* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Digital Communication System
Digitization wikipedia , lookup
Stingray phone tracker wikipedia , lookup
Nyquist–Shannon sampling theorem wikipedia , lookup
Single-sideband modulation wikipedia , lookup
Analog television wikipedia , lookup
Telecommunications engineering wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
History of wildlife tracking technology wikipedia , lookup
History of smart antennas wikipedia , lookup
Telecommunication wikipedia , lookup
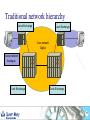
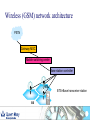
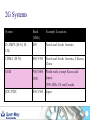
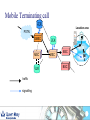
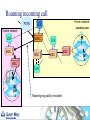
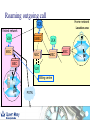
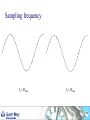
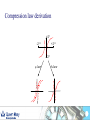
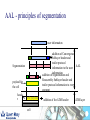
Telecoms Systems (Week 1) Prof. Laurie Cuthbert Dr. Michael Chai Dr Frank Gao Staff Prof Laurie Cuthbert – weeks 1 and 4 [email protected] Dr Michael Chai – week 3 [email protected] Dr Frank Gao – week 2 [email protected] 2 Changes since last year Content has not changed Exam format different – now 4 compulsory questions in 2 hours: – One on each week’s material Remember: – QM rules on extenuating circumstances apply 3 Assessment Exam: 88% Class tests: 12% – – – – – – – Class test every week of teaching on Friday Each group split into 2 You must be in the right group Test is a question on anything taught that week Roughly half an exam question Each test counts 3% Open book 4 Emphasis on Why How When you come to the lecture, bring: – – – – Pen Paper Lecture notes Calculator You will have to do problems in the class!! 5 Learning Outcomes Explain the principles of operation and architectures of circuit-switched and packet/cell-switched network; wired and mobile. Describe the operation of transmission and switching systems. Calculate simple numerical problems on aspects of source coding, error-control coding, Queuing Theory and Information Theory. 6 Extenuating circumstances Must be for 'unplanned circumstances that outside of your control These include medical and personal circumstances such as close family being ill, but not events such as: – – – – – – planned holidays, job interviews or internships GRE or IELTS preparation or test misreading timetables, computer problems, not being aware of rules or procedures. Medical conditions must be sufficiently serious that they would have a major affect on your examination. QM rules ECs for all QM modules will be treated under QM rules If you want to claim EC for an exam or class test you must: – Complete a form in English (from Jing Liu) – Add supporting evidence (e.g. medical certificate) – Give everything back to Jing Liu at least 1 week before the examination board Your BUPT tutor does NOT have the authority to approve ECs for QM modules MODERN TELECOMMUNICATIONS 9 Telecommunication system – a system for conveying content For example, the UK Telecommunications Act 1984, s.4(1) defines it as: “a system for the conveyance through the agency of electric, magnetic, electromagnetic, electro-chemical or electromechanical energy, of (a) speech, music or other sounds; (b) visual images; (c) signals serving the impartation (whether as between persons and persons, things and things or persons and things) of any matter otherwise than in the form of sounds or visual images; or (d) signals serving for the actuation or control of machinery or apparatus”. 10 “More communications than we know how to use” Many different technologies Developed in parallel Lead time to introduce new services decreasing “Reliability” of software decreasing – Online patches for mobile phones Remote working is now normal 11 Legacy - wired communications using telephony fax analogue digital Analogue Dial-up modem Obsolete !!!! exchange Digital 12 Mobile communications Tablet often a radio link to network WLAN 3G/HSDPA WLAN 2G/3G/HSDPA/LTE Cable / radio (Bluetooth) 13 IP allows competition with telephony Webcam Headset SIP phone Dual cordless phone that connects to a normal phone line and the computer All telephony is going IP 14 Now telephony is SIP based 15 Transport modes Traditionally telephony was circuit switched: – – – – – Call set up, conversation and clear-down phases 64 kbit/s (in digital era) allocated in both directions Much of the capacity wasted Analogue to digital conversion in local exchange Control very much centralised Now IP-based – – – – SIP sets up and clears down connections Transport RTP A-D conversion in the telephone More distributed 16 Traditional network hierarchy Local Exchange Local Exchange Core network Digital Access network Analogue Trunk Exchange Trunk Exchange 17 Transmission Connections are carrying little traffic are served with low capacity links – Up to 120Mbps in UK for broadband Very high speed optical fibre links between major cites – In excess of 500 Mbps and support over 7000 voice calls 18 Switching used to be manual 19 Then relays, then electronic – but specialised Electromechanical exchange picture courtesy of Nortel Private electronic exchange 1983 1960s 20 Now just boxes of electronics – high volume IP router WLAN AP Servers All of these are just “boxes” of Electronics IP switch IP phone 21 Wireless (GSM) network architecture PSTN Gateway MSC Mobile switching centre Base station controller BTS BTS=Base transceiver station BS History of wireless communications 1865 James Clerk Maxwell published his equations 1887 Heinrich Hertz demonstrated EM wave propagation 1893 Nicola Tesla demonstrated communication by radio 1895 Aleksandr Popov demonstrated a wireless system 1896 Guglielmo Marconi demonstrated wireless telegraphy 1901 First wireless signal sent across the Atlantic Ocean from Cornwall to St. John’s, Newfoundland (Canada) Marconi was not the ‘inventor’, but appreciated the commercial opportunities offered by the new medium. Why wireless? No more cables – No cost for installing wires or rewiring – Wiring is infeasible or costly in some areas, e.g.. rural areas, old buildings… Mobility and convenience – Allows users to access services while moving: walking, in vehicles… Flexibility – Roaming allows connection any where and any time Scalability – Easier to expand network coverage compared to wired networks. Challenges of wireless Limited resources: finite radio spectrum – Frequency reuse, breaking cells into smaller cells, more efficient medium access technology, e.g. CDMA… Supporting mobility - Location management, handover, … Maintaining Quality of Service (QoS) over unreliable wireless links – Radio propagation attenuation: path loss, shadowing, multipath fading. Connectivity and coverage - roaming and internetworking Security – Wireless channels are “open” – Certification and authentication Integrated services (voice, data, multimedia, etc.) over a single network – service differentiation, priorities, resource sharing,... Mobile terminal battery life You will learn more about all of this later Emerging and existing wireless technology Mobile Wireless: – 2G: GSM, TDMA, CDMA – 2.5G EDGE, GPRS – 3G W-CDMA, HSDPA, HSUPA – 4G - LTE Fixed Wireless: – MMDS, LMDS, Satellite dish, Microwave Mobile cellular Point-Point/ Multipoint Wireless Wireless LAN: – IEEE 802.11, Ad-hoc, Bluetooth, WiMax Wireless LAN Satellite wireless Types of wireless network WPAN (Wireless Personal Area Network) – typically operates within about 30 feet WLAN (Wireless Local Area Network) – operates within 300 yards WMAN (Wireless Metropolitan Area Network ) – operates within tens of miles WWAN (Wireless Wide Area Network ) – operates over a large geographical area, mobile phone, … Features of mobile communications Mobile phones are portable, convenient, move with people. – By their nature, they are location aware. Limited frequency bandwidth Low power: max mobile transmit power – 125mW for WCDMA – 2W peak for GSM900 – 1W for GSM1800/1900 Point to multi-point, not broadcast Cellular concept Late 40s: AT&T developed cellular concept for frequency reuse Break the service area into cells Shrink the cell size; adopt intensive frequency re-use Add more cells to add more capacity Mobility management is required Evolution of mobile networks “It is dangerous to put limits on wireless” Guglielmo Marconi in 1932……. 1970’s Proposed late 1980’s GSM launched in 1992 1990’s –present Proposed in 1998 Launched in UK 2003 1G 2G 2.5 G 3G Evolution of mobile networks NTT TACS NMT AMPS 1G GSM IS-136 IS-95 PDC GPRS HSCSD EDGE IS-95B W-CDMA (3GSM) TDSCDMA cdma2000 4G ? 3G 2.5G 2G Higher bit rate ? New applications ? Speech & low rate data service Digital transmission Speech, data, multimedia Speech service services Analogue Bit rate up to 2 Mbit/s transmission Digital transmission 1G systems Analogue – Speech – Some data at 1.2kbit/s Designed for car use First handportable – Motorola “Brick” (DynaTAC 8000X ) – – – – 1983 800g 30 mins talk time USD 3995 Insecure – Eavesdropping – Cloning Almost no roaming Some 1G systems System Band (MHz) Example Locations AMPS 800 US, Canada, Mexico, Australia, New Zealand, Hong Kong, Brazil, Argentina TACS 900 UK, Ireland, Spain, Italy, Austria NMT 450/900 Denmark, Finland, Norway, Sweden, Belgium, Austria, France, Hungary, Netherlands, Spain NTT 800 Japan (First cellular system 1979) No real roaming apart from NMT 2G Systems Speech and low bit rate data service Digital transmission Designed to be more secure Almost exclusively handportable 2G Systems System Band (MHz) Example Locations D-AMPS (IS-54, IS136) 800 North and South America CDMA (IS-95) 800/1900 North and South America, S Korea, China GSM 900/1800 World-wide (except Korea and Japan) 1900 1900 MHz US and Canada JDC/PDC 800/1500 Japan GSM Officially launched in 1992 Multiple access: TDMA 8 channels (frames of 8 time slots) on each carrier FDD (Frequency Division Duplex) – different frequencies for uplink and downlink 200kHz carrier bandwidth 9.6kb/s net data (13kb/s encoded voice) (Almost) worldwide availability with multi-band handset Useful link www.gsmworld.com GSM worldwide success Over 860 networks in 220 countries/areas Still growing: No of GSM + 3 GSM subscribers – – – – 11/9/2011 00.55 (CN time) 5,231,269,752 In the next 5 mins an increase of: 7,106 !!!!! World Population at same time: 6.914 billion Penetration 59% System Uplink (MHz) Downlink (MHz) GSM850 824 -849 880 -915 GSM900 890 -915 935 –960 GSM1800 (DCS1800) 1710 –1785 1805 –1880 GSM1900 (PCS1900): 1930 –1990 1850 –1910 GSM network architecture – core components BTS: Base Transceiver Station BSC: Base Station Controller BSS: Base Station Subsystem MSC: Mobile Switching Centre HLR: Home Location Register VLR: Visitors Location Register AuC: Authentication Centre GMSC: Gateway MSC PSTN: Public Switched Telephone Network AuC PSTN HLR VLR MSC GMSC BSC BSC BTS MT BSS GSM network architecture – other elements EIR: Equipment Identity Register – Record of status of phone – White / grey /black (stolen) SMS-C: Short Message Service Centre OMC: Operation and Maintenance Centre BS Locating a Mobile terminal When a MT moves from one location area to another: – – – – – MT initiates the location updating procedure. HLR is notified by the new MSC/VLR. HLR removes old MSC/VLR information HLR confirms and updates the new MSC/VLR. location area update is confirmed with the MT. Mobile Terminating call HLR Location area PSTN GMSC MSC VLR traffic signalling VLR MSC BSC BT S BSC Roaming incoming call PSTN Home network HLR Location area Visited network GMSC VLR MSC MSC VLR MSC BSC VLR BT S Roaming leg paid by recipient BSC BT S Roaming outgoing call Home network HLR Location area Visited network GMSC VLR MSC MSC VLR MSC BSC VLR Billing centre BT S PSTN BSC BT S GSM Mobility Management: Authentication Mobile Terminal Challenge: RAND Random number Key Ks in SIM A3 algorithm Key Ki in MSC A3 algorithm SRESMSC Response: SRESMT If results match, Ks=Ki and the user is genuine Only information transmitted over the air is RAND and SRESMT If equal, then authenticated How does communications everywhere affect the global economy? Increasingly reliant on communications technology for business Variety of actors with competing interests Communications systems becoming the target of cyber-terrorist attacks Communications networks now part of the national large-scale critical infrastructure. 45 INFORMATION CONVERSION Transmission of analogue information Multiplexing Information: ‘Hello! How are you?’ Demultiplexing You and I understand but not the telephone! Analogue signal can be understood by electrical systems but problematic! So all new systems digital 47 Information Conversion Different sources of information are presented with different formats at the input of transmitter. Formatting transforms the source information to a compatible digital format for digital processing. Four basic stages of information conversion 48 Overview of Digital Communication System Format Source encode Encrypt Channel encode Multiplex Pulse modulate Bandpass modulate Freq. spread Multiple access Transmitter Receiver Format Source decode Decrypt Channel Decode Demultiplex Pulse Detect Demodulate Freq. despread Multiple access 49 Transmission side Format Source encode Encrypt Channel encode Multiplex Pulse modulate Bandpass modulate Freq. spread Multiple access Transmitter Transform the source information into bits, assuring compatibility between the information and the signal processing within the DCS. Digital Information Textual Information Analogue Information Encoder Sample Pulse modulate Quantise 50 Formatting Textual Data Textual information compromises a sequence of alphanumeric characters. Each alphanumeric character is transformed into binary by character coding. Most popular character coding method is ASCII Encoded into sequence of k bits called [symbols] 51 You do not have to remember this [1] Sampling (ideal sampling) time domain t original signal x(t) t Sample pulse xp(t) t Sampled signal xs(t) frequency domain f -fm 0 fm f -2fs -fs 0 fs 2f f -fs-fm 0 fm fs s 53 Sampling (real sampling) time domain t original signal x(t) t Sample pulse xp(t) t Sampled signal xs(t) frequency domain f -fm 0 fm f -2fs -fs 0 fs 2f f -fs-fm 0 fm fs s 54 Sampling frequency fs > 2fmax fs < 2fmax 55 Aliasing (ideal sampling) You must remember the term aliasing original signal f signal sampled with fs > 2 fm -fm 0 fm f -fm 0 fm fs signal sampled with fs = 2 fm f -fm 0 fm fs 2fs signal sampled with fs < 2 fm aliasing occurs f -fm 0 fmfs 2fs 56 Aliasing in more detail original signal fmax low-pass filter can recover original signal fs signal sampled with fs > 2 fmax fs 2fs signal sampled with fs = 2 fmax recovery not possible - spectra interfere signal sampled with fs < 2 fmax aliasing distortion occurs Oversampling low-pass filter can recover original signal original signal fmax Easier to implement filter fs oversampling signal sampled with fs > 2 fmax Needs to be ideal filter fs 2fs signal sampled with fs = 2 fmax recovery not possible - spectra interfere signal sampled with fs < 2 fmax aliasing distortion occurs Sampling Theorem To prevent aliasing and hence to allow the original signal to be recovered the sampling frequency (fs) must be given by: fs ≥ 2 fmax where fmax is the highest frequency present in the original signal. This is the SAMPLING THEOREM and is a fundamental theorem. Notice that fmax is the highest frequency present, NOT the highest frequency of interest. 59 Oversampling A process of sampling a signal at more than twice the higher frequency than the highest frequency present in the original signal. Oversampled signal is normally expressed with the oversampled factor of . fs = fmax ; ≥ 2 Oversampling makes it easier to design a simpler filter to recover the original signal 60 Summary Different types of network – how they are linked and different network speeds Analogue, textual and digital transmission Character coding – ASCII Sampling, anti-aliasing and oversampling 61 QUANTISATION Scope Linear quantisation and non-linear quantisation Companding Delta modulation 63 Quantisation and PCM Quantisation results from mapping continuous analogue values to the discrete vales that can be represented digitally. May be linear or non-linear Pulse-code modulation (PCM) is a method used to digitally represent sampled analogue signals – there are many others. PCM invented in 1948 by Sir Alec Reeve at STL Harlow, UK 64 Principle of PCM time domain t original signal x(t) t Sample pulse t Sampled signal xs(t) Sample amplitude represented by N bits 65 Linear quantisation Quantised signal Peak-to-Peak Voltage, Vpp=Vp-(-Vp) = 2Vp Quantisation interval, q, (step size) uniformly distributed over the full range Approximation will result in an error no larger than ±q/2 q Quantising level 66 Quantising levels q Vp Vp q 0 0 -Vp -Vp Quantising level N levels gives a range of (N-1)q Quantising level N levels gives a range of Nq 67 Quantising distortion quantising level signal changes state half-way between quantising levels error q quantised signal +q/2 error signal -q/2 Quantising error power Error is approximately sawtooth over the quantisation region, apart from the dwell regions. p(e) +q/2 1/q t error e -q/2 -q/2 +q/2 A sawtooth waveform has a uniform pdf: all values are equally likely. The area under the pdf must be 1 so that the amplitude is 1/q. Note that p(e)=0 outside the range +q/2 to -q/2 Power in quantising distortion = q 2 2 1 q Dq e 2 p e de = e 2 de = 12 q q 2 Notes this holds for reasonable well-behaved signals without frequent dwell regions. quantising error leads to distortion, not noise, because it is causally related to and dependent on the input: the same input will always produce the same output. the statistics of the distortion are independent of the statistics of the input. this approximation shows that the distortion power is constant and depends only on the step size. Quantiser SDR Consider a quantiser with a maximum range of ±V and N bits. Then we have: q 2V 2N 4V 2 1 V2 and hence Dq 2 N 2 12 3 2 2 N If the signal power is S then we can define a signal to distortion ratio (SDR) : S 3 22 N SDR V2 or in dB: S SDR (dB) 10 log10 2 4.77 6.02N V Quantiser impairment curve SDR (dB) increase N usable clipping log (S/V2) These 2 curves have the same power (S) but clipping will have a different effect on each. As the slope of the clipping line is very steep, the quantiser must be operated well away from that boundary Such an impairment curve is not suitable for signals such as speech that have a very wide dynamic range (speech around 30dB). For instance, if S varies by 30dB this will not give satisfactory results. A flat impairment curve is needed. Dynamic Range (Dy) Max possible signal power (no overflow) Dy 10 log 10 dB. Min. power which gives acceptable SQNR For uniform quantisati on : Max signal power Min power Dy 10 log 10 10 log 10 2 2 q / 12 q / 12 Dy = max possible SQNR (dB) min acceptable SQNR (dB) This final expression for Dy is well worth remembering, but it only works for uniform quantisation! 73 ITU Recommendation – what we need A better impairment curve is obtained by non-liner quantisation known as companding (compressing and expanding). This is done in a codec (coder - decoder). here are two standardised coding laws: the (generally 7-bit) µ-law used in N. America and Japan and the 8-bit A-law used in the rest of the world (including Europe) approx. 30dB 33.2dB SDR(dB) CCITT (now ITU-T) recommendation input level (power) Speech and Linear Quantisation The higher values of the quantisation are rarely used for speech. SNR is worse for lower signals as quantisation noise is the same for all signal magnitudes. Non-uniform quantisation can provide fine quantisation of the weak signals and coarse quantisation of the strong signals. 75 Non-linear quantisation ♦ 8-bits per sample not sufficient for good speech encoding with uniform quantisation. ♦ Problem lies with setting a suitable quantisation step-size. ♦ One solution is to use non-linear quantisation. ♦ Step-size adjusted according to amplitude of sample. ♦ For larger amplitudes, larger step-sizes used as illustrated next. ♦ ‘Non-linear’ because step-size changes from sample to sample. 76 Linear Quantisation and Non-linear Quantisation 15 15 0 0 77 Non-linear quantisation Non linear quantisation uses the logarithmic compression and expansion function. Compress at the transmitter and expand at the receiver. Compression process changes the distribution of the signal amplitude. Lower amplitude signals strength to higher values of quantisation. As the result the compressed speech signal is now more suitable for linear quantisation. The logarithmic compression and expansion function is also called Companding. 78 Implementation of companding (in principle) Pass x(t) thro’ compressor to produce y(t). y(t) is quantised uniformly to give y’(t) which is transmitted or stored digitally. At receiver, y’(t) passed thro’ expander which reverses effect of compressor. analogue implementation uncommon but shows concept well. x(t) Compressor y(t) Uniform quantiser y’(t) Expander x’(t) Transmit or store 79 Companding There are two compading standards: A-law compression (used mainly in Europe) and µ-law compression (used in North America and Japan). The A-law is given by the mathematical expression: sgn x A x FA x 1 ln A and x 1 A sgn x 1 ln A x 1 ln A 1 A x 1 However, it is not used like this, but as a segmented, piece-wise linear approximation. The segmented A-law uses 13 segments (0, ±17) with A=87.6 8-bit code consist of i) polarity bit P (range is ±V) ii) 3 segment decoding bits XYZ iii) 4 bits (abcd) specifying intra segment value on a linear scale 80 Compression law derivation +27 -211 +211 -27 m-law A-law Variation of SQNR with amplitude of sample SQNR dB 48 Uniform 36 A-law 24 12 Amplitude of sample 0 V/16 V/4 V/2 3V/4 V 82 A-law encoding table Segment Coder input range 0 1 2 3 4 5 6 7 0-V/128 V/128-V/64 V/64-V/32 V/32-V/16 V/16-V/8 V/8-V/4 V/4-V/2 V/2-V output code P 000 abcd P 001 abcd P 010 abcd P 011 abcd P 100 abcd P 101 abcd P 110 abcd P 111 abcd P is a polarity bit abcd is a 4-digit intra-segment code quantum interval V/2048 V/2048 V/1024 V/512 V/256 V/128 V/64 V/32 PCM for telephony 8kHz sampling to satisfy Sampling Theorem 8 bits per sample with A-law encoding 64kbit/s digital speech signal Note that the sampling rate of 8kHz leads to a period of 125ms between speech samples Sampling theorem applied to telephony (PCM) Sampling frequency of 8kHz equivalent to a sample every 125ms low-pass anti-aliasing filter v v 3.4kHz f f v v 3.4kHz t t By bandlimiting the incoming speech signal to 3.4kHz and sampling at 8kHz, the sampling theorem is satisfied 8-bit A-law compander Delta modulation (DM) A simpler way than PCM Provides a staircase version of the message signal by referring to the difference between the input signal and its approximation Quantization is done using 2 levels: – Positive difference: + – Negative difference: - Provided that the input signal does not change too rapidly from sample to sample, this approximation works well 87 DM illustration mq(t) Staircase approximation of m(t) m(t) Input signal Binary sequence at modulator output 111111010000000000101111110101010 88 DM Discrete-time relations Let – Ts be the sampling period – e(nTs) be the error signal – eq(nTs) be the quantised error signal 89 DM transmitter Comparator Sampled Input m(nTs) + e(nTs) ∑ Quantiser eq(nTs) Encoder DM data sequence + ∑ mq(nTs-Ts) + Delay Ts mq(nTs) Accumulator 90 DM quantisation error Slope overload distortion Granular noise Slope overload distortion mq(t) Granular noise m(t) To minimise slope overload distortion dm ( t ) max Ts dt 91 Summary Sampling process is restricted by Nyquist criterion – Aliasing will occur during undersampling. The non-linear quantisation is more effective than the linear quantisation at lower quantisation values. A-Law and µ-Law compression are used in the non-linear quantisation. Delta Modulation is a simpler way than PCM. DM is efficient technique for signals that changes less rapid. Slope overload distortion at DM 92 ATM 93 ATM - Main features Legacy now – but structure and principles appear in modern systems Connection-oriented transfer mode The cells are much shorter than in a conventional packet network to get reasonable delay variance. Overhead is minimised to maximise efficiency (e.g. there is no error correction mechanism for payload) Cells are transported at regular intervals; there is no space between cells, idle periods on the link carry unassigned cells. ATM provides cell sequence integrity. ATM cell stream unassigned cell cell from source 1 cell from source 2 cell from source 3 ATM cell stream cell-based transfer mode this means that information from is transferred as fixed-length cells Principle of ATM cell-based transfer mode – this means that information from the source is transferred as fixed-length cells – no “white space” between cells - if no information an empty cell is sent instead. ATM cell structure 5 octet header 48 octet payload Details are given later Cell assembly delay with short blocks of data it takes time to assemble one cell for transmission payload ATM header this is cell assembly delay: for 64kbit/s it is 6ms Segmentation Large data packets need to be segmented: data segment cell stream This is done in the ATM Adaptation Layer (AAL) - considered later ATM relative merits Advantages of ATM – ease of handling VBR services – inherent multiplexing of the cells with ATM offers ease of integration of sources onto one link – the network operator only has to provide one connection (one access link) to the customer and all the services can be provided over this link. Disadvantages – cell delay variation – cell assembly delay. Cell delay variation caused by queueing delays cells from source being tracked this cell delayed by 1 slot because of queueing delays expected delay through the network increased gap reduced gap B-ISDN protocol reference model Management plane Control Plane User Plane Higher Layers Higher Layers ATM Adaptation Layer ATM Layer Plane management Physical Layer Layer management Normal OSI 7-layer model does not apply - separate B-ISDN model Original physical layer interfaces (ITU) Optical or electrical SDH framed or cell-based Bitrates: – 155.52 Mbit/s upstream and downstream – 622.08 Mbit/s in at least one direction (symmetry of this interfaces not yet defined) ATM layer -1 characteristics of ATM layer independent of physical medium. ATM uses virtual connections for information transport: the virtual path and the virtual channel All functions of ATM layer are supported by the ATM cell header. – Cell multiplexing and demultiplexing – Cell Virtual Path Identifier (VPI) and Virtual Channel Identifier (VCI) translation – Cell Header generation/extraction – Generic Flow Control Cell structure NNI header bit 8 5 octet header bit 1 VPI VPI octet 1 VCI VCI VCI 48 octet payload CLP PT HEC 1st octet, UNI header GFC VPI NNI: network node interface UNI: user network interface VPs and VCs Virtual Path (VP) Physical layer Virtual Channel (VC) Each VP within the physical layer has its own distinct Virtual Path Identifier (VPI); each VC within a VP has its distinct Virtual Channel Identifier (VCI) VPI & VCIs: specific to a link routeing information in switch VPIa, VCIb input output port VPI VCI port VPI VCI ....... ...... ...... ....... ..... ...... P a b Q x y ....... ...... ...... ....... ..... ...... VPIx, VCIy input port P output port Q VC & VP Switching VC switch Endpoint of VPC VP switch representation of VC and VP switching VP switch representation of VP switching Virtual Paths (VPs) VP generic name for a bundle of VC links, all VC links in the bundle having the same endpoints Virtual path links concatenated to form Virtual Path Connection (VPC) VPs provide logical direct routes between switching nodes via intermediate cross-connects. VP identified by VPI - routeing translation tables in each node provide VPI translation. VP concept may also be used in access network to provide virtual leased lines, or to allow access to competing operators. AAL introduction ATM Adaptation Layer (AAL) performs the necessary mapping between the ATM layer and the next higher layer at the edge of the network. Functions of AAL depend upon higher layers (ie on services as well) Examples of service provided by AAL: – – – – – handling of quantization effect from cell payload size handling of transmission errors handling of lost and mis-inserted cell conditions flow control and timing control segmentation and reassembly AAL - principles of segmentation user information addition of Convergence Sublayer header and trailer protocol AAL information to the user information addition of Segmentation and Reassembly Sublayer header and trailer protocol information to every segment Segmentation payload for the cell heade r cell payload cell addition of the ATM header ATM layer Segmentation without end segment indication data units 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 data segmented into cells received cells - with one missing because of cell loss 1 2 3 5 1 2 3 4 5 1 2 3 4 5 reconstructed segments - all in error because of the slip of 1 cell 1 2 3 5 1 2 3 4 5 1 2 3 4 5 Segmentation with end segment indication data units end segment indicator 1 2 3 4 5 data segmented into cells received cells - with one missing because of cell loss 1 2 3 4 5 1 2 3 4 5 1 2 3 1 2 3 4 5 5 1 2 3 4 5 reconstructed segments - only 1 in error because reconstruction starts again after end segment received 1 2 3 5 this data unit in error 1 2 3 4 5 1 2 3 4 5 these data units are correct Connection admission control (CAC) Network decides at call set-up whether to accept a (VP or VC) connection request. Criteria: – sufficient resources (QoS) available for connection request across network – agreed QOS of existing calls not affected Call can have more than one connection: CAC procedures should be performed for each CAC needs the following information: – source traffic characteristics – required QOS class. Connection admission control (CAC) CAC uses this information to determine: – whether the connection can be accepted or not – the traffic parameters needed by usage parameter control – the allocation of network resources. UPC continued Functions – checking validity of VCIs and VPIs – checking traffic volume per VPC and VCC to ensure contract not violated Actions on violation – – – – Discarding of cells Dropping connection Tagging of cells (Punitive charging)