format, Connection Setup, Disconnect IP: Address Spoofing, Covert Channel, Fragment Attacks, ARP, DNS TCP Flags: Syn Flood, Ping of Death, Smurf, Fin UDP Flood Attack Connection Hijacking Application: E-Mail, Web spoofing Ref: Gert De Laet and Gert Schauwers, “Network Security Fundamentals,” Cisco Press, 2005, ISBN:1587051672 20 Security Goals Security Goals Confidentiality: Need access control, Cryptography, Existence of data Integrity: No change, content, source, prevention mechanisms, detection mechanisms Availability: Denial of service attacks, Confidentiality, Integrity and Availability (CIA) 21 Security Attacks Security Attacks Snooping Modification Traffic Analysis Masquerading Threat to Confidentiality Replaying Denial of Service Threat to Availability Repudiation Threat to Integrity 22 Passive Versus Active Attacks Bob Alice Alice and Bob want to communicate in presence of adversaries Adversaries: Passive – just looking Active – may change msgs 23 Categorization of passive and active attacks Attacks Passive/Active Threatening Snooping Traffic Analysis Passive Confidentiality Modification Masquerading Replaying Repudiation Active Integrity Denial of Service Active Availability 24 TCP segment format 20 to 60 Byte header 25 Connection establishment using three-way handshaking A SYN segment cannot carry data, but it consumes one sequence number. A SYN + ACK segment cannot carry data, but does consume one sequence number. An ACK segment, if carrying no data, consumes no sequence number. 26 Connection termination using three-way handshaking The FIN segment consumes one sequence number if it does not carry data. The FIN + ACK segment consumes one sequence number if it does not carry data. 27 IP address Spoofing Send requests to server with someone X's IP address. The response is received at X and discarded. Both X and server can be kept busy ⇒ DoS attack 28 TCP Flags Invalid combinations May cause recipient to crash or hang 29 Syn Flood A sends Syn request with IP address of X to Server V. V sends a syn+ack to X X discards syn+ack leaving an half open connection at V. Many open connections exhausts resources at V ⇒ DoS 30 Ping of Death Send a ping with more than 64kB in the data field. Most systems would crash, hang or reboot. 31 Smurf Send a broadcast echo request with the V's source address. All the echo replies will make V very busy. 32 Fin In the middle of conversation between X and V. H sends a packet with Fin flag to V. V closes the connection and disregards all further packets from X. RST flag can be used similarly 33 Connection Hijacking H sends packets to server X which increments the sequence number at X. All further packets from V are discarded at X. Responses for packets from H are sent to V confusing him. 34 Address Resolution Protocol 35 ARP: Address Resolution Protocol Mapping from IP addresses to MAC addresses Request .1 08:00:20:03:F6:42 .2 .3 .4 00:00:C0:C2:9B:26 .5 192.168.0 arp req | target IP: 192.168.0.5 | target eth: ? Reply .1 08:00:20:03:F6:42 .2 .3 .4 00:00:C0:C2:9B:26 .5 192.168.0 arp rep | sender IP: 192.168.0.5 | sender eth: 00:00:C0:C2:9B:26 36 ARP Spoofing X tries to find the MAC address of Victim V Hacker H responds to ARP request pretending to be V. All communication for V is captured by H. Countermeasure: Use static ARP 37 DNS Spoofing DNS server is compromised to provide H's IP address for V's name. Countermeasure 38 Email Spoofing From address is spoofed. Malware attachment comes from a friendly address. From: [email protected] 39 Web Spoofing The web site looks like another Southwest Airline, http://airlines.ws/southwest-airline.htm For every .gov site there is a .com, .net giving similar information For misspellings of popular businesses, there are web sites. 40 Summary 1. TCP port numbers, Sequence numbers, ack, flags 2. IP addresses are easy to spoof. ARP and DNS are not secure. 3. Flags: Syn Flood, Ping of Death, Smurf, Fin, Connection Hijacking 4. UDP Flood Attack 5. Application addresses are not secure 41 References 1. Gert De Laet and Gert Schauwers, “Network Security Fundamentals,” Cisco Press, 2005, ISBN:1587051672 42 Lab Home Work 1: Gathering Information Learn about IPconfig, ping, arp, nslookup, whois, tracert, netstat, route, hosts file 1. Find the IP addresses of www.google.com 2. Modify the hosts file to map www.google.com to 128.252.166.33 and do a google search. Remove the modification to the host file and repeat. 3. Find the domain name of 128.272.165.7 (reverse the address and add .inaddr. arpa) 4. Find the owner of www.google.com domain 5. Find route from your computer to www.google.com 6. Find the MAC address of your computer 7. Print your ARP cache table. Find a server on your local network. Change its ARP entry in your computer to point to your computer’s MAC address. Print new ARP cache table. Now use the service and see what happens. 8. Print your routing table and explain each line (up to line #20 if too many) 9. What is the number of packets sent with “destination unreachable” 10. Find the location of 128.252.166.33 (use www.ipaddresslocation.org) 43 Questions! 44